Last year, we spearhead our first annual SaaS Security Survey Report, where the findings illuminated the SSPM landscape and where the market was holding. In the 2022 SaaS Security Survey Report, in collaboration with CSA, we examine the state of SaaS security in today’s enterprises and see how much the market and the overall space of SSPM has matured in just one year. This report gathers anonymous responses from 340 CSA members, CISOs and security professionals, to examine not only the growing risks in SaaS security but also how these different organizations are currently working to secure themselves. While there are many takeaways from the survey, these are our top seven.
Demographics
Before diving into the findings, here is some quick background information on the anonymous respondents. The majority (71%) of respondents were located in the Americas, another 17% from Asia, and 13% from EMEA. Of these participants 49% influence the decision making process while 39% run the process itself. The survey examined organizations from a variety of industries, such as telecommunications (25%), finance (22%), and government (9%). For more details regarding the demographics, please refer to full report.

1: SaaS misconfigurations are leading to security incidents
Since 2019, SaaS misconfigurations have become a top concern for organizations, with at least 43% of organizations reporting they’ve dealt with one or more security incidents caused by a SaaS misconfiguration. However, since many other organizations state they are unaware if they had experienced a security incident, the number of SaaS misconfigured-related incidents could be as high as 63%. These numbers are striking when compared to the 17% of security incidents caused by IaaS misconfigurations.
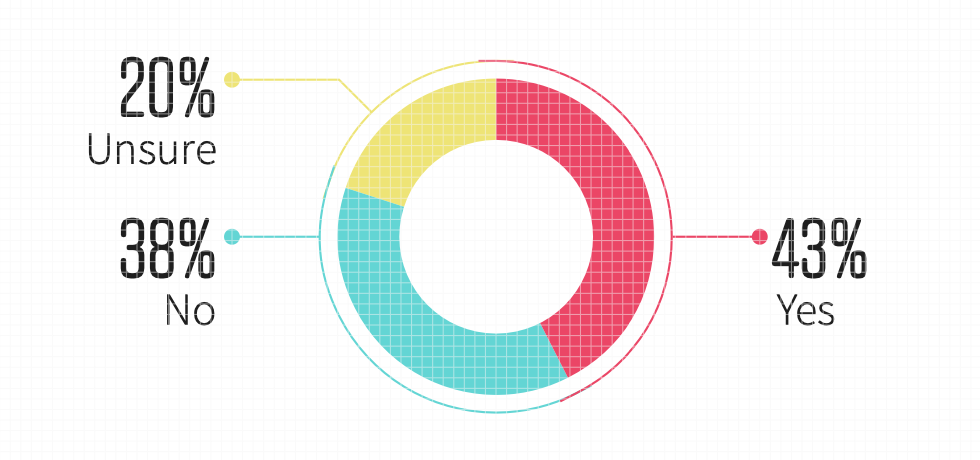
2: Lack of visibility and too many departments with access reported as leading Cause for SaaS misconfigurations
So what exactly is the cause of these SaaS misconfigurations? While there are several factors to consider, the survey respondents narrow it down to the two leading causes – having too many departments with access to SaaS security settings (35%), and a lack of visibility into the changes in the SaaS security settings (34%). These are two related issues, neither of which are surprising given that lack of visibility was rated a top concern when adopting SaaS applications, and that on average organizations have multiple departments with access to security settings. One of the leading reasons for the lack of visibility is the fact that too many departments have access to security settings and many of these departments don't have proper training and focus on security.

3: Investment in business-critical SaaS apps is outpacing SaaS security tools and staff
It’s well-known that businesses are adopting more apps – this past year alone, 81% of respondents say that they have increased their investments in business-critical SaaS applications. On the other hand, investment in security tools (73%) and staff (55%) for SaaS security is lower. This dissonance represents an increasing burden on the existing security teams to monitor SaaS security.

4: Manual detection and remediation of SaaS misconfigurations keeps organizations exposed
46% of organizations that manually monitor their SaaS security are conducting checks only once a month or less, while 5% don't conduct checks at all. After discovering a misconfiguration, it takes additional time for security teams to resolve it. Approximately 1 in 4 organizations take one week or longer to resolve a misconfiguration when remediating manually. This lengthy timing leaves organizations vulnerable.


5: Use of an SSPM reduces timeline to detect and remediate SaaS misconfigurations
The flip side of the coin for finding #4 is that the organizations that have implemented an SSPM can more quickly and accurately detect and remediate their SaaS misconfigurations. The majority of these organizations (78%) utilize an SSPM to check their SaaS security configurations once a week or more. When it comes to resolving the misconfiguration, 81% of organizations using an SSPM are able to resolve it within a day to a week.


6: 3rd party app access is a top concern
Third party apps, also called no-code or low-code platforms, can boost productivity, enable hybrid work, and are overall essential in building and scaling a company’s work processes. However, many users quickly connect 3rd party apps without considering what permissions these apps are requesting. Once accepted, the permissions and subsequent access granted to these 3rd party apps could be harmless or as malicious as an executable file. Without visibility into the SaaS-to-SaaS supply chain employees are connecting to their organization’s business-critical apps, security teams are blind to many potential threats.

7: Planning Ahead and Implementing SSPM
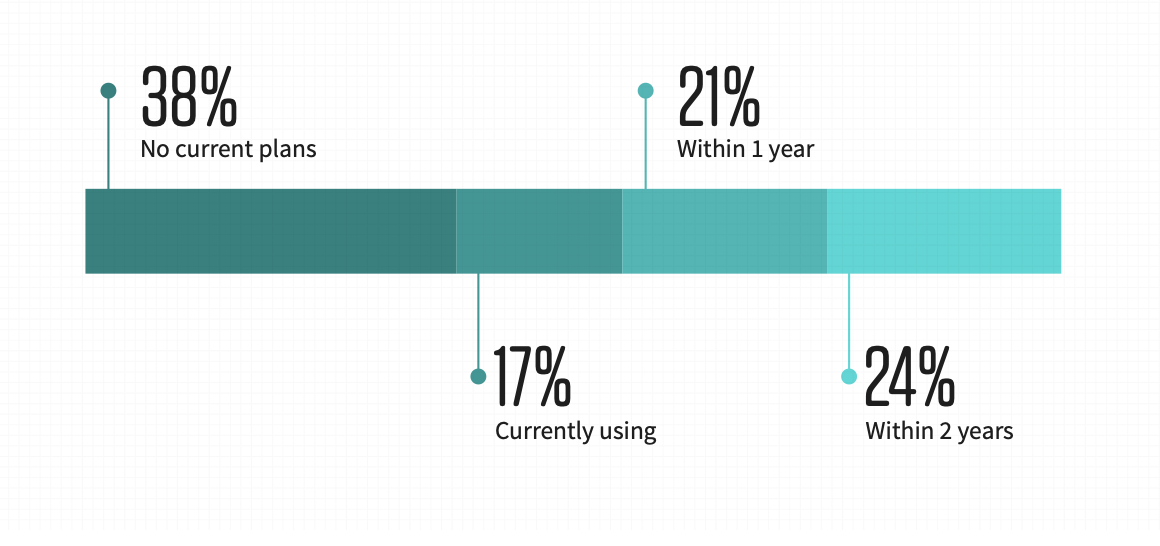
Despite the category being introduced to the market two years ago, it is fast maturing. When assessing four cloud security solutions, SSPM receives an average rating of “somewhat familiar”. Furthermore, 62% of respondents report that they are already using an SSPM or plan to implement one in the coming 24 months.
Conclusion
The 2022 SaaS Security Survey Report offers insights into how organizations are using and protecting their SaaS applications. It is without a doubt that as companies continue to adopt more business-critical SaaS apps, there is more risk. To face this challenge head on companies should begin securing themselves through two best practices:
- The first being to enable security teams to gain full visibility into all SaaS app security settings, including 3rd party app access and user permissions, which in turn allows departments to maintain their access without risk of making improper changes that leave the organization vulnerable.
- Secondly, companies should utilize automated tools, such as SSPMs, to continuously monitor and quickly remediate SaaS security misconfigurations. These automated tools allow security teams to recognize and fix issues in near-real time, reducing the overall time the organization is left vulnerable or preventing the problem from occurring all together.
These kinds of best practices will provide support to security teams without preventing them or any other departments from doing their work.
About the writer






.webp)









