

Adaptive Shield’s SaaS Security Posture Management (SSPM) platform has transformed the way organizations secure and monitor their applications. In our latest update, we add a new dimension to improve accountability and reporting – the ability to measure SaaS Security posture by business unit, subsidiary, team, or any other bucket of choice
SaaS applications are used by every department, each of which relies on multiple applications for collaboration, data storage, and getting the job done. SaaS security is unique in the sense that it involves multiple stakeholders across the corporation, working together in an integrated fashion with clear ownership, tracking, and measurement. Adaptive Shield’s platform monitors each user, application, misconfiguration, and connected app that potentially puts SaaS data at risk.
Using the platform, organizations can easily assign applications to different domains for better tracking, including:

With this new Organization Domain view, Adaptive Shield can easily be used to manage security for independent and semi-independent subsidiaries. It enables department heads to easily report on the security posture of their applications and create benchmarks of excellence based on the corporate division.
The new view provides security and business teams with a wealth of information. It provides an at-a-glance understanding of the state of SaaS security by division. Each domain card includes an overall posture score and a breakdown of the number of apps that fall within posture score ranges. The domain card also shows the number of users, devices, and third-party applications that are connected to the department’s applications.
Nearly every element within a division’s card can be clicked on for a deeper dive. See all the apps included in the domain; drill down into users, devices, and third-party apps; and review security checks to see issues that are impacting posture.
Adaptive Shield continues to innovate and enhance our SSPM platform. Stay tuned for more updates and we continue to continually develop more features and tools to secure the SaaS stack.


Detection and response sit at the heart of any well-thought-out cybersecurity program. As resilient and strong as perimeter-based defenses are, most security professionals will concede that threats can make their way into the network, device, or application.
Detection and response tools come into play after the breach has occurred, but often are able to stop the threat actor from moving forward. You can think about this in terms of a bank robbery, where the bad guys sneak their way into the vault and get caught before they can get out with the cash. The bank robbers were able to avoid security outside the vault, but once they were inside, some type of threat detection system alerted police that a robbery was in process, and the criminals were stopped.
Detection and response are the last lines of defense. Sometimes they can completely prevent a cybersecurity incident from occurring at all, while other times they detect a breach in progress and are able to significantly limit the damage. However, for all the benefits of detection and response, there is still some confusion in the marketplace about these tools.

Detection and Response have made their way into the names of many security tools. Endpoint Detection and Response, Extended Detection and Response, and Network Detection and Response are just a few of the many tools used to secure corporate and government networks.
These detection tools are vital but are limited to the areas that they serve. Detecting malware threats within endpoint devices is certainly critical in a world where data is accessed by computers, tablets, and mobile phones. XDR often takes EDR one step further, gathering intelligence from networks, users, and workloads.
XDR can be confusing to security teams, who believe they have threat detection covered across their organization. While XDR is a powerful tool, it often lacks the context to threats that native tools have to offer. For example, XDR is capable of some network threat detection capabilities, but it is a far less rich solution than NDR, which limits false positives through network context and automated threat response.
Identity Threat Detection and Response (ITDR) is one of the newest areas of threat detection. ITDR turns its attention to users and looks for any types of threats emanating from a user account.
User security starts with credentials, MFA, and SSO. However, not every application or organization requires MFA and SSO, and even some that use SSO allow local login for app admins. If a user hands over credentials during a social engineering attack, and MFA is not enforced, the threat actor may have full access to the application.
This is where ITDR steps in. It combines data from user and entity behavior analytics (UEBA), app logs, and IP data to find behavioral patterns that indicate an attack is underway. While some of this data may be accessible to an XDR, that tool lacks the deep user knowledge to be very effective.
Click here to read more about ITDR and key capabilities
For example, ITDRs are able to distinguish between a legitimate user logging in on a cellular and land-line connection, which may appear as coming from two different geo-locations, and a threat actor logging in from a foreign or unknown locale. Using the ITDR, security teams aren’t pestered by a series of false positives, whereas detection and response tools that aren’t designed with an understanding of identity context will deliver false positives and lead to alert fatigue.

Today’s successful security teams are developing models based on domain specialization, data enrichment, and integration. It combines a number of tools, including ITDR, EDR, XDR, NDR, DDR (Data Detection and Response), and CDR (Cloud Detection and Response).
Part of this is due to changes within organizations. Most have moved away from centralization, with the proliferation of cloud processing and SaaS apps.
To keep up, security teams are using decentralized, loosely coupled tools using advanced and nested analytics to monitor for threats, using multiple vendors and open content. As threats are detected by the various tools, they are sent to a central orchestration engine, where they can be analyzed and acted upon.
As the cybersecurity landscape evolves and threats become more sophisticated, the importance of detection and response cannot be overstated. While perimeter-based defenses are essential, the reality is that threats can find their way into networks, devices, and applications. This is where detection and response tools play a critical role in mitigating the impact of breaches and cyberattacks.
EDR, XDR, NDR, and ITDR are just a few examples of the specialized solutions available. Each tool has its strengths, but organizations require a combination of these tools to detect threats.
ITDR emerges as a vital addition to the cybersecurity arsenal. By focusing on users and analyzing behavioral patterns, ITDR provides a deeper understanding of identity context, helping to distinguish between legitimate users and threat actors. Integrating ITDR into a comprehensive security program alongside other tools creates a robust defense strategy.
.webp)
.webp)
The healthcare industry is under a constant barrage of cyberattacks. It has traditionally been one of the most frequently targeted industries, and things haven't changed in 2023. The U.S. Government's Office for Civil Rights reported 145 data breaches in the United States during the first quarter of this year. That follows 707 incidents a year ago, during which over 50 million records were stolen.
Health records often include names, birth dates, social security numbers, and addresses. This treasure trove of data is used in identity theft, tax fraud, and other crimes. It is the high value of the data that makes healthcare applications such a promising target.
The healthcare industry was hesitant to adopt SaaS applications. However, SaaS applications lead to better collaboration among medical professionals, leading to improved patient outcomes. That, combined with SaaS's ability to reduce costs and improve financial performance, has led to the industry fully embracing SaaS solutions.
Today, medical facilities store patient records, billing records, and other sensitive data containing both PHI (protected health information) and PII (personally identifiable information) are in many cases stored in Salesforce, Google Workspace, and Microsoft 365.
In the United States, medical data is protected under HIPAA, the Health Insurance Portability and Accountability Act. Security failings impacting more than 500 individuals are broadly reported in the media and are accompanied by significant fines.
SaaS applications like Salesforce, when they contain HIPAA-compliance add-ons, are secure enough to prevent threat actors from entering the applications and accessing patient data. SaaS applications are always updated to the latest version and don't have the same types of vulnerabilities found in on-premises software.
SaaS developers invest heavily in delivering secure software solutions. They maintain teams of security professionals who constantly monitor and update their software to address emerging threats. These applications run on advanced infrastructure with robust physical security measures, redundant systems, and disaster recovery systems. They adhere to strict industry standards, ensuring the highest level of security and compliance for healthcare data.
In a report issued in August 2022 by the Office of Information Security and the Health Sector Cybersecurity Coordination Center (HC3) on the impact of social engineering on healthcare, researchers found that 45% of all attacks on the healthcare industry began with a phishing attack. Employees were manipulated into handing over their login credentials, allowing threat actors to enter through the front door.
SaaS applications have multiple layers of defense against those types of breaches. For example, many SaaS applications require MFA during login. Without a one-time password, most threat actors will be thwarted when trying to access with just a username and password. Second, many organizations require SSO to access their apps. This additional layer of identity fabric creates more complexity for threat actors as they attempt to breach the SaaS application. There are over 100 security checks within Salesforce and Microsoft 365 that combine to form a strong perimeter of defense.
It wasn't long ago that anyone who managed to breach a SaaS application had carte blanche to do anything within their permission set. Steal credentials from an admin, and the entire app could be in control of the threat actor within minutes. That is no longer the case.
Leading SaaS security tools have added a layer of identity threat detection and response (ITDR) to the equation. This last line of defense ensures that if threat actors were able to access the application, security teams are alerted when threat actors enter the SaaS app, even if they access the application with valid credentials.
ITDR recognizes behavioral anomalies within the individual user. If a threat actor enters a SaaS stack and acts suspiciously, ITDR will flag those behaviors and alert the security team, who can disable the user account and conduct an investigation.
The healthcare industry is already familiar with role-based access to medical records. Those who don't need access to patient records aren't able to review medical files. This approach is critical to SaaS security. By following the Principle Of Least Privilege (POLP), each user is only able to access materials required for their role. If credentials for those users are compromised, threat actors will be unable to access the PHI data that they are searching for.
A SaaS Security Posture Management (SSPM) platform, like Adaptive Shield, is the most important tool used to defend healthcare applications. SSPMs conduct 24/7 automated monitoring of security settings, staying on top of settings and alerting security personnel when configurations are changed. If a user mistakenly reduces the app's security posture, SSPMs help to ensure that the misconfiguration is closed quickly.
SSPMs also monitor third-party applications that connect to the core SaaS apps. It tracks their permissions and triggers an alert when granted permissions exceed corporate policy or HIPAA standards. It tracks dormant users, external users, and authorized users, ensuring that they, like physicians treating patients, do no harm to the application.
By implementing an SSPM, healthcare organizations can ensure that the sensitive patient data stored within the applications are secure.


Identities in SaaS applications can be either human, associated with individuals, or non-human, such as service accounts, API keys, and 3rd party app OAuth authorizations. Any unsecured identity in a SaaS app can create an opening for cybercriminals to compromise, leading to data breaches, compliance violations, and financial losses.
In a webinar hosted by The Hacker News, Maor Bin, CEO and co-founder of Adaptive Shield, and CISO James Azar discuss how to protect SaaS applications from exposure to identity risks through a strong identity security posture.
Watch the full recording of the webinar here.
“SaaS applications are all about identity. This is the modern IT stack,” says Bin. “It’s about securing your entire stack, not one application or another. Threat actors will not sit at home and do nothing, they will go after the less secure application in the chain. There will always be more attacks.”
As Bin explains in the webinar, the challenge in securing identities in SaaS applications is not only their increasing volume and velocity of change in the SaaS environment, but the fact that each one is so different from the other. As security teams are not responsible for most apps, gaining visibility into the apps is crucial, he says.
Azar agrees. “When you talk to cybersecurity practitioners, the number one challenge they are dealing with is a lack of visibility in asset management. If you are running SaaS applications with limited visibility into the assets that you have, you are blind to any risks or threats to your SaaS stack,” he says.
In the webinar, Bin reviews the key characteristics of identity security for human and non-human accounts and how they differ, especially the fact that non-human identities behave differently, making threats more difficult to detect.
Human identity security components:
How non-human identities are different:
Despite the risks, non-human account monitoring is typically neglected. Human accounts get higher priority from a security perspective. Human and non-human accounts are often managed in a non-centralized manner.
It comes down to the fact that “you can’t secure what you can’t see,” says Bin.
Dedicated controls are needed for both human and non-human identities and to combine them into one view.

To ensure SaaS identity security for both human and non-human accounts, an Identity Threat Detection and Response (ITDR) mechanism comes in as a crucial layer to stitch everything together. Creating a strong identity fabric for identity security posture management within an SSPM, ITDR can identify irregularities specific to non-human identities including anomalous patterns of behavior.
Therefore a combination of prevention (SSPM) and threat detection (ITDR) can secure all types of user accounts, human and non-human, Bin concludes.
Watch The Hacker News webinar to learn more about Adaptive Shield’s SSPM and ITDR capabilities for identity security posture management.
.png)
.png)
The rapid uptake of cloud services is presenting a challenge for organizations to keep their ecosystems safe from security breaches. To provide guidance, Gartner® recently published a Quick Answer report for security and risk management leaders on security posture management tools for cloud environments.
As “cloud incidents continue to be dominated by configuration and identity errors on the part of the users, security and risk management leaders can ensure their clouds are configured securely by using the capabilities identified in this research,” Gartner says in the report.
The research, “Quick Answer: How to Choose the Right Security Posture Management Tools for Your Clouds,” covers infrastructure-as-a-service (IaaS), platform-as-a-service (PaaS), and software-as-a-service (SaaS) cloud environments. It provides organizations with a checklist of capabilities to look for when selecting a security posture management solution.
However, “SaaS protection remains segregated from IaaS and PaaS, and is covered by a separate family of SSPM products,” the report notes. According to the checklist, the primary function of Security Posture Management (SSPM) is “validation of secure configuration and interconnection of SaaS platforms.”
Adaptive Shield is named in the report as a Representative Vendor in SSPM.
In the report, Gartner provides a list of six key capabilities and criteria for selecting an SSPM. “Each SaaS platform is different, so SSPM vendors must be chosen based on both depth of visibility and which SaaS they support,” the report says.
Here’s how we believe the Adaptive Shield SSPM solution delivers on Gartner recommendations.
SSPM key capabilities:
A core SaaS stack of business-critical SaaS apps includes solutions such as Microsoft Office 365, Google Workspace, Salesforce, Workday, Slack, Teams, Zoom, Okta, GitHub, and ServiceNow. As the report notes, “each SaaS platform is different.”
These major SaaS apps are all sophisticated, each built with a complex set of security settings. The combined configurations for these apps alone can reach from hundreds to thousands that must be configured correctly and continuously to limit risk.
Adaptive Shield’s platform supports all these and other business-critical SaaS integrations. The platform conducts automated security checks to ensure proper configurations, identifies security drifts across all SaaS application security controls, and provides detailed step-by-step remediation.
One of the first steps when shrinking the threat surface is gaining an understanding of the full environment.
Adaptive Shield’s App Inventory shows all SaaS apps discovered, including API keys and OAuth apps, and the user who granted the OAuth consent, among many other important details. The inventory detects unsanctioned apps that are connected to apps integrated within the Adaptive Shield platform.
According to Gartner, a key selection criterion for an SSPM is the ability to provide visibility into identities, as identity errors are a factor currently dominating cloud incidents.
Every user identity is a potential entrance into a SaaS application. These include human and non-human accounts, including service accounts, API keys, and OAuth authorizations.
Adaptive Shield’s User Inventory delivers a robust Identity Security Posture where each SaaS user has consolidated information on permissions, roles, privileges, and user-specific failed security checks. By gaining in-depth knowledge of user permissions and behavior, security teams can identify users who put the application at risk, as well as inactive users, overprivileged admins, and other user-specific threats.
Key SSPM selection criteria:
Monitoring settings and identifying misconfigurations that could compromise the security of the SaaS application is a key component of SaaS security. The thousands of security checks within the Adaptive Shield platform form the foundation of our SSPM.
Through automated monitoring, Adaptive Shield identifies weaknesses in the application’s posture, and alerts stakeholders of the issue. It includes remediation directions needed to harden the app and reduce the attack surface.
Adaptive Shield also detects connected applications. It monitors their scopes and alerts stakeholders when applications request high-risk permissions, such as write, delete, or download capabilities. The security team can review the connected app, and make a determination as to whether the functionality it provides is worth the risk.
Enterprises are connected to hundreds of apps on average across business departments.
Adaptive Shield supports the industry’s widest portfolio of out-of-the-box integrations. In addition to 150+ out-of-the box apps, Adaptive Shield can integrate with any SaaS app. The Integration Builder covers custom, proprietary, or any other apps on top of the out-of-the-box SaaS integrations.
The Adaptive Shield Integration Builder enables the addition of less common or niche apps that could be critical for the needs of legal or medical teams, all with the same level of security.
To secure a company's SaaS stack, the security team needs to be able to identify and monitor all that happens within their SaaS ecosystem.
Adaptive Shield’s security checks are both numerous and complex. They review and capture a great deal of information, allowing those tasked with SaaS app security to make informed decisions.
Each security check includes:
Gartner, Quick Answer: How to Choose the Right Security Posture Management Tools for Your Clouds, Charlie Winckless, Manuel Acosta, and 1 more, 21 February 2024
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.


We’re excited to announce that Adaptive Shield has made its debut on the Cyber 66, the Citizens JMP annual list of the hottest privately held cybersecurity companies. The annual survey highlights the 66 most well-positioned companies currently influencing the cybersecurity landscape.
In compiling the 2024 list, the researchers predicted 2024 would continue to be impacted by “high-profile breaches leveraging identity-based attacks.”
“Cybersecurity remains in a constant state of flux, with threat actors, the organizations they target, and the security tools that attempt to be the shield between the two continuously shifting their goals and related strategies,” Trevor Walsh, research analyst at the firm, said in the decision to add Adaptive Shield to the list in 2024.
Adaptive Shield is a key player in the growing arena of SaaS security, which includes SaaS Security Posture Management (SSPM) and ITDR categories, with the purpose of safeguarding companies amid the rapid increase in demand for SaaS applications, the report noted.
“We’re excited to be recognized as a leader in cybersecurity innovation at a critical juncture as SaaS becomes mainstream for business-critical activities,” said Maor Bin, CEO and co-founder of Adaptive Shield. “We remain committed to advancing SaaS security to help organizations protect their SaaS attack surface that is increasingly being targeted by sophisticated cyberattacks.”
Adaptive Shield covers more than 150 popular SaaS applications under its platform, enabling streamlined protection, detection, and response across an organization’s entire SaaS stack through Misconfiguration Management, SaaS-to-SaaS Access and Discovery, Identity Security Posture, Device-to-SaaS User Risk Management, and Identity Threat Detection & Response (ITDR).
The honor follows the additional investment secured by Adaptive Shield in 2023 from Blackstone Innovations Investments, bringing its total capital raised to $44M.


Last month, The Verge reported on an amusing story of abusing Slack in a design, technology, science, and science fiction website. Tom McKay of IT Brew successfully hid on Slack after leaving the company in 2022 by assuming the persona of "Slackbot," remaining undetected by management for months. McKay shared screenshots of his antics on X and confirmed the escapade to The Verge. By changing his profile picture to resemble an angrier version of Slackbot's icon and altering his name to "Slackbot" using a special character (Unicode character “о”), McKay's account evaded deletion, allowing him to send bot-like messages to colleagues such as, “Slackbot fact of the day: Hi, I’m Slackbot! That’s a fact. Have a Slack-ly day!”.
On first read McKay's escapade seems as a lighthearted reminder of the potential for mischief in digital spaces. This was how the cyber community of Hacker News of Y Combinator received this news, which prompted users to share their own experiences from the old days, including a story from the days of dialup internet. However, as the thread continued, some people started wondering about the security impact. The r/sysadmin subreddit on the other hand was quick to realize the lack of an offboarding process. Other Slack admins shared their frustration and challenges of securing the SaaS app.
When employees transition out of an organization, it's imperative for security that access to corporate assets be promptly revoked. While much of this process is automated through workflows that remove employees from the identity provider (IdP), manual deprovisioning is necessary for applications not integrated into the IdP. Challenges in permanently removing users from SaaS applications include applications not synced with the IdP, the use of shared passwords among teams, and individuals retaining access through previously shared credentials acquired during their tenure. Failure to fully offboard users poses significant risks such as data theft or breaches, either by former employees or unauthorized individuals with stolen credentials. Overcoming these hurdles is crucial for maintaining robust security measures within organizations.
Slack is a leading collaboration and communication platform, revolutionizing how teams work together. With its intuitive interface, real-time messaging, and extensive integration options, Slack has gained popularity among organizations of all sizes. However, as with any cloud-based platform, it is crucial to address security issues and concerns to protect sensitive data and maintain a secure working environment. While Slack offers robust security measures, it is essential to be proactive in addressing potential security issues and concerns. Organizations must recognize the value of the data shared within the application, including sensitive files, proprietary information, and confidential communications.
To secure Slack, here are some best practices to follow:
As the cyber threat landscape evolves, even lighthearted stories like this one provide important lessons for organizations as they fortify their defenses against sophisticated attacks. The fake Slackbot underscores the pressing need for comprehensive security measures and proper off-boarding.
The easiest way to deprovision users from SaaS applications is through a SaaS Security Posture Management (SSPM) platform that is integrated with a SOAR. Using automated workflows, these processes quickly identify and fully deprovision offboarded employees who maintained access to SaaS applications.
By using an SSPM, enterprises can confidently move forward, knowing that access to their applications is under their full control.
Have users you need to deprovision? Download our latest ebook, Offboarding Employees from Your SaaS Stack in 7 Steps!
.png)

GitHub is in the news again, with malicious repositories stealing login credentials and cryptocurrency from developers’ devices. According to researchers at antivirus firm G-Data, these repositories, which are near clones of legitimate repositories, all lead to one of at least 13 GitHub repositories that install the RisePro malware.
Users have to go through several steps before they download the malware. They begin by downloading a README.md file, which contains a password for cracked software. From there, they can access the installer. The MSI installer unpacks a new executable file. Once the loader is executed, the malicious payload is injected into the victim’s device. RisePro gathers sensitive data and exfiltrates it to a Telegram channel.
While there are a number of settings one should check to make sure their GitHub is secure, protection from this type of attack begins with encouraging users to verify the authenticity of repositories before interacting with them. In this case, many of the repositories often mimic the naming of genuine repositories to confuse users.
GitHub has several configurations that organizations should secure to minimize the risk of accidental exposure. For example, enabling secret scanning and push protection for public and private repositories safeguards code against unauthorized access and code modifications.
Personal access tokens (PAT) should also be closely monitored. Configure the application to send alerts when unused PATs need to be revoked to prevent misuse, or let the security team know when an excessive amount of PATs are created.
Branch protection also plays a key role in GitHub security. To ensure that no malicious code is inserted into the main branch, all commits should be signed with a GPG or S/MIME signature. Furthermore, all code should pass a review that meets the company’s standards before it is merged.
Finally, security teams should review audit logs to find unauthorized changes. GitHub logs include information about additions to the codebase, which can be used for early detection of suspicious activities and identifying unauthorized access.
As the cyber threat landscape evolves, it becomes increasingly crucial for organizations to strengthen their defenses against sophisticated attacks, such as the one analyzed in this blog post. The recent malicious campaign targeting GitHub environments highlights the urgent need for robust security measures.
Deploying a SaaS Security Posture Management (SSPM) solution is essential for enhancing the security of GitHub environments. This involves prioritizing measures to counter coming from repositories. Furthermore, the importance of an Identity Threat Detection and Response (ITDR) solution cannot be emphasized enough, particularly for swiftly identifying and addressing incidents such as account compromises, unusual activities, and potential data leaks.
The insights shared in this blog post offer valuable guidance for organizations aiming to reinforce their security posture. They underscore the interdependence between SSPM solutions and ITDR capabilities in establishing a comprehensive SaaS security framework. By embracing these approaches, organizations can proactively shield their digital assets, ensuring resilience against evolving cyber threats while upholding the confidentiality, integrity, and availability of sensitive data.


The US National Institute of Standards and Technology (NIST) cybersecurity framework is one of the world's most important guidelines for securing networks. It can be applied to any number of applications, including SaaS.
One of the challenges facing those tasked with securing SaaS applications is the different settings found in each application. It makes it difficult to develop a configuration policy that will apply to an HR app that manages employees, a marketing app that manages content, and an R&D app that manages software versions, all while aligning with NIST compliance standards.
However, there are several settings that can be applied to nearly every app in the SaaS stack. In this article, we'll explore some universal configurations, explain why they are important, and guide you in setting them in a way that improves your SaaS apps' security posture.
Role-based access control (RBAC) is a key to NIST adherence and should be applied to every SaaS app. There are two types of permissions within a SaaS application. Functional access covers things like creating accounts and navigating the application. Data access permissions, on the other hand, govern which users can retrieve and modify data. The admin account (or the super-admin account in some apps) is the most sensitive within the app, as it has full access to both types of permissions.
For threat actors, breaching an admin account is akin to winning the lottery. They have access to everything. Organizations must do everything within their power to maintain control over these accounts. This control is managed through configurations and best practices.
It's important to have a minimum of two admins for every application. This redundancy makes it difficult for an admin to act alone against the best interests of the organization, as admins can monitor each other for any signs of a breach.
However, each admin increases the application's attack surface. Organizations must strike a balance between having enough admins to adequately service the application while limiting exposure. An automated review of the number of admins should trigger alerts when the number of admins is outside the preferred range.
External admins introduce a new layer of uncertainty into SaaS security. Because they sit outside the organization, the security team can't control the password policies or authentication tools that they use.
For example, should a threat actor try to log into your application and click Forgot Password, there is no way to know whether the threat actor can breach the external admin's email account. That lack of oversight of external users could lead to a deep breach of your SaaS application, which is why NIST advises against having external admins. Depending on the application, either block external admins from getting admin privileges or identify external users with admin rights and remove those privileges.
For companies that hire an external IT company or outsource to MSSPs, those individuals should not be considered external. However, they should continue to monitor for other external users being given admin permissions.
To comply with NIST standards, all admin user accounts should be required to access the application using multi-factor authentication (MFA), such as a one-time password (OTP). MFA requires users to present a minimum of two forms of ID before it authenticates the user. A threat actor would need to compromise two authentication systems, increasing the level of difficulty of the compromise and reducing the risk to the account. Make sure to set MFA for admins as required (we also recommend MFA for all users, but it is a must-have for admins).
SaaS data leaks pose significant risks to organizations and their users, potentially compromising sensitive information stored within cloud-based applications. SaaS applications are marketed as collaboration tools. However, the configurations that enable users to work together can also compromise files and data. NIST, for its part, advocates monitoring the permissions of every resource.
A visible calendar can expose employees to socially engineered phishing attacks, while shared repositories can lead to a company's internal source code being shared publicly. Email, files, and boards all contain sensitive data that should not be accessible to the public. While the following configurations are often called something different in each application, almost any app that stores content will have this type of control.
The difference between Share with All and Share with a User is profound. When items are shared with all, anyone with a link can access the materials. Share with a User, in contrast, adds an additional authentication mechanism, as the user needs to log in before accessing the material.
To reduce the content that is exposed, app admins should disable sharing over public URLs ("Anyone with the link"). In addition, some applications allow users to revoke access to URLs that have already been created. When available, organizations should be sure to toggle that setting to on.
Many applications allow authorized users to invite external users to the application. However, most applications don't implement an invite expiration date. In those circumstances, invites sent years prior can provide access to a threat actor who has just breached an external user's email account. Enabling an auto-expiration date on invites eliminates that type of risk.
It's worth noting that in some apps, configuration changes are retroactive, while others will only take effect moving forward.
Passwords are the first line of defense against unauthorized access. NIST advocates for a strong and well-managed password policy, which is essential to protect sensitive user data, confidential business information, and proprietary assets stored within the cloud-based infrastructure. The uniqueness, complexity, and regular updating of passwords are critical aspects of a robust security posture.
Passwords serve as a fundamental element in a layered security approach, complementing other security measures such as multi-factor authentication (MFA) and encryption. Compromised passwords can be a gateway for malicious actors to exploit vulnerabilities in the SaaS environment. The effective management of passwords enhances the overall resilience of SaaS systems, contributing to a more secure and trustworthy digital ecosystem for both businesses and their users.
In a spray attack, threat actors enter a username and common password terms, hoping to get lucky and access the application. Requiring MFA is the recommended way to prevent password spray attacks. For those that don't insist on employees using MFA as part of the authentication process, many apps allow organizations to ban words from being used as passwords. This list of words would include terms like password1, letmein, 12345, and the names of local sports teams. Additionally, it would include terms like the user's name, company products, partners, and other business terms.
Going into the configurations and adding a custom banned words list can significantly reduce the risk of a successful password spray attack.
Most SaaS applications allow the organization to customize password complexity. These range from allowing any password to requiring alphanumeric characters, capital and lowercase letters, symbols, or a password length. Update the password requirements in the app to match your organization's policy.
If your organization doesn't have a password policy, consider following NIST guidelines:
It may seem unlikely that threat actors spend their time looking for misconfiguration that they can exploit. Yet, that is exactly what the Russian state-sponsored group Midnight Blizzard did when it breached Microsoft this year. If misconfigurations can happen at Microsoft, it's worth reviewing to make sure that your applications are all secure.
.png)
.png)
We've partnered with GuidePoint Security, the leading cybersecurity solution provider that helps organizations make better decisions that minimize risk. Through this partnership, GuidePoint Security's customers have the opportunity to expand their use of SaaS applications while staying secure.
As part of the Security Partner Program, Adaptive Shield’s SaaS Security Posture Management (SSPM) and Identity Threat Detection and Response (ITDR) solution is available through GuidePoint Security to address the risks associated with the usage of SaaS applications.
“Just like Cloud Security Posture Management (CSPM) is a necessity for cloud infrastructures, SSPM has now become the solution for every organization to implement to prevent and detect threats within SaaS environments,” said Maor Bin, CEO and co-founder of Adaptive Shield. “We look forward to working with GuidePoint Security, a leader in cybersecurity strategy, as Adaptive Shield continues its global expansion to fulfill the growing demand for comprehensive SaaS security.”
“Cyber-attack vectors are expanding across SaaS applications, challenging organizations’ security efforts with a new level of complexity,” said Justin Iwaniszyn, Director, New & Emerging Alliances, GuidePoint Security. “As threat actors become increasingly sophisticated, it's crucial for organizations to adopt comprehensive SaaS security strategies that effectively mitigate risk across their entire SaaS ecosystem."
Supporting a portfolio of 150 out-of-the-box SaaS integrations with leading business-critical applications, Adaptive Shield enables organizations to control and manage the security of their entire SaaS stack. Adaptive Shield’s capabilities include:
Originally announced on businesswire.com: https://www.businesswire.com/news/home/20240305787393/en/


Oftentimes, there is a disconnect between identifying SaaS Security weak spots and remediation. Your SaaS Security Posture Management (SSPM) platform may have detected that MFA is turned off for admins, or a threat that requires immediate intervention by either the security team or the app owners.
Security Orchestration, Automation, and Response (SOAR) and Security Information & Event Management (SIEM) tools are the heavy lifters in the world of cybersecurity remediation. They are given marching orders from a number of different security tools, and then they implement them within the applications with which they are integrated.
SOARs and SIEMs are specialists in workflow automation. They automate routine tasks, so security team members can focus their efforts on more complex tasks. They also respond to threats before they can harm business operations. As a centralized platform, SOARs and SIEMs can help coordinate any type of incident response across different teams.
SSPM, or SaaS Security Posture Management, is a comprehensive cloud security solution designed to assess, monitor, and enhance the security posture of Software as a Service (SaaS) applications. It offers organizations real-time visibility into their SaaS environments, helping them proactively identify and mitigate security risks to ensure a robust and resilient cloud infrastructure.
SSPMs and SOARs are an ideal security combination. SSPMs find security misconfigurations and identify high-risk elements within the SaaS stack. However, they are rarely designed to remediate issues.
Automating this portion of SaaS security is essential. A recent Adaptive Shield report found large organizations have over 10,000 high-risk third-party apps connected to their core stack. Combine that with thousands of user accounts, tens of thousands of configurations, and thousands of resources that must be securely stored within the SaaS stack, and it’s evident why manual remediation approaches are a partial solution at best.
SOAR-driven automated remediation is essential to limiting risks and handling threats. In the world of securing SaaS apps from threats, that means providing the SOAR with detailed SaaS risks and mediation directions.
Organizations are leveraging SOAR for efficient incident response. Those tools are being powered by pre-written playbooks from SSPM platforms, which engage the SOAR and share workflows for Torq, Cortex Demisto, Chronicle, and others. Combining SSPM with SOAR automates remediation, and enables small security teams to secure large swaths of their SaaS stack.
There is no shortage of use cases driving SSPM and SOAR to work together.
Every organization can set its own policy for deprovisioning users, and in most cases, it can be adapted based on the application. Application configurations can be set to issue an alert once users have passed the dormant-user threshold. The SSPM passes the data to a SOAR, which accesses the application and removes privileges or shuts down the account for dormant users.
For a better understanding, see our example covering automated offboarding using Adaptive Shield’s integration with Torq.
When a SaaS app’s Identity Threat Detection and Response (ITDR) mechanism finds a user behaving anomalously in a way that could compromise the application or its data, it can use SOAR to respond. Users who are downloading an uncharacteristic volume of data can trigger a playbook that immediately disables the user account.
Collaboration is one of the core tenets of SaaS applications, so it is fitting that it takes SSPMs and SOARs to work together to secure applications. SSPMs monitor the attack surface, and scan for any vulnerabilities that could harm the SaaS stack. Once alerted to an issue, SOARs remediate the issue, enabling security teams to quickly handle problems that might have taken days to fully close if done manually.


In recent weeks, a concerning wave of cyber attacks has been targeting Microsoft Azure environments, compromising crucial user accounts, including those of senior executives. Proofpoint researchers have identified an ongoing malicious campaign, which utilizes sophisticated techniques like credential phishing and cloud account takeover (ATO).
This blog post will summarize and shed light on the nature of this attack. It will delve into some configurations that could mitigate the attack, and advise on activities to monitor within Azure to help organizations safeguard themselves.
The campaign, which started in late November 2023, employs credential phishing and cloud account takeover techniques. Threat actors use individualized phishing lures in shared documents, leading users to malicious websites. The targets vary across organizations, impacting individuals in different roles, including sales directors, account managers, and high-ranking executives.
Specific indicators of compromise (IOCs) include a Linux user-agent used during the access phase, primarily accessing Office365 applications. Full information on the IOCs can be found in the Proofpoint Community Alert.
Once compromised, attackers engage in MFA manipulation, data exfiltration, internal and external phishing, financial fraud, and mailbox rule creation to cover their tracks. The attackers' operational infrastructure involves proxies, data hosting services, and hijacked domains, with the use of proxy services to mask their location. Notably, non-proxy sources like Russia-based Selena Telecom LLC and Nigerian providers Airtel Networks Limited and MTN Nigeria Communication Limited may be involved.
While the campaign hasn't been attributed to a specific threat actor, Russian and Nigerian involvement is suggested based on previous cloud attacks.
In the ever-changing landscape of cybersecurity, hardening a SaaS environment and implementing robust threat detection capabilities are complementary strategies. They work together to create a resilient defense, reducing the attack surface, preventing vulnerabilities, and swiftly responding to emerging threats. Ultimately, they safeguard an organization's digital assets and ensure the confidentiality, integrity, and availability of sensitive information. In the next sections, we will show how to harden Microsoft Azure environments while implementing threat detection capabilities.
There are many legitimate uses of user-sent mail forwarding rules and addresses. However, as seen in these attacks it can lead to data leakage. Microsoft’s forwarding controls are complex and located in multiple places, including user and admin levels. It is important to review these settings and harden them.
Simultaneous activity from two different origins – Unless the attacker is sitting at a desk next to the compromised user, activity will be registered within the account from the compromised user and the attacker from different locations.
User appears from an unusual IP – A smart attacker can try to operate in hours when the compromised user is inactive to avoid simultaneous activity from two different origins. In such a case, it is important to monitor activity coming from an unusual IP.
User appears with an unusual device – Similar to an unusual IP, an unusual device can indicate a potential attack. In these attacks, Proofpoint noted that a Linux user-agent was used, which is a clear example of an unusual behavior.
User registered an authentication method from an unusual IP – Sometimes users change devices, go on vacation, and do other unusual things that may be legitimate from an unusual IP. However, changing an authentication method from an unusual IP is a red flag.
Brute force & password spray – These traditional attack vectors were not mentioned as used in this specific attack. Yet, these should always be mentioned and monitored while securing against an account takeover attack.
Downloads – Such as massive downloads from unusual IPs, or just uncharacteristic massive downloads.
Mailbox forwarding rules - Since massive downloads are frequently flagged, attackers are trying to find more elegant methods for data exfiltration. These include setting up mailbox forwarding rules that automatically forward every email from the victim to the attacker's email account. These are especially suspicious when coming from an unusual IP, or to an untrusted domain.
As the cyber threat landscape evolves, it becomes imperative for organizations to fortify their defenses against sophisticated attacks like the one dissected in this blog post. The malicious campaign targeting Microsoft Azure environments underscores the pressing need for comprehensive security measures.
Implementing a SSPM solution is paramount to hardening the Azure environment, with a focus on mitigating risks associated with credential phishing, cloud account takeover, and data exfiltration. Additionally, the significance of an ITDR solution cannot be overstated, especially when it comes to timely detection and response to account takeovers, unusual activities, and potential data breaches.
The insights provided in this blog post serve as a guide for organizations to bolster their security posture, emphasizing the symbiotic relationship between SSPM solutions and ITDR capabilities for a holistic SaaS security platform. By adopting these strategies, organizations can proactively safeguard their digital assets, ensuring resilience in the face of evolving cyber threats and maintaining the confidentiality, integrity, and availability of sensitive information.


Recent incidents continue to shed light on vulnerabilities that organizations face. A notable case involves a networking products company whose support website inadvertently exposed sensitive customer information, as reported by KrebsOnSecurity. This incident underscores the critical importance of robust security measures in safeguarding customer data. In this blog post, we'll delve into the details of the exposure, explore potential causes, and discuss actionable items to enhance security in Salesforce.
In this case, the support website that experiences a data exposure and was utilized by the networking products company was Salesforce. This lapse allowed unintended access to customer information, including device details, warranty status, and serial numbers. Discovered by a 17-year-old intern named Logan George, the incident highlights the potential risks associated with inadvertent data exposure.
Upon discovering the issue, the networking products company swiftly addressed the problem, emphasizing that the exposure resulted from a recent upgrade to its support portal. The company assured users that it has fixed the issue and currently has no reason to believe that any identifiable or personal customer data was compromised.
The company has not provided specific details on when the user rights issue was introduced. This raises concerns about the adequacy of user permissions within Salesforce assets, echoing a broader issue of misconfigurations that can lead to data exposure. This is the second time in less than a year that a Salesforce misconfiguration exposes sensitive information (that we know of).
In the wake of this incident, it is essential for businesses, particularly those dependent on platforms like Salesforce, to adopt strong security protocols. Here are key security principles crucial for safeguarding Salesforce. These security recommendations hold significance even in the absence of specific insights into the factors contributing to this particular data breach.
Salesforce Communities (“Experience”) refers to a feature within the Salesforce platform that allows organizations to create branded, customizable communities for collaboration and engagement with customers, partners, and employees in a secure and personalized online environment. Salesforce Communities often involve the sharing of sensitive data such as customer information, partner details, or internal communications. Proper security measures help safeguard this data from unauthorized access or breaches.
Salesforce Communities allow a high degree of customization. Therefore it's important to ensure that objects, files, records, and configurations follow best practices to minimize vulnerabilities. Regularly review and update security settings to adapt to evolving threats. Emphasis should be put on configurations that allow access and visibility to all users or guests.
In Salesforce, an object is a fundamental data structure used to store and organize information. Objects in Salesforce are akin to database tables and are central to the platform's data model. Salesforce provides a variety of standard objects, and users can also create custom objects to meet specific business requirements. Objects are made up of fields, which define the types of data that can be stored in them. Salesforce provides robust security features that allow administrators to control access to objects, fields, and records. This ensures that users have appropriate permissions to view, edit, or delete data. Objects should be reviewed constantly in order to make sure they are not exposed to unauthorized access. Also, make sure that they are not publicly accessible. Validate who has access to what object and how such access was given (such as Profile or Permission set).
Implementing robust authentication mechanisms ensures that only authorized users have access to the community. This involves using secure login methods and controlling user access based on their roles and permissions within the organization. Setting up strong password policies, requiring MFA, and using SSO is a good start. Complement good login methods with strong control on access to data with visibility into Profiles and Permission Sets making sure there is no permission sprawl and that all user access is only to “need to know”. Finally, implement monitoring tools and conduct regular audits to track user activities, identify potential security incidents, and ensure compliance with security policies.
The recent incident involving the networking products company's support website serves as a reminder of the ongoing challenges in managing large systems and the importance of robust cybersecurity measures. By implementing the suggested actionable items, organizations can fortify their defenses against potential data exposure risks, ensuring a safer digital environment for both the company and its customers.
Click here to read more about Salesforce’s Top Use Cases
.png)
.png)
A major player in the US telecommunications industry, with over 117,000 employees, recently experienced an insider data breach that has impacted nearly half of its workforce. The breach, discovered on December 12, 2023, occurred on September 21, 2023, when an unauthorized employee accessed a file containing sensitive information of over 63,000 employees.
The exposed data includes full names, physical addresses, Social Security numbers, national IDs, gender, union affiliations, date of birth, and compensation information. Fortunately, customer information remains unaffected.
The US telecommunications giant, in response to the breach, has emphasized its commitment to enhancing internal security measures. While there is currently no evidence of malicious exploitation or widespread data leaks, the company is taking proactive steps to prevent future incidents.
Sensitive employee data resides in Human Resources Information Systems (HRIS) and Applicant Tracking Systems (ATS), with Workday being a notable example. Sensitive records stored within these systems include:
As HR departments adopt more SaaS-based HRIS and ATS systems, they must take measures to prevent the cybersecurity risks associated with storing sensitive data on a cloud-based service. This is why HRIS and ATS systems based on SaaS became a prime target for threat actors. The Telecom incident underscores the urgency for organizations to fortify the security of these platforms.
In addition to the points addressed in the original breach article, it is important to understand the complexity of permission structures within their HR platforms and how they impact access control.
Organizations must invest time and resources to fully understand the permissions granted within their HR platforms. This includes not only knowing which employees have access to sensitive data but also understanding the specific actions they can perform with that data, for example read, modify, delete, etc. A lack of clarity in permission structures can lead to inadvertent exposure of sensitive information and increase the risk of insider threats. HR systems can have a very complex system composed of Security groups, Domains (within a Functional Area for example), Organizations, Roles, criterias, and more which interact with each other and add complexity that can create a security issue. Moreover, the importance of visibility into who has permission to what and through which controls cannot be overstated.
Continuous monitoring against insider threats is essential. Organizations should implement systems that provide real-time insights into user activities within HRIS. This includes monitoring for unusual behavior patterns such as excessive downloads, granting access to an external user (maybe their private email) and any deviations from normal usage patterns.
Continuous monitoring is not a one-time effort but an ongoing process. Regularly reviewing access logs, conducting periodic audits, and leveraging advanced analytics to detect anomalies are vital components of a comprehensive security strategy. This proactive approach allows organizations to identify and address potential security issues before they escalate into major breaches. An example of such a serious security issue is a threat actor changing the bank account details of an employee so that their payroll is redirected to the hacker's account. This example emphasizes the importance of safeguarding HRIS systems.

The recent data breach at the US telecommunications giant highlights the vulnerability of even major corporations to insider threats. By learning from such incidents, organizations can take proactive steps to secure their HR platforms, implement continuous discovery mechanisms, fortify their overall cybersecurity posture, and ensure a comprehensive understanding of complex permission structures. Constant adaptation and improvement are essential in the ever-changing landscape of cybersecurity.


Media firms in the business of image and reputation don’t want to get bad publicity. With regulations requiring companies to report data breaches, information companies handling personal data must take extra cybersecurity caution.
Take for example the case study of a European-headquartered global media and information services company with an annual revenue of over $10 billion. The growing adoption of cloud-based SaaS collaboration tools was making it a challenge for security teams to stay on top of emerging data leakage threats.
More of the organization’s sensitive and valuable data was moving to the cloud with business-critical SaaS applications being used across teams and departments. The firm was also acquiring small enterprises. Every acquisition increased the number of applications and geographically distributed SaaS tenants added even more complexity.
After discovering a series of internal data breach incidents involving data stored in SaaS applications, the company decided to look for an automated SaaS security posture management solution that would enable its security team to monitor and manage risk in its SaaS stack, efficiently and effectively.
The firm evaluated multiple SaaS Security Posture Management (SSPM) solution vendors, choosing the Adaptive Shield solution considering among other things that it supported the industry’s widest portfolio of SaaS applications.
Forrester Consulting conducted a Total Economic Impact™ (TEI) study commissioned by Adaptive Shield to assess the ROI and benefits of the organization’s SSPM investment. In the cost-benefit analysis, the company achieved benefits worth $2.18 million over three years with a 201% ROI, and a return on investment in less than six months.
The study, as follows, covers the customer journey, starting from the SaaS challenge to the successful implementation of an SSPM solution.
Before the adoption of Adaptive Shield’s SSPM, the case study found that the media company’s security team lacked the necessary knowledge and skills to identify and mitigate risk in the controls and settings of SaaS applications. Since the security team had limited familiarity with each application, they could not oversee each application’s configuration. As a result, they could not ask the business unit application owners the right security configuration questions. On the other hand, with their newfound SaaS independence, app owners with “the keys to the kingdom” were reluctant to participate in new initiatives brought by the security team. Moreover, they were neither educated nor equipped enough to exercise security.
“We started seeing some small incidents resulting from SaaS misconfiguration, so we needed to do something about it… [It] was a wake-up call for us that we really need to look at all the configurations at scale,” the chief security officer of the company said in an interview with Forrester for the study.
So clearly the traditional manual approach to managing SaaS security was failing, leading the firm to search for an automated solution that could provide visibility and control into its SaaS applications throughout the organization.
During the SSPM acquisition and rollout process, the company experienced a quick and significant improvement in its SaaS security posture score.
An immediate benefit was the quick reduction in the number of data breach incidents. Before implementing SSPM the firm had experienced six incidents in a year. With the launch of the solution, the number began to decline rapidly, going down to 3 in the second year, and projected to be one or less by the third year.
Before implementing Adaptive Shield, the company’s SaaS security posture score was 40%. During the proof-of-concept (POC) phase, the security team found issues in their SaaS configurations and fixed them.
“When we look at the security score trends, we observed a significant increase over time,” the CSO said.
The score improved rapidly to 70% in the first year, 85% in the second year, and was on track to reach 95% after three years. The total projected improvement in the overall score was 55%.
The substantial improvement in the overall security posture score was attributed to SSPM capabilities to deliver visibility, remediation guidance, and ongoing monitoring.
A major contribution to overall security posture was improvement in misconfiguration detection efficiency. Automating the traditional manual approach to SaaS configuration management and remediation improved the efficiency of the process. The combined effort by the security and business teams spent on configurations for each application’s traditional annual risk assessment was reduced by 70 percent, from 100 hours to 30 hours per application.
By deploying Adaptive Shield, the organization was also able to significantly expand the number of monitored applications over three years from 20 to 60.
An additional benefit was a savings of 90% in labor efforts in managing the firm’s compliance goals and priorities. Before the adoption of Adaptive Shield, the security team spent 2400 hours a year implementing compliance rules, with the time spent decreasing to 240 per year, for a 90% savings.
The study also found the SSPM opened conversations between security and business owners, enhancing collaboration and trust between business and security teams that saved company time.
In addition to quantifiable improvements, the company was interested in understanding the qualitative results of its investment in SSPM.
The study found that the solution helped the organization overcome the overall challenges introduced by the democratization of SaaS security and secure SaaS data. It enabled it to maintain a holistic view of SaaS-related inventory.
The security team gained a powerful tool to manage the inventory of SaaS applications, connected applications, users, and user devices, and track the status of SaaS subscriptions.
SSPM helped the organization achieve continuous compliance, avoiding any interruptions to business operations, and staying ahead of any SaaS security trends.
The Adaptive Shield solution also detected suspicious activities from new devices and new IP addresses.
The frequency of SaaS attacks is only growing and SaaS incidents are continuously exposing organizations to data leaks, breaches, compliance failures, and other potential disruptions in business operations.
This case study demonstrates how Adaptive Shield helped a media organization improve SaaS security and streamline security operations.
This article was originally published in Cyber Defense News.
To learn more about the study and 2024 SaaS security trends, join the webinar with CISO and renowned cybersecurity advocate, Matthew Rosenquist, and Adaptive Shield CEO & Co-founder, Maor Bin. February 20th, 2024 at 2pm EST. Register Now



Adaptive Shield is honored to announce that Frost & Sullivan recently assessed the Software-as-a-Service (SaaS) security posture management (SSPM) industry and based on its findings, recognizes Adaptive Shield with the 2023 Global Technology Innovation Leadership Award.
Ying Ting Neoh, research analyst for cybersecurity practice at Frost & Sullivan, said: “With continual enhancements to its SSPM technology offering to address customers’ pain points in the SaaS security space, the company is well-positioned as a technology innovation leader in the SSPM market.”
“Adaptive Shield has established a strong reputation and a steadily growing position in the global SSPM market. It is well positioned for continued growth, with its visionary and innovative platform for SaaS Security coupled with its established strategic partnerships and technology alliances,” added Neoh.
In the award, Frost & Sullivan states that Adaptive Shield offers an SSPM solution that helps customers secure their entire SaaS stack through risk management, threat prevention, and detection and response. Adaptive Shield’s SSPM platform provides a suite of capabilities with single-pane-of-glass visibility, such as:
In addition, Adaptive Shield’s SSPM platform expanded to enable over 140 out-of-the-box integrations of SaaS applications, making it the first and only SSPM solution provider with such a large number of out-of-the-box integrations. Its comprehensive security coverage of potential threats enhances visibility, security control, and application integration.
The SSPM platform also allows customers to easily manage sanctioned and unsanctioned applications connected to their core SaaS stack, regardless of the number of applications, thus minimizing the risk of SaaS-to-SaaS or third-party application access. This capability enables customers’ security teams to measure the access level to sensitive data across organizations’ SaaS stack while having advanced reporting capabilities that complement their risk assessments.
For its strong overall performance, Adaptive Shield was recognized with Frost & Sullivan’s 2023 Global Technology Innovation Leadership Award in the SaaS security posture management industry.
“Receiving Frost & Sullivan’s 2023 Global Technology Leadership Award in SaaS Security Posture Management is not just an accolade for Adaptive Shield, it’s a testament to our commitment in transforming the landscape of SaaS security,” said Maor Bin, CEO and co-founder of Adaptive Shield. “This recognition fuels our passion to not only protect, but empower businesses through revolutionizing the way they perceive and manage their SaaS security challenges.”
Each year, Frost & Sullivan presents this award to the company that has developed a product with innovative features and functionality that is gaining rapid acceptance in the market. The award recognizes the quality of the solution and the customer value enhancements it enables.
Frost & Sullivan Best Practices awards recognize companies in various regional and global markets for demonstrating outstanding achievement and superior performance in leadership, technological innovation, customer service and strategic product development. Industry analysts compare market participants and measure performance through in-depth interviews, analyses and extensive secondary research to identify best practices in the industry.


AT&T Cybersecurity recently discovered phishing attacks conducted over Microsoft Teams. During a group chat, threat actors distributed malicious attachments to employees, which led to the installation of DarkGate malware on the victim’s systems.
This attack shines a bright light on the everchanging phishing surface as it expands from email to communication applications like Teams. This blog post will shed light on the attack, draw parallels between a previously identified vulnerability, and provide actionable remediation steps to fortify your organization against threats of this nature.
Inside the Attack
The attackers leveraged Microsoft Teams to send over 1,000 group chat invites. Once targets accepted the invitation, they were manipulated into downloading a file containing DarkGate malware.
This attack vector exploits the default settings in Microsoft Teams, which allows external users to message other tenants’ users. The scale of this threat is significant, as Microsoft Teams’ massive user base is an attractive target for cybercriminals.
In light of previously identified vulnerabilities and misconfigurations in Microsoft Teams, it is evident that the platform is susceptible to multiple attack vectors. One previous vulnerability involved an insecure direct object reference (IDOR), which allowed threat actors to bypass file-sharing restrictions and deliver malware directly to a target’s Teams inbox. Understanding the interconnected nature of these vulnerabilities is crucial when crafting a comprehensive security strategy.
Remediation
This vulnerability affects all organizations using Microsoft Teams in its default configuration. The following measures prevent threat actors from bypassing traditional payload delivery security controls, and mitigate the risk. These measures also help prevent the GIFShell vulnerability and the IDOR vulnerability found by Max Corbridge and Tom Ellson from JUMPSEC's Red Team.
To fortify your organization against these phishing attacks and vulnerabilities, Adaptive Shield’s security research team recommends implementing the following remediation measures:
1. Review External Access
Assess the need for external tenants to message members of your organization. If it is not essential, disable external access in the Microsoft Teams Admins Center. Set the “Choose which external domains your users have access to” configuration to “Block all external domains.
If external communication through Teams is required, enable access only for specific domains that regularly interact with users through Teams, to strike a balance between the organization’s communication needs and its security.
2. Block Invitations of External Users to Shared Channels
Shared Channel owners have the ability to invite external users to join their channel. This allows external users to read and write messages. In the Microsoft Teams Admin Center, under teams policy, toggle “Invite external users to shared channels” to off.

Figure 1: Microsoft Teams’ Teams Policy Configurations
3. Limit Conversation Starters
Prevent unmanaged external Teams users from initiating conversations within your organization. In the Microsoft Teams External Access configurations, disable "External users with Teams accounts not managed by an organization can contact users in my organization." By limiting who can start conversations, you reduce the likelihood of unauthorized access and communication.

Figure 2: Microsoft Teams External Access Configurations
4. Use Defender for Teams
Organizations that use Microsoft Defender for Office 365 can activate the Safe Attachments for Office 365 in the global settings to prevent users from inadvertently sharing malicious files in OneDrive and SharePoint+OneDrive. Once activated, Safe Attachments prevent users from opening or downloading files that are identified as malicious.

Figure 3: Microsoft Defender detects malware files
5. Educate Staff
Raise awareness among staff about social engineering campaigns that use productivity apps like Microsoft Teams. Emphasize that phishing attacks can take various forms beyond traditional emails. Encourage a security-conscious mindset and provide ongoing training so employees recognize and report suspicious activities.
Conclusion
As the threat landscape continues to evolve, organizations must stay proactive in securing their communication SaaS platforms. By learning from recent phishing attacks and vulnerabilities, you can bolster your defenses against cyber threats. Implementing the recommended remediation measures will contribute to a more secure Microsoft Teams environment, safeguarding your organization and its sensitive data from malicious actors. Stay informed, stay vigilant, and prioritize SaaS security to ensure the resilience of your SaaS data.


In a recent cybersecurity event reported by Lawrence Abrams in Bleeping Computer and disclosed by the Microsoft Security Response Center, Microsoft found itself at the center of a cyber-attack. Nobelium, a Russian state-sponsored hacking group also known as APT29 and Midnight Blizzard, breached Microsoft corporate email accounts for over a month. The attack, which was discovered on January 12, underscores the need for enhanced cybersecurity measures, even for industry giants like Microsoft.
Microsoft disclosed that the breach was initiated in November 2023 when threat actors, identified as Nobelium, executed a password spray attack to compromise a legacy non-production “test” tenant account. A password spray attack involves attempting unauthorized access to multiple accounts by systematically testing a list of potential login names and passwords. Nobelium parlayed their access into the test account to access a small portion of Microsoft’s corporate email accounts for over a month, including those belonging to at least one member of their leadership team.
At this time, more detailed information on the breach is being withheld by Microsoft. However, the following suggestions are basic security recommendations based on the disclosed information.
The breach highlights the critical importance of implementing multi-factor authentication (MFA) as a primary defense against unauthorized access. By adding an extra layer of security beyond passwords, MFA can thwart unauthorized access attempts, providing a robust defense against password spray attacks.
Single Sign-On (SSO) integration minimizes the attack surface, reducing potential points of compromise. Widely adopting and enforcing SSO could significantly enhance security posture, preventing unauthorized access to critical systems.
The compromise was initiated through a “test” account, and should serve as a reminder for the need to conduct regular audits that identify and deactivate unused accounts. Adopting the Principle of Least Privilege (POLP) is crucial to prevent unauthorized access.
The breach highlights the potential risks associated with underestimating the security of test accounts. Organizations should apply the same level of security diligence to test accounts and sandboxes as they do to production accounts to avoid exploitation by threat actors.
Continuous monitoring of identity activity is crucial for detecting anomalous behavior indicative of a security breach. Implementing advanced identity and access management solutions together with identity threat detection solutions allows organizations to swiftly identify and respond to unauthorized access attempts.
Microsoft emphasizes that the breach was not caused by vulnerabilities in their products or services but resulted from a brute force password attack on compromised accounts. While investigations are ongoing, Microsoft assures that the breach has not materially impacted its operations. This incident serves as a stark reminder that even tech giants must remain vigilant against evolving cyber threats.
As Microsoft continues to share additional details about the breach, it should prompt organizations worldwide to reassess and reinforce their cybersecurity protocols. We will continue to monitor this story, and update our recommendations as needed. However, the steps recommended here should be adopted by every organization that is serious about minimizing the risk of a similar attack.


Today, we released that one of our customers achieved a 201% return on investment (ROI) in less than six months from adopting a SaaS Security Posture Management (SSPM) solution, according to results of a Forrester Consulting Total Economic Impact™ (TEI) study.
The 2024 Forrester Consulting TEI study is based on data from the customer experience of a global corporation with an annual revenue of over $10 Billion USD. The organization is undergoing rapid SaaS adoption across business-critical applications and has adopted Adaptive Shield’s SSPM platform in order to control and manage the security of their entire SaaS ecosystem.
The model Forrester designed to determine this ROI includes elements of SaaS Security score, operational efficiency against costs of a data breach like lost employee productivity, lawsuits and settlements, and regulatory fines.
“We started seeing some small incidents resulting from SaaS misconfiguration, so we needed to do something about it… The incident was a wake-up call for us that we really need to look at all the configurations at scale,” asserts the Chief Security Officer (CSO) of the $10 billion global media and information services corporation interviewed for the TEI.
After they brought on Adaptive Shield, the CSO shares, “When we look at the security score trends, we observed significant increase over time. In reality, the improvement is even greater because we have already fixed some issues during the POC (proof of concept).”
The financial analysis of the implementation of Adaptive Shield platform with this customer found benefits of $2.18 million over three years. The payback period on the original investment was less than six months. Results from utilizing Adaptive Shield included more efficient SaaS Security management with improved visibility for stakeholders, enhanced security compliance control, and increased collaboration between business and security teams.
“There is a common misconception that SaaS providers take care of the security of the organizations’ apps. While SaaS vendors invest a lot in their security, the market has now come to realize that it’s the organization’s ultimate responsibility to ensure that their apps’ security posture is monitored and managed internally. Similar to the case of IaaS and CSPM tools, ” says Maor Bin, CEO and co-founder of Adaptive Shield.
“With the frequency of SaaS attacks only growing and SaaS incidents continuously exposing organizations to data leaks, breaches, compliance failures, and other potential disruptions in business operations, SSPM is the only way for organizations to secure SaaS data. Beyond the qualitative, this TEI study quantitatively presents just how much Adaptive Shield helped improve our customer’s SaaS security and streamline business costs.”
Key benefits found in the study:
.webp)
.webp)
SaaS Security’s roots are in configuration management. An astounding 35% of all security breaches begin with security settings that were misconfigured. In the past 3 years, the initial access vectors to SaaS data have widened beyond misconfiguration management. “SaaS Security on Tap” is a new video series that takes place in Eliana V’s bar making sure that the only thing that leaks is beer (maximum), and not SaaS data. This series takes a look at the key concepts within SaaS security and educates organizations on what new threat vectors need to be addressed.
With the increase in SaaS application use, it’s no surprise that incidents are up. The SaaS Security on Tap series covers this year’s SaaS Security report which found that 55% of organizations have experienced a SaaS security incident within the last two years, including data leaks, data breaches, ransomware attacks, and malicious applications.
The report was not all doom and gloom. As Eliana V points out, companies are recognizing that manual audits and CASB deployments are only partial solutions at best. A surprising 80% of companies are either using or planning on using a SaaS Security Posture Management (SSPM) tool, like Adaptive Shield, for automated configuration and SaaS security monitoring by September 2024. That should take SaaS applications to a far more secure place than they are today.
SaaS Security on Tap reveals that as more organizations adopt SSPM, they are enhancing their visibility into SaaS app users. SaaS experts have come to recognize the critical nature of identity and access governance in securing SaaS apps. While much of SaaS security falls under the control of app owners, responsibility for identity and access governance falls squarely within the responsibility of the security and central IT team. They manage the company’s Identity Provider (IdP) and need visibility to see which users are accessing applications, the level of access they have, and the type of users they are.
Identity security is all about ensuring that identity and access tools and policies are in place. Security teams need a high degree of visibility to know which users, including external users, have access to each application and to what extent. To fully quantify the risk emanating from users, they also need visibility into the devices used to access those applications and the ability to monitor high-privilege users.
Third-party application integrations, also known as SaaS-to-SaaS access, have also developed into a serious attack vector. These applications, which are integrated through OAuth protocols with the click of a button, improve workflows and help businesses get more out of their applications. While many of these SaaS-to-SaaS applications are harmless, they pose a significant risk. 3rd-party apps often ask for intrusive permission scopes, like Eliana V quips in the On Tap video (below), “some scopes ask for your firstborn child.”
Users are granting permissions that allow read/write access, the ability to send email as a user, and most concerning, the ability to delete entire folders and drives of data. Eliana V points out that researchers found organizations with 10,000 SaaS users averaged over 6,700 applications connected to their Google Workspace, of which 89% requested medium- or high-risk permission scopes.
SaaS Security on Tap provides a fast-paced, entertaining look at the challenges and solutions organizations face as they try to secure their data in SaaS apps.
Hosted by Eliana V from the SaaS Security On Tap bar, the series gets inside the issues facing security teams and their application-owner partners. Take misconfiguration management. Using entertaining analogies and powerful examples, Eliana V demonstrates the dangers of misconfigurations and the ease with which organizations err with their settings.
Check out the trailer…and like and subscribe if you want more.
Don’t miss an episode of SaaS Security On Tap, the entertaining new video series that gets to the heart of SaaS security.


As we near the end of 2023, it's an opportune moment to assess your roster of SaaS users. Beyond the potential cost savings from eliminating unnecessary license fees, maintaining a well-organized user inventory plays a crucial role in fortifying the security of your SaaS applications. Here are five compelling security reasons to clean your user list.
When employees leave a company, they set a sequence of backend system adjustments in motion. The initial step involves their removal from the company's identity provider (IdP), initiating an automated process that deactivates their email and revokes access to all internal systems. Enterprises that utilize Single Sign-On (SSO automatically revoke access to various online properties, including SaaS applications.
However, deprovisioning from SaaS applications isn't automatic. Enterprises must manually deactivate or delete users from non-SSO-connected apps and SSO apps that also have local access. This is especially critical for high-privilege users, who often have local access even if the app is typically accessed through an SSO.
Ensuring the complete deprovisioning of users is critical. With the typical end-of-year slowdown, now presents an opportune time to reassess user roles and remove access for individuals who no longer need it.
User permissions dictate the extent of access granted to each employee within an application. Administrative permissions, typically granted to team leaders, enable tasks such as adding new users and overseeing application usage. Employees may require read/write permissions for their roles, while support personnel might only need read permissions or the ability to download reports.
Overpermissioning poses a security risk by unnecessarily expanding the attack surface. In the event of a compromised user account, the threat actor gains access equivalent to the compromised user. As the year concludes, it's prudent to review user permissions, aligning them with respective roles. Implementing the principle of least privilege (POLP) ensures employees have precisely the access needed for their tasks. For applications with group functionality, grouping like-users with preset permissions helps standardize access, while in other apps, a thorough review allows trimming access to essential functionalities.
Dormant accounts, which are unused SaaS accounts, fall into three primary types: admin accounts utilized during the application's initial setup with broad privileges, internal accounts belonging to employees who no longer require or use the application based on their roles, and external user accounts that remain inactive.
The risks associated with dormant accounts are substantial. Admin accounts shared among multiple users typically have easily guessable usernames and passwords, coupled with local access, which can create an environment prone to abuse. Unused employee accounts pose a risk in the aftermath of a phishing attack, potentially providing access to threat actors who exploit employees who are unaware of their retained access. Additionally, the lack of visibility into external user activity raises concerns about the security of the user account.
As enterprises navigate the holiday season, it is advisable to scrutinize dormant accounts and proactively assess their risk. When warranted, these accounts should be disabled or canceled to mitigate potential security threats.
Using a shared username to cut down on license fees introduces a heightened security risk. Shared accounts become challenging to secure as the number of users who know the access credentials expands with team changes. Moreover, opting for a shared login negates the use of critical security tools like Multi-Factor Authentication (MFA) and Single Sign-On (SSO), leaving the SaaS application more vulnerable.
The difficulties in detecting threats arising from shared accounts compound the security challenge. Anomalies in account access are less likely to trigger alerts if the account is regularly accessed from various locations, making it harder to identify suspicious activity.
Identifying departments that use shared accounts is not easy. However, enterprises can implement preventive measures and detection strategies. Mandating MFA or SSO complicates account sharing, and security teams can leverage user behavior analytics, including monitoring IP address logins, to identify instances of shared usernames. Taking the time now to uncover and address shared accounts contributes to a more secure SaaS environment in the upcoming year and beyond.
Manually reviewing user rosters and comparing them to the IdP is remarkably tedious and can easily lead to mistakes. So is checking permissions, reviewing dormant accounts, and looking for signs of account sharing. Using a SaaS Security Posture Management (SSPM) platform like Adaptive Shield’s simplifies the process through automation.

Using SSPM’s user inventory, companies can quickly identify accounts that haven’t been used over a preset time period, find external users with high permission sets, and detect users who were removed from the IdP. SSPMs can also associate users with devices to further limit risk.
As you prepare for 2024, introducing an SSPM to monitor users is the most effective and efficient way to know who is accessing your SaaS stack.


Over the past few years, SaaS has developed into the backbone of corporate IT. Service businesses, such as medical practices, law firms, and financial services firms, are almost entirely SaaS based. Non-service businesses, including manufacturers and retailers, have about 70% of their software in the cloud.
These applications contain a wealth of data, from minimally sensitive general corporate information to highly sensitive intellectual property, customer records, and employee data. Threat actors have noted this shift, and are actively working to breach apps to access the data.
Here are the top trends influencing the state of SaaS Security for 2024 — and what you can do about it.
SaaS apps have transformed the way organizations purchase and use software. Business units purchase and onboard the SaaS tools that best fit their needs. While this is empowering for business units that have long been frustrated by delays in procuring and onboarding software, it does require organizations to rethink the way they secure data.
Security teams are being forced to develop new ways to secure company data. Lacking access and visibility into an application, they are placed in the role of advising a business unit that is using SaaS applications. To further complicate matters, every SaaS application has different settings and uses different terminology to describe security features. Security teams can't create a one-size-fits-all guidance document because of the differences between the apps.
Security teams must find new ways to collaborate with business units. They need a tool that offers visibility and guidance for each application setting so that they – and the business unit – understand the risks and ramifications involved in the configuration choices that they make.
If a threat actor gains access to a high-privilege account, they gain unfettered access within the application. Organizations are now understanding that identity is the de facto perimeter for their SaaS applications.
When threat actors take over an authorized user account, they typically follow common tactics, techniques and procedures (TTP) as they work their way through the app toward the data they want. They leave behind indicators of compromise (IoC), which might be based on actions taken within the app or logs.
As we move into the new year, we are going to see more organizations adopting an Identity Threat Detection & Response (ITDR) approach. ITDR mitigates that concern. As a key component in Identity Security Posture Management, ITDR capabilities can detect TTPs and IoCs, and then send an alert to the incident response team. Through ITDR, threat actors who have managed to breach the identity perimeter can still be stopped before they steal critical data or insert ransomware into the application.
Global companies are increasingly facing different regulatory requirements from one country to the next. As a result, 2024 will see an increase in the number of geo-specific tenants as part of the effort to keep data segmented in accordance with the different regulations.
This change will have a limited impact on software costs as most SaaS app pricing is based on subscribers rather than tenants. However, it will have a significant impact on security. Each tenant will need to be configured independently, and just because one instance of the application is secure doesn't mean that all tenants are secure.
To secure all these tenants, security teams should look for a security solution that allows them to set app benchmarks, compare tenants, and display security settings side-by-side without charging extra for each additional tenant. By applying best practices throughout the organization, companies can keep all their tenants secure.

A default misconfiguration in ServiceNow triggered widespread panic in October. The setting, which was part of the application's Access Control Lists, allowed unauthorized users to extract data from records. The misconfiguration impacted thousands of companies. A similar misconfiguration in Salesforce Community back in May also impacted a significant number of companies and led to data breaches.
Misconfigurations like these have the potential to cause major damage to companies. They lead to data leaks that break the trust between companies and their stakeholders, and have the potential to turn into onerous fines, depending on the nature of the data that leaked.
Securing misconfigurations is an organization's best chance at preventing these exploits from impacting their operations and hurting their bottom lines.
Third-party applications add real value for end users. They improve processes, extend functionality, and connect data between multiple applications. Users connect these SaaS apps with the click of button, and instantly begin improving their workflows.
In March 2023, Adaptive Shield released a report showing that organizations using Google Workplace with 10,000-20,000 users averaged 13,913 third-party apps connected to Google Workplace alone. An astonishing 89% of these requested either high- or medium-risk permissions. Many of these high-risk apps are used once and forgotten about, or used by a small number of employees. However, even these dormant or lightly used applications have significant permissions and can be used to compromise or breach a SaaS application.
The use of third-party applications is only increasing, as more apps are developed and employees use their own judgment – rather than checking with their security team – when integrating third-party applications into their stack. Security teams must develop visibility into all their integrated apps, and gain insights into the permissions requested, the value the app contributes to the organization, and the risk it poses.

In 2023, nearly 40% of all employees worked from home at least part of the time. According to WFHResearch, approximately 12% of employees work exclusively in their homes, while another 28% have hybrid roles.
These figures should give pause to security personnel concerned about users logging in to their work accounts from personal devices. One of the biggest concerns security teams have is when high-privileged users log into their accounts using an unmanaged or unsecured device. These devices may have critical vulnerabilities, and create a new attack vector. For many teams, there is almost no way to tell which devices are used to access the SaaS app or see whether those devices are secure.
While all these trends point to legitimate SaaS security concerns, SaaS Security Posture Management (SSPM) tools coupled with ITDR capabilities, like Adaptive Shield, can fully secure the SaaS stack. SSPMs are designed to automatically monitor configurations, looking for configuration drifts that weaken an app's posture. In SaaS Security Survey, 2024 Plans & Priorities by Cloud Security Association and Adaptive Shield, 71% of respondents said their company had increased their investment into SaaS security tools over the past year, and 80% were either already suing SSPM or planned to invest in one within the next 18 months.
SSPMs can provide baselining tools for multiple tenants of the same app, and enable users to establish best practices, compare settings from different instances, and improve the overall posture of the SaaS stack.
SSPMs also detect and monitor third-party applications, alerting users if their integrated apps are requesting too much access and updating the security team when integrated apps are dormant. It tracks users, and monitors the devices being used to access applications to prevent the use of unmanaged or unsecured devices on corporate SaaS apps. Furthermore, their built-in communication tools make it easy for business units to collaborate with security personnel in securing their applications.
SaaS apps have grown in popularity for good reason. They allow organizations to scale as needed, subscribe to the apps they need at the moment, and limit investment in some IT. With SSPM, these applications can be secured as well.


On Wednesday, December 13, MongoDB detected an exposure in their systems, and customer account metadata and contact information. MongoDB is currently conducting an investigation to determine the extent of the exposure. In an email sent out to customers, MongoDB CISO Lena Smart informed users that at present they were “not aware of any exposure to the data customers store in MongoDB Atlas.” Despite these assurances, customers using MongoDB Atlas, the SaaS service provided by MongoDB, may be concerned that their managed environment is at risk.
MongoDB is a widely used and versatile NoSQL database management system that provides a flexible, scalable, and high-performance solution for handling unstructured or semi-structured data. Known for its document-oriented architecture, MongoDB stores data in JSON-like BSON documents, allowing for dynamic schema design and easy scalability. It is favored by developers for its ability to handle large amounts of data and its support for complex queries, making it a popular choice for modern, data-intensive applications.
MongoDB has told The Hacker News that the incident is still under investigation, and it’s not known how threat actors entered into the platform. However, the company believes the unauthorized access has been going on for some time before discovery. This type of exposure, where the threat actor has access for an extended period of time, is an indicator of data theft.
Due to the exposed customer account metadata and contact information, MongoDB has advised that customers be vigilant for social engineering and phishing attacks. Threat actors often use this type of data in developing sophisticated attacks.
Furthermore, MongoDB encourages all Atlas customers to activate multi-factor authentication (MFA) and implement a password rotation policy.
Adaptive Shield automatically checks MFA configurations, as well as all security-related settings in Atlas, as part of its automated monitoring processes, and issues alerts if the application is at risk. If you aren’t using Adaptive Shield, our security experts recommend checking the following settings to secure your Atlas instance:
Enterprises that use Adaptive Shield’s SaaS Security Posture Management (SSPM) platform can easily gain visibility into MongoDB’s Atlas posture. Adaptive Shield has 15 security checks covering access control, MFA, key management, and other security domains. Adaptive Shield also discovers admin and local accounts, as well as consolidates multiple identities into a single user for contextualized visibility into users accessing applications to enhance MongoDB security.



The dynamic landscape of cybersecurity is witnessing a paradigm shift, with the SaaS Security Posture Management (SSPM) market emerging as a critical and pivotal player in safeguarding organizations against evolving cloud-based threats. As a clear must-have solution, Forrester has now brought to market their SSPM Wave, laying out their assertions and designating the top providers in the space.
Proud to be named a Strong Performer, Forrester’s Wave Report acknowledges Adaptive Shield’s capabilities and details each vendor’s current offering, strategy and market presence.
Within this blog post, I analyze the report, highlighting some of its findings and opening avenues for discussion. I believe Forrester’s vendor positioning might raise questions and this might be due to criteria such as proxy-based tech that is considered to be a pure CASB capability, cost saving features that are typically found in SMPs, heavy weighting of secondary criteria the same as primary SSPM capabilities, and due to the Innovation criteria that is measured solely based on the company size.
A core criteria for an SSPM solution, configuration drift detection is explained as the SaaS app owner or admin's functional, intuitive, and simplified ability to configure known good baselines, set up configuration drift notifications, view affected user lists post-configuration changes, and configure both vendor-supplied and client organization-specific risk score definitions, rules, and remediation steps.
Forrester recognizes that Adaptive Shield received the highest score possible in the Configuration Drift Detection criterion in that all recommended baseline configurations are available in the UI of the Security Checks feature. These configurations are mapped to best practices, frameworks, and compliance standards. The Adaptive Shield solution provides the ability to receive configuration drift notifications via multiple channels such as Slack, Teams, Emails, or any ticketing system of choice. The notification can be app-specific and drift-specific. The affected user list after a configuration change appears in the Security Check feature under the "Affected" tab and also under "Alerts".
In custom Security Checks the user of the platform can add/edit the score, rule and remediation plan manually. In out-of-the-box Security Checks, the user can change the risk score and other variables to match a custom logic.
Forrester explains SaaS App Configuration Templates to involve the customer SSPM administrator's functional, intuitive, and simplified ability to use and configure various compliance templates, customize vendor-supplied templates, cross-reference individual configuration artifacts with compliance templates, utilize natural language misconfiguration impact and remediation descriptions, and configure reports on findings and differences between templates and actual app configurations.
Forrester acknowledges that Adaptive Shield received the highest possible score in the SaaS app Configuration Templates. Adaptive Shield’s Security Checks are mapped to all the industry compliance frameworks (ISO 27000 series, SOC2, NIST CSF, CIS, etc.) — and are available out-of-the-box for users to benchmark against. The platform also provides its own frameworks and customers have the flexibility to customize them- whether by adding rules, dismissing checks or defining parameters. In addition, the Security Checks feature allows users to see the configuration deltas between the different Templates and AS-IS of both passed and failed checks. On top of these capabilities, the Landscape view presents the increase or decrease in posture score based on the recent changes.
The remediation guides are in English, descriptive and user-friendly, encouraging app owners to easily remediate. There is also a journal feature that enables users to communicate through the platform on each check. The “Posture Overtime” feature shows any change in configurations, gathering logs from the past 180 days.
Forrester defines IAM administration as involving the functional, intuitive, and user-friendly configuration of user graphs, inactive admin user detection, authentication monitoring, high-risk business user-centric views, and fine-grained user permission management in applications.
Adaptive Shield’s robust User Inventory received the highest possible score for a strong Identity Security Posture where each SaaS user has consolidated information on what SaaS app he has access to, permissions, roles, groups, and more. This also presents the failing user checks and how to remediate. In the Security Check feature, there are specific checks for access to sensitive data and settings in the system. There are out-of-the-box security checks that check for inactive admins. These can be changed to fit company policies within a preset or custom timeframe. This information is also available in the User Inventory via filters and custom security checks.
Scale, as defined by Forrester, is determined by the largest number of SaaS applications handled at a single, direct, in-production, paying customer organization as of June 30, 2023.
Adaptive Shield collaborates with hundreds of F1000 and Large Enterprises, our innovative tech and infrastructure enables us to support enterprises at scale and has been recognized as superior compared to other vendors.
Within a few of the criteria listed by Forrester, I had a few questions by either the criteria, the definition of the criteria or the evaluation itself. Below are the items that raised the most questions for me.
In Forrester reports, the category weights are meant to prioritize key features and capabilities of a technology, but in this Wave, it seems that primary and secondary categories have been mixed. Why? SSPM, at its core, enables security teams to monitor and manage their SaaS stack. Items like configuration drifts, compliance frameworks and breadth of app integrations sit at its very heart. Taking a look at the categories and the weighting associated with each in this report, one can misunderstand the core features of an SSPM solution.
The Innovation criteria is solely based on technical employee headcount. The rating is calculated based on the absolute number of technical headcount, clearly disadvantageous to emerging vendors as opposed to larger vendors. Many would argue that the success of an emerging vendor lies in their innovation, agility, and ability to disrupt the norm also based on their tech, vision, research and more. This might explain why all emerging SSPM companies were given a lower rating, influencing their position in the Wave overall — as this criteria was given one of the highest category weights at 14%.
Respecting Forrester’s definition of innovation, perhaps it would be more logical to calculate the ratio of technical headcount vs overall headcount instead of the absolute number of technical headcount.
Forrester includes Shadow IT detection capabilities and remediation, OAuth grants discovery, automatic bulk revocation of grants, identification of managed and unmanaged applications, and proxy-based shadow IT discovery for the report scoring.
Adaptive Shield’s 3rd Party App Inventory shows all 3rd party apps discovered, including OAuth apps, and the user who granted the OAuth consent, among many other important details. The 3rd Party App Inventory detects unsanctioned apps that are connected to apps integrated within the Adaptive Shield platform. With over 140 apps out-of-the-box integrations and the ability to connect custom apps, Adaptive Shield customers have deep visibility into their large network of apps, sanctioned or unsanctioned, from within the solution.
Important to note is that Adaptive Shield does not support proxy-based shadow IT discovery, like a CASB. SSPM, being a modern solution, is API based. In fact, one of the reasons SSPM technology emerged was to intentionally shift away from control via proxy.
Another point of interest not mentioned in Forrester’s definition, is the innovative element to show API keys. Adaptive Shield’s 3rd Party App Inventory also presents API Key information, a new and important feature for this capability.
While Forrester's Wave report is a valuable resource for assessing solutions, my analysis has uncovered areas where we concur, and where we differ. I believe it's crucial for stakeholders to evaluate the report with a clear understanding of the details and delve into the above discussion to judge for themselves.
I’m thankful to Forrester for bringing this important sector of SSPM to front-of-mind, and ultimately, your organization's specific requirements and direct experience with the solution should guide your decision-making process, ensuring a tailored fit for your organization's SaaS Security needs.


Former employees retaining SaaS app access happens far more often than businesses care to admit. Nearly a third of all employees retain some degree of access to the SaaS stack.
When employees move on, voluntarily or otherwise, it’s in the organization’s best interests to remove all access to corporate assets. Much of this process is done through automated workflows, where employees are removed from the identity provider (IdP) which triggers their removal from other systems.
However, users must be manually deprovisioned from applications that weren’t integrated into the IdP. Failure to do so could lead to data theft, breaches, or other incidents conducted by either the former employee or someone who steals their credentials.
A newly released guide, “Offboarding Employees from Your SaaS Stack in 7 Steps”, explains why deprovisioning users isn’t always as straightforward as it seems, and gives step-by-step instructions to fully deprovision users, as well as automate the process. The process is summarized as follows: (For the full details, download the guide here).
Organizations must overcome many challenges to permanently remove a user from their SaaS applications:
Removing access for former employees requires that they be fully deprovisioned. If you are using a manual process, follow these steps. (For further explanation on all these steps, download the full guide here).
Following this process will remove ex-employee access while ensuring that other users will still have access to the app.
Beyond manual deprovisioning, introducing and enforcing strong governance policies for SaaS applications can go a long way toward reducing the risk. For example, if company policy required all SaaS users to login through an SSO or using MFA, user access would be curtailed the moment their login tools were deprovisioned.
Some users, particularly those with high privileges, are required by the application to have local access. Unfortunately, these users will retain their access even when they are removed from the SSO or MFA. In those circumstances, maintaining a list of users with local access can be used to identify is instrumental to identifying users that must be manually deprovisioned.
Shared passwords are another way users can get around deprovisioning, as they may maintain access through a shared team account. Enforcing an anti-password sharing policy and training users about the dangers of password sharing can go a long way toward reducing risk.
The easiest way to deprovision users from SaaS applications is through a SaaS Security Posture Management (SSPM) platform that is integrated with a SOAR. Using automated workflows, these processes quickly identify and fully deprovision offboarded employees who maintained access to SaaS applications.
By using an SSPM, enterprises can confidently move forward, knowing that access to their applications is under their full control.
Have users you need to deprovision? Download our latest ebook, Offboarding Employees from Your SaaS Stack in 7 Steps!


If forecasters are right, over the course of today, consumers will spend $13.7 billion. Just about every click, sale, and engagement will be captured by a CRM, Marketing or Customer Service platform and more operational apps. Inventory applications will trigger automated re-orders; communication tools will send automated email and text messages confirming sales and sharing shipping information.
SaaS applications supporting retail efforts will host nearly all of this behind-the-scenes activity. While retailers are rightfully focused on sales during this time of year, they need to ensure that the SaaS apps supporting their business operations are secure. No one wants a repeat of one of the biggest retail cyber-snafus in history, like when one U.S.-based national retailer had 40 million credit card records stolen.
The attack surface is vast and retailers must remain vigilant in protecting their entire SaaS app stack. For example, many often use multiple instances of the same application. They may use a different CRM or ServiceNow tenant for every region they operate in or have different tenants for each line of business. Each one of these tenants must set up their configurations independently, with each one limiting risk and meeting corporate standards.
Here are a few areas retailers should focus on to ensure their SaaS Security over the entire holiday season.
Access Control settings are particularly important to retailers as they typically have a lot of employees, in many types of roles and responsibilities, from operations and infrastructure to bookkeeping and finance. Retailers need to limit who can enter an application and the privileges those users will have once inside the app. Access and visibility to sensitive data should only go to those who require it to perform their job functions. Creating role-based access and monitoring employees then ensures that they have an appropriate level of access based on their role is a key step in reducing the risk level.
One additional area worth reviewing is access granted to former employees. Former employees should almost always be deprovisioned as part of the offboarding process. When applications are connected to an SSO and access is only through that SSO, the offboarding is automatic. Unfortunately, many retailers have apps that either sit outside the SSO or allow employees to log in locally. In those circumstances, employees must have their access removed manually from each application.
This is also a time of year when people receive emails to their corporate email addresses for end-of-year sales and promotions. Threat actors use this as an opportunity to carry out phishing attacks, making it all the more important to harden anti-phishing controls within the SaaS stack.
Pricing information is one of the most sensitive pieces of information retailers have. While web crawlers may have access to published prices, it’s of paramount importance to protect future pricing strategies and plans. During the holiday season, when competitors are looking for every pricing and promotion advantage, securing this information behind serious data leakage protection is a top priority.
When available, turn on encryption settings to prevent unauthorized users from viewing your critical data. Turn off the ability to share or email files outside the organization and require some form of user authentication before users can access boards, spreadsheets, and databases.
Protecting customer information from leaks should be another high priority for retailers. Nothing will drive customers away from your website than reports of personal information, such as PII (Personal Identifiable Information) and payment information, being leaked. Harden security settings to prevent unauthorized data leaks from the application.
One additional area of concern is mobile users. These devices are often unmanaged, and when used to access corporate SaaS applications, they can be used to provide threat actors with an entranceway into the application. Users should be directed to only use managed devices when accessing corporate applications.
Unfortunately, we live in an era of insider threats. In Adaptive Shield’s annual survey, 43% of respondents said they had experienced corporate espionage or an insider attack within their SaaS stack. Preventing these types of attacks are notoriously difficult, as authorized users log in with verified credentials and their nefarious activities are all within the parameters of their access.
For retailers, monitoring user activity is one way to detect threats before they turn into full-blown breaches. Monitoring and analyzing user behavior allows organizations to identify these threat actors by detecting anomalies in their behavior. By analyzing behavioral anomalies, which might include accessing data during unusual times or downloading an unusual amount of data, retailers can uncover insider threats and protect themselves.
Some retailers may monitor these settings and behaviors manually or with older technologies like CASBs. Neither of those approaches are likely to be effective. SaaS settings can change without notice, and it's far too easy to miss the signs of threats to the application.
SaaS Security Posture Management (SSPM) tools, like Adaptive Shield are the only effective way for retailers to secure their whole SaaS stack. They automatically and continuously monitor settings, even over the busy holiday season, to detect and identify misconfigurations, unauthorized access, and users that need to be fully deprovisioned.
Using an SSPM, retailers can move ahead confidently, knowing that every tenant of their applications in every country they operate is secure. They can update strategies, retain customer data, and monitor users to prevent insider attacks.


Earlier this month, threat actors leveraged compromised credentials to access Sumo Logic’s Amazon Web Services account. Sumo Logic immediately took down the infrastructure exposed by the incident, and conducted a rotation of credentials to prevent further compromises.
Sumo Logic is a cloud-based log management and analytics platform that empowers organizations to gain actionable insights from their machine-generated data. The platform is designed to handle and analyze massive volumes of log data, providing real-time visibility into the health and performance of applications, systems, and infrastructure. Sumo Logic helps organizations make informed decisions, troubleshoot issues, and optimize their IT environments by offering a centralized and scalable solution for log management, monitoring, and analytics.
At this time, Sumo Logic has reported that there is no evidence to suggest the breach will impact any of its customers.
It’s important to point out that the Sumo Logic breach was not a misconfiguration or vulnerability, but a breach caused by compromised credentials. The company reported that it has added extra security measures to further protect its system, including improved monitoring and fixing any gaps that might lead to future breaches of this nature.
Sumo Logic has recommended that its customers immediately rotate their Sumo Logic API Access key. This helps prevent attackers from using old keys that may have been compromised.
As an added precaution, Sumo Logic recommends that its customers rotate 3rd-party credentials that have been stored with Sumo Logic for data collection by the hosted collector (e.g., credentials for S3 access) or as part of webhook connection configuration.
Adaptive Shield’s platform has two security checks that are aligned with Sumo Logic’s recommendations.
Organizations that use Adaptive Shield’s SaaS Security Posture Management (SSPM) platform can easily gain visibility into Sumo Logic’s posture. Adaptive Shield has over 25 security checks for Sumo Logic, covering access control, key management, password management, and other security domains. Adaptive Shield also discovers administrative accounts and local accounts and consolidates multiple user identities into a single user as it monitors users and user behavior. This data, which is further enriched by other applications in the SaaS stack, provides contextualized visibility into those who are accessing the application and their behavior within the app, and is used to further secure the application.


Effective marketing operations today are driven by the use of Software-as-a-Service (SaaS) applications. Marketing apps such as Salesforce, Hubspot, Outreach, Asana, Monday, and Box empower marketing teams, agencies, freelancers, and subject matter experts to collaborate seamlessly on campaigns and marketing initiatives.
These apps serve as the digital command centers for marketing professionals. They house essential go-to-market strategies, and are often connected to live payment systems authorized to spend substantial budgets. Ensuring their security is a complex task, given the multitude of applications, application owners, configurations within each app, users, interconnected apps and more. In this article, we explore the top Marketing SaaS application use cases, from external users and publicly shared links to connected apps and credit cards — and how to ensure the security and integrity of the data stored within them.
Marketing departments frequently grant administrative or high-access permissions to agency and freelance partners who need access to sensitive reports and data in order to perform. However, managing these external users can be a daunting task. It's vital to closely monitor their permissions and trim them down to the minimum necessary level. Additionally, there's often a gap between the time an employee leaves an agency and when the agency notifies the client. During this period, former employees can retain their access.
Collaboration with agencies often requires sharing files, project management boards, and folders with various team members. Using one set of public links for all users is a tantalizing option, as it cuts down on administrative tasks every time a new user is introduced into the project.
However, this approach can inadvertently expose sensitive assets to former agency employees or other unintended recipients, as public links can be used by anyone.
Marketing budgets often involve significant sums of money, and this financial data is highly sensitive. It's not uncommon for external agencies to manage these budgets, and if left unsecured, it could lead to malicious activities like unauthorized data access or the running of negative campaigns. Organizations need to ensure that access configurations are tightly controlled, with Identity Threat Detection & Response (ITDR) mechanisms sending alerts when users exhibit anomalous behavior.
Marketing departments rely heavily on prospect and customer data, which is stored and analyzed in SaaS databases like Customer Relationship Management (CRM) systems, Marketing Automation Hubs, and Sales Development Representative (SDR) tools.
Protecting this sensitive data is highly important and requires robust access controls, multi-factor authentication (MFA), and constant monitoring of internal user behavior.
Marketing teams utilize a wide array of connected applications to support their daily operations. These range from calendar apps, to video conferencing plugins, design, project management tools and ad optimization apps. Each of these applications requests different levels of permissions to access company data, some of which are quite intrusive. Organizations need visibility to quantify the risk from these applications.
SaaS apps hold the key to productive and efficient work. Any potential data leak or breach is not only a problem for the organization at large, but especially for the Marketing department, who retains the ultimate responsibility for ensuring the brand. Any reputational damage, especially if caused by a MarTech solution, would bring severe impact.
SaaS Security Posture Management (SSPM) platforms enable security teams to work collaboratively with Marketing and ensure the security of these applications. SSPMs monitor and manage internal and external users, ensure tight access controls across the SaaS stack, and safeguard sensitive data. The right SSPM solution will ensure that no operational workflows are disrupted and that all marketing stakeholders remain efficient and productive.


Mergers and acquisitions (M&A) are exciting times for organizations. Initially, most of the attention is focused on integrating two companies into a single entity, and exploring the new capabilities brought on due to the merger. In this environment, surrounded by organizational changes and amid swirling questions surrounding responsibility, SaaS security is often nothing more than an afterthought that falls through the cracks.
While that attitude is understandable, it exposes companies to risk. Additional applications mean a larger attack surface, and delays in reviewing and upgrading SaaS security may expose newly acquired secrets to threat actors.
While there are a myriad of benefits to securing your new SaaS stack, here are three that demand your immediate attention.
During M&A, companies typically find they have multiple versions of the same applications in their SaaS stack. It can take years before all the applications are seamlessly integrated into a single instance, and some applications are never reconciled.
If the two companies originated in different industries, their configurations may be set to meet different compliance standards. Now that they are under the same corporate umbrella, those standards must be aligned.
Furthermore, different companies have different policies. With the two companies under a single roof, security teams must be able to automatically compare the differences to identify best practices and align the different instances under a single policy.
Employees are a common casualty in an M&A. When let go, they are removed from the Identity Provider (IdP) and automatically deprovisioned from any SaaS app connected to the company’s IdP.
While this would seem to solve the problem of former employees logging into corporate SaaS applications, it is only a partial solution. Applications connected to the company’s SSO will automatically deprovision the user’s SSO account. However, users will retain their access rights to any application that is not connected to the SSO. These users must be removed manually.
App admins introduce another challenge to security teams. While their SSO access may be deprovisioned, these users typically have local access as well. The combination of admin rights and local access means that employees in this category can inflict significant damage to their former employer. This includes the ability to change settings to make data public, add new user accounts to exploit at a later date, download and expose PII or corporate secrets, and delete all assets saved within the application.
Gaining a full picture of your users and their access is essential from the moment the acquisition is complete.
Companies in different countries and industries are held to different standards by regulatory agencies. These requirements apply to all company assets, including ones that are newly purchased.
While all companies do some form of due diligence on the security standards being maintained by the target company, the first time they can actually apply their standards to purchased SaaS applications is post-merger.
Public breaches following an M&A are a PR nightmare; ones that occur because newly acquired applications are non-compliant are a disaster. Customers and partners question the entire merger, and tend to look for other providers they can trust.
To avoid these issues and others, it’s vital that security teams rapidly review and monitor their newly acquired applications. An SSPM platform can be connected to applications over API in minutes, and begin sharing its findings quickly.
In addition to a posture score for each connected app, security teams can export app user lists for the entire SaaS stack. With that information in hand, they can run reports to identify users who must be deprovisioned, and have their SOAR automatically remove access to former employees.
SSPM-based ITDRs monitor the entire SaaS stack and will recognize the techniques, tactics, and processes of threat actors. Furthermore, it can identify anomalous user behavior, and prevent application breaches from turning into data breaches.
SSPMs can also show which misconfigured settings are hurting compliance scores, and help your organization meet required regulatory standards.
As time moves on, SSPMs will enable security teams to compare security settings from different instances of the same application. App owners and security teams can create benchmarks that derive from the best practices of both organizations, as they move forward in integrating the two SaaS stacks.
After a merger is an interesting time in every part of the organization. For SaaS security, it’s an important opportunity to secure the SaaS stack and allow business to proceed as usual.


Earlier this week, ServiceNow announced on its support site that misconfigurations within the platform could result in “unintended access” to sensitive data. For organizations that use ServiceNow, this security exposure is a critical concern that can result in a major data leakage of sensitive corporate data.
ServiceNow is a cloud-based platform used for automating IT service management, IT operations management, and IT business management for customer service, as well as HR, security operations, and a wide variety of additional domains. This SaaS application is considered to be one of the top business-critical applications due to its infrastructural nature, extensibility as a development platform, and access to confidential and proprietary data throughout the organization.
Simple List is an interface widget that pulls data that is stored in tables and uses them in dashboards. The default configuration for Simple List allows the data in the tables to be accessed remotely by unauthenticated users. These tables include sensitive data, including content from IT tickets, internal classified knowledge bases, employee details, and more.
These misconfigurations have actually been in place since the introduction of Access Control Lists in 2015. To date, there were no reported incidents as a result. However, considering the recent publication of the data leakage research, leaving it unresolved can now expose companies more than ever.
It’s important to point out that this issue was not caused by a vulnerability in ServiceNow’s code but by a combination of configurations that exist throughout the platform.
This issue stems from security controls in a ServiceNow Access Control List (ACL) widget called Simple List, which puts records into easily readable tables. These tables organize information from multiple sources and have configurations with a default setting of Public Access.
Because these tables are the core of ServiceNow, the issue isn’t contained within a single setting that can be fixed. Potentially, this needs to be remediated in multiple locations within the application in combination with the usage of the UI widget, and throughout all tenants. To further complicate the issue, changing a single setting could break existing workflows connected to the Simple List tables, causing severe disruption of existing processes.
On the other hand, leaving these tables and applications exposed could have major security implications now that this issue has received so much attention.
We encourage all ServiceNow customers to review the recent guidance published by ServiceNow in their knowledge base article – General Information | Potential Public List Widget Misconfiguration.
To summarize, exposure assessment and remediation measures shall include:
Organizations that use a SaaS Security Posture Management (SSPM) solution are able to gain visibility into ServiceNow’s configurations and remediate the issue based on the recommendations.

To help organizations secure ServiceNow, Adaptive Shield is offering a free ServiceNow assessment for this issue. After a quick validation of your org, our Security research team will send you a report detailing any exposure your portals may have from this misconfiguration.
Click here to request the complimentary assessment.


On October 7, 2023, as global news has reported, there was a brutal surprise attack by the Hamas terror organization on Israeli cities and villages. With thousands of civilian casualties, and hundreds taken hostage into the Gaza strip, Israel was forced to enter a state of war with Hamas.
At Adaptive Shield, our commitment to our team as well as to our customer’s business continuity are unwavering. This blog aims to shed light on the measures we are taking to ensure business continuity during these uncertain times.
Operational Resilience: We have large global teams across all departments, ensuring there is no business impact. We have also created business and tech readiness plans to adapt to changing circumstances, assessing potential scenarios to maintain operational continuity.
Communication Channels: Open and transparent communication is crucial. We will provide timely updates on any changes to our operations through various channels, keeping you informed and confident in our ability to navigate challenges.
Risk Mitigation: We are actively monitoring the situation and adjusting our strategies to mitigate potential risks. Our goal is to uphold the highest standards of service and protect the interests of our customers and partners.
Dedicated Support: Our dedicated customer success and support teams remain available to address any concerns or questions you may have. Your satisfaction and success are paramount to us, and we are committed to maintaining the quality of our relationships.
As we navigate these uncharted waters, Adaptive Shield remains steadfast. We understand the importance of stability and reliability in our relationships and partnerships, and we are confident in our ability to adapt, overcome, and emerge stronger together.
If you have any specific questions or if there's anything we can do to support you better, please don't hesitate to reach out.


Overpermissioning is one of the seven deadly SaaS sins. It paves a path straight to data leakage and catastrophic data breaches, and unnecessarily stretches resources that would be better served addressing other cyber threats.
This phenomenon happens for any number of reasons. Some admins decide to grant users all access so they aren’t bothered by future requests to increase access or to ensure productivity isn’t disrupted because a team member can’t access a key resource. In other cases, admins create multiple high-privilege accounts within their team to ensure access if the regular admin is OOO.
To truly secure SaaS data, organizations need to right-size their permissions, and develop a policy that follows the principle of least privilege.
When you consider that every user account makes up the perimeter of the app’s security fence, limiting access to individual accounts makes a lot of sense. Should high-privileged account credentials be compromised, the results could be disastrous.
A skilled threat actor that accesses a high-privilege account can move laterally through the application to accomplish its nefarious agenda.
The principle of least privilege maintains that users should only have access to the data, resources, and applications required to do their job. By right-sizing permission levels to the needs of the user, organizations limit their single points of exposure. Threat actors are limited to the permissions of the compromised account.
Customizing permission sets that match the needs of employees is not always easy. While almost all SaaS applications offer some form of role-based access control, these settings should be fine-tuned through the application’s configurations to meet the precise needs of the organization.
Roles should be defined for each application, making it easy for SaaS admins to assign the right level of access for each employee that uses the app.
Administrators also must be mindful of privilege creep. This takes place when employees are granted increased permissions while a co-worker is away or while working on a specific project, and then forgotten about.
Another common occurrence of privilege creep happens in Salesforce. When users are unable to access a specific file, they often fill out a ticket requesting access to the information they need. There are hundreds of different settings controlling access within that application. When administrators are unsure which configuration needs to change to provide access, they often grant the user View All Data rights. This high level of access is far greater than that which the user needs, and unnecessarily puts the company’s data at risk. Unfortunately, this type of overpermissioning is rarely closed.
When SaaS applications have too many admins, it becomes nearly impossible to maintain control over the application. Anyone with admin access can change settings to meet their needs at the moment, without realizing the implication of their actions.
Most admins are business users focused on getting the most value out of the application, or at least, focused on getting the job done quickly. If they feel that MFA is slowing down productivity, or want to share files with “Anyone with Link,” they have the means to make those changes.
While their intentions may be good, the consequences of removing MFA or allowing anyone to download a file can lead to serious issues, including data leakage or SaaS ransomware. The importance of right-sizing permissions and limiting the number of admins simply cannot be overstated.
SSPMs play an important role in right-sizing permissions. They identify high-permission users, and can alert security teams when the number of users with high permissions crosses a specific threshold.
Many SSPMs contain user inventories, which provide all the user data security teams need to help design right-sizing policies. While SSPMs are not Identity and Access Management (IAM) tools and shouldn’t be used as a replacement for them, they do provide governance over IAM solutions, ensuring that they are functioning as designed.
These automated tools help ensure that users aren’t overpermissioned, and maintain the overall safety of the data within the SaaS stack


The great thing about SaaS applications is that they are quick to install and ready from the start to get employees using them for their endless business needs. They easily integrate with third-party applications to increase functionality and make it easier for employees to get their job done. The downside, of course, is this integration creates a security risk for the SaaS stack and organization at large.
What kinds of security risks?
Dive into it with Eliana V.
In this video, you’ve learned about the risks and realities that third-party apps pose to organizations as they expand the organization’s attack surface. There is an automated solution to identify connected apps, enabling the security team to minimize risks and mitigate threats.
If you are interested in more SaaS security topics, check out the SaaS Security On Tap channel.


SaaS applications are the backbone of modern businesses, constituting a staggering 70% of total software usage. Applications like Box, Google Workplace, and Microsoft 365 are integral to daily operations. This widespread adoption has transformed them into potential breeding grounds for cyber threats. Each SaaS application presents unique security challenges, and the landscape constantly evolves as vendors enhance their security features. Moreover, the dynamic nature of user governance, including onboarding, deprovisioning, and role adjustments, further complicates the security equation.
With great convenience comes great responsibility, as securing these SaaS applications has become a top priority for Chief Information Security Officers (CISOs) and IT teams worldwide.
Effectively securing SaaS applications requires a delicate balance between robust security measures and enabling users to perform their tasks efficiently. To navigate this complex terrain, this article excerpts a step-by-step guide to establish a robust SaaS security strategy – from planning to execution and performance measurement.
Before embarking on a SaaS security journey, it's imperative to understand your organization's specific landscape and security needs. While applications like Salesforce and Microsoft 365 may contain more critical data, even smaller, niche apps used by various teams can store sensitive information that must be protected.
Consider the regulatory and compliance requirements applicable to your business. Industries such as finance adhere to SOX, while healthcare organizations must comply with HIPAA. Understanding your regulatory environment is essential for shaping your security strategy.
Additionally, prioritize user access and data privacy. Implementing the principle of least privilege (POLP) ensures users have access only to the data required for their roles, reducing the risk of data breaches and unauthorized access. If your apps handle personally identifiable information (PII), ensure your security program aligns with privacy laws.
Here is some basic info you should collect for each app:

To be most effective, your SaaS security program must integrate tightly into the existing infrastructure. It must connect with the organization's Identity Provider (IdP) for effective user governance and your single sign-on (SSO) provider to make it more difficult for unauthorized users to access the SaaS stack. These integrations enhance the protection of your applications and make it easier for security professionals to do their job.
It's also important to integrate your SaaS security tools with existing SOC, SIEM, and SOAR tools. The SOC team can analyze alerts and quickly make a determination as to the mitigation required. Meanwhile, SIEM can manage events while SOAR can orchestrate remediations, deprovision users, and automate many of the mitigations needed to secure the SaaS stack.
SaaS security is a collaborative effort involving multiple stakeholders. Business units manage SaaS applications with a focus on productivity, while the security team's priority is data protection. Bridging the gap between these groups and deciphering the unique language of each SaaS application's settings is challenging.
Effective SaaS security demands collaboration and compromise between these parties to mitigate risks without hindering productivity.
Creating a successful SaaS security program requires clear goals and key performance indicators (KPIs) to measure progress. Begin with a pilot program focused on critical applications managed by different departments. Establish a timeline for the pilot, typically around three months, and set realistic improvement goals.
A posture score, measured on a scale of 0-100%, can help gauge security effectiveness. Aim to maintain a score above 80% at the conclusion of a three-month pilot program and target a long-term score of 90-100%.
Start by securing high-risk, low-touch items in collaboration with app owners. Close communication is crucial to understanding the impact of security changes on workflows and processes. Address high-risk security checks impacting a small number of employees first. Utilize Security Posture Management solutions to guide remediation efforts based on application, security domain, or severity.
Some organizations choose to improve posture one application at a time. Others improve posture by domain across multiple applications, while still others choose to remediate issues by severity regardless of the application. Whichever model you choose, it is important to develop a process to help you move systematically through your applications.
Frequent meetings with stakeholders involved in remediation are essential, especially during the pilot phase. As the posture stabilizes, adjust the frequency of these meetings to ensure sustained security.
Continue onboarding and monitoring additional applications to enhance the security posture of your entire SaaS stack.
Embrace the principle of least privilege (POLP) to restrict user access to essential tools and data. Deprovision users who no longer require access to minimize risks associated with active accounts. Regularly monitor external users, particularly those with admin rights, to safeguard app data.
By adhering to these principles and following a structured approach, organizations can establish a robust SaaS security program. Remember, SaaS security is an ongoing process, and continuous adaptation and improvement are key to staying ahead of evolving threats in the digital landscape.
Excerpt from The Hacker News article published Sept 12, 2023.


In today's digital landscape, organizations are increasingly relying on software-as-a-service (SaaS) applications to drive their operations. However, this widespread adoption has also opened the doors to new security risks and vulnerabilities.
The SaaS security attack surface continues to widen. It started with managing misconfigurations and now requires a comprehensive approach to handling the entire SaaS ecosystem. This includes the continuous monitoring and management of user access, roles and permissions, 3rd party apps installed by users, risks deriving from SaaS user devices and Identity Threat Detection & Response (ITDR).
There are a variety of reasons that SaaS security is so complex today. Firstly, there are a diverse range of applications, each having its own UI and terminology. And those environments are dynamic, from SaaS vendors understanding the importance of security and continually enhancing their applications with modern security measures to the ever-evolving user governance required such as onboarding, deprovisioning, adjustments in user access, etc.. These controls are effective only when continuously governed, for each app and each user. If that’s not enough, these apps are managed by dispersed business departments, making it almost impossible for the security team to implement their security policies.
When it comes to dealing with SaaS threats, existing threat detection and identity management methods don’t go far enough. Today’s SaaS environments are complex and ITDR capabilities within these landscapes require deep knowledge and proven expertise.
To address the Identity Threat Detection & Response challenge within the SaaS ecosystem, Adaptive Shield has developed a powerful solution that detects and responds to identity-related security threats based on key Indicators of Compromise (IOCs) and User and Entity Behavior Analytics (UEBA). These indicators provide forensic signs of a potential breach, such as malware, data breaches, unusual behavior, and other suspicious events.
ITDR is designed to tackle various SaaS-related threats, including password-based attacks, IP behavior anomalies, OAuth-based attacks, unauthorized document access, unusual user agent activities, and more. By offering a comprehensive suite of protective measures, organizations must proactively defend their SaaS stack and ensure the integrity of their sensitive data.
Adaptive Shield’s ITDR is built on the foundation of a deep understanding of SaaS characteristics and Identity Governance within this landscape, based on its broadest coverage of SaaS applications in the market, encompassing over 130 applications.
As a means of prevention and first layer of defense, SSPM operates as the security layer in the Identity Fabric to establish robust user governance. This includes excessive permissions, access entitlement, user deprovisioning, and more, across the entire SaaS stack. Adaptive Shield provides organizations with deep and consolidated visibility and control of user accounts, roles, permissions, privileged users, and activities.
As a second layer of threat protection, Adaptive Shield’s ITDR capabilities provide extensive coverage in detecting anomalies and Tactics, Techniques, and Procedures (TTPs). By focusing on context and creating user and company profiles, it increases the accuracy of these detection alerts. Additionally, understanding expected behavior patterns and considering factors such as user access, permissions, and devices, enables the solution to better understand and prioritize alerts.


Identification of common tactics and techniques that adversaries use to compromise systems, steal data, or disrupt operations. By understanding these TTPs, ITDR improves incident response capabilities through:
Indicator of Compromise (IOC) Detection: Collection of evidence indicating that the organization's SaaS apps are under attack or have been compromised. IOCs can include data from IP addresses, domain names, URLs and more.
User and Entity Behavior Analytics (UEBA): Detection of behavioral anomalies, Adaptive Shield’s ITDR can identify threat actors as they navigate through the organization’s applications, offering proactive threat detection.
Enhance incident response capabilities and improve threat detection and mitigation by aligning observed or potential attack techniques with the MITRE ATT&CK framework.
Get alerts in multiple channels such as email, Slack, or Teams, indicating potential security incidents or suspicious activities that require immediate investigation or response.
Seamlessly integrate with your existing Security Operations Center (SOC) and Security Orchestration, Automation, and Response (SOAR) tools, improving threat correlation and incident response efficiency.
Get actionable recommendations and step-by-step guidance to address and mitigate vulnerabilities, weaknesses, or compromises in the event of a security incident.
When securing your SaaS environments, ensure your security platform goes beyond identity threat detection and response. Your solution should include a range of capabilities that strengthen your overall security management and offer a holistic prevention model for securing the SaaS Identity Fabric:
Read more about the different SaaS Security use cases
With unparalleled insights and an array of features, Adaptive Shield empowers organizations to protect their SaaS stack, prevent data breaches, and safeguard their SaaS data from emerging threats.
.png)
.png)
Over the last three years, Simple Storage Service (S3) buckets in Amazon Web Services (AWS) have leaked a lot of information. An American publishing company for educational content exposed grades and personal information for 100,000 students. A consumer ratings and review website exposed 182 GB worth of data covering American and Canadian senior citizens. Thousands of UK consultants had their passport scans, tax documents, background checks, job applications, and other personal information exposed.
Go back further in time, and S3 has leaked social security numbers, driver’s license information, military secrets, and more. S3 buckets have been considered the leakiest buckets in the world. Until now.
Over the past few months, analysts have started referring to GitHub as the new S3 bucket. This is due to multiple pieces of sensitive data leaking from GitHub repositories, including private repositories that were accidentally exposed to the public due to a misconfiguration. Twitter and Slack have both had code leak out of their GitHub repository. GitHub is known for containing sensitive secrets like 0Auth tokens, API keys, usernames and passwords, encryption keys, and security certificates.
The reasons are many. Sometimes, users make a mistake and accidentally expose private repositories. Other times, the fault is applications that request – and are granted – too much access. Another common scenario centers on a lack of control of who can change repositories and the users who have access to advanced settings.
User mistakes are the common denominator across almost every GitHub leak. The application, in a vacuum, is remarkably secure. However, when used in practice developers often hand over the keys to their repositories.
When publicly sharing repositories, users receive a warning message recommending that they revert the setting back and not allow wide access to the code. However, users tend to ignore those types of warnings. One click of the button later, and the repository is public, and the headlines are waiting to write themselves.
A few years ago, the issues caused by leaky S3 buckets were a driving force in the development and growth of CSPM solutions. This response helped improve cloud security. Leaks coming from GitHub and other repository apps are having a similar effect on SaaS security. They have raised awareness of the need for SaaS security, and have helped businesses upgrade their security profile.
Securing GitHub and preventing them from leaking source code and other information isn’t a particularly complex task. It requires an SSPM to monitor the application’s configurations and share settings. SSPMs provide automated, 24/7 monitoring, and they alert security team members and developers when settings are changed.
There are several high-risk settings to keep an eye on. Two-factor authentication should always be required, protecting the source code from password spray attacks or phishing attacks. Public GitHub pages should be closely watched. Public repositories should be closed to the public; if information needs to be shared with outside users, it should be shared with specific users who need to authenticate themselves before accessing the repository. GitHub keys should be rotated, and be deactivated over a reasonable amount of time.
These configurations are just some of the steps savvy organizations should take to plug their GitHub leaks. Controlling access, implementing data leakage protection, and monitoring key management help shore up the applications, and keep source code and other data safe.


We're excited to announce a new investment from Blackstone Innovations Investments, Blackstone's strategic investment arm, bringing our total capital raised to $44M. This investment will be used to accelerate Adaptive Shield’s mission to protect companies as the number of SaaS applications used by enterprises has continued to grow rapidly. This growth is creating a new and complex mesh of business-critical applications that are increasingly being targeted by attackers.
“With Blackstone's support, we will continue our trajectory for growth and expansion while keeping up with the constantly evolving threats.” - Maor Bin, CEO and Co-founder of Adaptive Shield
“Thinking about where attackers are going next is key to growing a world-class cybersecurity program that protects our brand, reputation, investors, and intellectual property,” says Adam Fletcher, Chief Security Officer at Blackstone. “We have partnered with and are using Adaptive Shield to help us continuously monitor the security posture of business-critical SaaS applications used across Blackstone to further protect the firm from attackers. We believe in Adaptive Shield’s mission and are excited to support the company with our investment as they enter their next stage of growth.”
With Adaptive Shield, organizations can prevent, detect, and respond to identity-centric SaaS threats through Misconfiguration Management, SaaS-to-SaaS Access and Discovery, Identity & Access Governance, Device-to-SaaS User Risk Management, and Identity Threat Detection & Response (ITDR).
"Blackstone's investment demonstrates its success with our offering and underscores Adaptive Shield’s innovative capabilities as the only SaaS security platform to integrate with more than 130 applications that covers an expansive SaaS attack surface,” said Maor Bin, co-founder and CEO at Adaptive Shield. “With Blackstone's support, we will continue our trajectory for growth and expansion while keeping up with the constantly evolving threats.”
"At Blackstone, we have a dedicated team of cybersecurity professionals advising hundreds of our portfolio companies to further strengthen the cyber defense across the entire Blackstone ecosystem,” says Adam Mattina, Deputy Chief Security Officer and Head of Portfolio Cybersecurity at Blackstone. “We view the SaaS ecosystem as one of the top emerging attack vectors today, and our usage and investment in Adaptive Shield is highly strategic for the broader Blackstone portfolio as we collectively strive to stay ahead of such threats.”
To learn more about Adaptive Shield’s different use cases, please visit the use cases overview page.


Companies store an incredibly large volume of data and resources within SaaS apps like Box, Google Workplace, and Microsoft 365. SaaS applications make up 70% of total company software usage, and as businesses increase their reliance on SaaS apps, they also increase their reliance on security solutions.
SaaS security is not a new problem, however, the attack surface has widened. It started with managing misconfigurations and now goes far beyond. Today, it takes a holistic approach that includes the continuous monitoring and management of user access, roles and permissions, 3rd party apps installed by users, risks deriving from SaaS user devices and Identity Threat Detection & Response (ITDR).
Securing numerous potential attack vectors for each user becomes a challenge when dealing with a diverse range of applications, each having its own unique characteristics. Additionally, the environment is dynamic, from SaaS vendors recognizing the importance of security and continually enhancing their applications with robust security measures to the ever-evolving user governance required (onboarding, deprovisioning, adjustments in roles and permissions). These controls are effective only when properly configured by the organization, for each app and each user, on an ongoing basis. If that’s not enough, these applications are managed by various business departments, making it impractical for the security team to exercise complete control.
The objective in SaaS security is finding the balance between securing applications while still enabling users to do their jobs efficiently.
Below we explain each attack vector and line of defense for a strong SaaS ecosystem security lifecycle.
Misconfigured SaaS settings are one of the leading causes of SaaS data breaches. Security teams have no visibility into security-related aspects of these apps that in most cases are managed by the business departments. To further complicate the picture, each SaaS application uses its own language for settings. This prevents security teams from developing an easy-to-use guide for business teams directing their security efforts. With companies easily averaging over 100 applications, each with hundreds of configurations and multiple users, deciphering and managing security settings is no easy task.
Adaptive Shield integrates with more than 130 SaaS applications to monitor and manage security misconfigurations through in-depth security checks and auto/step-by-step remediation.

Image 1: Bird’s-eye view of the security posture by app
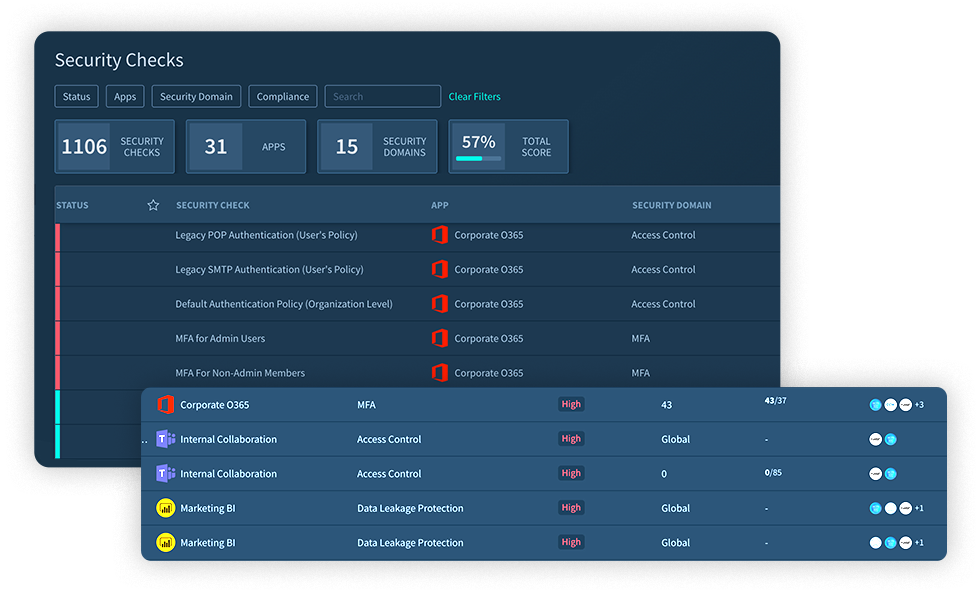
Image 2: List of security checks categorized by app, domain, severity, numbers of users, etc.
Identity Threat Detection and Response (ITDR) capabilities feature a set of security measures designed to detect and respond to identity-related security threats based on key Indicators of Compromise (IOCs). These IOCs provide forensic signs of a potential breach, such as malware, data breaches, unusual behavior, and other suspicious events. ITDR closes the gap between continuous identity governance and identity threat detection within the SaaS ecosystem, covering Tactics, Techniques, and Procedures (TTPs) and unusual User & Entity Behavior Analytics (UEBA) such as account takeover through compromised identities.
When it comes to SaaS threats, existing threat detection and identity management methods don’t go far enough. Today’s SaaS environments are complex and ITDR capabilities within these landscapes require deep knowledge and proven expertise in the way SaaS applications are designed.
Adaptive Shield’s engines cross-reference and analyze in-context TTPs and suspicious events from multiple sources, enabling the accurate detection of very complex and subtle threats.
As a means of prevention and first line of defense, SSPM should operate as the security layer in the identity fabric to establish robust user governance. This includes excessive permissions, access entitlement, user deprovisioning, and more, across the entire SaaS stack. Adaptive Shield provides organizations with deep and consolidated visibility and control of user accounts, roles, permissions, privileged users, and activities.
Identity governance use cases include:

Image 3: View of User Inventory broken down by privileges and user-specific security checks.

Image 4: View of Threat Center and activity information
To improve app functionality, many users integrate third-party apps into the core SaaS stack. These integrations take place without the knowledge of the security team and often ask for intrusive permission scopes, such as the ability to read, write, and delete data. While many of these applications are harmless, if taken over by a threat actor they can cause significant damage.
Adaptive Shield detects every connected third-party application, as well as identifies their scopes. Security teams can then review the information, and make an informed decision on whether to continue using the application.
3rd party app use cases include:

Image 5: View of 3rd-party connected apps with their severity levels and accessed scopes.
The login-anywhere nature of SaaS enables users to access sensitive corporate systems using unmanaged and compromised devices. These devices, which may contain malware, can be exploited to capture access credentials and tokens that can be used by threat actors. This is particularly high-risk when being done by an admin with broad access within the application.
Your SaaS security tool must review device data, and associate each device with a user. When high-privilege users access SaaS apps on a device that contains critical vulnerabilities, it pours the entire application at risk. Managing that risk is a key element of maintaining a secure SaaS stack.

Image 6: View of the SaaS User Device Inventory
Device-to-SaaS Risk Management includes:
Click here to request a short demo and get started with Adaptive Shield


Brick-and-mortar retailers and e-commerce sellers may be locked in a fierce battle for market share, but one area both can agree on is the need to secure their SaaS stack. From communications tools to order management and fulfillment systems, much of today's critical retail software lives in SaaS apps in the cloud. Securing those applications is crucial to ongoing operations, chain management, and business continuity.
Breaches in retail send out seismic shockwaves. Ten years later, many still remember one national retailer that had 40 million credit card records stolen. Those attacks have continued. According to Verizon's Data Breach Investigations Report, last year saw 629 cybersecurity incidents in the sector. Clearly, retailers must take concrete steps to secure their SaaS stack.
And yet, securing applications is complicated. Retailers tend to have multiple tenants of apps, which leads to confusion over which instances of the application were already secured and which are vulnerable to attack. They also have high employee turnover rates, and must quickly deprovision employees as they move on to other opportunities.
Retailers tend to use multiple tenants of the same app to manage different regions within the chain and different product lines across the chain. Consider a scenario where a retailer has fifty different instances of their CRM or ticketing system. Each tenant must be independently secured, following the retailer's guidelines.
While some instances of that application are undoubtedly secure, others present themselves more as a black hole, where no one in the company really knows what's happening. Some instances may have SSO, require MFA, and provide limited role-based access, while other instances may allow all users to login locally with only a single factor.
When most organizations discuss SaaS security, the concern is on protecting data. While that holds true for retailers as well, many retailers have tied their operations to SaaS apps. ServiceNow has reimagined retail experience, enabling retailers to better solve issues, manage their supply chains, and streamline operations.
Risks in apps like these would be catastrophic for a retailer. They could lose visibility and control of their entire supply chain, ordering system, and franchise support platform. This isn't an inconvenience; now that many retailers have completed their digital transformation they must make securing the applications powering operations a top priority.
According to the US Chamber of Commerce, nearly 70% of all retail jobs are unfilled, and surveys indicate that 74% of retail workers are planning to switch jobs this year. Those numbers indicate a transient workforce that needs rapid onboarding and even faster deprovisioning from company SaaS applications.
Many of these processes are automated. However, SaaS applications that are not integrated with the company's Identity Provider (IdP) software retain the employee's access to those apps. Additionally, employees with local access to apps often lose the ability to login with SSO but are still able to directly enter applications.
As part of any retail SaaS security program, attention must be paid to former employees. Revoking access immediately helps reduce the likelihood of data leaks, breaches, and other cyber attacks.
SaaS Security Posture Management (SSPM) enables companies to quantify the risk to their SaaS applications and take the steps needed to secure the stack. SSPMs monitor each tenant of an application independently in one single pane of glass, enabling security teams to identify under-protected applications and take the steps needed to prevent unauthorized access. To further enhance security, SSPMs help users find the most secure tenant and use it as a baseline for securing the other tenants.
SSPMs also monitor users. It can search users to identify those that need to be deprovisioned, and guide the security team on how to best remove access. Meanwhile, SSPMs threat detection capabilities can issue an alert when threat actors have breached the application.
By implementing an SSPM program, retailers can control and protect their SaaS stack, and take advantage of the benefits that come from their digital transformation.


It's easy to think high-tech companies have a security advantage over other older, more mature industries. Most are unburdened by 40 years of legacy systems and software. They draw some of the world's youngest, brightest digital natives to their ranks, all of whom consider cybersecurity issues their entire lives.
Perhaps it is due to their familiarity with technology that causes them to overlook SaaS security configurations. During the last Christmas holiday season, Slack had some private code stolen from its GitHub repository. According to Slack, the stolen code didn't impact production, and no customer data was taken.
Still, the breach should serve as a warning sign to other tech companies. Stolen tokens allowed threat actors to access the GitHub instance and download the code. If this type of attack can happen to Slack on GitHub, it can happen to any high-tech company. Tech companies must take SaaS security seriously to prevent resources from leaking or being stolen.
Slack's misfortune with GitHub wasn't the first time a GitHub breach occurred. Back in April, a stolen OAuth token from Heroku and Travis CI-maintained OAuth applications were stolen, leading to an attacker downloading data from dozens of private code repositories.
MailChimp, a SaaS app used to manage email campaigns, experienced three breaches over 12 months spanning 2022-23. Customer data was stolen by threat actors, who used that data in attacks against cryptocurrency companies.
SevenRooms had over 400 GB of sensitive data stolen from its CRM platform, PayPal notified customers in January that unauthorized parties accessed accounts using stolen login credentials, and Atlassian saw employee data and corporate data exposed in a February breach.
Clearly, tech companies aren't immune to data breaches. Protecting their proprietary code, customer data, and employee records that are stored within SaaS applications should be a top priority.
A strong SaaS posture is important for any company, but it is particularly important for organizations that store their proprietary code in SaaS applications. This code is especially tempting to threat actors, who would like nothing more than to monetize their efforts and ransom the code back to its creators.
Tech companies also tend to rely on a large number and mix of SaaS applications, from collaboration platforms to sales and marketing tools, legal and finance, data warehouses, cybersecurity solutions, and many more – making it even more challenging to secure the entire stack.
Tech employees heavily depend on SaaS apps to do their day-to-day work; this requires security teams to strictly govern identities and their access. Moreover, these users tend to log into their SaaS apps through different devices to maintain efficiency, which may pose a risk to the organization based on the device's level of hygiene. On top of this, tech employees tend to connect third-party applications to the core stack without thinking twice, granting these apps high risk scopes.
The high-tech industry is known for periods of hyper-growth, followed by downsizing. Over the past few months, we've seen Facebook, Google, Amazon, Microsoft, LinkedIn, Shopify and others announce layoffs.
Deprovisioning employees from SaaS applications is a critical element in data security. While much of the offboarding of employees is automated, SaaS applications that are not connected to the company directory don't automatically revoke access. Even those applications that are connected may have admin accounts that are outside the company's SSO. While the primary SSO account may be disconnected, the user's admin access through the app's login screen is often accessible.
At the same time, the industry is ripe with mergers and acquisition announcements. As a result of M&As, the acquiring company needs to create a baseline for SaaS security and monitor all SaaS stacks of merged or acquired companies, while enabling business continuity. Whether the hyper growth is organic or through an M&A, organizations need to be able to ensure access is right-sized for their users, at scale and rapidly.
The majority of data breaches impacting tech companies stem from stolen credentials and tokens. The threat actor enters the system through the front door, using valid credentials of the user.
Identity Threat Detection and Response (ITDR) picks up suspicious events that would otherwise go unnoticed. An SSPM (SaaS Security Posture Management) solution with threat detection engines in place will alert when there is an Indicator of Compromise (IOC). These IOCs are based on cross-referencing of activities such as user geolocation, time, frequency, recurring attempts to login, excessive activities and more.
Maintaining a high SaaS security posture is challenging for high tech companies, who may mistakenly believe they are equipped and well trained to prevent SaaS attacks. SaaS Security Posture Management is essential to preventing SaaS breaches, while an SSPM with ITDR capabilities will go a long way toward ensuring that your SaaS data is secure.


Recently, Max Corbridge and Tom Ellson from JUMPSEC's Red Team discovered a vulnerability in Microsoft Teams. This vulnerability allows for the introduction of malware into organizations using Microsoft Teams in its default configuration. In this blog post, we will delve into the details of this vulnerability and explore its potential impact.
In Microsoft Teams' default configuration, external tenants can reach out to staff members within an organization using Teams. Despite the presence of a banner indicating that the message is from an external tenant, a considerable number of staff members are prone to clicking on such messages. Exploiting this behavior, threat actors can bypass client-side security controls and send files containing malware to target organizations.
While messaging staff members from another organization, users are prohibited from sending files. However, researchers have discovered a method to circumvent this control, enabling seamless delivery of malware directly into a target's inbox. Leveraging an insecure direct object reference (IDOR) vulnerability, threat actors manipulate the recipient ID on the request and send malicious payloads. These files appear as innocuous attachments in the target's Teams inbox, disguising their true nature.
This vulnerability poses a significant risk as it bypasses most modern anti-phishing security controls. Furthermore, the payload is delivered through a trusted SharePoint domain, eliminating the suspicion associated with clicking on links in emails.
This vulnerability affects all organizations using Microsoft Teams in its default configuration. Although it has the potential to bypass traditional payload delivery security controls, there are measures that organizations can take to mitigate the risk. These are the same measures that can also help prevent the GIFShell vulnerability.
Assess whether your organization truly requires external tenants to message your staff. If not, tighten the security controls and disable external access in the Microsoft Teams Admin Center by setting the "Choose which external domains your users have access to" configuration to "Block all external domains". If communication with external tenants is necessary, consider in the above configuration allowing communication only with specific domains that your organization regularly interacts with. This approach strikes a balance by blocking unknown external sources while maintaining essential communication channels.
Prevent unmanaged external Teams users from starting a conversation with people in the organization by disabling the "External users with Team accounts not managed by an organization can contact users in my organization" configuration.

Raise awareness among staff members about the possibility of social engineering campaigns using productivity apps like Microsoft Teams. It is crucial to recognize that email is not the sole avenue for social engineering attack.
Enable Automated Protection with an SSPM
If you are already an SSPM solution, these Microsoft Teams configurations should be part of the platform’s security checks. The following actions can help the security team gain a better understanding of an organization's SaaS attack surface and its security posture.
Thanks to the efforts of Max Corbridge and Tom Ellson, a critical vulnerability in Microsoft Teams has been identified. With the widespread adoption of Microsoft Teams and its vast user base, this vulnerability poses a significant concern for organizations. By understanding the risks and implementing appropriate mitigation measures such as simple configurations, organizations can better protect themselves against this vulnerability and stay one step ahead of threat actors.


The Quick Serve Restaurant (QSR) industry is built on consistency and shared resources. National chains like McDonald’s and regional ones like Cracker Barrel grow faster by reusing the same business model, decor, and menu, with little change from one location to the next.
QSR technology stacks mirror the consistency of the front end of each store. Despite each franchise being independently owned and operated, they share subscriptions to SaaS applications, or use multiple tenants of the same application. Each app is typically segmented by store. Corporate IT and Security has access to the entire database, while each franchise has visibility into its own data.
These SaaS apps cover everything from CRMs to supply chains to marketing and HR. The data within is used to understand consumer habits, improve marketing campaigns, and manage employees. Like every other industry, QSR SaaS apps contain a wealth of data that needs to be secured.
At the same time, we’re seeing food chains come under attack. While it is unclear whether the recent breaches at fast food chains involved SaaS applications, what is clear is that threat actors are increasingly turning their attention to restaurant chains. QSRs have unique challenges and should take specific, significant security measures to protect their SaaS applications.
Like all businesses, QSRs need to prevent their data from falling into the hands of threat actors. In addition, QSRs have a secondary concern that few other businesses experience.
Burger King has about 7,000 franchises in the United States. These individually owned and operated restaurants often compete with each other. The different franchises may store data within the same SaaS applications. However, the data is segmented to prevent stores from seeing intra-chain competitor data.
Segmenting data so that the corporate CISO team has a full view of their applications, regional management offices have access to aggregated data within their region, and individual franchises are only able to see their data requires sensitive configurations through role-based access tools.
If misconfigured, data can easily be exposed within the chain. System administrators must constantly monitor their configurations to ensure this doesn’t happen.
In addition to sharing segmented applications, many QSRs use different tenants of the same application. Each tenant must be secured separately, with its configurations following the guidelines of the chain.
Some stores may have instances of applications that are highly secure, while others may have poor security posture. Ensuring that each branch maintains strict security standards in this type of environment is a monumental task.
Another unique challenge for today’s QSRs stems from the fact that they have been one of the major players affected by COVID-19 and the great resignation. Many restaurants have cut back hours, reverted to drive-thru only, or operate with skeleton crews trying to serve their customers.
The employee shortage means that more employees are given access to systems that would have been controlled by managers in the past. The shortage is also driven by employees staying at the job for short periods of time. These employees are not “cyber-trained,” and are far more susceptible to social engineering attacks like phishing. Furthermore, they tend to be younger, and don’t always appreciate the repercussions of sharing their login credentials with friends and social networks.
As a result, onboarding and deprovisioning employees from thousands of chains across the globe is more important than ever before. Former employees need their access revoked as quickly as possible to limit the likelihood of data leaks, breaches, and other cyber attacks.
To battle these unique challenges, a SaaS Security Posture Management (SSPM) can come into the picture. SSPMs help restaurants manage the settings that separate data by store. It also compares different tenants, letting the corporate CISO team know which stores, regions, and countries have secured their applications, and which have misconfigurations that could result in data leaks or breaches.
Furthermore, SSPM alerts restaurants when they have connected high-risk third party apps to the core hub, or if their employees are accessing the SaaS application with low-hygiene devices. It governs users and access, ensuring that security tools like MFA are in place, and reviews user activity to detect threats that could lead to breaches.
When security settings are misconfigured, it lets app administrators and security teams know when configuration drifts have made data accessible to other stores, and offers remediation guidelines to help them reseal the data wall between franchises.
With an effective SSPM tool in place, QSRs can manage their restaurants using SaaS applications with confidence that their data is safe.


As SaaS adoption continues to grow in the business landscape, it brings emerging security challenges that high-tech and telecom companies must grapple with.
A particularly attractive target for cybercriminals, the telecom industry allows attackers to inflict maximum damage with little effort. The combination of interconnected networks, customer data, and sensitive information allows cybercriminals to inflict maximum damage through minimal effort.
When it comes to the high-tech industry, there is a common misconception that these companies have an advantage, compared to older and established industries that are weighed down by decades of legacy systems and software. However recent breaches, such as the Slack Github attack, have highlighted how the more modern tech companies are also at risk when it comes to SaaS security.
While high-tech and telecom companies operate in different industries, they face common challenges when it comes to SaaS security. The key to choosing and implementing a comprehensive solution is by first recognizing the shared struggles such as the complexity of configurations, third-party app risks, and deprovisioning.
Securing the vast and complex network of SaaS apps, devices, and applications while ensuring smooth operations is not a simple feat. To keep the attack surface limited, organizations need to correctly configure all settings, continuously. In addition to the multitudes of settings, each SaaS app has unique terminology, UI, etc. It is the security team's job to learn every app's "language". With organizations deploying more and more apps everyday, the need for clear and contextualized visibility across all SaaS apps configurations has never been greater.
Both high-tech and telecom companies heavily rely on third-party apps to help boost efficiency and productivity in their day-to-day operations. When these third-party apps are integrated, they are granted permissions known as scopes. While some permissions may be completely harmless, others have the ability to expose an organization's most sensitive data. Security teams need to have visibility into both the number of connected apps and the permissions granted to effectively assess and manage the risk of a third-party app.
The high-tech industry is known for periods of hyper-growth, followed by downsizing. Meanwhile, Telecom companies are among the largest employers in the world with turnover rates hovering at about 18%. Companies operating in either of these sectors are especially exposed when proper deprovisioning lags. Proper deprovisioning ensures that former employees, especially those who are being removed from their job, have access to sensitive data revoked.
While much of the offboarding of employees is automated, SaaS applications that are not connected to the company directory don't automatically revoke access. Even applications that are connected may have admin accounts that are outside the company's SSO. While the primary SSO account may be disconnected, the user's admin access through the app's login screen is often accessible.
Both industries must find a balance between SaaS security and usability. On one hand, robust security measures protect sensitive data, prevent unauthorized access, and mitigate threats. On the other hand, user experience and productivity should not be sacrificed in the pursuit of stringent security measures. Organizations need to educate employees to create a solid understanding of security best practices. This can be achieved through security awareness programs and regular training workshops. Creating this balance is heavily dependent on the collaboration between app owners and security teams.
An SaaS Security Posture Management (SSPM) solution can play a vital role in securing SaaS applications for both telecom and high-tech companies. By providing comprehensive visibility and control over the SaaS environment, an SSPM enables organizations to effectively manage security risks. Consistent security across multiple SaaS applications reduces complexity and minimizes the risk of misconfigurations. By leveraging the capabilities of an SSPM, telecom and high-tech companies can enhance their SaaS security posture, protect sensitive data, and confidently adopt new SaaS apps while mitigating risks.
.png)
.png)
Adaptive Shield, June 13, 2023 – Adaptive Shield, an industry leader in SaaS security, today announces its partnership with leading cloud security provider Wiz as the company unveils Wiz Integrations (WIN). Adaptive Shield, hand selected as a launch partner, brings the power of SSPM to WIN, so that customers can seamlessly integrate Wiz into their existing workflows.
WIN enables Wiz and Adaptive Shield to share prioritized security findings with context including inventory, vulnerabilities, issues, and configuration findings. Mutual customers receive the following benefits:
The combined value of these two offerings will streamline security for organizations that are on a cloud journey, regardless of where they may be on that journey.
“This partnership enables security teams to complement CSPM security with SaaS security, providing security to cloud-based products. Additionally, this allows Security teams to make sure that the Wiz solution is secure, and detect any misconfigurations or threats to the security platform provided by Wiz” - Hananel Livneh, Head of Product Marketing
WIN is designed to enable a cloud security operating model where security and cloud teams work collaboratively to understand and control risks across their CI/CD pipeline. Wiz is setting the industry standard in integrated solution strategy to maximize operational capabilities of organizations with partners like Adaptive Sheild in WIN.


The Cloud Security Alliance (CSA), the world’s leading organization dedicated to defining standards, certifications, and best practices to help ensure a secure cloud computing environment, today released the findings of its latest survey, SaaS Security Survey Report: 2024 Plans & Priorities. Commissioned by Adaptive Shield, the leading SaaS Security Posture Management (SSPM) company, the survey gathered responses from 1,000-plus C-level security executives and professionals from all over the world, with the majority from North American enterprises.
“Many recent breaches and data leaks have been tied back to SaaS apps. We wanted to gain a deeper understanding of the incidents within SaaS applications, and how organizations are building their threat prevention and detection models to secure their SaaS ecosystem," said Hillary Baron, lead author and Senior Technical Director for Research, Cloud Security Alliance. “This explains why 71% of respondents are prioritizing their investment in security tools for SaaS, most notably turning to SaaS Security Posture Management (SSPM) as the solution to secure their entire SaaS stack.
“The attack surface in the SaaS ecosystem is widening and just as you would secure a cloud infrastructure with Cloud security posture management, organizations should secure their SaaS data and prioritize SaaS security,” asserts Maor Bin, CEO and co-founder of Adaptive Shield. “In last year’s survey, 17% of respondents said they were using SSPM. This year that figure has soared, with 80% currently using or planning to use an SSPM by the end of 2024. This dramatic growth is fueled by the fact that 55% of organizations stated they recently experienced a SaaS security incident, which resulted in ransomware, malware, data breaches, and more. Threat prevention and detection in SaaS is critical to a robust cybersecurity strategy spanning SaaS Misconfigurations, Identity and Access Governance, SaaS-to-SaaS Access, Device-to-SaaS Risk Management, and Identity Threat Detection & Response (ITDR).”
Among the survey’s key findings:
The survey gathered more than 1,000 responses from IT and security professionals from various organization sizes, industries, locations, and roles.


We are happy to announce that we have successfully earned the latest International Organization for Standardization (ISO) privacy certification ISO/IEC 27701:2019 ("ISO 27701") after an independent third-party audit by Standards Institution of Israel. Additionally, the company has successfully earned its Service Organization Control (SOC) 2 Type II certification, completed by Ernst & Young. These certifications, along with being GDPR compliant and ISO 27001 certified for many years, underscore Adaptive Shield’s unwavering commitment to the highest standards to protect its systems, users and data from constantly evolving risks and threats.
The ISO privacy standard includes requirements and provides guidance for establishing, implementing, maintaining and continually improving a Privacy Information Management System (PIMS). ISO 27701 builds on the International Standards Organization (ISO) 27000 series, a globally recognized framework for best practices in information security management.
“As a security organization, we are deeply committed to providing solutions to continuously monitor SaaS apps, users, and devices, and immediately identify, alert, and provide actionable remediation information, when needed,” said Maor Bin, our CEO. “As part of that core mission, it is our priority to maintain careful compliance with the global standards which protect data and the privacy of our customers, especially in increasingly complex SaaS environments and the evolving digital landscape.”
We recognize that SaaS apps like Microsoft 365, Slack, Zoom, and Salesforce are vital to the day-to-day operations of a business, but can often introduce security challenges. Featuring proactive, deep, continuous, and automated monitoring and management of business critical SaaS applications, Adaptive Shield’s SSPM platform allows security teams to gain control over these apps to harden security settings and reduce organizational risks.


In a world where identity is the new perimeter, user passwords are essential to protect your SaaS applications from unauthorized access. Effective password policies that are enforced at the corporate level reduce the gateway into your corporate data.
SaaS applications include a number of security settings that promote safe password use. When these settings are misconfigured, however, users can use passwords that are easily guessed by threat actors or can be discovered by hackers during a brute-force attack.
Compromised passwords do more than provide threat actors with access to information that should be protected. They open the possibility of an account takeover attack. Savvy threat actors may take their infiltration to the next level, particularly when accessing high-privilege accounts. Once in, they create new high-privilege users accounts that can be weaponized to download confidential data, conduct ransomware attacks, or maintain long-term espionage programs.
Password configurations make up about 6% of all SaaS app settings. Despite their small number, they play a large role in limiting access to sensitive information.
The configurations within the SaaS application are in place to better secure account access, which is why we’re sharing some key password configuration benchmarks for Salesforce, M365, and Google Workspace.
Password configurations cover the makeup of acceptable passwords as well as passwords for different categories of users. These configurations include:
There was a time when security experts universally recommended users update their passwords every 60-90 days to prevent accounts from being accessed by cybercriminals. As a result, most users got in the habit of using easily memorable passwords that didn’t change much.
In 2017, Digital Identity Guidelines from the National Institute of Science and Technology (NIST) recognized that this approach led to an overall weakening of user passwords. Instead, they recommended strong passwords that only need to be changed in the event of a user request or evidence of an authenticator or credentials being compromised.
Salesforce’s settings take the NIST recommendation into account with two settings. Passwords Expiration and Profile Passwords Expiration should both be set so that they never automatically expire.
To do so, first set the general policy following these steps:
This password setting is governed by default in the general Password Policies of the account but can be overridden by selecting a different setting in a specific profile.
Take the following steps for specific profiles, which can be used to override the general policies for a specific user account.
Here are some Salesforce user benchmarks to measure your settings against.

Microsoft 365 uses several settings to prevent users from using easily guessable words as their passwords, which helps defend against password spray attacks.
The Custom Banned Password and the Enforce Custom Banned Password security settings allow administrators to add a list of up to 1,000 words that cannot be included in a password. The Password Protection for Windows Server Mode and Password Protection for Windows Server Active Directory configurations are relevant for organizations using hybrid environments. These two settings configure Azure Active Directory to work with on-prem data centers, and prevent the use of corporate specified words.
The list of banned words should include corporate keywords, such as company products, trademarks, or executive names. It should also include things like local sports teams names, popular players, or famous actors.
Here are some M365 benchmarks to measure your settings against.

App passwords can be used in some circumstances to bypass MFA security checks and company-monitored SSO. These apps can be easily compromised when threat actors get a user’s login credentials.
Super Admins with App Passwords is particularly dangerous. These high-privilege users require app passwords so they can access apps when SSO is down. However, this access is risky because it bypasses multi-factor authentication. Configurations should be set to periodically confirm with Super Admins that they require their high-privilege level of access.
Regular users that are accessing apps with a password should also be approached, through the system, to confirm that they require access to specific apps. Those who are no longer in need of the applications should remove apps that they no longer need.
Here are some Google Workspace benchmarks to measure your settings against.

Passwords are most effective when coupled with MFA or as part of an SSO.
Strong passwords policy includes:
Up next in our Benchmark for SaaS Apps Series is Endpoint Protection.


The telecom industry has always been a tantalizing target for cybercriminals. The combination of interconnected networks, customer data, and sensitive information allows cybercriminals to inflict maximum damage through minimal effort.
It's the breaches in telecom companies that tend to have a seismic impact and far-reaching implications — in addition to reputational damage, which can be difficult to measure, telecoms are often at the receiving end of government fines for their cybersecurity and privacy failures.
There are few industries in the world that collect as much sensitive data as telecom companies. In recent years, telecom companies have accelerated their digital transformation, shedding legacy systems and reducing costs. These changes, coupled with the need for stronger collaboration with third-party vendors, have led them to SaaS applications to handle their CRM.
Today, telecoms are using SaaS apps for billing, HR, call management, field operations management, tracking call center effectiveness, and hundreds of other applications. While these apps facilitate communication and help improve processes, the sheer size of these companies requires extra security precautions to be taken, particularly in the areas of collaboration and identity management.
Demographics, behaviors, purchase history, family data, mobile preferences, and browsing history are just a few of the data points that are collected in a global Telecom.
This data is analyzed, packaged, and shared with mobile advertisers. The advertisers are given access to the telecom's SaaS apps, where they can mine for data and develop powerful marketing and advertising campaigns.
However, the partnership between telecoms and their vendors requires app settings to be configured in a way that allows external access while preventing unwanted visitors from seeing, copying, and downloading data.
When configurations drift, they can expose personal data to a far greater audience and put the telecom at risk of breaches.
Telecom partnerships extend to other telecoms. Roaming charges need to be shared between GSM providers for billing purposes, while MVNOs build their entire business model on the telecom's network. This data is captured and stored within SaaS applications, and it may be vulnerable at the point where it is shared between operators.
Telecom companies are among the largest employers in the world. With turnover rates hovering at about 18%, a telecom with 200,000 employees can expect 36,000 employees to leave the company every year, or about 140 per workday.
Much of the employee deprovisioning process is automated. HR removes the employee from the company directory, which triggers processes that shut down their email, network access, SSO access, and other identity-based access points.
Some SaaS applications are connected to the company directory, but many are not. They require additional efforts to deprovision. An admin on a SaaS application, for example, may have multiple logins to the SaaS – one through the SSO and one with a username and password to allow access in the event of an SSO outage. While the SSO access may be automatically revoked, oftentimes in SaaS applications, the secondary access remains active.
Former employees, especially those who are being removed from their job, need their access revoked immediately to prevent the likelihood of data leaks, breaches, and other cyber attacks.
A strong SaaS posture is a must-have for any company. Communication service providers, however, are a tantalizing target to threat actors and need to take their threat detection capabilities to the next level.
SaaS threat detection involves reviewing data from the entire SaaS stack to identify indications of compromise (IOC). These signs of malware, data breaches and other suspicious events within the SaaS ecosystem can direct the security team to any compromised account, and allow them to mitigate the threat.
SaaS Security Posture Management (SSPM) is the first line of SaaS defense. Telecom operators can use the tool to manage their sensitive configurations. Its round-the-clock monitoring of all settings will alert the security team in the event of drift, and its remediation guidelines will show app owners how to secure their data.
SSPMs are also used to monitor users. It can search user rolls from across the SaaS stack to find former employees that need to be deprovisioned, and guide users on how to best remove access. Meanwhile, SSPM's threat detection capabilities can alert the security team when they are facing an imminent threat.
With an effective SSPM in place, telecom operations can use their SaaS applications with confidence, knowing that their data is secure.


Malware is harmful code designed to infect, damage, or provide access to computer systems. It can take many different forms, including viruses, worms, Trojan horses, ransomware, adware, and spyware. While it is easy to understand how that impacts a computer or mobile device, it is less clear when discussing SaaS applications.
However, malware can be used for various purposes, such as stealing sensitive information, destroying or altering data, causing system failures or crashes, and creating a backdoor for hackers to gain unauthorized access to a system. It spreads through infected email attachments, downloads, malicious websites, or vulnerabilities in a system's software or security protocols.
Research has shown that 40% of businesses using SaaS applications have malware hidden within the files and documents stored in their SaaS stack. Almost any file, from presentations, spreadsheets, and documents to images and PDFs can have harmful malware embedded within it. Once the file is accessed, the malware may have a chance to enter the user’s device or network and cause damage.
SaaS applications include settings designed to prevent the spread of malware in this manner. These configurations can protect against malware, as they reduce the vulnerabilities in a system that malware can exploit. Malware often targets known security weaknesses and exploits them to gain access to a system or to spread throughout a network. By setting security configurations, users remove these vulnerabilities and make it more difficult for malware to gain a foothold in your system.
Clickjacking is a type of attack that takes something which appears safe, such as a button or link on a webpage, and hides a malicious link within it. Once clicked upon, it can lead to data intrusions, unauthorized email, credential changes, or other site-specific results.
Within Salesforce, hidden iframes can be maliciously placed to entice users to click buttons and links that are in the hidden iframe. Once the user clicks on the link, they have triggered some type of attack.
There are four levels of protection to prevent clickjacking attacks from taking place:
Here are the malware configuration benchmarks that you can use to measure your security posture.
Please note: Data in these tables comes from over 200 anonymized customer tenants in the Adaptive Shield platform

The best way to prevent malware from causing any damage is to prevent it from reaching your users’ inboxes. However, malware does occasionally find a way to get past filters and checks within email gateways and make its way to the user.
With Zero Hour Auto Purge enabled, Microsoft 365 continues to check unread messages in the inbox for malware. This advanced level of protection stops all types of malicious code from entering the system, preventing large-scale attacks capable of infecting an entire network.
However, Zero Hour Auto Purge is only effective when it is enabled. To turn it on, follow these steps.
Here are the malware configuration benchmarks that you can use to measure your security posture.
.png)
Google Workspace prevents malware from reaching your inbox with a series of settings that identify malicious codes, encrypted messages, and harmful links. Some of these measures include scanning email attachments and blocking those with malware, identifying phishing emails, blocking malicious links from reaching the inbox, and using encrypted connections to prevent unauthorized access.
When it detects suspicious attachments and encrypted messages, Google Workspace isolates the attachments, moving them to the spam folder or into quarantine. Users are protected from unknown senders and the damage they wish to inflict on the company.
However, Google Workspace is only able to provide those protections when its settings are configured securely. To prevent suspicious attachments and scripts from unknown senders from reaching employee inboxes, follow these steps.
Here are the malware configuration benchmarks that you can use to measure your security posture.

Up next in our Benchmark for SaaS Apps Series is Password Management.
.png)
.png)
According to a recent report by cybersecurity expert Brian Krebs, several organizations, including banks and healthcare providers, are leaking sensitive information due to a misconfiguration in Salesforce Communities. Communities, which allows Salesforce users to easily create websites, has two means of entry. Some sites require user login, while others allow guests to view content without any authentication.
The misconfiguration reported on by Krebs gives unauthenticated guest users access to records, some of which contain sensitive information like social security numbers and bank account information. Krebs notes that this is not an isolated incident and that configuration-based security risks are a common problem across many SaaS products on the market today. This post will cover the leak as well as best practices to secure your Salesforce Community.
Salesforce Community Sites are designed to provide a platform for users to engage with one another, share information, and collaborate. The custom-branded sites run on Salesforce’s Lightning framework and are integrated with the Salesforce instance. Guest user access is a feature that allows unauthenticated users to view designated content and resources without requiring a login.
However, Salesforce administrators sometimes erroneously give guest users access to internal resources, which can lead to unauthorized users accessing private information and data leaks. In the Krebs report, security researcher Charan Akiri said he identified hundreds of organizations with misconfigured Salesforce Community sites.
Salesforce states that the data exposures are not the result of vulnerabilities in the Salesforce platform but are due to customers' misconfigured access control permissions. In September 2022, Salesforce issued an advisory in which it recommended that users utilize its Guest User Access Report package to assist in reviewing access control permissions for unauthenticated users. Krebs also cited a written statement from Salesforce, in which the company said it continues to release “robust tools and guidance for our customer.”
One of the organizations with multiple misconfigured Salesforce Community sites is a US State. The team had hastily created multiple Community sites in response to the COVID-19 pandemic which were not subject to the State’s normal security review process. The State’s Chief Information Security Officer said his “team is frustrated by the permissive nature of the platform.”
He is not the only one; reading the responses to the Krebs article on the Salesforce subreddit (r/salesforce) is alarming. One Salesforce admin admitted on Reddit that “I accidentally did this at my last company when I was messing around with our Knowledge sites.” Another one acknowledged that this “mistake is easily made.”
As this leak is not due to a vulnerability in Salesforce's app, it is important to note which configurations can lead to such a leak, and overall how customers can and should continuously control (assess, monitor, and remediate) the app’s configurations.
Additionally, the issue with misconfigurations providing pathways to critical data is not unique to Salesforce. SaaS products have become increasingly complex over time, making it challenging for administrators and security teams to ensure that the correct security and access configurations are in place. Moreover, SaaS providers often introduce new features into their products, which can expose customers to new risks that negatively impact their organization's security posture.
An additional challenge is the gap of knowledge between app owners and security experts, and the complex responsibility assignment matrix for SaaS security.
Salesforce admins can take the following steps to prevent their sensitive data from being exposed to guests in Communities:
If you are already an Adaptive Shield customer, these configurations have been monitored by our platform for the past couple of years, as Adaptive Shield’s cyber experts have a deep understanding of this Salesforce domain. The following actions can help the security team gain a better understanding of an organization's SaaS attack surface and its security posture.


Data leakage is the unauthorized transmission of data from within an organization to external destinations or parties. In a SaaS context, it can refer to data that is exposed without passwords or an expiration date. The data may contain sensitive financial records, customer PII, strategic documents, or any number of things that are best kept within the organization.
Data Leakage Protection (DLP) are the configurations within the SaaS applications that limit exposure. They make up 13% of all SaaS app configurations, protecting sensitive data in Google Workspace, Microsoft 365 (M365), Salesforce, Box, Workplace, ServiceNow, and hundreds of other applications.
Employees often need to share documents with external stakeholders, including vendors, partners, and freelancers. To truly be secure, files should be authorized for use by specific users and include an expiration date when the file is no longer accessible. However, this can become difficult in practice.
When multiple users within a vendor need to review the document, employees must choose between clicking “share with all users” or add specific users that can access the files. For employees that aren’t security experts or concerned about security issues, sharing with anyone with the link is the preferred choice. They don’t need to add multiple users to a file or be bothered by file-sharing requests.
The trade-off for that convenience is a weakening of document security. When files don’t require passwords or login names, they can be accessed by anyone. The configurations within the SaaS application are in place to prevent this type of exposure, which is why we’re sharing some key benchmarks that companies are using for high-risk DLP configurations in Salesforce, M365, and Google Workspace.
Monitoring files that have been shared outside the organization is a difficult task. Once files have been shared, it is almost impossible to track their distribution. The types of configurations that are most concerning from a DLP perspective center on:
Salesforce relies on configurations to prevent data from being exposed to external users. When set correctly, Guest User Sharing Rules ensure that documents remain secure and that only authenticated guest users can access a file.
However, when Guest User Sharing Rules are enabled, uncredentialed users can access any document that matches the sharing rule’s criteria. In its guidelines, Salesforce tells administrators to implement security controls that match the sensitivity of the data, and reminds users that “Salesforce is not responsible for any exposure of your data to unauthenticated users based on this change from default settings.”
While there are use cases for allowing this permission, it is critical that security teams periodically review their sharing settings to protect confidential files from exposure. To check those permissions:
Benchmark your Data Leakage Protection settings against other Salesforce users.

Automated email forwarding to external email addresses can pose a security risk, as confidential information and files may be shared outside the organization. Microsoft 365’s configurations enable administrators to configure inbox rules that prevent users and administrators from mailbox forwarding.
Outbound spam filter policies can be used to control automatic forwarding. By turning the setting off or selecting Automatic - System-controlled, automatic forwarding to external email addresses is disabled.
Here are some M365 benchmarks to measure your settings against.

Google Workspace enables users to have desktop access to their files in Google Drive by deploying the Backup and Sync client. However, this feature stores Google files locally on the desktop, where they can be opened and read by anyone with access to the computer.
To reduce the risk of data leaks, desktop access to Drive should be removed. To do so, follow these steps:
Here are some Google Workspace benchmarks to measure your settings against.
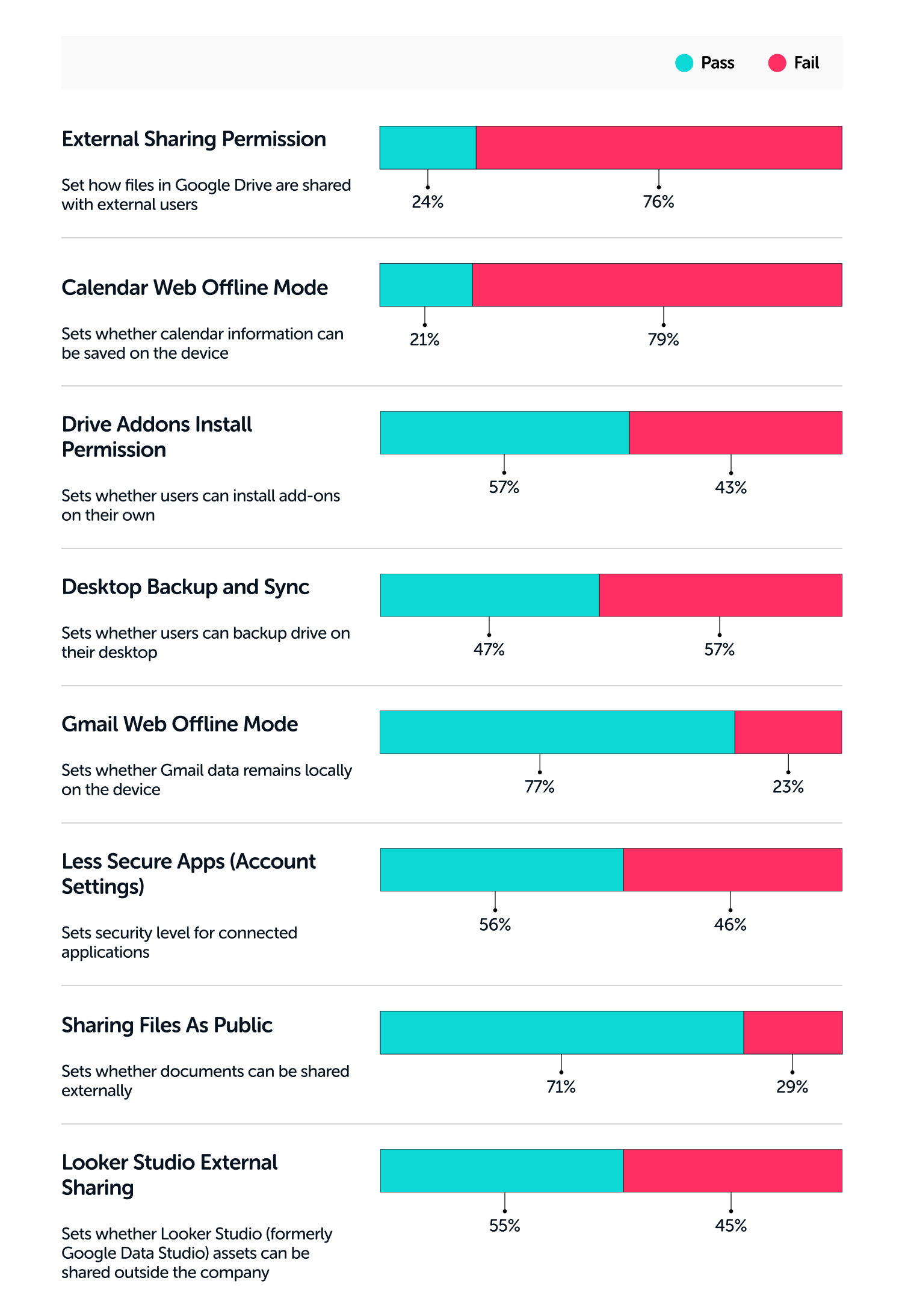
Data leakage is a serious problem facing organizations using SaaS applications. Users often want reduced friction when sharing files with external parties, but that reduced friction can expose company secrets to others.
Security teams can better secure company documents by:
Up next in our Benchmark for SaaS Apps Series is Malware Protection.


CASBs and SSPM are complementary solutions that focus on different aspects of SaaS data security. CASBs apply corporate policies relating primarily to identity, permissions, and data encryption while SSPM protects data from each individual SaaS app based on the usage and settings within each application including identity, permissions, data encryption, and much more.
CASBs have been around for over a decade, continually adapting to meet the needs of cloud and SaaS security. CASBs focus on applying corporate policies to cloud-based entities, and have a wide range of uses.
Traditional CASBs act like a firewall, where all connectivity to SaaS applications passes through a CASB proxy server where it is monitored and all actions are approved. Next gen CASBs connect to SaaS apps through APIs, giving them more access and increasing their SaaS monitoring functionality.
CASBs enable organizations to apply policy across all corporate users, covering things like password rules, SSOs, and permissions, as well as monitoring and applying the way data moves from place to place.
In contrast to CASB’s ability to apply broad corporate policies across all applications, SSPM secures the configurations of each individual application. CASBs function as a broker, viewing the SaaS application from the outside. They track information and users as they access select SaaS applications. SSPMs, in contrast, survey the landscape from within the entire SaaS stack, with protections customized for each application.
This is an important distinction. Salesforce, which is used by the sales team, and Workday, which is used by the HR team, are both SaaS applications but are used by different teams in different ways. The developers of each application also used different languages and strategies while designing security features for each application. Applying a one-size-fits-all CASB-like policy to address security concerns of these two applications simply wouldn’t work. It requires the delicate, individualized touch only an SSPM can provide.
SSPM provides full visibility into business-critical SaaS applications and enables the security team to gain control of every security element. From maintaining continuous hygiene of all security controls to detecting threats within the SaaS ecosystem, SSPMs enable the management and response to any configuration drift or threat.
SSPMs enable organizations to maintain a high SaaS security posture. It checks for misconfigurations, connected third-party applications, identity and access governance, and monitors user devices and their hygiene score. CASBs, however, can only manage some misconfigurations that relate to identity management, permission scopes, and data encryption. CASBs also lack the visibility needed to see third-party applications that are integrated into the SaaS stack.
SSPMs are also capable of threat detection stemming from misconfigurations, third-party applications, and vulnerable user devices in real time.
SSPMs also allow organizations to respond to threats and configuration drifts in real time to mitigate risk. They provide remediation steps, alerts, and ticket creation to help security teams protect SaaS data.
SSPMs and CASBs do have some overlap between them, but the two solutions complement each other. Both are part of a rich, cloud security fabric necessary to protect sensitive data. CASBs focus on applying corporate policies relating to identity, permissions, and encryption. SSPMs complement those efforts by protecting the data and securing access within the individual SaaS application based on usage and configuration settings.
CASBs are proxy-based solutions. They inspect traffic, as well as identify malicious activity and data exfiltration from an in-line perspective of a governed user. SSPMs extend that coverage to external users, contractors, partners, third-party applications, and IoT devices.
CASBs are effective at detecting users who access more data than they should or access data that they should not be seeing. SSPMs add additional protection by identifying misconfigurations that could lead to data becoming publicly accessible without user registration or user creation.
SSPMs are significantly less expensive than CASBs and have a far simpler setup, allowing organizations to protect their entire SaaS stack rather than just a few critical applications. Furthermore, SSPMs can identify non-IdP users that sit outside the organization, and identify user devices with poor security hygiene, capabilities that complete CASB.


Cloud Security Posture Management (CSPM) and SaaS Security Posture Management (SSPM) are frequently confused. The similarity of the acronyms notwithstanding, both security solutions focus on securing data in the cloud. In a world where the terms cloud and SaaS are used interchangeably, this confusion is understandable.
This confusion, though, is dangerous to organizations that need to secure data that exists within cloud infrastructures like AWS, Google Cloud, and Microsoft Azure, as well as data within SaaS applications like Salesforce, Microsoft 365, Google Workspace, Jira, Zoom, Slack and more.
Assuming that either your CSPM or SSPM will secure your company resources that live off-premises is misplaced trust in a security tool that was only designed to secure either your cloud or your SaaS stack.
It's absolutely vital for decision makers to understand the difference between CSPM and SSPM, the value derived from each solution, and that both complement each other.
CSPMs monitor standard and customized cloud applications that are deployed by the customer in a public cloud environment for security and compliance posture. Additionally, they usually provide compliance monitoring, DevOps, and dynamic cloud integration functionality.
Businesses use cloud platforms for many things. Whether it is being used as Infrastructure-as-a-Service (IaaS), which allows businesses to manage elements such as networks, servers, and data storage, or platforms which facilitate the hosting, building, and deploying of customer-facing applications, cloud platforms contain critical business components.
For example, a company might use an IaaS to host its e-commerce website. By using a cloud provider, they have the flexibility to scale their web traffic capacity based on traffic flows. Peak times of day or seasons might increase their capacity, while fewer resources would be needed during off-peak or off-season times.
Within that site, a company might have a separate app that enables customers to prove their identity (know your customer process – KYC). That customer is stored in a container, where the app can access the information as needed, and then authorize the user within the website.This is a common practice of separating different elements of a service (e-commerce, in this case) into different apps, containers, servers, and networks. Such separation, which is enabled by using an IaaS, provides flexibility, better performance, customization, and potentially better security. But all this comes at a cost of great complexity and expanding the attack surface
CSPMs are tasked with monitoring the security posture of the cloud services hosted in IaaS. In practical terms, this means scanning cloud settings and identifying any misconfigurations that could introduce elements of risk to the service. In circumstances where using a complex architecture, using containers in a Kubernetes system, the configurations are particularly complex, and securing them without a CSPM can lead to configuration drifts that expose data to the public.
SSPMs, like Adaptive Shield, integrate with a company's applications, like Salesforce, Jira, and Microsoft 365, to provide visibility and control to the security teams and app managers for their SaaS stack. Such SaaS (Software-as-a-Service) apps are not hosted in the company's network or cloud infrastructure, rather they are hosted by the software provider.
Security teams have a unique challenge in securing SaaS applications. Each SaaS application uses a different topology for its settings. Security teams can't issue a one-size-fits-all directive on SaaS app configurations, while they need to secure many apps.
SaaS applications store a tremendous volume of company data and resources. Customer data, financial reports, marketing plans, employee profiles, and more are all stored within different SaaS apps. This makes sharing and collaboration simple but also acts as a beacon to threat actors who wish to monetize or sabotage company resources.
SSPMs deliver visibility into the settings of each application, providing a security score and alerting security teams and app owners when there are high-risk misconfigurations.
SSPMs extend their coverage into apps that are easily onboarded by employees. SSPMs provide security teams with a list of connected applications, as well as the permission scopes that have been granted to the app.
Security teams are also concerned about users, especially privileged users, accessing SaaS applications using a compromised device. SSPMs provide a user inventory and device inventory. These inventories display users, the apps they are associated with, their permission scopes, and the hygiene of the devices they are using to access SaaS applications.
Clearly, CSPMs and SSPMs are integral pieces of a robust cloud security platform. Any company using multiple SaaS applications with multiple users needs an SSPM solution to protect its data. At the same time, any company using cloud services like Azure, GCP, or AWS would be putting its operations at risk without a CSPM solution.
CSPMs allow organizations to identify their misconfigured networks, assess data risk, and continually monitor cloud events in their cloud environment. SSPMs help organizations identify and remediate misconfigurations, manage third-party applications, detect configuration drifts, manage users, and comply with universal or industry standards.
The two security tools each cover valuable use cases. CSPMs identify vulnerable cloud configuration settings, provide compliance for security frameworks, monitor cloud services, and manage changes that are made to their logs.
SSPMs have similar use cases, but in the SaaS environment. They offer continuous 24/7 visibility into misconfiguration management, and enable security teams to monitor SaaS-to-SaaS access. It offers compliance reports from the entire stack, rather than individual applications, and can help IT teams optimize their SaaS license spending. It manages risk from users and devices, as it ensures that only authorized personnel have access to the SaaS data.
SSPMs are also used to monitor CSPM applications. As the CSPM is a SaaS solution, SSPMs can ensure the CSPM configurations are set correctly, review connected third-party applications, and provide user governance.
Working together, SSPMs and CSPMs ensure the security of your off-premise data by providing visibility and remediation actions that close vulnerabilities and reduce risk.


Access control is the key to your SaaS kingdom. It determines who has access, their permission levels, and the steps they need to take to enter into the system.
Access control is the center of your SaaS security foundation, which is why it accounts for 59% of all SaaS configurations. Of the 13,000 configurations Adaptive Shield checks out of the box, over 7,500 address access control.
Access control is a multi-level domain, with layers of security elements all intended to prevent unauthorized users and threat actors from accessing your data. This first line of defense requires oversight and nuanced approach to balance SaaS usability and availability with security.
Access control configurations impact every employee within the company with access to specific apps. Employees from different teams may require different areas of access, while employees with a team may need different levels of access.
In an app like Salesforce, IT admins need administrative access. Some sales personnel may need access to marketing costs, while others might also need access to reports. On the sales team, sales reps should only have access to their leads, while sales managers should have access to all the leads within their department or domain.
Creating these types of role-based access profiles is complex, and it’s tempting to over-permission users. The configuration settings may appear overwhelming, which is why we’re sharing some foundational settings within Salesforce, Microsoft 365, and Google Workspace for an effective access control policy.
Salesforce is the leading CRM in the market. It contains an immense amount of sensitive information, and protecting that data is of paramount importance. Comprehensive user authentication policies are vital to ensuring security.
Connecting Salesforce to your organization’s SSO/IDP solution is one of the core ways to ensure and enforce access control. Over 80% of the Salesforce instances our research team reviewed have enabled SSO. However, only 2% of those organizations required users to login through SSO.
A surprising 98% of organizations allow their users to access Salesforce using a basic username and password authentication. This misconfiguration enables threat actors to capture usernames and passwords through sophisticated phishing attacks or other means. Once that username is compromised, threat actors have access to a wealth of customer and pipeline data.
Here are some other Access Control configuration benchmarks that you can use to measure your security posture against.


Microsoft 365 documents, presentations, spreadsheets, and email are among a company’s most valuable resources. Sharepoint servers contain files, making it easy for employees to collaborate on critical projects. The data within Microsoft 365 demands robust access control. Here are Access Control benchmarks to measure your company against.
Legacy authentication protocols in M365 may be undermining your entire security setup. Security teams can implement SSO, harden password policies, require MFA, and keep Azure Active Directory updated and well maintained – and still find themselves exposed.
Legacy authentication protocols within M365 means usernames and passwords are often stored on the device. These login credentials are sent at every request, increasing the likelihood of those access credentials being compromised especially if sent without Transport Layer Security (TLS).
Basic authentication, while necessary for companies using legacy software, is unable to enforce MFA and is superseded by modern authentication. These include IMAP, OAB, Exchange ActiveSync (EAS), and others.
As a result, over 80% of the M365 instances we reviewed had at least one legacy authentication protocol enabled, and over 50% had two or more. 10% have almost all legacy authentication protocols enabled, and many of them are used daily.

As a result, over 80% of the M365 instances we reviewed had at least one legacy authentication protocol enabled, and over 50% had two or more. A surprising 10% have almost all legacy authentication protocols enabled, and many of them are used daily.

Like M365, Google Workspace uses legacy authentication protocols, such as IMAP and POP. In addition, it uses some high-risk configurations that are unique to Google Workspace. App Passwords are a special tool used to connect third party applications to a SaaS stack. App Passwords can provide access into an application, and they don’t require MFA for authentication.
App Passwords were created to allow external apps to integrate with Google Workspace as the equivalent of an API key. However, they allow users to bypass MFA and SSO.
To strengthen an organization’s security and reduce risk, app passwords should never be used by super admins. Regular users can use App Passwords, as long as the passwords are monitored and rotated appropriately.


Access Control is a significant security function and creates the first line of defense of an organization’s SaaS security policy. In turn, security teams are responsible for strengthening and ensuring an organization’s access control.
Security teams can begin creating a strong foundation of access control by:
Up next in our Benchmark for SaaS Apps Series is Data Leakage Protection, the practice of detecting and preventing data breaches, exfiltration, or unwanted destruction of sensitive data.


As organizations work toward securing their SaaS apps, security teams are looking for benchmarks that can help guide their efforts. SaaS ecosystems are growing quickly, and without some standardized tool to measure success, most security teams lack the data to know where they stand.
In our Benchmarks for SaaS Apps series, we’ll share benchmark data for five high-impact security domains. These domains contain thousands of settings, spanning organizational users, applications, and instances. When configured correctly, they limit data access to authorized users, protect against SaaS ransomware, and limit potential breaches.
Each article in this series will cover high-risk configurations in Google Workspace, Microsoft 365, and Salesforce, as well as provide data that can be applied to every app in your SaaS stack.
The top five security domains in SaaS are:
Adaptive Shield cybersecurity experts and researchers extracted anonymized data from hundreds of tenants and apps within the Adaptive Shield system.
First up in the series is Access Control!


Collaboration sits at the essence of SaaS applications. The word, or some form of it, appears in the top two headlines on Google Workspace's homepage. It can be found six times on Microsoft 365's homepage, three times on Box, and once on Workday. Visit nearly any SaaS site, and odds are 'collaboration' will appear as part of the app's key selling point.
By sitting on the cloud, content within the applications is immediately shareable, making it easier than ever to work with others.
However, that shareability is a two-sided coin. On the flip side are often sensitive links sitting on public-facing websites that can be easily accessed. The exposure caused by leaked documents can cause tremendous harm, from competitors trying to gather corporate secrets to whistleblowers sharing internal information with reporters or legislators. As integral as collaboration is to SaaS, sharing links creates a high-risk situation, and real-life breaches, that can be mitigated through the right processes.
There are essentially two ways to share files and documents out of a SaaS application, although the terminology used by M365, Salesforce, Google Workspace, and Box is slightly different. The file owner can either make the resource available to specific users or make it available to "anyone with a link".
Sharing the file with specific users can be cumbersome and time-consuming. As the file gets passed to different stakeholders, the file owner needs to add every user as they need it. When working with an outside vendor, that requires coordination with the vendor contact to understand who will be working with the file. Each user's email address needs to be added individually, and if someone is missed, the file owner needs to go back into the sharing settings and add them.
Sharing a file with anyone who has the link is much less cumbersome. The document owner can copy the link, send it to the vendor, and not have to think about document management any longer. Additionally, often people request access from a private account (for example, their gmail email) instead of a business-monitored email account. This could be due to the fact that sometimes external vendors only have a private domain, or it could be they are also logged in to their private account and so they accidentally request access to it.
However, as tempting as it is to share the link freely, doing so primes the document to being leaked. There is no controlling what happens to the file once the link is shared, and users can access the file from any account. The degree of risk that the file can be leaked increases exponentially.
New York City school officials learned the dangers of link sharing the hard way. In 2021, school officials confirmed a data leak that contained sensitive information of over 3,000 students and 100 staff members in the NYC public school system. The data was exposed when a student gained access to a Google Drive.
That story came on the heels of a Microsoft Sharepoint breach, during which a student doing homework stumbled onto a draft document discussing when schools would reopen during COVID-19. The letter included details of testing policies, quarantine policies, and other information that the school system was not ready to release. This data was exposed due to unsecured document-sharing settings.
It isn't just school officials who need to be careful with their shared links. In 2021, an armed forces unit asked soldiers to fill in a Google form relating to their COVID-19 vaccines. Each soldier entered their name and ID number, and answered questions relating to coronavirus.
However, the author of the Google Form allowed respondents to review the results. Anyone with the link had access to the soldiers' names and ID numbers. The data was listed chronologically, making it easy to group specific soldiers by their unit. This data was accessible to anyone with a browser and link. After being alerted, the military unit removed the form, but it's impossible to know how far the data leaked.
According to TechCrunch, in 2019 security researchers found dozens of companies were leaking sensitive corporate and customer data that was saved in Box. Using a script to scan for box accounts, researchers found over 90 companies – including Box – with data that was visible to anyone with the link.
Companies, which included Amadeus, Apple, Edelman, and Herbalife, exposed customer names and contact information, project proposals, donor names, patient information, and more. This information could have easily been protected had companies used the access controls available within the platform.
The data contained in SaaS apps lives on the cloud, but it doesn't need to be exposed to anyone with a link. Security-conscious organizations should follow these guidelines to ensure their data remains secure.
Share files with specific users – Requiring users to login before they can access the data drastically reduces the likelihood of data falling into the wrong hands
Add expiration dates to shared links – Most documents and files are shared and eventually forgotten about, putting companies in a position where they don't even know that they are exposed. By adding an expiration date to the link, that oversight won't come back to hurt the company.
Password protect all links – Add an additional layer of data security by requiring password protection on all external-facing files
Create a Resource Inventory – List all corporate resources in a single place that includes each file's share settings, providing security teams with a single view that enables them to evaluate risk and exposure.
Every unprotected link has the potential to expose data. As the link sharer, it is impossible to know the hygiene of the recipient's device, whether they will share the link with others, or even whether they provide others with access to their email account. Securing links is one of the main ways of protection available to limit this risk.
Another approach to protecting against links being overly shared is the automated method, through use of an SSPM solution. An SSPM, like Adaptive Shield, helps organizations protect against data loss by identifying which resources are being publicly shared and are at risk. It can also identify resources that are shared without an expiration date, or are set to allow guests to share the item. Once the security team is aware of the attack surface, they can remediate and secure the link as needed.
.png)
.png)
It’s that time of the year, when RSA brings together leaders and visionaries from across the cybersecurity world. During these four days, visitors gain insight, join conversations, and experience solutions that make an impact on their business and career. From live sessions and parties to games and demos galore, RSA packs it all. That being said, there’s a lot to choose from and only so many hours in the day. That's why we have gathered a list of the top 7 activities for the SaaS security aficionados to hit at RSA 2023.
Book an in-person meeting with our experts at RSA here.
With the world of cybersecurity changing so rapidly, it’s often difficult to keep up with new attack vectors and terminology. Two vastly different topics but often referred to interchangeably are IAM and identity security. That's why Derek Melber, VP of Product Engagement and Outreach at QOMPLX is hosting a roundtable to dive deeper into the difference between the two.
Microsoft’s Principal Product Manager, Shinesa Cambric, takes to answering the question: Is it possible to apply Zero Trust to billions of consumer identities while simultaneously addressing the challenges of growing a business and preventing fraud? Through this case study, attendees will learn about the challenges faced and lessons learned when balancing user experience and protection while simultaneously introducing friction to prevent and detect malicious actors.
Adaptive Shield is bringing the Fun Fair all the way to RSA at booth #1449. Our experts will demonstrate the Adaptive Shield Platform and cover use cases like misconfiguration management, SaaS-to-SaaS access discovery and control, Device-to-SaaS user risk management, Identity and Access Governance, and Identity and Threat Detection and Response (ITDR).
Vulnerabilities in the attack surface are everywhere, yet most of today’s approach to threat management is reactive-focused. Nico Popp, Chief Product Officer at Tenable, criticizes the emphasis placed on detecting and containing threats instead of preventing them in the first place. This session will delve into how exposure management delivers unified visibility, context-driven prioritization, and risk-based metrics as the foundation for tomorrow’s preventive security.
In the past ten years, organizations have adopted and come to depend on SaaS apps and other technologies to keep their businesses successful. However as business tools evolve, so does their risk. David Foote, Chief Analyst and Research Officer at Foote Partners, dives into the challenges of the conventional thinking about the ‘Future of Work’, presenting an alternative view from deep insights gained from 4,100 employers.

Everyone deserves a little fun at the end of a hard day’s work which is why Adaptive Shield is the title sponsor of the FOMO party. This afterparty will have great music and scrumptious food. The FOMO party is definitely the place to be. Don’t miss your chance to attend THE afterparty at RSA, register now.
It’s a known fact that everyone is moving to the cloud. The conversation has shifted from the “battle” to the transformation of the cloud. The largest benefit of moving to the cloud is security, and the advantages are clear compared to the on-premise environments. This session, led by Orcale’s Senior Vice President David Cross, will cover not only the advantages, but more importantly how to compare and evaluate the on-premise security posture to the next generation SaaS cloud environment in a detailed framework.
For anyone attending RSA interested in SaaS security, or even those who are not, these 7 activities are sure to provide insights into today's market and available solutions. Make sure to visit booth #1449 to experience the Adaptive Shield Fun Fair and try your hand to win a carnival-worthy prize. Also, schedule a meeting with one of our experts for a customized look into how you can gain control over your SaaS stack . We look forward to seeing you there!


Microsoft is a primary target for threat actors, who scour Microsoft applications for weaknesses. Our security research team at Adaptive Shield recently discovered another new attack vector caused by a vulnerability within Microsoft’s OAuth application registration that allows attackers to leverage Exchange's legacy API to create hidden forwarding rules in Microsoft 365 mailboxes.
To understand this new attack vector, you must understand the key components therein. These include hidden forwarding rules and SaaS-to-SaaS app access, all of which amount to a malicious SaaS rootkit that can infiltrate users' accounts and control their mailboxes — without the users' knowledge.
Inbox rules are actions that occur based on preset conditions within a Microsoft mailbox. Users or admins can use forwarding rules to trigger protocols based on different attributes of the user's inbox.
Hidden forwarding rules (Figure 1) were first discovered by Compass Security’s Damian Pflammater in 2018. He covered the discovery and Microsoft’s response in a blog post titled “Hidden Inbox Rules in Microsoft Exchange.” These rules are fully functional and can be seen on the backend. However, they are not visible common interfaces such as email clients, an admin dashboard, or an API (Figure 2).


SaaS-to-SaaS app access, also referred to as third-party app access, describes the conditions under which one app can connect to another app and, in doing so, gain access and permission to different information and settings. The OAuth 2.0 mechanism simplifies the process of authentication and authorization between consumers and service providers through a seamless process that allows users to quickly verify their identities and grant permissions to the app. The app is then allowed to execute code and perform logic within its environment behind the scenes.
In many instances, these apps are completely harmless and often serve as a valuable business tool. In other instances, these apps can act as malware, similar to an executable file.

With this SaaS rootkit, threat actors can create malware that lives as a SaaS app and can infiltrate and maintain access to a user’s account while going unnoticed.
While bad actors can't find Exchange Legacy scopes that can be used to add programmatically online hidden forwarding in the Microsoft UI, they can add them through a terminal script.
The attacker's job is simple: Create an app that looks credible, add the legacy scope protocols removed from the UI to the app (exploiting the vulnerability that the Adaptive Shield team uncovered), and send an offer to users to connect to it. The user will see an OAuth app dialog box on the official Microsoft site, and many will likely accept it (Figure 4).

Once a user accepts, the bad actor receives a token that grants permission to create forwarding rules and hides them from the user interface like a rootkit.
An attack through these hidden forwarding rules should not be mistaken for a one-off attack but, rather, the start of a new attack method through SaaS apps.
In 2022, Adaptive Shield contacted Microsoft about the issue, Microsoft in response said that the issue has been flagged for future review by the product team as an opportunity to improve the security of the affected product.
There's no bullet-proof way to eliminate SaaS rootkit attacks but there are a few best practices that can help keep organizations more protected.
Hidden forwarding rules are still a threat, even more so when they appear through the trusted Microsoft website. The traditional controls that were created to stop malware have struggled to keep up with the evolution of malware and the new attack vector that can exploit any SaaS app, from M365 to Salesforce to G-Workspace, etc. Organizations should utilize native security configurations to control the OAuth application installations across SaaS apps to protect users from malicious attacks like these.


The National Institute of Standards and Technology (NIST) is one of the standard-bearers in global cybersecurity. The U.S.-based institute’s cybersecurity framework helps organizations of all sizes understand, manage, and reduce their cyber-risk levels and better protect their data. Its importance in the fight against cyberattacks can’t be overstated.
While NIST hasn’t directly developed standards related to securing the SaaS ecosystem, they are instrumental in the way we approach SaaS security.
NIST recently released its Guide to a Secure Enterprise Network Landscape. In it, they discuss the transformation from on-premise networks to multiple cloud servers. Access to these servers, and the accompanying SaaS apps, is through both secure and unsecured devices and locations across disparate geography.
The move to the cloud has effectively obliterated the network perimeter. As a result, companies have increased their attack surface and are experiencing an escalation of attacks that span across network boundaries.
Rather than focus on network-centric security, security must take a three-pronged approach. The user, endpoint, and application are keys to protecting data. This new paradigm emphasizes the importance of identity, location, and contextual data associated with the user, device, and service.
Today’s security tools need to scale to meet the volume, velocity, and variety of today’s applications. They need to integrate seamlessly with SaaS applications and provide coverage for the entire SaaS stack.
To be effective, these tools need to minimize human intervention for monitoring and remediation. Automation is critical for an ecosystem that demands secure configurations for each user account that has access to the application. Large organizations may have millions of configurations to secure across their entire SaaS stack; closing them manually is an impossible task.
SaaS security tools must be able to integrate with all the apps on the stack and identify each application through the SaaS app’s APIs. Once connected, it must monitor the security configurations, staying alert to any changes. This configuration drift can have severe consequences, as it exposes SaaS applications by removing the safeguards put in place to prevent unauthorized access. It needs to continuously monitor applications, and issue alerts as risk increases.

Effective SaaS security tools use contextual data to detect threats to the application and its data. These threats can come from humans and machines and may have access to the system using verified credentials.
Contextual data from across the SaaS stack can help identify paradoxical travel, spikes in failed authentication attempts from the same IP address for multiple accounts, or attempts where automated tools test weak and common passwords against known user names. It can also recognize malicious third-party applications that are significantly overprivileged for their functionality.

In the world of SaaS, the devices represent the network perimeter. Accessing SaaS applications with devices that have poor hygiene can put all the data at risk. Compromised devices can hand over login credentials to threat actors, who can leverage that into breaching and stealing data.
Effective SaaS security tools partner with endpoint security providers to ensure that the devices that access SaaS apps have an up-to-date operating system, all software has been updated, and any patches have been applied.

While devices may be the perimeter, user ID is the barrier preventing unfettered access to company data. Access should be given using a zero-trust approach. All access should be granted through an SSO connected to an enterprise-managed IdP. Organizations should reinforce this entryway with a phishing-resistant MFA authenticator.

Effective SSPM platforms are built on robust security checks that review each SaaS configuration to ensure they are optimized for protection. Typically, security setting recommendations are influenced heavily by NIST’s cybersecurity approach, and their guidance enables SSPM vendors to monitor and track usage, users, and behaviors, as well as identify threats.


Spoiler Alert: Organizations with 10,000 SaaS users that use M365 and Google Workspace average over 4,371 additional connected apps.
SaaS-to-SaaS (third-party) app installations are growing nonstop at organizations around the world. When an employee needs an additional app to increase their efficiency or productivity, they rarely think twice before installing. Most employees don't even realize that this SaaS-to-SaaS connectivity, which requires scopes like the ability to read, update, create, and delete content, increases their organization's attack surface in a significant way.
Third-party app connections typically take place outside the view of the security team, are not vetted to understand the level of risk they pose.
Adaptive Shield's latest report, Uncovering the Risks & Realities of Third-Party Connected Apps, dives into the data on this topic. It reviews the average number of SaaS-to-SaaS apps organizations have, and the level of risk they present. Here are the top 5 findings.
The report focuses on Google Workspace and Microsoft 365 (M365), as it paints a clear picture of the scope of applications that are integrating with the two applications.
On average, a company with 10,000 SaaS users using M365 has 2,033 apps connected to its suite of applications. Companies of that size using Google Workspace have more than three-times the amount, averaging 6,710 connected applications.
Even smaller companies aren't immune. The report found that companies using M365 average 0.2 applications per user, while those using Google Workspace average 0.6 applications per user.
In contrast to most growth curves, the research shows that the number of apps per user doesn't level off or plateau once reaching a critical mass of users. Rather, the number of applications continues to grow with the number of users.
As seen in figure 1, companies using Google Workspace with 10,000-20,000 employees average nearly 14,000 unique connected applications. This continued growth is shocking to security teams, and makes it nearly impossible for them to manually discover and manage the high volume of applications.

When third-party apps integrate with core SaaS apps, they gain access using an OAuth process. As part of this process, applications request specific scopes. These scopes hand over a lot of power to the apps.

Among high-risk scopes, 15% of M365 applications request the authority to delete all files that the user can access. It gets even scarier in Google Workspace applications, where 40% of high-risk scopes receive the ability to delete all Google Drive files.
As shown in this permission tab, the application explicitly requests permission to see, edit, create, and delete all Google Docs documents, Google Drive files, Google Slides presentations, and Google Sheets spreadsheets.
For security teams accustomed to controlling the data, permission sets like these are unsettling. Considering that many applications are created by individual developers who may not have prioritized security in their software development, these permissions provide threat actors with everything they need to access and steal or encrypt company data. Even without a threat actor, a bug in the software can have disastrous consequences for a company's data.
While the report deep dives into the big two SaaS apps, it does also release research into Salesforce (and Slack). Salesforce averages 41 integrated apps per instance. The implication of this is noteworthy.
Salesforce is primarily used by a small subset of the company. In that regard, it's similar to Workday, Github, and ServiceNow, which are used by HR, developers, and finance teams. A typical company with 10,000 employees has over 350 SaaS applications in its stack, many of which are used by smaller departments like the apps discussed here.
Assuming Salesforce is typical of similar applications, those 350 apps integrating with 40 apps each adds an additional 14,000 third-party applications into the equation.
One of the more interesting takeaways was the high volume of high-risk apps connecting to Microsoft compared to Google Workspace. Apps request high-risk permissions from M365 39% of the time; Google Workspace apps only request high-risk permissions 11% of the time. In terms of real numbers, an average installation in a company with 10,000 SaaS users using M365 will have 813 high-risk apps, while Google Workspace will have 738 apps that are considered high-risk.
In all likelihood, this disparity is caused due to the app creation process. Google requires apps requesting high-risk (it calls them Restrictive) permissions to be reviewed. The review process is far easier for those requesting medium, or sensitive, permissions. Microsoft doesn't label requested scopes with severity levels. This lack of oversight makes it much easier for apps that connect with M365 to request high-risk scopes.
The overall takeaway from reading the report is the immense challenge of securing SaaS software. It's clear that security teams need visibility into the thousands of apps being connected to the SaaS stack, and make a cost-benefit analysis for each high-risk connected app.
SaaS security solutions, like Adaptive Shield, provide security teams with the visibility needed to see connected applications and their scopes, among other important SaaS security capabilities. Armed with this information, security teams will be in a far better position to harden their applications' security posture and prevent data from falling into the wrong hands.


Tel Aviv, February 27, 2023—Adaptive Shield, the leading SaaS Security company, today announced the release of its SaaS-to-SaaS Access Report. According to the research, employees are granting thousands of third-party apps access to the two most dominant workspaces, Microsoft 365 (M365) and Google Workspace. With no oversight or control from security teams, companies have no way to quantify the risk that these SaaS-to-SaaS connections present to their businesses.
While these SaaS-to-SaaS connections provide enhanced features that boost workflow efficiency, they also give permission for apps to read, update, create, delete, or otherwise engage with corporate and personal data. In its report, Adaptive Shield identifies how many SaaS apps are being connected to the core SaaS stack, specifically M365 and Google Workspace and business-critical apps such as Salesforce and Slack, the types of permissions being granted to these applications, and the risk level these apps present.
According to the research, companies with 10,000 SaaS users average 2,033 applications connected to M365 and 6,710 connected to Google workspace. For the companies using Google Workspace, that figure jumps to an average of 13,913 connected apps for 10,000 - 20,000 SaaS users.
While the risk level for permissions varies from one app to the next, Adaptive Shield researchers found that 39% of apps connected to M365 and 11% to Google Workspace have ‘high-risk’ permission access. Additional details on these include
“The simple app-to-app connectivity that makes SaaS apps vital productivity tools also makes them significantly dangerous,” said Maor Bin, CEO of Adaptive Shield. “While it’s clearly unrealistic to expect businesses to curb their reliance on SaaS apps, they cannot allow this adoption to go unchecked. To eliminate these risks companies must develop policies for integrating apps, prioritize employee training, and deploy monitoring solutions that help over-taxed security teams identify and eliminate high-risk permission sets before it’s too late.”
While these challenges are most prominent in M365 and Google Workspace, they are not exclusive to these apps. As part of this effort, Adaptive Shield examined two other business-critical apps, Slack and Salesforce. The research shows that organizations have an average 222 SaaS-to-SaaS apps for Slack and another 41 apps for Salesforce.
A final area of research are app categories that are connected most frequently. According to the research, email applications are far and away the number one connected category followed by apps related to file and document management, communications and meetings, and calendars and scheduling.
The Adaptive Shield full report, 2023 SaaS-to-SaaS Access Report: Uncovering the Risks & Realities of Third-Party Connected Apps, is available now.


When SaaS applications started growing in popularity, it was unclear who was responsible for securing the data. What's far murkier, however, is where the data responsibility lies on the organization's side. For large organizations, this is a particularly challenging question. They store terabytes of customer data, employee data, financial data, strategic data, and other sensitive data records online.
SaaS data breaches and SaaS ransomware attacks can lead to the loss or public exposure of that data. Depending on the industry, some businesses could face stiff regulatory penalties for data breaches on top of the negative PR and loss of faith these breaches bring with them.
Finding the right security model is the first step before deploying any type of SSPM or other SaaS security solution.
There are several different groups of players involved in the SaaS security ecosystem.
SaaS App Owners – When business units subscribe to SaaS software, someone from within the business unit is typically responsible for setting up and onboarding the application. While they may have some help from IT, the application is their responsibility.
They choose settings and configurations that align with their business needs, add users, and get to work. SaaS App Owners recognize the need for data security, but it isn't their responsibility or something they know very much about. Some mistakenly assume that data security is only the responsibility of the SaaS vendor.
Central IT – In most large organizations, Central IT is responsible for things like infrastructure, hardware, and passwords. They manage IDP and servers, as well as oversee help desk activities. SaaS applications typically do not fall under their direct domain.
Central IT is more familiar with security requirements than the average employee, but it isn't their primary concern. However, it is important to keep in mind that they aren't security professionals.
Security Teams – The security team is the natural fit for implementing security controls and oversight. They are tasked with creating and implementing a cybersecurity policy that applies across the organization.
However, they have several challenges inhibiting their ability to secure applications. For starters, they are often unaware of SaaS applications that are being used by the company. Even for applications that they are aware of, they lack access to the configuration panels within the SaaS stack, and aren't always aware of the unique security aspects associated with each application. Those are controlled and maintained by the SaaS App Owners and Central IT.
GRC Teams – Compliance and governance teams are tasked with ensuring that all IT meets specific security standards. While they don't play a specific role in securing corporate assets, they do have oversight and need to determine whether the company is living up to its compliance responsibilities.
SaaS Vendor – While the SaaS vendor is absolved from any responsibility to secure the data, they are the team that built the security apparatus for the SaaS application, and have a deep knowledge of their application and its security capabilities.
Securing the entire SaaS stack requires close collaboration between the security experts and those managing and running their individual SaaS applications. We developed this RACI chart to share our perspective on the departments that are responsible, accountable, consulted, and informed for the different tasks involved in securing SaaS data.
Bear in mind, this table is not one size fits all, but a framework based on the way we see many companies handling their SaaS security roles. It should be adapted to the needs of your organization.

Developing the RACI matrix is important, but without the right tools in place, implementing security responsibilities becomes a near-impossible task.
Adaptive Shield’s SSPM platform facilitates clear communication between the security team and app owners. This communication includes alerts when misconfigurations occur that weaken the individual app’s security posture and when threats are detected by our IAM governance tools.
Communication is channel agnostic, so users can receive messages and alerts over email, Slack, Splunk, or the messaging platform of choice. All security-related notifications include remediation steps, providing app owners and central IT with a clear understanding of the steps required to mitigate the risk.
Within the platform, app owners have visibility and access to the app or apps under their control. They can see the status of their security settings, their security score, their users, third-party SaaS applications that are connected to their app, and the devices being used to access their SaaS app.
App owners and central IT are also able to dismiss a security alert due, either because it doesn’t apply or due to business needs, and consult with the security team on risk.
It’s easy for SaaS application security to be overlooked. It sits outside the view of the security team and is managed by competent professionals whose responsibilities don’t include security.
However, the data contained within the SaaS applications are often the lifeblood of an organization, and failure to secure the data can have disastrous consequences.
Fully protecting the data from exposure requires a cross-team effort and commitment from all parties involved, as well as a sophisticated SSPM platform built for SaaS in the real world.
.png)
.png)
Security teams can’t protect every byte within their digital footprint. Limited resources mean making choices, and so security teams run assessments to evaluate the value of their assets, the cost to protect those assets, and the damage to the company should an asset be breached or compromised.
In some industries, regulatory requirements shape those decisions, while other industries can be determined based on organizational needs.
The assessment frequently leaves SaaS applications, and the data they contain outside of the company’s protective shield. Organizations often believe the data stored within SaaS applications is less sensitive than other corporate IP and accept that the security tools built into the SaaS app are strong enough to provide adequate protection.
In a sense, those assessments are right. Most SaaS apps don’t contain the company's crown jewels, and nearly every SaaS application comes with a robust security tool set that should protect all the data within the SaaS app. Unfortunately, that view is leaving critical data exposed online, putting organizations at risk of data exposure, ransomware, and regulatory fines.
Companies store some of their most important data within SaaS applications.
Salesforce stores all company leads, its sales pipeline, and customer data. Sharepoint contains critical files and work product. Bamboo HR stores employee data. GitHub contains software code. Netsuite stores key financial documents. Google Workspace and Microsoft 365 contain files and email.
Organizations’ tech stacks are comprised of applications like these. Failing to secure the data would represent a significant loss to a company. Depending on the nature of the attack, all data stored within the application could be lost forever, shared with competitors, or held for ransom.
Generally speaking, there are three motivations for an attack on a SaaS app. Threat actors want to steal data, steal money, or sabotage a company. Each of these attack types manifests itself in different forms. A grab for data, for example, might involve threat actors remaining in the shadows while playing the long game, while a saboteur or ransomware attack would involve different styles of attack.
When SaaS applications are left unprotected organizations can quickly find themselves dealing with a large scale SaaS security incident.
Data theft often involves competitors accessing a SaaS application and downloading critical company information. Threat actors need to gain credentials to access the SaaS, and then move laterally to increase their access and find the intellectual property they crave. Once they find the data, they tend to download it slowly to avoid raising any security flag.
These attacks can be difficult to detect, considering that the perpetrators are often authorized or former employees. Companies that recently laid off employees or are involved in negative news stories are at higher risk of sabotage.
Like all SaaS apps, security begins with access management. Organizations should be especially careful with high-privilege dormant accounts, such as those accounts that were used for setup but have been dormant or accounts shared by multiple users. Access must also be removed for employees that have been let go.
These accounts, if left active, offer pathways to sensitive data without any way for security teams to know which current or former user is accessing them.
Most don’t usually associate ransomware with SaaS applications. Today, we are seeing an increase in these types of attacks. SaaS data is accessed through a user account or malicious app, and then encrypted pending the payment of a ransom.
These ransomware attacks often carry a secondary attack mode, particularly when the compromised SaaS app contains PII data or involves highly regulated industries. In addition to encryption, the threat actor threatens publishing the data online. In these nightmarish scenarios, organizations are motivated to pay the ransom to protect themselves from negative PR and regulatory penalties for failing to adequately protect the data they collected.
For the most part, the security configurations on SaaS applications are sufficient to secure the data contained within the application. In a perfect world, those configurations would be set once, securing the apps and the data within against nearly all threats.
However, SaaS configurations are often adjusted by users trying to enhance functionality or improve accessibility. Configuration drift leads to vulnerabilities, which creates an opening for threat actors to take advantage. Third-party applications, which are connected to SaaS applications and granted scopes enabling them to delete records, send emails, and add new data, increase the attack surface.
Lacking visibility, the security team has no way of knowing whether SaaS applications have retained their secure posture over time, or whether a malicious third-party application has been inadvertently connected to a business-critical application.
SaaS Security Posture Management (SSPM) with SaaS threat detection automates security checks and provides the visibility needed for every third-party app. It enables security teams to detect threats against data and respond appropriately against imminent threats. Adding SSPM to your security stack is vital in securing SaaS-based critical data.


Adaptive Shield has partnered with Datadog, the observability service for cloud-scale applications, to provide joint customers with the ability to stream and visualize SaaS security alerts from Adaptive Shield.
Adaptive Shield continuously monitors all SaaS apps, users, and associated devices, the platform immediately identifies, alerts, auto-fixes or provides actionable remediation information when any misconfiguration or security drift happens.
Datadog continuously monitors cloud applications, providing unified, real-time observability of customers’ entire technology stack including end-to-end traces, metrics, and logs. These originate from applications, infrastructure, and third-party services. These capabilities help businesses secure their systems, avoid downtime, and ensure customers are getting the best user experience.
Gilad Walden, VP of Product at Adaptive Shield asserts, “This partnership enables security teams to gain visibility, prioritize, and respond to SaaS Security configuration drifts reported by Adaptive Shield’s platform, within the Datadog dashboard”. Gilad continues, “This allows for an easy and streamlined incident management for all connected SaaS apps.”

This integration is one of the first OAuth integrations of Datadog with the added benefits of not having to enter API keys or application keys, reducing the risk of sensitive data leaks and simplifying the user experience.
How to Integrate

Once integrated, alerts are streamed into Datadog as Events and a dashboard is generated in Datadog for visualized alert analysis.


The move to SaaS and other cloud tools has put an emphasis on Identity & Access Management (IAM). After all, user identity is one of the only barriers standing between sensitive corporate data and any unauthorized access.
The tools used to define IAM make up its identity fabric. The stronger the fabric, the more resistant identities are to pressure from threat actors. However, those pressures are only increasing. Decentralized IT, evolving threats, and zero-trust tools are pushing many IAM tools to their limits.
To maintain their effectiveness, IAM are shifting to operating as an agile, interconnected identity fabric rather than just siloed IAM tools. The demands of today's IT operating environment are forcing IAM to support decentralized IT environments while still providing centralized management and governance for its users.
Interestingly, many of the identity fabric principles they define are currently found in leading SSPM tools. It's important to note that identity fabric isn't composed of a single tool. Rather, a number of different tools, including directories, authentication, and threat detection, come together to form an enforceable IAM perimeter.
The scope of identity fabric includes any human, machine, or application that is granted access to your applications and data. Looking at this through an SSPM lens, your platform should be able to track all access to your SaaS applications and alert you whenever dangerous or suspicious entities or malicious applications access your SaaS stack.
This extends beyond humans and covers the devices they use to access their data. As we look ahead into the near future, it also includes connected devices which may require access to perform their tasks.
Traditional IAM solutions were siloed. Over time, organizations recognized the need to centralize IAM to enable governance and policy management that applied to the entire network.
Today's work environment demands both centralized control and decentralized enforcement so that SaaS applications adhere to the same identity policies that are required to access other corporate assets.
SSPM plays a key role in identity fabric, centralizing identity governance in a single user inventory that is applied to all SaaS apps using data from within each SaaS that goes beyond traditional IAM solutions.
Identity security must be adaptive, ongoing, risk-aware, resilient, and use-case appropriate. SSPM platforms contribute to an organization's overall identity fabric by reviewing compliance against industry standards and ensuring that all identity-centric security checks are configured correctly.
SaaS environments are incredibly dynamic, and require identity tools with the flexibility and agility to keep up with demands. SSPMs are remarkably adept at staying on top of SaaS identity-based changes, supporting new users and new applications.
SSPM plays a critical role in identity-based threat detection. While individual SaaS apps lack sign-in context, SSPM captures user login information from all applications. It provides a tremendous level of context to better understand user behaviors that may threaten SaaS security.
SSPMs can also track user behavior based on user identification, looking for behavioral patterns. When it detects suspicious anomalies in behavior, such as downloading large volumes of data, it also triggers an alert to the SOC team.
Third-party applications are often granted privileges that could compromise data privacy. SSPMs use identity-based tools to recognize these applications and alert security teams when they are engaging in high-risk behavior.
The core strength of an SSPM, like Adaptive Shield's, lies in the visibility it provides to security teams and application owners. Its ability to identify misconfigurations, shadow IT applications, and devices make it an integral part of any SaaS-centric security strategy.
However, its ability to identify and track users makes it an important thread in identity fabric. Its broad scope across multiple applications, centralized location, and ability to flag suspicious behaviors and associate them with an identity cannot be understated. Organizations looking to stitch together a robust, resilient identity fabric would be well served to explore the identity governance benefits inherent in SSPM.
This is an excerpt from an article that was published in The Hacker News on Jan 23, 2023.


Earlier this year, threat actors infiltrated Mailchimp, the popular SaaS email marketing platform. They viewed over 300 Mailchimp customer accounts and exported audience data from 102 of them. The breach was preceded by a successful phishing attempt and led to malicious attacks against Mailchimp's customers' end users.
Three months later, Mailchimp was hit with another attack. Once again, an employee's account was breached following a successful phishing attempt.
While the identity of the Mailchimp accounts that had been compromised wasn't released, it's easy to see how user permission settings could have played a role in the attack. Once threat detectors breached the system, they had the access needed to utilize an internal tool that enabled them to find the data they were looking for. The attack ended when security teams were able to terminate user access, although data which had already been downloaded remained in the threat actor's hands.
Introducing user permissions, through role-based account control (RBAC), could have severely limited the damage caused by the breach. Had the rule of least privilege been applied, it's likely that the breached account would not have afforded access to the internal tools that were used in the attack. Furthermore, reduced access might have completely prevented the attack or limited the number of affected accounts to far fewer than the 100 which were ultimately compromised.
SaaS user permissions allow app owners to limit a user's resources and actions based on the user's role. Called RBAC, it is the permission set that grants read or write access, assigns privileges to high-level users, and determines access levels to company data.
The rule of least privilege is an important security concept that provides the least amount of access needed for users to perform their job functions. In practice, it reduces the attack surface by limiting high-level access to a few privileged individuals. If a low-privilege user account is breached, the threat actor would have less access to sensitive data contained within the application.
App administrators frequently grant full access to team members, particularly when dealing with a small user group. As business users rather than security professionals, they don't always recognize the degree of risk in granting those access permissions. Furthermore, they prefer to give full authorization rather than be asked for specific permissions later on.
Unfortunately, this approach can put sensitive data records at risk. User permissions help define the exposed data in the event of a breach. By protecting data behind a permission set, threat actors that access a user identity are limited to the data available to their victim.
Loose user permissions also make it easier for threat actors to carry out automated attacks. Having multiple users with wide API permissions makes it easier for cybercriminals to breach a SaaS app and either automate ransomware or steal data.
User access reviews are essentially audits that look at users and their access. They show security team members and app owners the degree of access each user has and allows them to adjust permission levels as needed.
This is important, as it helps identify users who may have switched roles or teams within the company but retained an unnecessary level of permissions, or alerts security teams regarding employees whose actions have deviated from normal behaviors to include suspicious behavior. Furthermore, it helps identify former employees who still have access and high-privilege permissions.
Access Reviews should take place at predetermined intervals, ensuring that unnecessary permissions are identified within a set time frame.
User permissions are often a misunderstood security feature. It protects organizations from both external attacks and internal data-sharing errors.
An SSPM solution enables effective user permission management, giving security personnel and app owners the confidence to know the extent of any user permission and see that user's SaaS security hygiene. This real-time view of users is far more effective than User Access Audits, which only present a snapshot view of the users' permissions at a specific moment in time.


Nissan North America is informing customers of a data breach that occurred at a third-party service provider. The security incident was reported to the Office of the Maine Attorney General on January 16, 2023, and it was disclosed that almost 18,000 customers were affected by the breach. According to the notification, Nissan received notice of the data breach from one of its software development vendors on June 2022. The vendor had received customer data from Nissan to use in developing and testing software solutions, which was inadvertently exposed due to a poorly configured cloud-based public repository.
Nissan took immediate action to secure the exposed repository and launched an internal investigation. It was determined that an unauthorized person had likely accessed the data. The exposed data includes full names, dates of birth, and Nissan account numbers, but does not include credit card details or Social Security numbers. Nissan says that to this date, there has been no evidence that any of this information has been misused.
There are two key lessons to learn from the incident. The first is the recurring lesson about the importance of securing repository access (such as GitHub, GitLab, Bitbucket, and more). Just last week we published a blog post covering the breach of Slack’s GitHub repositories. In the case of the 3rd party vendor Nissan used, the issue is even simpler than the previous ones –- organizations must make sure that private repositories used for code development and testing stay private, and only open repositories (such as sharing back to the community) should be public. Security teams must constantly monitor and evaluate which repositories are open, and who should have access to other repositories. Any changes to the visibility of a repository should be alerted, logged, and evaluated by the security team.

Figure 1. Changing repository settings in Github
The second is the use of real customer data for development and testing purposes. This should be discouraged, and instead, use synthetic data mimicking the real data. In my previous blog post, Not All Sandboxes Are for Children: How to Secure Your SaaS Sandbox this was discussed in depth. The main problem is that many times, for no good reason, test environments are not considered as important to secure and keep good configuration hygiene compared to a production environment. But time and time again this is shown to be an Achilles' heel. Many times real data is used in such environments and combined with low security and minimum safeguards, leads to data leakage.
The impact of such a breach is considerable. Not only was sensitive customer data stolen, but Nissan needed to publicly send out notifications, report it to the Office of the Maine Attorney General, and also gave all the affected customers a one-year membership of identity protection services through Experian for free.
You can protect your organization by securing your repository and making sure all repositories that need to be private stay private. Additionally, treat test environments just like production environments from a security standpoint. These are measures that, if done correctly, and with the aid of automatic tools, can keep your organization and customer data secure.


On average, organizations report using 102 business-critical SaaS applications, enabling operations of most departments across an organization, such as IT and Security, Sales, Marketing, R&D, Product Management, HR, Legal, Finance, and Enablement. An attack can come from any app, no matter how robust the app is.
Without visibility and control over a critical mass of an organization's entire SaaS app stack, security teams are flying blind. This is why it's important that all SaaS apps across the organization be managed at scale.
While this breadth of coverage is critical, each app has its own characteristics, UI, and terminology. Mitigating these threats requires a deep understanding of all security controls its configurations.
Security teams need to map out the entire SaaS ecosystem within the organization, including the core SaaS apps and the numerous additional apps that employees connect to without checking or informing the security team.
Each of these apps needs to be governed in Identity & Access, ensuring:
If these checks are not enough for security teams to handle, they also need to check the device posture of all their SaaS users to map risks.
SaaS Security Posture Management (SSPM) is the only solution that can automate misconfiguration management, monitor SaaS-to-SaaS access, harden identity and access governance, and manage SaaS risks stemming from user devices — for all apps and all users.


Over the last year, we’ve seen increasing evidence of an upcoming recession. Interest rate hikes and inflation, energy uncertainty, and the war in Ukraine are all harbingers of rough times ahead. CNBC reported that more than 50,000 employees from Twitter, Meta, Amazon, Salesforce, and other tech companies lost their jobs in November. While no one knows exactly what 2023 will bring to the labor market, organizations need to be prepared for potential downsizing.
Removing user access for employees who no longer require access to company SaaS applications should be fairly straightforward. Most companies will disable users from their active directory and expect those users to be automatically removed from every application they have access to.
That works well when the SaaS app was set up with an SSO. However, many SaaS apps aren’t set up with an SSO. When users are removed from the IDP, they retain their login credentials.
Furthermore, many high-privilege users have extra accounts that are not managed within the IDP. This particularly applies to admins and app owners. Those users retain their high-privilege access, which can put all the data within the application at risk.
When SaaS applications are created, the install team typically creates multiple testing user accounts that are not associated with an IDP. These accounts are granted various levels of access, depending on the functionality or activity being tested. Often, these accounts are given names that are easy to remember, and since the account may be shared by multiple users, passwords are often a simple phrase or number pattern that is easy to share and remember. After setup is completed, these accounts are dormant but can be used to provide access.
Additionally, teams will often share a single user license among multiple employees. Again, these accounts are frequently high-privilege with easy-to-remember passwords, simplifying the team’s ability to get their work done.
These dormant and shared high-privilege accounts represent a significant threat during periods of downsizing. Former employees can use them to easily access corporate SaaS apps and sabotage or steal corporate IP. During periods of downsizing, security should be tightened to include reviewing permissions of these types of accounts, rotating passwords, and limiting shared accounts to situations where it is the only option.
User accounts are also frequently given to external users. As teams collaborate with vendors and partners, it’s more efficient to provide access to the system rather than have employees copy, paste, and email data to their partners. While some accounts are limited through RBACs, often times partner and vendor accounts have full access.
These external user accounts always create a degree of risk for organizations. However, when employees are let go and vendors lose their connection to the company, the risk level increases. Unaffiliated third-party vendors and partners may share data with competitors The only thing standing between company data and the public internet are login credentials. Company and customer data may be stolen, leaked, or shared with competitors.
User inventories provide a complete account of each user in every SaaS system. These were easy to assemble when everything was done on-premises. However, the transition to the cloud and SaaS applications has decentralized user data and limited the view of security personnel.
An effective user inventory would enable security teams and SaaS app owners to find and disable these types of accounts, eliminating the threat they pose following layoffs.
The inventory should be the single source of truth for everything a security team needs to know about a user. It should include login names the user may use on different applications, mulitple login names a high-privilege user might have for a single app, the applications that they can access, and the level of privilege they have within the application. It is vital to disable every access credential once an individual is no longer part of the organization.
However, the user inventory also needs to include test accounts, shared accounts, and external user accounts. Security personnel should be able to see which accounts are not using corporate IDP, the last date the account accessed the system, and access roles that are available to the user account. With that information in hand, security teams and app owners can make an informed decision as to whether these accounts represent a threat and need their access removed or limited.
Downsizing can be traumatic for a company and its employees, but is usually done to protect the long-term interests of the organization. Ensuring that data remains safe throughout this challenging period is not an easy task, but with the right tools in place, security teams and app owners can ensure the integrity and security of their SaaS.


Earlier today, a story broke that GitHub repositories of Slack were breached over the holiday weekend. Slack detected the breach after noticing suspicious activity, and in their investigation found that stolen Slack employee tokens were the source of the breach.
As a result of the attack, private Slack code repositories were downloaded, but no customer data was exposed.
While Slack is in the news today, they are definitely not the first, and will not be the last. Among the numerous breaches thus far, the Dropbox breach consisting of 130 Dropbox GitHub repositories is noteworthy. This was done using credentials that were stolen in a phishing attack, the current method of choice for bad actors. This also was discovered by noticing suspicious activity. GitHub itself has fallen victim to a breach that resulted in stolen repositories using stolen OAuth user tokens issued to two third-party OAuth integrators – Heroku and Travis-CI.
These breaches show how important it is to secure repositories. This is even more true in the modern cloud-based world where repositories are hosted within SaaS platforms for managing Git – such as GitHub, GitLab, Bitbucket, and others. These repositories are the keys to the kingdom. Sometimes repositories include databases of customers, patients, assets, and other sensitive data. This type of breach is a disaster for any company.
Once accessed, the attacker has an intimate understanding of how the product was built and can use that information to compromise the product in follow-up attacks.
To protect against such attacks, organizations should follow these security measures:

As seen in the incidents mentioned above, monitoring is key. Make sure to enable audit logs and consume them to gain visibility to user actions, in addition to having tools, like a SaaS Security Posture Management solution (SSPM), for threat detection.
These are just some of the many methods, tools, and configurations that should be used to secure access to a repository. In addition, employees should be trained to detect phishing and keep their credentials safe and secure.
A breach of a repository in a Git SaaS is not a force majeure. With proper security tools and training the risk can be reduced drastically.


Business leaders may fear an upcoming recession, but they fear falling behind their competitors even more. PwC’s November Pulse Survey found that 35% of executives are planning an acquisition or divestiture within the next 12-18 months. M&A has proven itself to be a key to business resurgence, strategic growth, and capability expansion.
One area that’s often overlooked during M&A due diligence is a target company’s SaaS landscape. These applications, which host tremendous amounts of sensitive company and customer data on the cloud, are often left unsecured through misconfigurations, orphan user accounts, and third-party applications with high permission sets.
While SaaS applications are secured by the app developer, the data within them can be easily exposed. Most large organizations have over 40 million toggles, switches, and checkboxes across their SaaS landscape that have to be set correctly to prevent data breaches, ransomware attacks, and malware.
Connecting an acquisition target’s SaaS stack to an SSPM can be done easily through existing APIs. Once connected, it takes just minutes to see the target’s SaaS hygiene and evaluate whether risk levels for the data within SaaS apps.
Merging two companies together is always high risk. By connecting an SSPM and looking under the SaaS hood, security analysts can offer their perspective on the merger and the level of risk they are taking on.
Getting ready for M&A? See how Adaptive Shield can protect you from SaaS surprises. Schedule a demo today.


Healthcare has been cautious in moving toward cloud technologies and SaaS applications. Concerns over privacy and the need to comply with HIPAA regulations had left them stuck using on-premises software solutions. However, COVID forced healthcare organizations to develop telehealth models. Patients increasingly wanted digital access to their records, and healthcare organizations recognized the need to meet interoperability mandates.
As patient and industry needs continue to evolve, more healthcare organizations have adopted SaaS apps, evidenced by a predicted SaaS global healthcare market growth of 19.5% between 2021 and 2028. As the industry embraces this shift to the cloud, healthcare security professionals need to understand how SaaS security impacts their Health Insurance Portability and Accessibility Act (HIPAA) compliance posture.
Across the industry, healthcare organizations leverage SaaS applications to streamline patient care and administrative tasks. Meanwhile, the industry faces unique security and compliance concerns.
Cybercriminals target the healthcare industry because they can use protected health information (PHI) in various ways. Some examples of how they use this valuable data include:
Between tight budgets and the cybersecurity skills gap, the healthcare industry often lacks the resources needed to implement security. IT budgets often focus on technologies that enable patient care and administrative functions. Simultaneously, the limited number of skilled security professionals often means that healthcare organizations struggle to find and retain the talent they need.
In January 2022, Congress signed a HITECH Amendment into law that requires the Department of Health and Human Services (HHS) to create standards, guidelines, best practices, methodologies, procedures, and processes for protecting ePHI. In response, the HHS Office for Civil RIght (OCR) recommended the Health Industry Cybersecurity Practices: Managing Threats and Protecting Patients (HICP) publication and the National Institute of Standards and Technology Standards (NIST) Cybersecurity Framework (CSF).
HICP outlined the following ten most effective Cybersecurity Practices:
As healthcare organizations adopt more SaaS applications, their security teams find that manually managing HIPAA compliance becomes overwhelming. For example, many organizations struggle with:
As the healthcare industry adopts more SaaS applications, security professionals need to manage the three primary HIPAA compliance pain points associated with them:
SSPM solutions enable covered entities and business associates to monitor their SaaS environments and enforce security policies.
SSPM solutions solve the IT, security, and privacy SaaS misconfiguration challenges by offering:
Implementing the right SSPM solution enables covered entities and business associates to enforce security configurations across their SaaS ecosystem. As organizations research SSPM solutions, they need to consider the technology’s capabilities and functionalities. With the right SSPM, organizations gain continuous, automated surveillance of all SaaS apps and the documentation supporting their HIPAA compliance posture.


With 2022 coming to a close, there is no better time to buckle down and prepare to face the security challenges in the year to come. This past year has seen its fair share of breaches, attacks, and leaks, forcing organizations to scramble to protect their SaaS stacks. March alone saw three different breaches from Microsoft, Hubspot, and Okta.
With SaaS sprawl ever growing and becoming more complex, organizations can look to four areas within their SaaS environment to harden and secure.
Enterprises can have over 40 million knobs, check boxes, and toggles in their employees’ SaaS apps. The security team is responsible to secure each of these settings, user roles and permissions to ensure they comply with industry and company policy.
Not only because of their obvious risk or misalignment with security policies, misconfigurations are overwhelmingly challenging to secure manually. These configurations can change with each update, and their complexity is compounded by the many compliance industry standards. Adding to that challenge, SaaS app owners tend to sit in business departments outside the security team’s scope and are not trained or focused on the app’s security.
Security teams should onboard a SaaS Security Posture Management (SSPM) solution, like Adaptive Shield, that provides full visibility and control across a critical mass of SaaS apps in the SaaS stack. The solution must identify both global app settings and platform-specific configurations within each app. Security teams should be able to use the solution to gain context into security alerts and gain answers to questions like: Which users are subject to a certain misconfiguration? Are they admins? Is their MFA enabled? By having these answers at their fingertips, security teams can enforce company and industry policies to remediate potential risks from any misconfiguration.
Another growing security challenge derives from the increasing volume of apps connected to the company’s SaaS environment. On average, thousands of apps are connected without the approval or knowledge of the security team. Employees connect these apps, often to boost productivity, enable remote work and to better build and scale company's work processes.
However, when connecting apps to their workspaces, employees are prompted to grant permissions for the app to access. These permissions include the ability to read, create, update, and delete corporate or personal data, not to mention that the app itself could be malicious. By clicking "accept," the permissions they grant can enable threat actors to gain access to valuable company data. Users are often unaware of the significance of the permissions they’ve granted to these 3rd-party apps.
Falling in the Shadow IT domain, security teams must be able to discover 3rd party apps and identify which pose a risk. From access scopes requested by these apps, to authorized users and cross referencing, the security team should be able to measure the level of access to sensitive data across the organization’s stack. An SSPM solution like Adaptive Shield, can arm the security team with this type of discovery and control in addition to providing advanced reporting capabilities for effective and accurate risk assessments to drive actionable measures.
Security teams must deal with threats from users accessing their SaaS applications from personal, unsecured devices. Accessing a SaaS app via an unmanaged device poses a high level of risk for an organization, especially when the device owner is a highly privileged user. Personal devices are susceptible to data theft and can inadvertently pass on malware into the organization’s environment. Lost or stolen devices can also provide a gateway for criminals to access the network.
Security teams need a solution that enables them to manage SaaS risks originating from compromised devices. An SSPM solution like Adaptive Shield can identify privileged users such as admins and executives, calculate user-risk levels, and recognize which endpoint devices need to be more secured.

Every SaaS app user is a potential gateway for a threat actor, as seen in the most recent Uber MFA Fatigue attack. Processes to ensure proper users’ access control and authentication settings are imperative, in addition to validation of role-based access management (as opposed to individual-based access) and establishing an understanding of access governance. Identity and access governance helps ensure that security teams have full visibility and control of what is happening across all domains.
Security teams need to monitor all identities to ensure that user activity meets their organization’s security guidelines. IAM Governance enables the security team to act upon arising issues by providing constant monitoring of the company’s SaaS Security posture as well as its implementation of access control.
Gartner called SaaS Security Posture Management (SSPM) in the “4 Must-Have Technologies That Made the Gartner Hype Cycle for Cloud Security, 2021” for solutions that continuously assess security risk and manage the SaaS applications’ security posture. With an SSPM platform organizations can harden their SaaS security to identify and remediate issues faster and prevent future attacks. Security teams can introduce best practices for SaaS security that extend beyond Misconfiguration Management to cover SaaS-to-SaaS Access, Device-to-SaaS User Risk levels, and Identity & Access Management Governance.


The short answer: It’s no secret that in today’s day and age, organizations rely heavily on hundreds of SaaS apps for their day-to-day operations. While SaaS apps include a host of native security settings, they need to be hardened and monitored by the organization’s security team.
SaaS Security Posture Management (SSPM), a category created by Gartner, refers to SaaS security solutions that continuously assess security risk and manage the SaaS applications’ security posture.
The longer answer: Stick around, and we’ll explain why SSPM is important to your organization, its benefits, and the difference between SSPM and some of the other cloud security tools.
SSPM protects data stored in SaaS apps and helps organizations meet compliance requirements through these features:
Organizations require visibility into their entire SaaS stack. The high volume of configurations, user roles, permissions, devices, and third-party apps make it impossible for security teams to secure the apps manually. SSPMs automatically review security settings from all apps in one unified display that can be interpreted easily.
SaaS apps are dynamic and ever-evolving; their speed of change makes them incredibly hard to govern. Apps’ settings need to be continuously modified to accommodate security updates, feature enhancements, and employee provisioning. There are also continuous compliance updates to meet industry standards and best practices (NIST, SOC2, ISO, MITRE, etc.) that need to be checked and modified.
Securing the SaaS stack periodically is far from enough to keep it secure year-round. Non-stop monitoring enables security teams to stay aware of risks in real time.
As the SaaS landscape widens, so does the SaaS attack surface. Organizations need a comprehensive SaaS security solution to prevent data theft, encryption, or sabotage.
Among others, an SSPM solution detects threats stemming from anomalous user behavior, such as logging onto applications from irregular locations or using a suspicious browser. It identifies and raises an alert for lateral movements – such as the creation of a new admin account – that indicates an attack may be under way.
When misconfigurations are found, SSPMs provide step-by-step remediation descriptions to show exactly how to fix the SaaS misconfiguration. Advanced SSPMs may also include an auto-remediate feature directly from the platform.
Security teams need to have a long-term view of their security posture to understand how their system has evolved over time. SSPM solutions provide posture-over-time graphs to enable teams to benchmark individual applications against each other, compare different instances of the same app, or compare segments.
While the native security controls of SaaS apps are often robust, it falls on the responsibility of the organization to ensure that all configurations are properly set — from global settings, to every user role and privilege. The security team is tasked with knowing every app, user, and configuration, and ensuring they are all compliant with industry and company policy.
With an SSPM solution, security teams can increase their SaaS security beyond Misconfiguration Management to also cover SaaS-to-SaaS Access, Device-to-SaaS User Risk levels, and Identity & Access Management Governance.
Each app can have hundreds of global settings, such as which files can be shared, whether MFA is required, or whether recording is allowed in video conferencing. Then multiply this number by thousands of employees. Security teams must familiarize themselves with every application’s specific set of rules and configurations and ensure they are secure. Additionally, the SaaS app owner often sits outside of the security team, in the department that most uses the app, and have their priorities focused on productivity rather than the security upkeep of the app.
SSPM bridges these gaps and enables security teams to continuously oversee and fix the posture of each app and communicate its configuration fixes through the platform while enabling business continuity.
Employees often extend the functionality of their primary SaaS applications by connecting them to a secondary SaaS app, otherwise known as 3rd-party app access. However, users rarely realize they've handed over significant permission rights to the new 3rd-party application.
The security team needs to be able to identify and monitor all that happens within their SaaS ecosystem. Visibility into all configurations and user permissions of each and every app, including all the SaaS-to-SaaS apps that have been granted access by users is crucial. This way, security teams can retain control of the SaaS stack, remediate any issues, block any apps using too many privileges, and mitigate their risk.
Employees often use personal and company devices to get the jobs done. However, if their device’s hygiene contains even one vulnerability, it increases the risk for the organization and widens the attack surface for bad actors.
Security teams need to be able to remediate threats posed by endpoint devices. To get a handle on which devices and users pose the highest risk, security teams can correlate devices, their users, and associated SaaS app permissions.
Implementing Identity & Access Management best practices are crucial to secure the SaaS environment. IAM Governance enables the security team to act upon arising issues by providing constant monitoring of the company’s SaaS Security posture as well as its implementation of access control. An SSPM solution enables this by managing prevention domains such as misconfigurations, vulnerabilities, and exposure.
CSPM refers to IaaS security solutions while an SSPM solution is specialized in SaaS app technology and offers unique value to be able to integrate with any app in the organization’s SaaS app stack.
SSPM is frequently confused with CASB, as both are designed to address security issues within SaaS applications. While there may be some overlap between the two, SSPM looks at security settings within SaaS applications, including user profiles, devices, and third party SaaS applications that connect to core SaaS apps. CASB, in contrast, functions as a gatekeeper, allowing organizations to extend their security policies into the cloud.
SSPM provides visibility across a company’s entire SaaS stack to protect against cybersecurity attacks and data breaches. It offers non-stop monitoring of millions of configurations, SaaS app connections, user security hygiene, and devices used to reduce risks and detect threats. While there are multiple security tools that focus on cloud-based data protection, SSPM is the only one that provides real-time protection for all your SaaS data.


This past month, Adaptive Shield partnered with Panorays (a SaaS-based third-party security risk management platform) to produce a joint webinar Pinpoint Your SaaS App Risks: From Evaluation to Usage. These two security experts, Maor Bin, CEO of Adaptive Shield, and Demi Ben Ari, CTO OF Panorays, discussed the evolution of third-party apps, the tools used to secure them, and the best practices and processes for using these tools. Here are some of the highlights and key takeaways.
Click here to watch the full recorded webinar.
Maor Bin, CEO & Co-Founder at Adaptive Shield, brings over 16 years of experience in the cyber security industry. Before founding Adaptive Shield, Maor served as a cybersecurity intelligence officer in the IDF and later led SaaS Threat Detection Research at Proofpoint.
Demi Ben Ari, CTO & Co-Founder at Panorays, is a software engineer, entrepreneur, and international tech speaker. He has over 10 years of experience in building systems both from the field of near real-time applications and big data distributed systems.
Demi Ben Ari: “The SaaS stack that you are using today is really your new attack surface”
As illustrated in Figure 1, the supply chain has become more complicated and complex due to many changes in the industry.

It's clear that 3rd party apps like Salesforce, Slack, and Monday are critical to businesses and have become an inseparable part of employee’s day to day. It’s also clear that proper risk assessment and security for these apps is vital.
Demi takes a moment to discuss how this risk is understood in today’s market:
“Think that today when we were speaking about third-party breaches that people speak about and echo in the media… it isn't really an attack, right? There is a vulnerability exposed to the world and a lot of hackers and a lot of malicious actors actually try to exploit them with the spray and pray attack. So most of it is not even really targeted.”
This signifies two things. The first being that most breaches are happening simply as a result of apps being poorly secured. The second is understanding that attackers are continuing to explore new means to access and exploit organization's data and this can be true for both targeted and non-targeted organizations, meaning hardening security settings for every app cannot be overstated.
For example, Salesforce is crucial to today's business but in order to operate, the app houses sensitive information that if leaked could potentially ruin a business. The 2022 SaaS Security Survey Report shows that while the investment in SaaS applications is growing, the investment in security tools and staff is lagging behind, as seen in Figure 2.

Organizations need a new tool set to secure the onboarding of new apps and other developments in their SaaS landscape. However, the process needed for organizations to secure their 3rd party apps goes far beyond just implementation; organizations need to evolve their security protocols to include a continuous and repetitive means of evaluating and hardening app security.
Demi: “We spoke about identification and how to know all the vulnerabilities, but it’s a process, and the process does not finish at ‘I'm installing something and this magic box will solve all of my problems’...the continuous monitoring aspect is really crucial.”
Maor Bin: “We need to understand first of all what we need to do to create this [continuous assessment] process internally to work in a secure fashion.” Maor outlines the process of initial and continuous SaaS security assessment into three levels – discovering and assessing risks, obtaining and maintaining hygiene, and managing threats.

Figure 3 outlines the entire process that security teams should be conducting and repeating in order to keep their SaaS stack secure. While the details of this process should be customized to each organization's size, needs, and resources, the overall methodology is the key to create a continuously secure SaaS environment.
The first step in securing one’s SaaS ecosystem is having comprehensive and robust discovery processes to learn of the potential apps’ digital footprint. Security teams need to understand where they have visibility and, more importantly, where they don't. Addressing blind spots should be a top priority to ensure risk can be discovered and reduced.
Then, throughout the onboarding process, from users, their permissions, and their devices, security teams can be hyper aware of all the moving parts that should be checked. Organizations also need to be able to identify and discover SaaS-to-SaaS applications, including ones that are connected without the security team’s knowledge. Today's workforce depends on apps that easily connect with the user's workspace.These 3rd-party applications, which can number in the thousands for larger organizations, all must be monitored and overseen by the security team.
Once the initial assessment is complete, security teams must maintain (or increase) the level of hygiene. Security teams should focus on closing gaps that exist in their posture to remediate faster and reduce risk. This requires that security teams evaluate configurations, compliance requirements, and other changes in their SaaS estate not just once, but repeatedly.
The final step is threat management. Security teams must identify misconfigurations or vulnerabilities in a device or user that is causing risk and quickly remediate the issue.
Gartner recently named a new security discipline called Identity Threat Detection and Response (ITDR). ITDR incorporates detection mechanisms that investigate suspicious posture changes and activities, and responds to attacks to restore the integrity of the identity infrastructure.
ITDR incorporates strong SaaS Security IAM Governance methodologies and best practices that are found in SaaS Security Posture Management solutions (SSPM). This enables security teams to gain continuous and consolidated visibility of user accounts, permissions, and privileged activities across the SaaS stack, such as:
Regardless of how secure an organization's SaaS posture is, new threats continue to emerge and security teams need the right tools to combat them.
Maor Bin: “We need to understand the privacy policy for these 3rd party applications. We have a process for it when it comes to endpoint, which we call application control, and everybody understands that they need to do it for their endpoints…but when it comes to 3rd party apps, things are falling between the cracks.”
Demi Ben Ari: “It always starts from visibility and onboarding. Eventually when you end up with continuous monitoring, it’s also continuously onboarding all of these third-party engagements, and this can be on multiple layers.”
Salesforce can be used as an example of these layers and is considered the first layer. Next, a user may install 5 plug-in applications from the app exchange – apps that may not even be verified by a security expert – creating the second layer, also called SaaS-to-SaaS access or 3rd party app access. This second layer alone already introduces dozens of granted permissions into your environment, multiplying the attack surface. It doesn't stop there – an app connected in the second layer may have its own connected plug-ins which in turn create the third layer and so on and so forth. Security teams must have an assessment process for onboarding the entire entity from the core apps to all its plugins.
Maor iterates: the first step is to identify and discover all these applications and then understand what other apps are connected. History has taught us that many breaches happen as a result of attackers gaining access to small supported apps as opposed to the core SaaS workspace.
Maor: “The idea, when we talk about security, is not just protecting one application or a handful of applications, it’s protecting your entire stack”.
The high volumes of apps, users, and settings makes maintaining a secure SaaS stack a near impossible challenge. Security teams need all-around visibility into different aspects of their SaaS stack while simultaneously implementing and maintaining continuous security assessments. SaaS Security Posture Management (SSPM) solutions enable security teams to gain complete control over their SaaS stack and significantly aid in implementing the continuous process of assessment.
SSPM combat the challenges existing in the SaaS landscape through:
.png)
.png)
Tel Aviv, November 30, 2022—Adaptive Shield, the leading SaaS Security Posture Management (SSPM) company, today announced new capabilities to discover and monitor 3rd party apps connected to the core SaaS stack. With this new capability, Adaptive Shield is minimizing the risk that SaaS-to-SaaS, also known as 3rd party app access, presents. Security teams can now quickly and easily manage sanctioned apps and discover unsanctioned apps that have access to the company’s data.
Today’s modern workforces rely on SaaS apps to run their business — and employees in pursuit of productivity and efficiency connect hundreds to thousands of SaaS apps to the core stack, from the smallest plugin to more robust apps, without consulting the organization's security team. These employees connect apps without understanding the level of risk each presents, the types of permissions they are requesting, or whether the app itself is malicious. Without this departmental oversight, businesses cannot properly evaluate or manage their attack surface.
The challenge is exacerbated by the fact that 56% of organizations adopting SaaS apps state their top concern is the lack of visibility into connected apps, according to the 2022 SaaS Security Survey Report from Adaptive Shield and CSA (Cloud Security Alliance).
“As SaaS app dependency grows, so too does our comfort level in using these apps — this is why many grant access without considering the possible consequences. As a result, third-party app access has become the new executable file,” states Maor Bin, co-founder and CEO of Adaptive Shield. Bin continues, “Now, with these new capabilities, whether employees have connected 50 to 5000 apps, Adaptive Shield equips security professionals with the solution to regain control over their SaaS Security.”
Adaptive Shield recently announced their ability to integrate with 100+ SaaS apps, the first and only SSPM solution to provide this large number of out-of-the-box integrations. Their deep knowledge and expertise over the wide array of application characteristics, hubs and interconnected apps powers these new capabilities of 3rd party discovery within the Shadow IT domain.
From access scopes requested by these apps, to authorized users and cross referencing, the security team can now measure the level of access to sensitive data across the organization’s stack. In addition, the security team gains advanced reporting capabilities for effective and accurate risk assessments to drive actionable measures.
The original PR was released through Business Wire on Nov 30, 2022.


Forrester, a research and advisory company, offers organization’s a variety of services including research and consulting. Their reports help professionals understand their customer’s behavior, concerns, and interests to help organizations make more informed decisions. Their Trend Report ‘Embrace A Paradigm Shift In SaaS Protection: SaaS Security Posture Management’ looks at the increased use of SaaS apps and the value of an SSPM solution. This blog will summarize key takeaways from the report.
Click here to read the full report.
“Organizations’ cloud-first or on-premises augmentation strategies caused an explosive, decentralized, and uncontrolled growth of SaaS application use. Consequently, the increase in the number of cloud assets has also increased overall IT risks.”
The ease with which SaaS apps can be adopted is remarkable, but it has become a double-edged sword. The cloud has enabled organizations to store and manage near endless data and scale their operations, but it has opened the doors for relentless attackers and new attack vectors. Organizations have dozens to over a hundred different SaaS apps critical to maintaining day-to-day operations, each with nuanced access patterns from sharing, uploading, downloading, sorting, searching, and filtering activities.
Access patterns and activities, when looked at individually, may appear harmless. However when looked at as part of a bigger picture, security teams can often quickly identify risk by spotting unusual behavior, suspicious geolocations movements, and uncommon access requests. Organizations not only gain visibility into different domains and activities but also monitor data movement to and from SaaS apps to help detect threats.
The skills shortage and gap between application owners and security teams only adds to the challenge. The report found that even the largest organizations interviewed stated that they lack the resources needed to fully understand the connectivity between SaaS apps and their security implications. Organizations are in dire need of a security solution, such as an SSPM, which is able to provide visibility and understanding into these apps.
In turn, an effective SSPM needs to be able to integrate with all their apps to support the organization's security policies and goals. Contextualized visibility into each app helps security teams prioritize configuration weaknesses and increase time and efficiency to remediation across multiple attack surfaces.
“SSPM solutions differ in breadth and depth of SaaS app coverage”
Simply put, not all SSPM solutions are created equal. SSPMs can vary in the amount of apps they support, the thoroughness of their security checks, and the range of their capabilities. Forrester describes needed functionalities within the organization’s chosen SSPM solution:

At Adaptive Shield, we like to boil it down to four main use cases: misconfiguration management, SaaS-to-SaaS access discovery, device-to-SaaS user management, and identity and access management governance. An SSPM will present detailed and dedicated security checks within each of these use cases.
The 2023 SaaS Security Posture Management Checklist covers all the critical features and capabilities to look out for when evaluating a solution.
“SSPM solutions can make recommendations on how to trim business users’ privileges without impeding their user experience (i.e., they continue to have access to data and the SaaS application functionality that they need to do their jobs without access to data they do not need).”
An SSPM’s user inventory is one of many critical features. A user inventory helps security teams gain visibility of users, their privileges, and user-specific failed security checks. By gaining in-depth knowledge of user permissions and behavior, security teams can identify inactive users, overprivileged admins, and other user-specific threats. SSPMs can help trim unnecessary user privileges without limiting access to the data needed to complete their work.
The report outlines the following identity and access management related SaaS settings that SSPM solutions can enforce.
It's not surprising that SaaS apps do not properly guard organization’s data and are susceptible to data breaches. SSPM solutions provide relief to security experts by offering data protection features such as:


Every SaaS app user and login is a potential threat; whether it’s bad actors or potential disgruntled former associates, identity management and access control is crucial to prevent unwanted or mistaken entrances to the organization’s data and systems.
Since enterprises have thousands to tens of thousands of users, and hundreds to thousands of different apps, ensuring each entrance point and user role is secure is no easy feat. Security teams need to monitor all identities to ensure that user activity meets their organization’s security guidelines.
Identity and Access Management (IAM) solutions administer user identities and control access to enterprise resources and applications. As identities became the new perimeter, making sure this area is governed by the security team is vital.
Gartner has recently named a new security discipline called Identity Threat Detection and Response (ITDR) that incorporates detection mechanisms that investigate suspicious posture changes and activities, and responds to attacks to restore the integrity of the identity infrastructure.
ITDR incorporates strong SaaS Security IAM Governance methodologies and best practices that are found in SaaS Security Posture Management solutions (SSPM), enabling security teams to gain continuous and consolidated visibility of user accounts, permissions, and privileged activities across the SaaS stack, such as:
Whether you are a CISO, IT or on the Governance, Risk and Compliance (GRC) team, this article will cover the role of Identity and Access Management Governance as part of the organization’s SaaS security program.
IAM Governance enables the security team to act upon arising issues by providing constant monitoring of the company’s SaaS Security posture as well as its implementation of access control.
There are a few critical prevention domains where an SSPM can manage Identity and Access Management Governance: 1) Misconfigurations 2) Vulnerabilities 3) Exposure.
IAM controls need to be properly configured on a continuous basis. The IAM configurations should be monitored for any suspicious changes and ensure that the appropriate steps are taken to investigate and remediate when relevant.
For example, an organization can enable MFA across the organization and not require it. This gap in policy enforcement can leave the organization at risk — and an SSPM can alert the security team about this gap.
The SSPM solution can utilize patching or compensating controls to address commonly exploited vulnerabilities in the identity infrastructure such as the SaaS user’s device. For example, a privileged CRM user can present a high risk to the company if their device is vulnerable. To remediate potential threats that stem from devices, security teams need to be able to correlate SaaS app users, roles, and permissions with their associated devices' hygiene. This end-to-end tactic enables a holistic zero-trust approach to SaaS security.
Another critical vulnerability stems from authentication protocols that the password access is limited to a single-factor authentication method, such as with legacy protocols like IMAP, POP, SMTP and Messaging API (MAPI). An SSPM can identify where these protocols are in place across the organization’s SaaS stack.
The SSPM helps to reduce the attack surface by identifying and mitigating places of exposure. For example, removing unnecessary or excessive privileges or allowing an external admin for a business-critical app. (See figure 1.)

Additionally, 3rd party app access, also known as SaaS-to-SaaS access can leave an organization exposed. Users connect one app to another app to either provide enhanced features or user’s information (e.g contacts, files, calendar, etc). This connection boosts workflow efficiency and as a result, employees’ workspaces are connected to multitudes of different apps. However, the security team is most often in the dark about which apps have been connected to their organization’s ecosystem, unable to monitor or mitigate any threats.
IAM is a method for hardening access control, whereas IAM Governance in SSPMs offer continuous monitoring of these features to ensure security teams have full visibility and control of what's happening in the domain.


Tel Aviv, November 9, 2022—Adaptive Shield, the leading SaaS Security Posture Management (SSPM) company, today announced it is the first and only SSPM platform to cover 100 SaaS platforms and applications out of the box. Security teams will now be able to gain visibility and control of 100 SaaS apps and automate misconfiguration management, monitor SaaS-to-SaaS access, harden identity and access governance and manage SaaS risks stemming from user devices.
“It’s not enough to cover the core five business-critical apps,” asserts Gilad Walden, VP Product at Adaptive Shield. “While that is the start, an attack can come from any app. Security teams are also flying blind without visibility and control over a critical mass of their SaaS app stack. This is why the depth of security checks offered by each app’s integration is critical. Each of these 100 app integrations has been researched to ensure it provides comprehensive coverage of the potential threat models.”
Walden continues, “One of our favorite moments is seeing the customer’s reaction when they connect their entire SaaS stack. Instantly — and without any changes to their architecture — they gain deep visibility into all security controls and can finally identify and prioritize any potential threat.”
Adaptive Shield’s approach combats the widespread misunderstanding in the market about how organizations can best secure their SaaS stack and attain strong SaaS governance. Companies are investing solutions like CASB, manual audits, proprietary solutions, and others yet, their SaaS stacks remain unsecure.
In addition to the breadth, depth and context security teams gain for their SaaS app stack, Adaptive Shield’s flexible architecture enables security teams to keep up with the fast pace of new app releases and integrate on-demand.
Click to see the list of Adaptive Shield supported integrations
The original PR was released through Business Wire on Nov 9, 2022.


When creating a Sandbox, the mindset tends to be that the Sandbox is considered a place to play around, test things, and there will be no effect on the production or operational system. Therefore, people don’t actively think they need to worry about its security. This mindset is not only wrong, but extremely dangerous.
When it comes to software developers, their version of sandbox is similar to a child’s playground — a place to build and test without breaking any flows in production. Meanwhile, in the world of cybersecurity, the term ‘sandbox’ is used to describe a virtual environment or machine used to run suspicious code and other elements.
Many organizations use a Sandbox for their SaaS apps — to test changes without disrupting the production SaaS app or even to connect new apps (much like a software developer’s Sandbox). This common practice often leads to a false sense of security and in turn a lack of thought for its security implications. This article will walk you through what is a SaaS sandbox, why it is vulnerable, and how to secure it.
A cybersecurity sandbox allows separation of the protected assets from the unknown code, while still allowing the programmer and app owner to see what happens once the code is executed. The same security concepts are used when creating a SaaS Sandbox — it duplicates the main instance of SaaS including its data. This allows playing around with the SaaS app, without influencing or damaging the operational SaaS — in production.
Developers can use the sandbox to test the API, install add-ons, connect other applications, and more — without worrying about it affecting the actual users of the organization. Admins can change configurations, test SaaS features, change roles, and more. This allows the user to better understand how the changes to the SaaS will go before implementing it on an operational, and critical, SaaS instance. This also allows time to create guidelines, train staff, build workflows, and more.
All in all, using a Sandbox is a great concept for all software and SaaS usage; but like all great things in the world of SaaS, the problem is that there is a major security risk lurking within.
A large private hospital inadvertently revealed data of 50,000 patients when they built a demo site (i.e a Sandbox) to test a new appointment-setting system. They used the real database of the medical center, leaving patients' data exposed.
Often a Sandbox is created using real data, occasionally even a complete clone of the production environment, with its customizations. Other times, the Sandbox is directly connected to a production database. If an attacker manages to penetrate the Sandbox because of lax security, they will gain access to troves of information. (This leakage of information can be problematic especially if you are an EU company or processing EU data because of GDPR. If you are processing medical information in the USA or for a USA company, you can be in violation of HIPPA.)
Even organizations that use synthetic data, which is recommended for all companies, can still be at risk for an attack. An attacker can use the Sandbox for reconnaissance to gain insight on how an organization sets up its security features and its possible weak spots. Since the Sandbox reflects to some degree how the operational system is configured, an attacker can use this knowledge to penetrate the production system.
The solution for the problem of the non-secure Sandbox is rather simple – secure the Sandbox step-by-step as if it was a production system.
Step 1. Manage and control access to a Sandbox and limit users’ access to the Sandbox. For example, not every user that has access to production should also have access to the Sandbox. Controlling which users can create and access a Sandbox is the first step for keeping your SaaS environment secure.
Step 2. Implement the same security settings that are configured within the operational system to the Sandbox version; from requiring MFA to implementing SSO and IDP. Many SaaS apps have additional security features that are tailor-made for that specific SaaS app and should be mirrored in the Sandbox. For example, Salesforce has unique security features such as: Content Sniffing Protection, Default Data Sensitivity Levels, Authentication Through Custom Domain, and so on.
Step 3. Remove production data and replace it with synthetic (i.e. made up) data. Sandboxes are typically used for testing changes in configurations, processes, flows (such as APEX), and more. They don’t require real data for testing changes - any data with the same format can be sufficient. Therefore, avoid copying the production data and use Data Mask instead.
Step 4. Keep your Sandbox inline with security improvements done in the production environment. Often a Sandbox is neither refreshed or synced on a day-to-day basis, leaving it vulnerable to threats that were minimized in the production. To reduce risk and to make sure your Sandbox is serving its purpose, a Sandbox should be synced every day.
Security teams can also implement and utilize SSPM (SaaS Security Posture Management) solutions, to automate their SaaS security processes and address the challenges detailed above, to monitor and prevent threats from infiltrating the SaaS sandbox. An SSPM enables security teams to identify, analyze, and prioritize misconfigurations in the Sandbox and across the whole SaaS app stack, as well as provide visibility to 3rd party apps with access to the core apps, Device-to-SaaS User posture management and more.
This is an excerpt from an article that was published in The Hacker News on Oct 20, 2022.


“SaaS applications have native security controls as part of their offering which makes them security products themselves — that security teams now need to manage”.
Asserted by Adaptive Shield’s CEO, Maor Bin partnered with Okta’s VP of Strategy, Stephen Lee in the Security Boulevard Webinar: SaaS Security Trends, Challenges, and Solutions for 2022. This joint webinar discusses the struggles that security professionals face today and how organizations can address the risks stemming from key attack areas. This blog highlights some of the dialogue between these two industry thought leaders.
(For the whole webinar, click here.)
Organizations use dozens to hundreds of apps throughout different departments and with each app comes a sea of configurations to set and secure, not once but constantly. Over time, apps have updates and new security settings or new users with different permissions levels to add or adjust. Security teams need to invest many resources to continuously be on the lookout for misconfigurations and quickly remediate them.
The challenge of managing configurations goes beyond the sheer volume to the intricacies of understanding each app.
Stephen Lee: “If you look at the SaaS applications out there and you go to that security tab or that user management tab – they all look different. Sometimes, you almost have to be that specific app expert to be able to know what to do.”
Maor Bin: “That's one of the reasons for the challenge of securing your SaaS estate – you have so many applications and each one is different from the other one.”
Different apps may have the same or similar security settings but the names of these settings and how to access them can differ vastly. Security teams who are trying to manually secure each configuration have to be an expert on every single app to secure them, which is a far from realistic request.
Stephen Lee: “One beautiful thing about SaaS applications is that it's very easy to integrate with them. [However] once you've shared the power with the downstream applications or clients that are talking to it and then it all becomes ‘who is the weakest link?’ and that becomes a potential security hole.”
SaaS-to-SaaS access has become a balance between the convenience of having end users be able to easily integrate and use these applications (that boost productivity and remote work) and the ability for security teams to have the necessary visibility to secure and monitor these apps.
The risks from SaaS-to-SaaS app access stem from the connection process; the app requests permissions in the user’s workspace and oftentimes, the app is asking for high-risk permissions (the app could also be malicious itself, unbeknownst to the user). Typically defined as allowing an app to gain access to user data (e.g. read/write permissions and more), high-risk permissions, and any unknown app, should only be granted access after the secure team has been able to fully vet it and have a system in place to monitor it.
The 2022 SaaS Security Survey Report demonstrates just how prevalent of a concern 3rd party app access is for today’s CISOs and security professionals.

Maor Bin: “The challenge is not only misconfigurations and native security controls within SaaS applications but what actually happens after you login, what happens within your device…and get a better understanding of what's going on with your users. So for example: if you see you have a Office 365 admin and this user has 3 critical vulnerabilities on their device, it’s obviously a huge problem because this isn't just a regular SaaS user accessing the SaaS applications but it's an admin with privileged roles.”
When individuals with advanced privilege levels use devices that are unsecured, they expand the attack surface with what amounts to an open gateway.
With today's modern workforce working from home, cafes, or even abroad, security teams need to secure all the devices the employees are using. Personal devices are vulnerable to data theft and can inadvertently pass on malware that was downloaded for personal use into the organization’s environment. Lost or stolen devices can also provide a gateway for criminals to access the network.
Stephen Lee: “You can hire the best IT folks and you can hire the best app admins, the best Security Experts… but things do happen. I think it’s not about how to prevent it from happening; I think it’s a lot about mitigation, mitigating the risk…This is relevant to not just a small company with 50 people all the way up to large Enterprises.”
“There's a lot of stuff happening outside of what Okta is able to manage…For us, I’m excited to see how Adaptive Shield can help solve these problems.”
In order to cover the many attack surfaces of SaaS apps, an SSPM solution can enable security teams to gain control of the core misconfiguration management use case; and go beyond to the added layers of SaaS-to-SaaS access, device-to-SaaS user risk, and identity and access management governance.
If you’d like to learn more, contact one of our experts here.


The ease with which SaaS apps can be deployed and adopted today is remarkable, but it has become a double-edged sword. On the one hand, apps are quickly onboarded, employees can work from anywhere, and there is little need for operational management. On the other hand, there are pain points that stem from the explosion of SaaS app usage, explained by the "3 V" s:
Named by Gartner as a MUST HAVE solution in the "4 Must-Have Technologies That Made the Gartner Hype Cycle for Cloud Security, 2021," SaaS Security Posture Management (SSPM) solutions come to answer these pains to provide full visibility and gain control of the company's SaaS security posture.
As one might expect, not all SSPM solutions are created equal. The Misconfiguration Management use case sits at the core of SSPM. However, there are more advanced use cases that tackle the emerging and growing challenges existing in the SaaS landscape.
When comparing SSPM options, here are some key features and capabilities to look out for (excerpted from the complete guide):
Run comprehensive security checks to get a clear look into your SaaS estate, at all the integrations, and all the domains of risk.
First and foremost for an SSPM's core solution, is the SSPM's ability to integrate with all your SaaS apps.
The other vital component to a core SSPM solution is the expanse and depth of the security checks. Each domain has its own facets for the security team to track and monitor.
Combat threats with continuous oversight and fast remediation of any misconfiguration
Remediating issues in business environments is a complicated and delicate task. The core SSPM solution should provide deep context about each and every configuration and enable you to easily monitor and set up alerts. This way vulnerabilities are quickly closed before they are exploited by cyberattacks.
SSPM vendors like Adaptive Shield provide you with these tools, which allow your security team to communicate effectively, shut down vulnerabilities, and protect your system.
Your SSPM solution should be easy to deploy and allow your security team to easily add and monitor new SaaS applications. Top security solutions should integrate easily with your applications and your existing cybersecurity infrastructure, to create a comprehensive defense against cyber threats.
In an effort to improve productivity, employees often extend the functionality of their primary SaaS applications by connecting them to a secondary SaaS app, or otherwise known as 3rd-party app access. These rights include the ability to read, create, update, and delete corporate or personal data. This access is granted in seconds, usually far outside the view of the IT and security teams, and significantly increases an organization's attack surface.
However, users rarely realize they've handed over significant permission rights to the new 3rd-party application. These 3rd-party applications, which can number in the thousands for larger organizations, all must be monitored and overseen by the security team.
To prevent secondary apps from providing an unauthorized gateway into your system, your SSPM solution should be equipped with the following capabilities:
Even before employees were routinely working from home, user devices posed a risk to corporate networks. Security teams had no visibility into the owners of different devices and couldn't ensure that the devices were secure. When individuals with advanced privilege levels use devices that are unsecured, they expand the attack surface with what amounts to an open gateway.
Track and monitor all device-to-SaaS user risk to eliminate surprise vulnerabilities
Associating Devices with Users
Over time, the number of users with access to different parts of an enterprise's system increases. While some users may move on, oftentimes they remain in the system and retain the same privileges that they had. Threat actors or disgruntled associates of the company can use these credentials to gain access to unauthorized areas of the system. Security teams need a tool to identify and disconnect these users from multiple environments and applications within the company. They also need to monitor every SaaS login and ensure that user activity meets security guidelines.
Identify all users with access to any system or application within the environment:
User Authorizations
Identifying Users
The Right SSPM solution PREVENTS your next attack.
SSPM is similar to brushing one's teeth: it's a foundational requirement needed to create a preventative state of protection. The right SSPM provides organizations continuous, automated surveillance of all SaaS apps, alongside a built-in knowledge base to ensure the highest SaaS security hygiene.
Get the complete guide along with the printable checklist here.


The International Organization for Standardization (ISO) sets standards across various industries. As an internationally recognized standards organization, its two information technology security standards - ISO 27000:2018 and ISO 27001:2013 - can be used to help build out a strong security posture.
SaaS security is critical to ISO compliance in the modern business world. However, with all the non-stop developments in the organization's SaaS stack, from updating and modifying configurations to discovering SaaS-to-SaaS access and securing devices etc., it can become overly burdensome for a security team to handle. SSPM solutions come to answer this pain by providing proactive, deep, continuous and automated monitoring & management capabilities. (SSPM solutions can also offer security checks per compliance framework so the security team can easily see where their posture is compliant or needs remediation.)
This blog will take a deep dive into understanding the ISO compliance standards, with its two recent yet different versions, and how SSPM can help security teams ensure ISO compliance.
Simply put: ISO 27000:2018 gives you goals to accomplish while ISO 27001:2013 outlines the steps you have to take to achieve those outcomes.
ISO 27000 sets out the following fundamental principles of your security program:
ISO 27001 focuses on best practices and establishing an Information Security Management System (ISMS) that consists of policies and procedures. It includes five processes for achieving these security fundamentals:
A lot of this sounds fairly vague, and it is. ISO takes a risk-based approach to establishing an ISMS, but that doesn’t mean you’re on your own.
The first three clauses give you the basic terminology and scoping. It’s clauses four through ten that start to get into some more detail. These are:
Again, this is fairly high-level, even though ISO gives detailed definitions within the clauses. The real work of getting ISO compliant is found in Annex A which lists 114 controls aligned to ten clauses.
The problem with understanding the importance of SaaS security within the ISO context is that ISO never specifically mentions SaaS apps. Since it acts as a risk-based framework, you need to start by identifying the risks that SaaS apps pose, then put the controls around them.
Going into all the controls listed in ISO 27001 would be too long for this post. However, you can get a general sense of how SaaS security - and SaaS Security Posture Management (SSPM) - fits into your ISO compliance plans with a few examples.
Under Access Control, you need to ensure that all users are assigned the appropriate access needed to complete their job functions.
Ensuring SaaS security under this requirement can be challenging because you need to make sure that you meet the following sub-requirements:
Permission drifts occur when a user has certain permissions as part of a group membership, but then gets assigned a specific permission that is more privileged than what the group has. Over time many users get extra permissions. This undermines the idea of provisioning using groups.
SSPM gives you a way to govern users’ cloud access by:
Operations security is the process of ensuring correct and secure operations for all information processing facilities. In cloud environments, managing operations security becomes more difficult because you often lack visibility.
Ensuring SaaS security under this requirement can be challenging because you need to make sure that you meet the following sub-requirements:
OAuth is an extremely common action that users take, but implementation mistakes can lead to attacks. You need to make sure that you have the appropriate documented operating procedures for onboarding new applications that use OAuth. Further, cybercriminals can use misconfigurations, like the sending OAuth application phishing emails, as part of their ransomware attacks.
SSPM gives you the ability to run continuous security checks for all SaaS apps in use, in addition to the SaaS-to-SaaS access, so that you can:
This requirement focuses on avoiding legal, statutory, regulatory, or contractual obligations.
Ensuring SaaS security under this requirement can be challenging because you need to make sure that you meet the following sub-requirements:
Default configurations can lead to PII leaks as seen in the 2021 Power Apps portal issue that Microsoft fixed. Knowing what default configurations create a compliance violation and monitoring to ensure that you fix issues is key to compliance.
SSPM can help you get compliant by:


Imagine this: a company-wide lockout to the company CRM, like Salesforce, because the organization's external admin attempts to disable MFA for themselves. They don't think to consult with the security team and don't consider the security implications, only the ease which they need for their team to use their login.
This CRM, however, defines MFA as a top-tier security setting; for example, Salesforce has a "High Assurance Login Value" configuration and immediately locks out all users as a safety precaution. The entire organization hits a standstill and is frustrated and confused.
Deeply concerning, this is not a one-off event, admins for business-critical SaaS apps often sit outside the security department and have profound control. Untrained and not focused on security measures, these admins are working towards their departmental KPIs. For instance, Hubspot is usually owned by the marketing department, likewise, Salesforce is often owned by the business department, etc. Business departments own these apps because it's what allows them to do their job efficiently. However, the paradox lies in the fact that it's the security team's responsibility to secure the organization's SaaS app stack and they cannot effectively execute this task without full control of the SaaS app.
The 2022 SaaS Security Survey Report, conducted by CSA and Adaptive Shield, delves into the reality of this paradox, presenting data from CISOs and security professionals today. This article will explore important data points from the respondents and discuss what the solution for security teams could be.
Across a typical organization, a wide array of SaaS apps are used (see figure 1), from cloud data platforms, file sharing and collaboration apps to CRM, project and work management, marketing automation, and a whole lot more. The need for each and every SaaS app fills a certain niche role required by the organization. Without the use of all these SaaS apps, a business could find itself lagging or taking more time to achieve its KPIs.

The 2022 SaaS Security Survey Report reports that 40% of these apps are managed and owned by non-security teams, such as sales, marketing, legal, etc. (see in figure 2). While the security and IT teams are reported to be the main destination for SaaS app management, it's the 40% of business departments also taking part and having full access that complicates the threat landscape.
Security teams can't take away this ownership as the business applications' owners need to maintain a high level of access to their relevant SaaS apps for optimal use. Yet, without in-depth knowledge of security or the vested interest (a security KPI that reflects on their work product), it's not reasonable for the security team to expect that the business owner will ensure a high level of security in their SaaS.

When asked the main reason for misconfiguration-led security incidents (figure 3), respondents of the survey report cited these as their top four: (1) There are too many departments with access to security settings; (2) Lack of visibility to security settings when they are changed (3) Lack of SaaS security knowledge; (4) Misappropriated user permissions. All of these reasons, either overtly or implied, can be attributed to the SaaS App Ownership Paradox.

The leading cause of security incidents caused by misconfigurations is having too many departments with access to security settings. This goes hand in hand with the next cause – lack of visibility when security changes are changed. A business department may make changes to an app setting to optimize its ease of use without consulting with or notifying the security department.
In addition, misappropriated user permissions can easily stem from a business department owner at the helm who is not paying careful attention to the app's security. Often users are granted privileged permissions that they don't even need.
With this shared responsibility model, the only efficient way to bridge this communication gap is through a SaaS Security Posture Management platform (SSPM). With an SSPM solution, owned and managed by the organization's security team, the security team can gain complete visibility of all the company's SaaS apps and their security settings, including user roles and permissions.
Organizations can take it one step further and have the app owners join the SSPM platform so they can actively control and oversee all configurations in their owned apps. By using a scoped admin capability (figure 4) the security team can grant the app owners access to the apps they own and can remediate security issues, with their supervision and direction.

There's no way to eliminate business departments' access to SaaS app security settings, and while users across the organization should be educated on basic SaaS security in order to reduce the risk that may occur from business departments, it doesn't always happen or it's just not enough. Organizations need to implement a solution that helps avoid these situations by enabling visibility and control for the security team, including alerting on configuration drifts and audit logs that provide insight into actions within the SaaS apps and scoped admins.


TEL AVIV, Israel - Sept 13 2022 - Adaptive Shield, the leading SaaS Security Posture Management (SSPM) company, today announced a partnership with Tenable, the Cyber Exposure Management company, to provide a consolidated posture management solution that correlates the risk of SaaS users and their endpoints.
While SaaS providers build in security features, it is the company’s responsibility to continuously cover all attack surfaces: from misconfigurations to identifying SaaS apps connected to the core SaaS app, while also detecting and remediating SaaS threats stemming from user devices with poor hygiene.
By correlating Tenable’s rich vulnerability insights within Adaptive Shield’s SaaS security posture technology, security teams will gain context and visibility to easily see and manage the risks that come from SaaS users and their associated devices. This partnership enables organizations to enrich their understanding of device and user posture and their influence on one another.
“When mitigating the SaaS attack surface, vulnerability management is an integral part of SaaS security hygiene, especially when it comes to privileged users and their device posture,” said Maor Bin, Co-Founder and CEO of Adaptive Shield. “By partnering with Tenable, we are proud to advance a new standard for organizations to protect their SaaS stack.”
“Understanding exposure and risk across SaaS deployments has never been more important than in today’s cloud-first world,” said Ray Komar, vice president of technical alliances, Tenable. “We’re excited to bring Adaptive Shield into our technology ecosystem, providing customers with increased visibility and context across their attack surface.”
For the full solution brief, take a look at our resources.
The original PR was released through Business Wire on Sept 13, 2022.


Another day, another attack method.
GIFShell attack technique enables bad actors to exploit several Microsoft Teams features to act as a C&C for malware, and exfiltrate data using GIFs without being detected by EDR and other network monitoring tools. The technique assumes an already-compromised target.
Discovered by Bobby Rauch, the main component of this attack allows an attacker to create a reverse shell that delivers malicious commands via base64 encoded GIFs in Teams, and exfiltrates the output through GIFs retrieved by Microsoft's own infrastructure.
How does it work?
As reported by Lawrence Abrams in BleepingComputer, Microsoft agrees that this attack method is a problem, however, it “does not meet the bar for an urgent security fix.” They “may take action in a future release to help mitigate this technique.” Microsoft is acknowledging this research but asserting that no security boundaries have been bypassed.
While Rauch claims that indeed “two additional vulnerabilities discovered in Microsoft Teams, a lack of permission enforcement and attachment spoofing”, Microsoft argues, "For this case… these all are post exploitation and rely on a target already being compromised.” Microsoft is asserting that this technique is using legitimate features from the Teams platform and not something they can mitigate currently.
In accordance with Microsoft's assertions, indeed this is the challenge many organizations face — there are configurations and features that threat actors can exploit if not hardened. A few changes to your tenant’s configurations can prevent these inbound attacks from unknown Teams tenants.
There are security configurations within Microsoft that if hardened can help to prevent this type of attack.
Microsoft Teams by default allows for all external senders to send messages to users within that tenant. Many organization admins likely are not even aware that their organization allows for External Teams collaboration. You can harden these configurations:

Endpoint security tools are your first line of defense against suspicious activity such as accessing the device's local teams log folder which is used for data exfiltration in GIFShell. You can ensure your entire organization's devices are fully compliant and secure by using your XDR / EDR / Vulnerability Management solution, like CrowdStrike or Tenable.
You can even go a step further and integrate an SSPM (SaaS Security Posture Management) solution, like Adaptive Shield, with your endpoint security tools to gain visibility and context to easily see and manage the risks that stem from these types of configurations, your SaaS users and their associated devices.


The ease with which SaaS apps can be deployed and adopted is remarkable, but it has quickly become a double-edged sword. On one hand, the availability of SaaS tools enables employees to work from anywhere. For IT and security teams however, the adoption of SaaS apps has become a daunting endeavor.
CISOs and security professionals have cited SaaS misconfigurations as a leading cause (up to 63%!) of security incidents in the past year. Misconfigurations are brought on by many different factors, the top three can be summed up into the three V’s:
There is an inherent paradox in SaaS security: Most SaaS app owners and admins, the ones responsible to manage the app’s security settings and have profound control, are individuals who sit outside the security department. Business departments own these apps because it's what allows them to do their job efficiently. However, these individuals are untrained and not focused on security measures; these admins are working towards their departmental KPIs. For instance, Hubspot is usually owned by the marketing department, likewise, Salesforce is often owned by the business and/or Sales department, etc. Yet, it’s the security team's responsibility to secure the organization's SaaS app stack and they cannot effectively execute this task without full control and visibility of the SaaS app. The security teams often end up in the dark about the security protocols in place — and need to proactively check in with the numerous app owners to see the configurations and remediate any issues.
If you break it down by the numbers, a typical enterprise has hundreds to thousands of SaaS apps. Each app has as many as hundreds of global settings such as which files can be shared, whether MFA is required, if recording is allowed in video conferencing, and more. Multiply this number by thousands – or tens (or even hundreds) of thousands – of employees.
Security teams must familiarize themselves with each application’s specific set of rules and configurations and ensure they are compliant with their company’s policies. With hundreds of app setups and tens of thousands of user roles and privileges, this quickly becomes an unsustainable scenario. Not to mention the SaaS-to-SaaS apps that are being added to the organization’s ecosystem without the security team’s knowledge.
The SaaS app environment is dynamic and continuously evolving. Employees consistently are added or removed, new apps onboarded with permissions and configurations set, reset, changed and/or updated. There are also continuous, compliance updates to meet industry standards and best practices (NIST, SOC2, MITRE, etc.) that need to be checked. Security teams need to continuously ensure that all configurations are correctly configured company-wide, with no exceptions. Considering the high volume of apps and configurations, as mentioned in the first ‘V’, this translates to hundreds of hours of continuous work and effort that is just not sustainable.
Companies aren’t about to slow down their adoption of SaaS apps and with each new app integration comes a series of new configurations to secure. To regain control, organizations need a solution that can resolve all the challenges brought on by these 3 Vs: Volume, Velocity, and Lack of Visibility.
Organizations can ease the burden of misconfiguration management by implementing an automated solution, such as SSPM, that offers:
Misconfiguration management is one of the crucial areas security teams need to secure, but not the only area that secures an organization’s SaaS stack. Other key areas include SaaS-to-SaaS Access and Discovery and Device-to-SaaS User Management. The right SSPM solution will allow security teams to not only gain control of their misconfigurations but also these additional use cases to ensure an organization’s overall SaaS security.


According to Okta's Business of Work report, large companies use 187 different SaaS apps on average, and this number is only growing—Gartner reports that end-user spending on SaaS will reach more than $171 billion in 2022.
As this investment trend continues, new critical SaaS challenges emerge beyond the classic use case of misconfiguration and user permissions management, such as SaaS-to-SaaS access and device-to-SaaS-user posture management. This blog will give a brief overview of the trends in SaaS security.
An Unrelenting Volume Of Misconfigurations
Core SaaS offerings such as Office 365, Slack, Zoom and Salesforce, as well as the myriad of other SaaS apps that companies have deployed, are vital to a business's day-to-day operations. While these benefits are widely recognized, many companies are just now beginning to learn about the risk they introduce to the company.
Case in point, while app providers build in native security settings and configurations designed to protect businesses, the solutions can only be as secure as their weakest security control. This means that it is up to the organization to correctly configure all settings, continuously.
While that may seem straightforward, many don't consider how apps are like snowflakes when it comes to their build and security configurations—each has unique terminology, UI, etc. It is the security team's job to learn every app's "language." While that might not seem insurmountable, consider that many enterprises today have thousands of employees relying on hundreds of apps. This creates a chaotic SaaS environment where manual audits become impossible and unsustainable.
SaaS-to-SaaS Access Discovery and Control
Another growing SaaS challenge stems from SaaS-to-SaaS apps connected to the company’s core SaaS applications, also known as SaaS-to-SaaS supply chain. Today, employees are frequently prompted to give permission for one SaaS app to connect with another, and, for the most part, they oblige. That's where the problem begins. Today most users view this scenario from a productivity perspective—if they connect their SaaS apps, it will allow them to work more efficiently and ultimately help the business achieve its goals.
Every day, people give apps permission to connect with their Google Workspace or M365 environment (for example). By just clicking "accept," they give these apps permission to provide a new avenue for threat actors to gain access to valuable company data.
Now imagine this practice is happening throughout a business's workforce unbeknownst to the security team. The security team needs to see:
1. The SaaS apps that are being granted access to business-critical apps.
2. Which of these apps pose the most risk by the level of scopes (permissions) being given.
3. Which users, most especially the privileged users, granted them.
The security team needs to be equipped to decide whether to revoke access to these apps to the core SaaS apps, protecting the business yet still ensuring that the employee maintains the functionality required to do their job.
Device-To-SaaS Posture Management: The SaaS Security Zero-Trust Approach
In today’s hybrid working world, security teams must contend with threats of users accessing their SaaS applications from unsecured devices. While accessing a SaaS app via a mobile device helps boost productivity, it adds another challenge to the security team. It can pose a high level of risk for an organization, especially when the device owner is a highly privileged user.
To remediate potential threats, security teams need to be able to correlate SaaS app users, roles and permissions with their associated devices' hygiene. This end-to-end tactic enables a holistic zero-trust approach to SaaS security that is only now coming into the picture.
The Whole SaaS Security Picture
The bottom line is that checking for misconfigurations and misappropriated user roles and permission within business-critical SaaS apps is the classic SaaS Security Posture Management (SSPM). However, if the organization adopts a zero-trust approach, it is worth considering SaaS-to-SaaS access and device-to-SaaS-user monitoring and management an integral part of SSPM.
This is an excerpt from an article that was published in Forbes Council on August 10, 2022.


Typically, when threat actors look to infiltrate an organization’s SaaS apps, they look to SaaS app misconfigurations as a means for entry. However, employees now use their personal devices, whether their phone or personal laptop, etc. to get their jobs done. If the device’s hygiene is not up to par, it increases the risk for the organization and widens the attack surface for bad actors. And so, Endpoint (Device) Protection — through EDR, XDR, and vulnerability management solutions – has arisen as a critical factor in SaaS Security.
The challenge in remediating the threats posed by endpoints and devices lies in the ability to correlate between the SaaS app users, their roles, and permissions with their associated devices' compliance and integrity levels. This end-to-end approach is what's needed for the organization to implement a holistic, zero-trust approach for their SaaS Security.
Not a simple feat, however, automated SaaS Security Posture Management solutions, like Adaptive Shield, can now provide visibility that correlates the SaaS user and their associated devices with the device’s hygiene score.
How do you classify high-risk devices in the context of SaaS security?
Devices that are owned, or used by users with high levels of permissions to the company’s core SaaS apps. For example, someone who has high levels of access to the company’s CRM can present a high risk to the company if their device is vulnerable and this needs to be remediated immediately. These high-risk devices serve as a critical threat vector to an organization’s SaaS environment.
Security teams should continuously map devices to their users and their associated permissions to get a handle on which devices/users pose the highest risk.
As mentioned, the more privileged the user, the higher their device is at risk. To gain deep observability into the user, app and device posture, security teams need to check the hygiene of their users’ devices, for example up-to-date OS configurations, and any vulnerabilities. With that assessment and score in hand, security teams can map and monitor the user’s SaaS app access (in addition to, of course, securing the SaaS apps themselves).
Once these cross references are in place and accessible, organizations can enable “soft” enforcement enhancements, through policies and organizational best practices. This way security teams can monitor risks and threats without severely limiting the user.
Zero-trust is a concept much batted about in cybersecurity vernacular today. While many consider it a buzzword, its meaning represents an important approach that can not be emphasized enough. To wholly secure the organization’s SaaS stack, end-to-end, and continuously, calls for a holistic and automated solution.
Adaptive Shield has been built to resolve not only the need for management of the SaaS app configurations themselves, but also the devices the organization’s employees use. (Not to mention third party app access — and you can read more about that here.) When integrated with MDM (mobile device management) solution, Adaptive Shield will pull the device data and map the device to the owner.

By looking at the device posture while conducting a SaaS security assessment, organizations can achieve a holistic zero trust approach.


It's no secret that SaaS-to-SaaS apps can boost productivity, enable remote and hybrid work and are overall, essential in building and scaling a company's work processes.
It's an innocuous process much like clicking on an attachment was in the earlier days of email -- people don't think twice when connecting an app they need with their Google workspace or M365 environment, etc. Simple actions that users take, from creating an email to updating a contact in the CRM, can result in several other automatic actions and notifications in the connected platforms.
As seen in the image below, the OAuth mechanism makes it incredibly easy to interconnect apps and many don't consider what the possible ramifications could be. When these apps and other add-ons for SaaS platforms ask for permissions' access, they are usually granted without a second thought, not realizing that these addition connections present more opportunities for bad actors to gain access to their company's data.

How Do SaaS-to-SaaS Apps Work?
OAuth 2.0 has greatly simplified authentication and authorization, and offers a fine-grained delegation of access rights. Represented in the form of scopes, an application asks for the user's authorization for specific permissions. An app can request one or more scopes. Through approval of the scopes, the user grants these apps permissions to execute code to perform logic behind the scenes within their environment. These apps can be harmless or as threatening as an executable file.
There are four recommended ways to help secure a company's SaaS stack. Here's what a security team can share with employees and handle themselves to mitigate SaaS-to-SaaS app access risk.
The first step in cybersecurity always comes back to raising awareness. Once the employees become more aware of the risks and dangers that these OAuth mechanisms present, they will be more hesitant to use them. Organizations should also create a policy that enforces employees to submit requests for third party apps.
Security teams should gain visibility into every business critical app and review all the different third party apps that have been integrated with their business-critical SaaS apps - across all tenets. One of the first steps when shrinking the threat surface is gaining an understanding of the full environment.
Once the security team knows which third party apps are connected, they should map the permissions and the type of access that each third party app has been given. From there they will be able to see which third party app presents a higher risk, based on the higher level of scope. Being able to differentiate between an app that can read versus an app that can write will help the security team prioritize which needs to be handled first.
In addition, the security team should map which users granted these permissions. For example, a high-privileged user, someone who has sensitive documents in their workspace, who grants access to a third party app can present a high risk to the company and needs to be remediated immediately.
SaaS Security Posture Management solutions can automate the discovery of 3rd party apps. The right SSPM solution, like Adaptive Shield, has built-in logic that maps out all the 3rds party apps with access to the organization's SSPM integrated apps. This visibility and oversight empowers security teams so whether a company has a 100 or 600 apps, they can easily stay in control, monitor and secure their company's SaaS stack.
To secure a company's SaaS stack, the security team needs to be able to identify and monitor all that happens within their SaaS ecosystem. SaaS-to-SaaS access is just one use case in the SaaS Security Posture Management picture (take a look at the next addition in the series, SaaS-Device user protection).
Most existing cybersecurity solutions still do not offer adequate protection or a convenient way to monitor a company's SaaS stack, let alone the communications between their known apps and platforms, leaving companies vulnerable and unable to effectively know or control which parties have access to sensitive corporate or personal data.
Organizations need to be able to see all the configurations and user permissions of each and every app, including all the SaaS-to-SaaS apps that have been granted access by users. This way security teams can retain control of the SaaS stack, remediate any issues, block any apps using too many privileges and mitigate their risk.


It’s not a new concept that Office 365, Salesforce, Slack, Google Workspace or Zoom, etc. are amazing for enabling the hybrid workforce and hyper productivity in businesses today. However, there are three main challenges that have arisen stemming from this evolution: (1) While SaaS apps include a host of native security settings, they need to be hardened by the security team of the organization. (2) Employees are granting 3rd party app access to core SaaS apps which pose potential threats to the company. (3) These SaaS apps are accessed by different devices without their device hygiene score even being checked.
It’s not an easy task to have every app setting properly configured — at all times. The challenge lies within how burdensome this responsibility is — each app has tens or hundreds of security settings to configure, in addition to thousands of user roles and permission in a typical enterprise, compounded by the many compliance industry standards and frameworks that organizations strive to follow.
The complexity to secure SaaS apps is only increased by the fact that often the SaaS app owner sits outside the security team, in the department that most uses the app (think Sales has CRM app, Marketing has automation app) — and they are untrained and not focused on the security upkeep of the app. It all amounts to just how burdensome and unrealistic it is to expect security teams to be able to stay in control of the organization’s SaaS stack.
OAuth 2.0 has greatly simplified authentication and authorization, and offers a fine-grained delegation of access rights. Represented in the form of scopes, an application asks for the user's authorization for specific permissions. An app can request one or more scopes. Through approval of the scopes, the user grants these apps permissions to execute code to perform logic behind the scenes within their environment. These apps can be harmless or as threatening as an executable file.
When it comes to local machines and executable files, organizations already have control built in that enables security teams to block problematic programs and files. It needs to be the same when it comes to SaaS apps.
From first entry through to the device posture, security teams need to be able to identify and manage the risks coming from SaaS users and their associated devices. A device with a low hygiene score poses a high risk depending on which apps this employee is using. In the case of a highly privileged user, an unsecured device can pose an even higher level of risk for an organization. The security team needs the ability to correlate SaaS app users, their roles and permissions with their associated devices’ compliance and integrity level. This end-to-end approach enables a holistic zero-trust approach to SaaS security that is only now coming into the picture.
That’s why Gartner named SaaS Security Posture Management (SSPM) as a MUST HAVE solution to continuously assess security risks and manage the SaaS applications' security posture in the “4 Must-Have Technologies That Made the Gartner Hype Cycle for Cloud Security, 2021.” Other cloud solutions don’t offer preventative coverage. For example, a CASB solution is event-driven; CASB will alert the organization to a SaaS leak or breach only once it has occurred.
Our SSPM solution comes into play to enable security teams to identify, analyze, and prioritize misconfigurations as well as provide visibility to 3rd party apps with access to their core apps and Device-to-SaaS-User posture management.
This is an excerpt from an article that was published in The Hacker News on July 11, 2022.


Tel Aviv – July 6, 2022, Adaptive Shield today announced that its SaaS Security Posture Management (SSPM) platform has been recognized as a Trust Award finalist in the Best Cloud Security Posture Management Solution category for the 2022 SC Awards. Now in its 25th year, the SC Awards are cybersecurity’s most prestigious and competitive program where finalists are recognized for outstanding solutions, organizations, and people driving innovation and success in information security.
“Adaptive Shield and other Trust award finalists reflect astonishing levels of innovation across the information security industry and underscore vendor resilience and responsiveness to a rapidly evolving threat landscape,” said Jill Aitoro, Senior Vice President of Content Strategy at CyberRisk Alliance. “We are so proud to recognize leading products, people and companies through a trusted program that continues to attract both new entrants and industry mainstays that come back year after year.”
“Company reliance on cloud-native applications continues to accelerate, and with that come a host of new security challenges, especially managing configurations across hundreds of unique apps. To remediate SaaS issues and fully realize the benefits of these investments, businesses are turning to SaaS Security Posture Management (SSPM) solutions,” said Maor Bin, co-founder and CEO of Adaptive Shield. “We are thrilled to be named a finalist in the ‘Best Cloud Security Posture Management Solution category.’ This recognition validates the incredible work of our team and the platform’s success in delivering businesses the visibility needed to regain control of their entire SaaS environment.”
The 2022 SC Awards were the most competitive to date, with a record 800 entries received across 38 categories - a 21% increase over 2021. Entries for the SC Awards were judged by a world-class panel of industry leaders, from sectors including healthcare, financial services, manufacturing, consulting, and education, among others.
Winners will be announced during SC Awards week, scheduled to begin on August 22, 2022. A Meet the Winners networking reception celebration will take place during InfoSec World 2022, September 27th in Orlando, Florida.
About CyberRisk Alliance
CyberRisk Alliance (CRA) is a business intelligence company serving the high growth, rapidly evolving cybersecurity community with a diversified portfolio of services that inform, educate, build community, and inspire an efficient marketplace. Our trusted information leverages a unique network of journalists, analysts and influencers, policymakers, and practitioners. CRA’s brands include SC Media, SecurityWeekly, ChannelE2E, MSSP Alert, InfoSec World, Identiverse, Cybersecurity Collaboration Forum, its research unit CRA Business Intelligence, and the peer-to-peer CISO membership network, Cybersecurity Collaborative. Click here to learn more.
The original PR was released through Businesswire on July 6, 2022.


Adaptive Shield is officially On the Radar in Omdia's report for an innovative solution making a big impact in the SaaS security space.

In the report, Rik Turner, Senior Principal Analyst at Omdia, discusses accelerated cloud adoption, the rapid increase in threats, and ongoing shortage of skilled security professionals, that is driving the cybersecurity world towards more proactive approaches, after a decade in which reactive (detect and respond) ones held sway.
Rik Turner specializes in cybersecurity technology rents, IT security compliances, and call recording. His reports offer insights and analysis on the market evolution to help users determine what kind of technology and vendor they should pursue. Prior to joining Omdia RIk worked as an IT journalist, specializing in networking and security.
Rik Turner begins his analysis of Adaptive Shield with:
Adaptive Shield's SSPM Platform combines proactive, continuous, and automated monitoring capabilities with a built-in knowledge base of compliance standards and benchmarks. Once in place, it delivers visibility into the whole SaaS ecosystem, sending an alert whenever it detects a security misconfiguration. Security issues can be fixed automatically, or a ticket can be created for the customer’s security team, with detailed remediation steps.
By taking a close up look at the platform, Rik examines how the uses application programming interfaces (APIs) to query the apps and build a picture of the customer’s SaaS estate, highlighting misconfigurations, mistakes in set-up, and excessive access permissions.
The customer’s security team is provided with a user interface in which they can view how effectively each of their security controls, such as access control or their endpoint security platform, is addressing the vulnerabilities Adaptive Shield is detecting, with the ability to filter their view by app, security control, or compliance requirement, for instance.
With every SaaS application is a world unto itself each with its own API, Rik emphasizes the importance of an SSPM solution that is able to integrate a variety of apps. SaaS security
As Rik sees it, while Adaptive Shield is currently staying within the walls of the SSPM market segment, it plans to broaden its offering and enhance SaaS security by looking at the device posture of the app user and 3rd party app discovery. He predicts part of this will come through partnerships with other security vendors, such as those in endpoint security and vulnerability management. As the SSPM market continues to grow, so is it expected of Adaptive Shield.


The old days of buying new software, installing it on the company servers, and making sure everything works is gone. All hail the new IT king - SaaS platforms. Ready to go from the start, no installation needed, no hardware involved, and easy to connect the organization and its users. An IT department haven of sorts. Yet the ease of connection should not create a false sense of security. Every SaaS platform’s settings need to be hardened to protect the company's assets. While the settings are built-in natively, configurations are not always enabled by default, and are critical for SaaS security.
The responsibility to ensure the SaaS app settings are set correctly falls on the shoulders of the security team who are already overburdened with work. This blog post aims to ease that burden by providing a basic SaaS security checklist to make sure the basics are covered. I do want to stress the importance of tightening all security configurations. This list is not all encompassing, and there are other configurations that need to be checked that are SaaS-app specific.
One of the most important tools to secure a SaaS platform, and sadly one of the least properly set up tools, is SSO.
Single Sign On, SSO, is a powerful tool for taking care of one of the biggest problems in the SaaS world - too many passwords and access control. Every employee has access to dozens of SaaS platforms, and each and every one requires a username and password. This is a security disaster waiting to happen with users recycling passwords, writing them down on post-it notes, and saving them on the computer in an insecure manner.
SSO enables you to avoid all of this, and just connect using the organization's SSO. As the name suggests, Single Sign On eliminates this to a single place to log into. Every organization should have an SSO, and that SSO should be connected to each new SaaS integration app used by the organization.
Now add to the SSO an IdP (Identity provider) / Federation where supported, and you are set to have a much easier life managing any SaaS platform. This allows your users to be managed and for you to control access to the different SaaS apps from one central point.
Multi Factor Authentication (MFA), previously known as Two Factor Authentication (2FA), is a critical security feature, necessary not only for organizations, but also for private accounts. MFA is a simple concept, requiring in a log-in to not only provide a password but also a second form of authentication such as a physical key, SMS, authentication app, and others. The reason for adding this second layer of protection is first and foremost the importance of not basing the whole security of an account on a single point of failure. The second reason is that passwords are not the best form of authentication. Users recycle passwords, use easy to guess or brute force passwords, write them down on pieces of paper, and other human behavior that can compromise the password. Therefore, adding an additional layer of security is very much needed.
Not all SaaS apps allow you to connect them to an SSO, and sometimes you’ll want to allow some users to bypass SSO. Admins, for example, should be allowed to bypass SSO so they can manage the SaaS app at all times, especially if there is an SSO failure. When you allow users to bypass SSO, or don’t use SSO at all - a strong password policy and adding MFA becomes your first line of defense.
The SSO is another place that needs special care. Since, of course, there is no SSO for the SSO app, the access to the SSO account needs MFA and a strong password policy. This is the key to the kingdom, and should be secured appropriately.
When deciding on the additional factor to use for MFA, it is recommended to avoid using SMS (and use instead a physical key or an authenticator app). The reason for this is that it is relatively easy to intercept and fake SMS messages. Attacks on the SS7 protocol that are used, among other purposes, for SMS are well documented and have been used for attacking accounts that use SMS for MFA.
A strong password policy sounds like a simple matter. Force 8 characters, upper case, lower case, number, special character, and rotate the password every 90 days. This is what most enterprises do, yet this is not usually the default of a SaaS integration, and therefore should be configured to match your organization's password policy. Setting up a strong password policy can help minimize security risks of an account breach. Together with MFA, it is an extremely good protection measure.
If your organization does not have a password policy, or is in a position to change it, we recommend following the updated recommendation of NIST, the US National Institute of Standards and Technology, which is well known in the security world as the leader in recommendations and standards. NIST recommends, based on the NIST Special Publication 800-63B, the following password policy:
Users will recycle passwords, write them down, and choose easy passwords to brute force if they are forced to switch passwords frequently. It is better to have a very strong password, and change it only if there is a chance it was compromised.
Combinations of numbers, special characters, and lower-upper cases usually follow the format of “Password1!”. This is easy to brute force. Much better to use a very long password that is easy to remember - such as “MyPetAlligatorAteMySchoolHomework”. Use a minimum of 8 characters, but consider forcing at least 12 and encourage users to have 16 characters for their passwords. The example above is 33 characters long but extremely easy to remember and very hard to brute force (entropy of roughly 150 bits).
Don’t allow a user to endlessly try to put in the correct password. This is usually a brute force attempt. Or just a really hard password to remember. In any case, it shouldn’t be allowed. We recommend limiting it to no more than 10 attempts.
Screen new passwords against published passwords, dictionaries, the name of the user, and other easy to brute force. Many SaaS providers already have such tools available to enforce.
Another important aspect of setting up a SaaS app in your organization is planning the governance scheme. Many times this is ignored, and then all users get very high privilege roles and scopes. This is a major security and privacy risk, since it only takes one highly privileged account to be breached, and then the whole SaaS tenant is at risk.
It is recommended to use the principle of least privileged access needed. This mindset and security policy is one that is practiced wherever sensitive information is to be found. The idea is that every user should get exactly the role and scopes needed to perform his or her work, and nothing else. If an employee does not need admin access, they shouldn’t receive such a role.
Yet it is important not to go on the extreme with this philosophy. Every organization should have at least 2 org admins for each SaaS. This allows continuity in case one of the admins has a problem with accessing the SaaS. Also, it is recommended that the bigger the tenant is, the more admins are added to help monitor the SaaS and assist users where needed. It is difficult to strike the balance between too few admins to manage the account and too many that there is a security risk. The key way to deal with this is to continually monitor the amount of admins, and have at least an annual review of all admins and decide what the limit should be.
Well done. You set up the SaaS app, all is working, hardened, and ready to go. But how do you know your SaaS security posture will stay secure overtime? Configurations can be changed, privileged roles granted, extra scopes given, data exposed and many other disastrous changes to the SaaS settings, you put so much effort into securing. The solution for this is to set up continuous monitoring for the SaaS, often called an Audit Trail. Make sure it is configured to record any security related change in the system. Then make sure alerts are set up so you don’t need to review the logs every day of every SaaS app that you have. With an SSPM solution like Adaptive Shield, your security team can continuously monitor their SaaS security posture and receive real-time alerts when configuration drifts happen.
Finally, it is recommended to send all the logs to a central source, such as SEIM. This allows you to monitor all the SaaS apps from one plane of glass. Also, it allows you to keep an independent source of truth regarding what has happened in your SaaS. This is very important if there is a breach, since it allows you to understand how this happened, when, and how the SaaS was affected.


After 2 years of virtual events, RSA Conference 2022 in San Francisco brought back face-to-face interaction. And wow, what an experience! From live sessions and parties to games and demos galore, RSA was packed with it all. Here’s a recap of Adaptive Shield at RSA.
Our CEO, Maor Bin took the stage at RSA to speak about a new SaaS vulnerability discovered by Adaptive Shield security researchers, within Microsoft’s OAuth application registration. Bin took the audience through a live demo of the vulnerability and demonstrated how it allows anyone to leverage the Exchange’s legacy API to create hidden forwarding rules in O365 mailboxes. But it didn’t stop there.

Bin’s Session was followed by a Birds of a Feather talk where he and a handful of security experts dove deeper into the vulnerability and its implications.

The CSA panel was made up of our CEO Maor Bin, CSA Global Vice President of Research John Yeoh, A10 Networks Vice President of Product Management Mikko Disini, Lacework Global Field CTO Chris Pedigo, and Orca Security Chief Executive Officer and Co-Founder Avi Shua. These leaders in cyber security discussed the risks organizations face in today’s digital world and whether security teams are properly supporting business transformation decisions. The panel dove into questions like, what are the challenges when tracking cloud and other digital assets, etc. It goes without saying that this session was insightful and thought provoking.
During RSA, Cyber Defense Magazine celebrated its 10th year of Global Infosec Awards. Cyber Defense Magazine shares cutting edge knowledge, real world stories and awards on the best ideas, products and services in the information technology industry.
We were thrilled to have Adaptive Shield named a winner of the 2022 Global InfoSec Awards as the Next Gen in SaaS/Cloud Security.
Over the 4 days at RSA our booth greeted many friendly faces. Our experts were always up and ready to chat with visitors and talk about SaaS security, SSPM, and give a live demo of the Adaptive Shield platform.

Everyone that visited our booth had the chance to play our game “How Fast Can You Fix Your SaaS Stack?”, where we tested people’s speed and knowledge to see who could configure 20 settings in under 30 seconds.
Players that got a score of 85% or higher got their pick from an assortment of games or toys, and our grand prize winner, Erick Binti, with a perfect score of 100% received a mini Apple speaker.

Our partner Torq joined us at our booth to give a demo of our paired solution. Torq is a no-code platform that’s purpose-built for security automation. Together with Adaptive Shield, Torq streamlines the deprovisioning process through automation, lifts the burden of manually auditing and deactivating accounts, and provides continuous visibility and control to increase the organization’s SaaS security posture.

To top off the hard day's work, Adaptive Shield co-sponsored the FOMO party with a live performance from the band, Incubus. With rock-out music, glowing bracelets, and tasty food, the FOMO party was definitely the place to be.


RSA 2022 was a great way to bring back in-person events and we are looking forward to seeing what next year has in store.



The SaaS app attack surface has widened and recent research shows that up to 63 percent of organizations have dealt with security incidents because of a SaaS misconfiguration. Lack of visibility, thousands of configurations for the security team to monitor and remediate, and too many departments with access are the leading causes of SaaS misconfigurations. There are unrealistic expectations on security teams and app owners (who sit outside the security team) to manually handle every app, configuration, and user role.
Gartner created the SSPM category in 2020 to address these challenges to refer to tools that enable security teams to have full and continuous visibility of SaaS security settings and configurations. Up until this category emerged, Cloud Security Posture Management (CSPM) and Cloud Access Security Broker (CASB) were considered able to secure the Saas stack. However, CSPM focuses on infrastructure-as-a-service security solutions, where SSPM is specifically catered to SaaS app technology. Meanwhile, while CASB and SSPM are both designed to address security issues within SaaS applications, CASB falls short as it identifies incidents after they happen. SSPM offers organizations a SaaS-specific, preventative solution that allows them to gain full visibility of their SaaS stack security.
According to our 2022 SaaS Security Survey completed in conjunction with CSA (Cloud Security Alliance), SSPM has become the top priority with 62% of companies currently using or planning to implement in the coming 24 months.
From the breadth of applications supported to the depth of its security checks, an SSPM provides organizations continuous, automated surveillance of all SaaS apps, alongside a built-in knowledge base to ensure the highest SaaS security hygiene. When comparing SSPM solutions there's a few key features to keep in mind to make sure your business is getting the best SaaS security.
When evaluating different SSPM the first thing to look out for is its ability to integrate all your needed SaaS apps. Every organization uses at least a handful of SaaS apps if not hundreds, each with their own unique settings. Any app can pose a risk and smaller apps often serve as a gateway for an attack, this is why it’s crucial to have every app to be fully integrated. As a rule of thumb, look for an SSPM with a minimum of 30 integrations that are adaptable and able to run checks on every data type to protect against misconfigurations.
The other vital component to an effective SSPM is the expanse and depth of the security checks. Every SaaS app has its list of domains to monitor, such as: identity and access management, malware protection, data leakage protection, auditing, access control for external users, and so on.
This goes hand in hand with continuous monitoring and remediation. Part of an SSPM’s job is to not only detect the threats but to combat them. Remediating issues in business environments is a complicated and delicate task. The best SSPM solution should provide context about each configuration, enable you to easily monitor, and set up alerts. When alerts do happen, the platform should map out remediation. This way, when misconfigurations do happen, a business is left vulnerable for a minimal window of time.
Part of what enables an SSPM solution to provide full visibility is its user and device inventory. User inventory takes into account all the different SaaS apps used by different employees and the level of access which they have. When a user fails a security check, security teams are immediately notified to enable a seamless user management and investigation across all SaaS apps. Device inventory allows security teams to see which devices have access to company SaaS apps and manage the risk based on the device hygiene score.
An effective SSPM maps out the security controls of major compliance frameworks such as SOC 2, ISO 27001 and NIST Special Publication 800-53, in order to provide in-depth security checks by app, user, severity or any other metric indicating misconfigurations. When misconfigurations or failed security checks do happen, security teams are not only alerting immediately, they also get a step-by-step remediation description to see exactly how to fix the SaaS misconfiguration
Another aspect that is growing in importance on the SaaS security landscape is that of 3rd party app access. Users don't think twice about connecting an app with their Google Workspace or M365 but these automatic actions are becoming a threat in the corporate cybersecurity landscape. That being said, 3rd party app access is also a key feature that helps boost companies’ productivity and enable remote work. Adaptive Shield, for example, gives security teams visibility into these business-critical apps and reviews the permission and access levels of different 3rd party apps being integrated to reduce the severity of a threat.
We are honored that Gartner has named Adaptive Shield a 2022 Gartner Cool Vendors™ in Application Security: Protection of Cloud-Native Applications. We believe that this is a powerful step not just for Adaptive Shield, but for the field of SaaS Security Posture Management (SSPM).


When it comes to keeping SaaS stacks secure, IT and security teams need to be able to streamline detection and remediation of misconfigurations in order to best protect their SaaS stack from threats. However, while companies adopt more and more apps, their increase in SaaS security tools and staff has lagged behind, as found in the 2022 SaaS Security Survey Report.
The survey report, done in collaboration with CSA, dives into how CISOs today are managing the growing SaaS app attack surface and the steps they are taking to secure their organizations. While there are 7 significant takeaways from the report, this blog takes a closer look at the 5th finding - how the use of an SSPM reduces the amount of time it takes to to detect and remediate SaaS misconfigurations.
The report finds that at least 43% of organizations have experienced a security incident as a result of a SaaS misconfiguration, however with another 20% being “unsure”, the real number could be as high as 63%. These numbers are particularly eye-opening when compared to the 17% of organizations experiencing security incidents due to an IaaS misconfiguration. Bearing this in mind, the question follows: how fast are SaaS misconfigurations detected and how long does it take to remediate the issue? In order to answer these questions, it's important to make a distinction between organizations that have implemented an SSPM solution and those that have not.
For organizations that are yet to onboard an SSPM, the IT and security teams can only manually check the apps’ many configurations to secure their SaaS stack. This means security teams need to not only be on top of remediating misconfigurations but also conducting regular security checks in order to manually detect any of these misconfigurations. The longer either of these actions take to be completed, the longer the company is exposed to threats.
One of the major problems for organizations’ security teams is the overwhelming amount of manual work. Companies today are reliant on dozens upon dozens of business-critical apps each with hundreds of configurations, which then need to be set according to the hundreds to thousands of employees.
Nearly half (46%) of the survey respondents, as seen in figure 2, check their SaaS security monthly or less frequently, and another 5% don’t check at all. It seems that security teams are overwhelmed with the workload, and are struggling to stay on top of all the settings and permissions. As organizations continue to adopt more and more apps, their gap of visibility into all configurations grows.

When a security check fails, security teams must then go in and understand why exactly the check failed and the best course of action to fix it. Approximately 1 in 4 organizations, as seen in figure 3, take one week or longer to resolve a misconfiguration when remediating manually. Overall, security teams trying to manage their SaaS security are not only overwhelmed but are also in turn leaving the organization exposed for a longer period of time.

Organizations using SSPM are able to conduct security checks more often and remediate misconfigurations within a shorter time frame. An SSPM enables security teams to conduct frequent checks in compliance with both industry standards and company policy. The 2022 SaaS Security Survey Report found that the majority of these organizations (78%) run security checks once per week or more often, as seen in figure 4.

When a misconfiguration is detected, 73% of organizations using an SSPM resolved it within a day, and 81% resolved it within the week, as seen in figure 5. A good SSPM solution however will not only evaluate failed security checks caused by misconfigurations, but will also assess risk and configuration weakness — and provide exact instruction on how to remediate the issue.

SSPM not only reduces the workload on security teams, but also eliminates the need for them to be experts on each SaaS app and its settings. The data presented in the 2022 SaaS Security Survey Report highlights the drastic differences between companies using SSPM and those not, showing how valuable SSPM is to SaaS security detection and remediation.


Every year the leaders and entrepreneurs of the cybersecurity world come together for four days for the annual RSA Conference. During these four days, visitors gain insight, join conversations, and experience solutions that could make an impact on their businesses and careers.
Finally, after many years of the event being virtual, RSA is back in its physical form. This year's conference will feature numerous presentations from industry leaders offering unique insights and fresh perspectives on the world of cloud and SaaS security. We have gathered a list of the 13 top talks taking place at RSA 2022.
Pete Chronis, SVP,CISO, ViacomCBS
Ami Luttwak, Chief Technology Officer & Co-Founder, Wiz
John Yeoh, Global Vice President of Research, Cloud Security Alliance
Tuesday, Jun. 7, 2022 9:40 AM - 10:30 AM PT
The shared responsibility model is broken. As companies fail to keep up with cloud complexity, vendors and cloud providers each continue to maintain inconsistent sets of cloud misconfigurations to track. This panel of experts will debate the need for extending the current CVE model to become more cloud friendly and discuss how CSA is leading the charge.
Maor Bin, CEO and co-founder of Adaptive Shield
Wednesday, Jun. 8, 2022 1:15 PM - 2:05 PM PT
Adaptive Shield security experts found a new SaaS vulnerability within Microsoft’s OAuth application registration. This vulnerability allows anyone to leverage the Exchange’s legacy API to create hidden forwarding rules in O365 mailboxes. This talk will demo the OAuth registration process in Microsoft as well as the use of the new vulnerability.
Mary Yang, Chief Marketing Officer, LookingGlass Cyber Solutions
Monday, Jun. 6, 2022 10:50 AM - 11:40 AM PT
For many organizations, reducing their attack surface has become a critical goal. Yet vulnerabilities and vectors continue to be exploited. Organizations are left asking themselves what they can do to get a better handle on their attack surface? This Birds of a Feather will dive into not only the growing challenges but also the best practices for managing one’s attack surface.
Tal Darsan, Manager, Managed Cybersecurity Services, Cato Networks
Etay Maor, Sr. Director Security Strategy, Cato Networks
Monday, Jun. 6, 2022 2:20 PM - 3:10 PM PT
Network based threats have evolved and are finding new ways to evade security solutions. This session will take a look at different case studies and techniques that organizations can use when implementing network based threat hunting and show how teams can face cloud native threats with a cloud native security approach.
Michael Coden, Senior Advisor, Boston Consulting Group
Colin Troha, Managing Director, Boston Consulting Group
Tuesday, Jun. 7, 2022 8:30 AM - 9:20 AM PT
The concept of work has shifted from office buildings to something that can be done anywhere at any time. Point products, VPN, and “trusted” network zones no longer provide the protection they once did. In fact, now they introduce risk. Securing hybrid work requires a fundamental change that challenges traditional security approaches and exposes legacy architectures.
Rohit Joshi, SecDevOps Engineer, SAP
Joseph McCrea, DevSecOps Engineer, SAP
Wednesday, Jun. 8, 2022 8:30 AM - 9:20 AM PT
When migrating to public cloud, organizations introduce new attack surfaces which are usually the exploitation of misconfigured resources. It raises the question: how are threats detected in a cloud that contains millions of resources? This talk will discuss the journey from security policy documentation to scanning and detecting security compliance violations in product infrastructure from the start of the development life cycle.
Petko Stoyanov, Global CTO, Forcepoint
Wednesday, Jun. 8, 2022 1:15 PM - 2:05 PM PT
The security industry has reached a breaking point. The never ending line of technologies are doing the same thing over and over. Analysts have agreed that true platforms are the new path forward. This session offers insights on what distinguishes “real” platforms and how they’re making security simpler.
Nir Ohfeld, Senior Security Researcher , Wiz
Shir Tamari, Head of Research, Wiz
Wednesday, Jun. 8, 2022 1:15 PM - 2:05 PM PT
A new risk for cloud users has arised that relates to software being run by the cloud providers within the customer cloud. A chain of critical vulnerabilities found in Azure built-in VM agents affecting almost every customer using Azure. The question addressed in this talk then becomes: who owns the fix?
Sander Vinberg, Threat Research Evangelist, F5
Wednesday, Jun. 8, 2022 1:15 PM - 2:05 PM PT
This presentation features the 5th annual Application Protection report from the F5 Labs team. The session will focus on the trends and data from multiple angles and help provide an overall picture of the application security threat landscape. The session will dive deep into application-related security breaches and cloud security with some never-before-seen data.
Maor Bin, CEO and Co-Founder of Adaptive Shield
John Yeah, Global Vice President of Research, CSA
Mikko Disini, Vice President of Product Management, A10 Networks
Avi Shua, Chief Executive Officer and Co-Founder, Orca Security
Jun. 6, 2022 9:45 AM - 10:30 AM PT
The last few years have shown an accelerated adoption of cloud products and services. Many organizations have moved quickly towards digital transformation in order to stay engaged with customers and employees and keep pace with the competition. What are the challenges when tracking cloud and other digital assets? Are businesses measuring the risk associated with these assets? The panel discusses the cybersecurity risks organizations face in today’s digital world and whether security teams are properly supporting business transformation decisions.
Tanya Janca, Founder and CEO, We Hack Purple
Monday, Jun. 6, 2022 8:30 AM - 9:20 AM PT
As security teams become vastly outnumbered, many organizations have responded with different program scaling methods, including building security champions programs. Which leads to questions: How does a security champions program work? How are champions selected? This talk outlines the path for success, touching on recruitment, engagement, teachings, recognition, reward, and more.
Christopher Romeo, CEO, Security Journey
Monday, Jun. 6, 2022 9:40 AM - 10:30 AM PT
Many people have a Security Champion program, but not all of them are effective. This session will map out the qualities of an elite Security Champion program in the DevSecOps world, for those who don’t have a program and those whose programs need a reboot.
Steven Lipner, Executive Director, SAFECode
Tony Sager, Senior VP and Chief Evangelist, Center for Internet Security
Monday, Jun. 6, 2022 2:20 PM - 3:10 PM PT
Many concepts discussed in software supply chain security are derived from old-fashioned material goods supply chains. The word "chain" is a broken metaphor for security. The "web" of software supply would be more appropriate. This session will present and discuss alternative models from other industries that developers should use. These are a mix of standards, some testing, and some enforcement.
These 13 talks can be a great kick off, inspiring middle, or a sweet ending to your RSA experience so make sure to pencil them into your schedule.
Claim your $150 discount on a conference ticket and make sure to visit us at booth #1655 in the Moscone South Expo for great prizes and fun games. We look forward to seeing you there!



“How many people do you know that clean their house once a quarter? …you have to keep a certain level of hygiene both in your house and your SaaS stack.”
Uttered by our CEO, Maor Bin, in a webinar with Omdia Senior Principal Analyst, Rik Turner about the growing need to take a proactive, automated approach to SaaS security. Here are some highlights from the webinar - catch the whole webinar in full here.
Rik Turner begins the webinar by reflecting on the emergence of SaaS apps in the early 1990s leading up to 2010. “The world of SaaS apps grew rapidly and for good reason,” Rik explains, “SaaS is so easy that once you’ve adopted it, someone in the next business unit comes and says ‘oh you guys are using that? That looks great’ and next thing you know half the company is using something that nobody in IT even sanctioned.” Security teams need control and visibility to all the configurations of the company’s SaaS apps in use.
By 2014, Cloud Access Security Broker (CASB) had reared its head as a powerful cloud security solution to address the above mentioned issue. CASBs proved effective in helping restore visibility to the IT and security teams, however, as a reactive solution, there was still no preemptive approach for giving visibility to all the (mis)configurations across the growing SaaS app stack. It wasn't long after that Gartner brought SSPM into the playing field with its SaaS specific security solution.
An SSPM’s job is to maintain continuous hygiene across a SaaS stack by continuously monitoring all the SaaS security risks and automatically identifying if all the native security controls are correctly configured. By doing so, SSPM offers businesses a preventative SaaS security solution.
The webinar pulls findings from the 2022 SaaS Security Survey Report to demonstrate the current state and perception of SSPM. Rik Turner highlights the significant correlation between SaaS misconfigurations and security incidents, showing that up to 63% of security incidents are caused by a SaaS misconfiguration.

“This kind of datapoint isn't very surprising. We are always talking about how configurations are the number one attack vectors. They’re the number one threat for companies when we’re talking about cloud security. These small mistakes can lead to very, very serious problems - account takeover, data leakage, and more,” asserts Bin.
SaaS apps have changed the way security and IT teams think about security. Gone are the days of security teams being experts on every company program or system. It becomes impossible for security teams to be familiar with the in and outs of every SaaS app. The fact of the matter is that while companies have quickly implemented new SaaS apps, they have lagged behind when growing their security teams and tools. There is a reported 81% increase in SaaS apps but only a 73% increase in security tools and a lesser 55% increase in security staff. This is causing security teams to be overburdened which in turn creates a cycle of companies leaving themselves exposed.

Simply put, security teams today don't have the capacity to manually configure every SaaS setting in an effective way. Nearly half of the security teams today attempting to do so are only checking their SaaS security settings monthly or less often — 15% are checking quarterly.
Meanwhile as Rik Turner points out, companies that have embraced SSPM have provided security teams with deep visibility into their SaaS stack security allowing them to deal with the misconfiguration threats.

Businesses and organizations are inseparable from the use of their SaaS apps. Bin and Turner address these issues and more in the full webinar, giving further insight to how the world of SaaS is growing and how SSPM is taking a proactive approach to securing businesses’ SaaS stacks.
“As these numbers show, once you introduce an SSPM, it dramatically improves an organization’s ability to detect and remediate these misconfigurations.” Turner.


Last year, we spearhead our first annual SaaS Security Survey Report, where the findings illuminated the SSPM landscape and where the market was holding. In the 2022 SaaS Security Survey Report, in collaboration with CSA, we examine the state of SaaS security in today’s enterprises and see how much the market and the overall space of SSPM has matured in just one year. This report gathers anonymous responses from 340 CSA members, CISOs and security professionals, to examine not only the growing risks in SaaS security but also how these different organizations are currently working to secure themselves. While there are many takeaways from the survey, these are our top seven.
Demographics
Before diving into the findings, here is some quick background information on the anonymous respondents. The majority (71%) of respondents were located in the Americas, another 17% from Asia, and 13% from EMEA. Of these participants 49% influence the decision making process while 39% run the process itself. The survey examined organizations from a variety of industries, such as telecommunications (25%), finance (22%), and government (9%). For more details regarding the demographics, please refer to full report.

Since 2019, SaaS misconfigurations have become a top concern for organizations, with at least 43% of organizations reporting they’ve dealt with one or more security incidents caused by a SaaS misconfiguration. However, since many other organizations state they are unaware if they had experienced a security incident, the number of SaaS misconfigured-related incidents could be as high as 63%. These numbers are striking when compared to the 17% of security incidents caused by IaaS misconfigurations.
So what exactly is the cause of these SaaS misconfigurations? While there are several factors to consider, the survey respondents narrow it down to the two leading causes – having too many departments with access to SaaS security settings (35%), and a lack of visibility into the changes in the SaaS security settings (34%). These are two related issues, neither of which are surprising given that lack of visibility was rated a top concern when adopting SaaS applications, and that on average organizations have multiple departments with access to security settings. One of the leading reasons for the lack of visibility is the fact that too many departments have access to security settings and many of these departments don't have proper training and focus on security.

It’s well-known that businesses are adopting more apps – this past year alone, 81% of respondents say that they have increased their investments in business-critical SaaS applications. On the other hand, investment in security tools (73%) and staff (55%) for SaaS security is lower. This dissonance represents an increasing burden on the existing security teams to monitor SaaS security.

46% of organizations that manually monitor their SaaS security are conducting checks only once a month or less, while 5% don't conduct checks at all. After discovering a misconfiguration, it takes additional time for security teams to resolve it. Approximately 1 in 4 organizations take one week or longer to resolve a misconfiguration when remediating manually. This lengthy timing leaves organizations vulnerable.


The flip side of the coin for finding #4 is that the organizations that have implemented an SSPM can more quickly and accurately detect and remediate their SaaS misconfigurations. The majority of these organizations (78%) utilize an SSPM to check their SaaS security configurations once a week or more. When it comes to resolving the misconfiguration, 81% of organizations using an SSPM are able to resolve it within a day to a week.


Third party apps, also called no-code or low-code platforms, can boost productivity, enable hybrid work, and are overall essential in building and scaling a company’s work processes. However, many users quickly connect 3rd party apps without considering what permissions these apps are requesting. Once accepted, the permissions and subsequent access granted to these 3rd party apps could be harmless or as malicious as an executable file. Without visibility into the SaaS-to-SaaS supply chain employees are connecting to their organization’s business-critical apps, security teams are blind to many potential threats.

Despite the category being introduced to the market two years ago, it is fast maturing. When assessing four cloud security solutions, SSPM receives an average rating of “somewhat familiar”. Furthermore, 62% of respondents report that they are already using an SSPM or plan to implement one in the coming 24 months.
The 2022 SaaS Security Survey Report offers insights into how organizations are using and protecting their SaaS applications. It is without a doubt that as companies continue to adopt more business-critical SaaS apps, there is more risk. To face this challenge head on companies should begin securing themselves through two best practices:
These kinds of best practices will provide support to security teams without preventing them or any other departments from doing their work.


Adaptive Shield’s SaaS Security Posture Management (SSPM) platform has transformed the way organizations secure and monitor their applications. In our latest update, we add a new dimension to improve accountability and reporting – the ability to measure SaaS Security posture by business unit, subsidiary, team, or any other bucket of choice
SaaS applications are used by every department, each of which relies on multiple applications for collaboration, data storage, and getting the job done. SaaS security is unique in the sense that it involves multiple stakeholders across the corporation, working together in an integrated fashion with clear ownership, tracking, and measurement. Adaptive Shield’s platform monitors each user, application, misconfiguration, and connected app that potentially puts SaaS data at risk.
Using the platform, organizations can easily assign applications to different domains for better tracking, including:

With this new Organization Domain view, Adaptive Shield can easily be used to manage security for independent and semi-independent subsidiaries. It enables department heads to easily report on the security posture of their applications and create benchmarks of excellence based on the corporate division.
The new view provides security and business teams with a wealth of information. It provides an at-a-glance understanding of the state of SaaS security by division. Each domain card includes an overall posture score and a breakdown of the number of apps that fall within posture score ranges. The domain card also shows the number of users, devices, and third-party applications that are connected to the department’s applications.
Nearly every element within a division’s card can be clicked on for a deeper dive. See all the apps included in the domain; drill down into users, devices, and third-party apps; and review security checks to see issues that are impacting posture.
Adaptive Shield continues to innovate and enhance our SSPM platform. Stay tuned for more updates and we continue to continually develop more features and tools to secure the SaaS stack.


Detection and response sit at the heart of any well-thought-out cybersecurity program. As resilient and strong as perimeter-based defenses are, most security professionals will concede that threats can make their way into the network, device, or application.
Detection and response tools come into play after the breach has occurred, but often are able to stop the threat actor from moving forward. You can think about this in terms of a bank robbery, where the bad guys sneak their way into the vault and get caught before they can get out with the cash. The bank robbers were able to avoid security outside the vault, but once they were inside, some type of threat detection system alerted police that a robbery was in process, and the criminals were stopped.
Detection and response are the last lines of defense. Sometimes they can completely prevent a cybersecurity incident from occurring at all, while other times they detect a breach in progress and are able to significantly limit the damage. However, for all the benefits of detection and response, there is still some confusion in the marketplace about these tools.

Detection and Response have made their way into the names of many security tools. Endpoint Detection and Response, Extended Detection and Response, and Network Detection and Response are just a few of the many tools used to secure corporate and government networks.
These detection tools are vital but are limited to the areas that they serve. Detecting malware threats within endpoint devices is certainly critical in a world where data is accessed by computers, tablets, and mobile phones. XDR often takes EDR one step further, gathering intelligence from networks, users, and workloads.
XDR can be confusing to security teams, who believe they have threat detection covered across their organization. While XDR is a powerful tool, it often lacks the context to threats that native tools have to offer. For example, XDR is capable of some network threat detection capabilities, but it is a far less rich solution than NDR, which limits false positives through network context and automated threat response.
Identity Threat Detection and Response (ITDR) is one of the newest areas of threat detection. ITDR turns its attention to users and looks for any types of threats emanating from a user account.
User security starts with credentials, MFA, and SSO. However, not every application or organization requires MFA and SSO, and even some that use SSO allow local login for app admins. If a user hands over credentials during a social engineering attack, and MFA is not enforced, the threat actor may have full access to the application.
This is where ITDR steps in. It combines data from user and entity behavior analytics (UEBA), app logs, and IP data to find behavioral patterns that indicate an attack is underway. While some of this data may be accessible to an XDR, that tool lacks the deep user knowledge to be very effective.
Click here to read more about ITDR and key capabilities
For example, ITDRs are able to distinguish between a legitimate user logging in on a cellular and land-line connection, which may appear as coming from two different geo-locations, and a threat actor logging in from a foreign or unknown locale. Using the ITDR, security teams aren’t pestered by a series of false positives, whereas detection and response tools that aren’t designed with an understanding of identity context will deliver false positives and lead to alert fatigue.

Today’s successful security teams are developing models based on domain specialization, data enrichment, and integration. It combines a number of tools, including ITDR, EDR, XDR, NDR, DDR (Data Detection and Response), and CDR (Cloud Detection and Response).
Part of this is due to changes within organizations. Most have moved away from centralization, with the proliferation of cloud processing and SaaS apps.
To keep up, security teams are using decentralized, loosely coupled tools using advanced and nested analytics to monitor for threats, using multiple vendors and open content. As threats are detected by the various tools, they are sent to a central orchestration engine, where they can be analyzed and acted upon.
As the cybersecurity landscape evolves and threats become more sophisticated, the importance of detection and response cannot be overstated. While perimeter-based defenses are essential, the reality is that threats can find their way into networks, devices, and applications. This is where detection and response tools play a critical role in mitigating the impact of breaches and cyberattacks.
EDR, XDR, NDR, and ITDR are just a few examples of the specialized solutions available. Each tool has its strengths, but organizations require a combination of these tools to detect threats.
ITDR emerges as a vital addition to the cybersecurity arsenal. By focusing on users and analyzing behavioral patterns, ITDR provides a deeper understanding of identity context, helping to distinguish between legitimate users and threat actors. Integrating ITDR into a comprehensive security program alongside other tools creates a robust defense strategy.
.webp)
.webp)
The healthcare industry is under a constant barrage of cyberattacks. It has traditionally been one of the most frequently targeted industries, and things haven't changed in 2023. The U.S. Government's Office for Civil Rights reported 145 data breaches in the United States during the first quarter of this year. That follows 707 incidents a year ago, during which over 50 million records were stolen.
Health records often include names, birth dates, social security numbers, and addresses. This treasure trove of data is used in identity theft, tax fraud, and other crimes. It is the high value of the data that makes healthcare applications such a promising target.
The healthcare industry was hesitant to adopt SaaS applications. However, SaaS applications lead to better collaboration among medical professionals, leading to improved patient outcomes. That, combined with SaaS's ability to reduce costs and improve financial performance, has led to the industry fully embracing SaaS solutions.
Today, medical facilities store patient records, billing records, and other sensitive data containing both PHI (protected health information) and PII (personally identifiable information) are in many cases stored in Salesforce, Google Workspace, and Microsoft 365.
In the United States, medical data is protected under HIPAA, the Health Insurance Portability and Accountability Act. Security failings impacting more than 500 individuals are broadly reported in the media and are accompanied by significant fines.
SaaS applications like Salesforce, when they contain HIPAA-compliance add-ons, are secure enough to prevent threat actors from entering the applications and accessing patient data. SaaS applications are always updated to the latest version and don't have the same types of vulnerabilities found in on-premises software.
SaaS developers invest heavily in delivering secure software solutions. They maintain teams of security professionals who constantly monitor and update their software to address emerging threats. These applications run on advanced infrastructure with robust physical security measures, redundant systems, and disaster recovery systems. They adhere to strict industry standards, ensuring the highest level of security and compliance for healthcare data.
In a report issued in August 2022 by the Office of Information Security and the Health Sector Cybersecurity Coordination Center (HC3) on the impact of social engineering on healthcare, researchers found that 45% of all attacks on the healthcare industry began with a phishing attack. Employees were manipulated into handing over their login credentials, allowing threat actors to enter through the front door.
SaaS applications have multiple layers of defense against those types of breaches. For example, many SaaS applications require MFA during login. Without a one-time password, most threat actors will be thwarted when trying to access with just a username and password. Second, many organizations require SSO to access their apps. This additional layer of identity fabric creates more complexity for threat actors as they attempt to breach the SaaS application. There are over 100 security checks within Salesforce and Microsoft 365 that combine to form a strong perimeter of defense.
It wasn't long ago that anyone who managed to breach a SaaS application had carte blanche to do anything within their permission set. Steal credentials from an admin, and the entire app could be in control of the threat actor within minutes. That is no longer the case.
Leading SaaS security tools have added a layer of identity threat detection and response (ITDR) to the equation. This last line of defense ensures that if threat actors were able to access the application, security teams are alerted when threat actors enter the SaaS app, even if they access the application with valid credentials.
ITDR recognizes behavioral anomalies within the individual user. If a threat actor enters a SaaS stack and acts suspiciously, ITDR will flag those behaviors and alert the security team, who can disable the user account and conduct an investigation.
The healthcare industry is already familiar with role-based access to medical records. Those who don't need access to patient records aren't able to review medical files. This approach is critical to SaaS security. By following the Principle Of Least Privilege (POLP), each user is only able to access materials required for their role. If credentials for those users are compromised, threat actors will be unable to access the PHI data that they are searching for.
A SaaS Security Posture Management (SSPM) platform, like Adaptive Shield, is the most important tool used to defend healthcare applications. SSPMs conduct 24/7 automated monitoring of security settings, staying on top of settings and alerting security personnel when configurations are changed. If a user mistakenly reduces the app's security posture, SSPMs help to ensure that the misconfiguration is closed quickly.
SSPMs also monitor third-party applications that connect to the core SaaS apps. It tracks their permissions and triggers an alert when granted permissions exceed corporate policy or HIPAA standards. It tracks dormant users, external users, and authorized users, ensuring that they, like physicians treating patients, do no harm to the application.
By implementing an SSPM, healthcare organizations can ensure that the sensitive patient data stored within the applications are secure.


The US National Institute of Standards and Technology (NIST) cybersecurity framework is one of the world's most important guidelines for securing networks. It can be applied to any number of applications, including SaaS.
One of the challenges facing those tasked with securing SaaS applications is the different settings found in each application. It makes it difficult to develop a configuration policy that will apply to an HR app that manages employees, a marketing app that manages content, and an R&D app that manages software versions, all while aligning with NIST compliance standards.
However, there are several settings that can be applied to nearly every app in the SaaS stack. In this article, we'll explore some universal configurations, explain why they are important, and guide you in setting them in a way that improves your SaaS apps' security posture.
Role-based access control (RBAC) is a key to NIST adherence and should be applied to every SaaS app. There are two types of permissions within a SaaS application. Functional access covers things like creating accounts and navigating the application. Data access permissions, on the other hand, govern which users can retrieve and modify data. The admin account (or the super-admin account in some apps) is the most sensitive within the app, as it has full access to both types of permissions.
For threat actors, breaching an admin account is akin to winning the lottery. They have access to everything. Organizations must do everything within their power to maintain control over these accounts. This control is managed through configurations and best practices.
It's important to have a minimum of two admins for every application. This redundancy makes it difficult for an admin to act alone against the best interests of the organization, as admins can monitor each other for any signs of a breach.
However, each admin increases the application's attack surface. Organizations must strike a balance between having enough admins to adequately service the application while limiting exposure. An automated review of the number of admins should trigger alerts when the number of admins is outside the preferred range.
External admins introduce a new layer of uncertainty into SaaS security. Because they sit outside the organization, the security team can't control the password policies or authentication tools that they use.
For example, should a threat actor try to log into your application and click Forgot Password, there is no way to know whether the threat actor can breach the external admin's email account. That lack of oversight of external users could lead to a deep breach of your SaaS application, which is why NIST advises against having external admins. Depending on the application, either block external admins from getting admin privileges or identify external users with admin rights and remove those privileges.
For companies that hire an external IT company or outsource to MSSPs, those individuals should not be considered external. However, they should continue to monitor for other external users being given admin permissions.
To comply with NIST standards, all admin user accounts should be required to access the application using multi-factor authentication (MFA), such as a one-time password (OTP). MFA requires users to present a minimum of two forms of ID before it authenticates the user. A threat actor would need to compromise two authentication systems, increasing the level of difficulty of the compromise and reducing the risk to the account. Make sure to set MFA for admins as required (we also recommend MFA for all users, but it is a must-have for admins).
SaaS data leaks pose significant risks to organizations and their users, potentially compromising sensitive information stored within cloud-based applications. SaaS applications are marketed as collaboration tools. However, the configurations that enable users to work together can also compromise files and data. NIST, for its part, advocates monitoring the permissions of every resource.
A visible calendar can expose employees to socially engineered phishing attacks, while shared repositories can lead to a company's internal source code being shared publicly. Email, files, and boards all contain sensitive data that should not be accessible to the public. While the following configurations are often called something different in each application, almost any app that stores content will have this type of control.
The difference between Share with All and Share with a User is profound. When items are shared with all, anyone with a link can access the materials. Share with a User, in contrast, adds an additional authentication mechanism, as the user needs to log in before accessing the material.
To reduce the content that is exposed, app admins should disable sharing over public URLs ("Anyone with the link"). In addition, some applications allow users to revoke access to URLs that have already been created. When available, organizations should be sure to toggle that setting to on.
Many applications allow authorized users to invite external users to the application. However, most applications don't implement an invite expiration date. In those circumstances, invites sent years prior can provide access to a threat actor who has just breached an external user's email account. Enabling an auto-expiration date on invites eliminates that type of risk.
It's worth noting that in some apps, configuration changes are retroactive, while others will only take effect moving forward.
Passwords are the first line of defense against unauthorized access. NIST advocates for a strong and well-managed password policy, which is essential to protect sensitive user data, confidential business information, and proprietary assets stored within the cloud-based infrastructure. The uniqueness, complexity, and regular updating of passwords are critical aspects of a robust security posture.
Passwords serve as a fundamental element in a layered security approach, complementing other security measures such as multi-factor authentication (MFA) and encryption. Compromised passwords can be a gateway for malicious actors to exploit vulnerabilities in the SaaS environment. The effective management of passwords enhances the overall resilience of SaaS systems, contributing to a more secure and trustworthy digital ecosystem for both businesses and their users.
In a spray attack, threat actors enter a username and common password terms, hoping to get lucky and access the application. Requiring MFA is the recommended way to prevent password spray attacks. For those that don't insist on employees using MFA as part of the authentication process, many apps allow organizations to ban words from being used as passwords. This list of words would include terms like password1, letmein, 12345, and the names of local sports teams. Additionally, it would include terms like the user's name, company products, partners, and other business terms.
Going into the configurations and adding a custom banned words list can significantly reduce the risk of a successful password spray attack.
Most SaaS applications allow the organization to customize password complexity. These range from allowing any password to requiring alphanumeric characters, capital and lowercase letters, symbols, or a password length. Update the password requirements in the app to match your organization's policy.
If your organization doesn't have a password policy, consider following NIST guidelines:
It may seem unlikely that threat actors spend their time looking for misconfiguration that they can exploit. Yet, that is exactly what the Russian state-sponsored group Midnight Blizzard did when it breached Microsoft this year. If misconfigurations can happen at Microsoft, it's worth reviewing to make sure that your applications are all secure.


Oftentimes, there is a disconnect between identifying SaaS Security weak spots and remediation. Your SaaS Security Posture Management (SSPM) platform may have detected that MFA is turned off for admins, or a threat that requires immediate intervention by either the security team or the app owners.
Security Orchestration, Automation, and Response (SOAR) and Security Information & Event Management (SIEM) tools are the heavy lifters in the world of cybersecurity remediation. They are given marching orders from a number of different security tools, and then they implement them within the applications with which they are integrated.
SOARs and SIEMs are specialists in workflow automation. They automate routine tasks, so security team members can focus their efforts on more complex tasks. They also respond to threats before they can harm business operations. As a centralized platform, SOARs and SIEMs can help coordinate any type of incident response across different teams.
SSPM, or SaaS Security Posture Management, is a comprehensive cloud security solution designed to assess, monitor, and enhance the security posture of Software as a Service (SaaS) applications. It offers organizations real-time visibility into their SaaS environments, helping them proactively identify and mitigate security risks to ensure a robust and resilient cloud infrastructure.
SSPMs and SOARs are an ideal security combination. SSPMs find security misconfigurations and identify high-risk elements within the SaaS stack. However, they are rarely designed to remediate issues.
Automating this portion of SaaS security is essential. A recent Adaptive Shield report found large organizations have over 10,000 high-risk third-party apps connected to their core stack. Combine that with thousands of user accounts, tens of thousands of configurations, and thousands of resources that must be securely stored within the SaaS stack, and it’s evident why manual remediation approaches are a partial solution at best.
SOAR-driven automated remediation is essential to limiting risks and handling threats. In the world of securing SaaS apps from threats, that means providing the SOAR with detailed SaaS risks and mediation directions.
Organizations are leveraging SOAR for efficient incident response. Those tools are being powered by pre-written playbooks from SSPM platforms, which engage the SOAR and share workflows for Torq, Cortex Demisto, Chronicle, and others. Combining SSPM with SOAR automates remediation, and enables small security teams to secure large swaths of their SaaS stack.
There is no shortage of use cases driving SSPM and SOAR to work together.
Every organization can set its own policy for deprovisioning users, and in most cases, it can be adapted based on the application. Application configurations can be set to issue an alert once users have passed the dormant-user threshold. The SSPM passes the data to a SOAR, which accesses the application and removes privileges or shuts down the account for dormant users.
For a better understanding, see our example covering automated offboarding using Adaptive Shield’s integration with Torq.
When a SaaS app’s Identity Threat Detection and Response (ITDR) mechanism finds a user behaving anomalously in a way that could compromise the application or its data, it can use SOAR to respond. Users who are downloading an uncharacteristic volume of data can trigger a playbook that immediately disables the user account.
Collaboration is one of the core tenets of SaaS applications, so it is fitting that it takes SSPMs and SOARs to work together to secure applications. SSPMs monitor the attack surface, and scan for any vulnerabilities that could harm the SaaS stack. Once alerted to an issue, SOARs remediate the issue, enabling security teams to quickly handle problems that might have taken days to fully close if done manually.


Today, we released that one of our customers achieved a 201% return on investment (ROI) in less than six months from adopting a SaaS Security Posture Management (SSPM) solution, according to results of a Forrester Consulting Total Economic Impact™ (TEI) study.
The 2024 Forrester Consulting TEI study is based on data from the customer experience of a global corporation with an annual revenue of over $10 Billion USD. The organization is undergoing rapid SaaS adoption across business-critical applications and has adopted Adaptive Shield’s SSPM platform in order to control and manage the security of their entire SaaS ecosystem.
The model Forrester designed to determine this ROI includes elements of SaaS Security score, operational efficiency against costs of a data breach like lost employee productivity, lawsuits and settlements, and regulatory fines.
“We started seeing some small incidents resulting from SaaS misconfiguration, so we needed to do something about it… The incident was a wake-up call for us that we really need to look at all the configurations at scale,” asserts the Chief Security Officer (CSO) of the $10 billion global media and information services corporation interviewed for the TEI.
After they brought on Adaptive Shield, the CSO shares, “When we look at the security score trends, we observed significant increase over time. In reality, the improvement is even greater because we have already fixed some issues during the POC (proof of concept).”
The financial analysis of the implementation of Adaptive Shield platform with this customer found benefits of $2.18 million over three years. The payback period on the original investment was less than six months. Results from utilizing Adaptive Shield included more efficient SaaS Security management with improved visibility for stakeholders, enhanced security compliance control, and increased collaboration between business and security teams.
“There is a common misconception that SaaS providers take care of the security of the organizations’ apps. While SaaS vendors invest a lot in their security, the market has now come to realize that it’s the organization’s ultimate responsibility to ensure that their apps’ security posture is monitored and managed internally. Similar to the case of IaaS and CSPM tools, ” says Maor Bin, CEO and co-founder of Adaptive Shield.
“With the frequency of SaaS attacks only growing and SaaS incidents continuously exposing organizations to data leaks, breaches, compliance failures, and other potential disruptions in business operations, SSPM is the only way for organizations to secure SaaS data. Beyond the qualitative, this TEI study quantitatively presents just how much Adaptive Shield helped improve our customer’s SaaS security and streamline business costs.”
Key benefits found in the study:
.webp)
.webp)
SaaS Security’s roots are in configuration management. An astounding 35% of all security breaches begin with security settings that were misconfigured. In the past 3 years, the initial access vectors to SaaS data have widened beyond misconfiguration management. “SaaS Security on Tap” is a new video series that takes place in Eliana V’s bar making sure that the only thing that leaks is beer (maximum), and not SaaS data. This series takes a look at the key concepts within SaaS security and educates organizations on what new threat vectors need to be addressed.
With the increase in SaaS application use, it’s no surprise that incidents are up. The SaaS Security on Tap series covers this year’s SaaS Security report which found that 55% of organizations have experienced a SaaS security incident within the last two years, including data leaks, data breaches, ransomware attacks, and malicious applications.
The report was not all doom and gloom. As Eliana V points out, companies are recognizing that manual audits and CASB deployments are only partial solutions at best. A surprising 80% of companies are either using or planning on using a SaaS Security Posture Management (SSPM) tool, like Adaptive Shield, for automated configuration and SaaS security monitoring by September 2024. That should take SaaS applications to a far more secure place than they are today.
SaaS Security on Tap reveals that as more organizations adopt SSPM, they are enhancing their visibility into SaaS app users. SaaS experts have come to recognize the critical nature of identity and access governance in securing SaaS apps. While much of SaaS security falls under the control of app owners, responsibility for identity and access governance falls squarely within the responsibility of the security and central IT team. They manage the company’s Identity Provider (IdP) and need visibility to see which users are accessing applications, the level of access they have, and the type of users they are.
Identity security is all about ensuring that identity and access tools and policies are in place. Security teams need a high degree of visibility to know which users, including external users, have access to each application and to what extent. To fully quantify the risk emanating from users, they also need visibility into the devices used to access those applications and the ability to monitor high-privilege users.
Third-party application integrations, also known as SaaS-to-SaaS access, have also developed into a serious attack vector. These applications, which are integrated through OAuth protocols with the click of a button, improve workflows and help businesses get more out of their applications. While many of these SaaS-to-SaaS applications are harmless, they pose a significant risk. 3rd-party apps often ask for intrusive permission scopes, like Eliana V quips in the On Tap video (below), “some scopes ask for your firstborn child.”
Users are granting permissions that allow read/write access, the ability to send email as a user, and most concerning, the ability to delete entire folders and drives of data. Eliana V points out that researchers found organizations with 10,000 SaaS users averaged over 6,700 applications connected to their Google Workspace, of which 89% requested medium- or high-risk permission scopes.
SaaS Security on Tap provides a fast-paced, entertaining look at the challenges and solutions organizations face as they try to secure their data in SaaS apps.
Hosted by Eliana V from the SaaS Security On Tap bar, the series gets inside the issues facing security teams and their application-owner partners. Take misconfiguration management. Using entertaining analogies and powerful examples, Eliana V demonstrates the dangers of misconfigurations and the ease with which organizations err with their settings.
Check out the trailer…and like and subscribe if you want more.
Don’t miss an episode of SaaS Security On Tap, the entertaining new video series that gets to the heart of SaaS security.


As we near the end of 2023, it's an opportune moment to assess your roster of SaaS users. Beyond the potential cost savings from eliminating unnecessary license fees, maintaining a well-organized user inventory plays a crucial role in fortifying the security of your SaaS applications. Here are five compelling security reasons to clean your user list.
When employees leave a company, they set a sequence of backend system adjustments in motion. The initial step involves their removal from the company's identity provider (IdP), initiating an automated process that deactivates their email and revokes access to all internal systems. Enterprises that utilize Single Sign-On (SSO automatically revoke access to various online properties, including SaaS applications.
However, deprovisioning from SaaS applications isn't automatic. Enterprises must manually deactivate or delete users from non-SSO-connected apps and SSO apps that also have local access. This is especially critical for high-privilege users, who often have local access even if the app is typically accessed through an SSO.
Ensuring the complete deprovisioning of users is critical. With the typical end-of-year slowdown, now presents an opportune time to reassess user roles and remove access for individuals who no longer need it.
User permissions dictate the extent of access granted to each employee within an application. Administrative permissions, typically granted to team leaders, enable tasks such as adding new users and overseeing application usage. Employees may require read/write permissions for their roles, while support personnel might only need read permissions or the ability to download reports.
Overpermissioning poses a security risk by unnecessarily expanding the attack surface. In the event of a compromised user account, the threat actor gains access equivalent to the compromised user. As the year concludes, it's prudent to review user permissions, aligning them with respective roles. Implementing the principle of least privilege (POLP) ensures employees have precisely the access needed for their tasks. For applications with group functionality, grouping like-users with preset permissions helps standardize access, while in other apps, a thorough review allows trimming access to essential functionalities.
Dormant accounts, which are unused SaaS accounts, fall into three primary types: admin accounts utilized during the application's initial setup with broad privileges, internal accounts belonging to employees who no longer require or use the application based on their roles, and external user accounts that remain inactive.
The risks associated with dormant accounts are substantial. Admin accounts shared among multiple users typically have easily guessable usernames and passwords, coupled with local access, which can create an environment prone to abuse. Unused employee accounts pose a risk in the aftermath of a phishing attack, potentially providing access to threat actors who exploit employees who are unaware of their retained access. Additionally, the lack of visibility into external user activity raises concerns about the security of the user account.
As enterprises navigate the holiday season, it is advisable to scrutinize dormant accounts and proactively assess their risk. When warranted, these accounts should be disabled or canceled to mitigate potential security threats.
Using a shared username to cut down on license fees introduces a heightened security risk. Shared accounts become challenging to secure as the number of users who know the access credentials expands with team changes. Moreover, opting for a shared login negates the use of critical security tools like Multi-Factor Authentication (MFA) and Single Sign-On (SSO), leaving the SaaS application more vulnerable.
The difficulties in detecting threats arising from shared accounts compound the security challenge. Anomalies in account access are less likely to trigger alerts if the account is regularly accessed from various locations, making it harder to identify suspicious activity.
Identifying departments that use shared accounts is not easy. However, enterprises can implement preventive measures and detection strategies. Mandating MFA or SSO complicates account sharing, and security teams can leverage user behavior analytics, including monitoring IP address logins, to identify instances of shared usernames. Taking the time now to uncover and address shared accounts contributes to a more secure SaaS environment in the upcoming year and beyond.
Manually reviewing user rosters and comparing them to the IdP is remarkably tedious and can easily lead to mistakes. So is checking permissions, reviewing dormant accounts, and looking for signs of account sharing. Using a SaaS Security Posture Management (SSPM) platform like Adaptive Shield’s simplifies the process through automation.

Using SSPM’s user inventory, companies can quickly identify accounts that haven’t been used over a preset time period, find external users with high permission sets, and detect users who were removed from the IdP. SSPMs can also associate users with devices to further limit risk.
As you prepare for 2024, introducing an SSPM to monitor users is the most effective and efficient way to know who is accessing your SaaS stack.


Over the past few years, SaaS has developed into the backbone of corporate IT. Service businesses, such as medical practices, law firms, and financial services firms, are almost entirely SaaS based. Non-service businesses, including manufacturers and retailers, have about 70% of their software in the cloud.
These applications contain a wealth of data, from minimally sensitive general corporate information to highly sensitive intellectual property, customer records, and employee data. Threat actors have noted this shift, and are actively working to breach apps to access the data.
Here are the top trends influencing the state of SaaS Security for 2024 — and what you can do about it.
SaaS apps have transformed the way organizations purchase and use software. Business units purchase and onboard the SaaS tools that best fit their needs. While this is empowering for business units that have long been frustrated by delays in procuring and onboarding software, it does require organizations to rethink the way they secure data.
Security teams are being forced to develop new ways to secure company data. Lacking access and visibility into an application, they are placed in the role of advising a business unit that is using SaaS applications. To further complicate matters, every SaaS application has different settings and uses different terminology to describe security features. Security teams can't create a one-size-fits-all guidance document because of the differences between the apps.
Security teams must find new ways to collaborate with business units. They need a tool that offers visibility and guidance for each application setting so that they – and the business unit – understand the risks and ramifications involved in the configuration choices that they make.
If a threat actor gains access to a high-privilege account, they gain unfettered access within the application. Organizations are now understanding that identity is the de facto perimeter for their SaaS applications.
When threat actors take over an authorized user account, they typically follow common tactics, techniques and procedures (TTP) as they work their way through the app toward the data they want. They leave behind indicators of compromise (IoC), which might be based on actions taken within the app or logs.
As we move into the new year, we are going to see more organizations adopting an Identity Threat Detection & Response (ITDR) approach. ITDR mitigates that concern. As a key component in Identity Security Posture Management, ITDR capabilities can detect TTPs and IoCs, and then send an alert to the incident response team. Through ITDR, threat actors who have managed to breach the identity perimeter can still be stopped before they steal critical data or insert ransomware into the application.
Global companies are increasingly facing different regulatory requirements from one country to the next. As a result, 2024 will see an increase in the number of geo-specific tenants as part of the effort to keep data segmented in accordance with the different regulations.
This change will have a limited impact on software costs as most SaaS app pricing is based on subscribers rather than tenants. However, it will have a significant impact on security. Each tenant will need to be configured independently, and just because one instance of the application is secure doesn't mean that all tenants are secure.
To secure all these tenants, security teams should look for a security solution that allows them to set app benchmarks, compare tenants, and display security settings side-by-side without charging extra for each additional tenant. By applying best practices throughout the organization, companies can keep all their tenants secure.

A default misconfiguration in ServiceNow triggered widespread panic in October. The setting, which was part of the application's Access Control Lists, allowed unauthorized users to extract data from records. The misconfiguration impacted thousands of companies. A similar misconfiguration in Salesforce Community back in May also impacted a significant number of companies and led to data breaches.
Misconfigurations like these have the potential to cause major damage to companies. They lead to data leaks that break the trust between companies and their stakeholders, and have the potential to turn into onerous fines, depending on the nature of the data that leaked.
Securing misconfigurations is an organization's best chance at preventing these exploits from impacting their operations and hurting their bottom lines.
Third-party applications add real value for end users. They improve processes, extend functionality, and connect data between multiple applications. Users connect these SaaS apps with the click of button, and instantly begin improving their workflows.
In March 2023, Adaptive Shield released a report showing that organizations using Google Workplace with 10,000-20,000 users averaged 13,913 third-party apps connected to Google Workplace alone. An astonishing 89% of these requested either high- or medium-risk permissions. Many of these high-risk apps are used once and forgotten about, or used by a small number of employees. However, even these dormant or lightly used applications have significant permissions and can be used to compromise or breach a SaaS application.
The use of third-party applications is only increasing, as more apps are developed and employees use their own judgment – rather than checking with their security team – when integrating third-party applications into their stack. Security teams must develop visibility into all their integrated apps, and gain insights into the permissions requested, the value the app contributes to the organization, and the risk it poses.

In 2023, nearly 40% of all employees worked from home at least part of the time. According to WFHResearch, approximately 12% of employees work exclusively in their homes, while another 28% have hybrid roles.
These figures should give pause to security personnel concerned about users logging in to their work accounts from personal devices. One of the biggest concerns security teams have is when high-privileged users log into their accounts using an unmanaged or unsecured device. These devices may have critical vulnerabilities, and create a new attack vector. For many teams, there is almost no way to tell which devices are used to access the SaaS app or see whether those devices are secure.
While all these trends point to legitimate SaaS security concerns, SaaS Security Posture Management (SSPM) tools coupled with ITDR capabilities, like Adaptive Shield, can fully secure the SaaS stack. SSPMs are designed to automatically monitor configurations, looking for configuration drifts that weaken an app's posture. In SaaS Security Survey, 2024 Plans & Priorities by Cloud Security Association and Adaptive Shield, 71% of respondents said their company had increased their investment into SaaS security tools over the past year, and 80% were either already suing SSPM or planned to invest in one within the next 18 months.
SSPMs can provide baselining tools for multiple tenants of the same app, and enable users to establish best practices, compare settings from different instances, and improve the overall posture of the SaaS stack.
SSPMs also detect and monitor third-party applications, alerting users if their integrated apps are requesting too much access and updating the security team when integrated apps are dormant. It tracks users, and monitors the devices being used to access applications to prevent the use of unmanaged or unsecured devices on corporate SaaS apps. Furthermore, their built-in communication tools make it easy for business units to collaborate with security personnel in securing their applications.
SaaS apps have grown in popularity for good reason. They allow organizations to scale as needed, subscribe to the apps they need at the moment, and limit investment in some IT. With SSPM, these applications can be secured as well.


Former employees retaining SaaS app access happens far more often than businesses care to admit. Nearly a third of all employees retain some degree of access to the SaaS stack.
When employees move on, voluntarily or otherwise, it’s in the organization’s best interests to remove all access to corporate assets. Much of this process is done through automated workflows, where employees are removed from the identity provider (IdP) which triggers their removal from other systems.
However, users must be manually deprovisioned from applications that weren’t integrated into the IdP. Failure to do so could lead to data theft, breaches, or other incidents conducted by either the former employee or someone who steals their credentials.
A newly released guide, “Offboarding Employees from Your SaaS Stack in 7 Steps”, explains why deprovisioning users isn’t always as straightforward as it seems, and gives step-by-step instructions to fully deprovision users, as well as automate the process. The process is summarized as follows: (For the full details, download the guide here).
Organizations must overcome many challenges to permanently remove a user from their SaaS applications:
Removing access for former employees requires that they be fully deprovisioned. If you are using a manual process, follow these steps. (For further explanation on all these steps, download the full guide here).
Following this process will remove ex-employee access while ensuring that other users will still have access to the app.
Beyond manual deprovisioning, introducing and enforcing strong governance policies for SaaS applications can go a long way toward reducing the risk. For example, if company policy required all SaaS users to login through an SSO or using MFA, user access would be curtailed the moment their login tools were deprovisioned.
Some users, particularly those with high privileges, are required by the application to have local access. Unfortunately, these users will retain their access even when they are removed from the SSO or MFA. In those circumstances, maintaining a list of users with local access can be used to identify is instrumental to identifying users that must be manually deprovisioned.
Shared passwords are another way users can get around deprovisioning, as they may maintain access through a shared team account. Enforcing an anti-password sharing policy and training users about the dangers of password sharing can go a long way toward reducing risk.
The easiest way to deprovision users from SaaS applications is through a SaaS Security Posture Management (SSPM) platform that is integrated with a SOAR. Using automated workflows, these processes quickly identify and fully deprovision offboarded employees who maintained access to SaaS applications.
By using an SSPM, enterprises can confidently move forward, knowing that access to their applications is under their full control.
Have users you need to deprovision? Download our latest ebook, Offboarding Employees from Your SaaS Stack in 7 Steps!


If forecasters are right, over the course of today, consumers will spend $13.7 billion. Just about every click, sale, and engagement will be captured by a CRM, Marketing or Customer Service platform and more operational apps. Inventory applications will trigger automated re-orders; communication tools will send automated email and text messages confirming sales and sharing shipping information.
SaaS applications supporting retail efforts will host nearly all of this behind-the-scenes activity. While retailers are rightfully focused on sales during this time of year, they need to ensure that the SaaS apps supporting their business operations are secure. No one wants a repeat of one of the biggest retail cyber-snafus in history, like when one U.S.-based national retailer had 40 million credit card records stolen.
The attack surface is vast and retailers must remain vigilant in protecting their entire SaaS app stack. For example, many often use multiple instances of the same application. They may use a different CRM or ServiceNow tenant for every region they operate in or have different tenants for each line of business. Each one of these tenants must set up their configurations independently, with each one limiting risk and meeting corporate standards.
Here are a few areas retailers should focus on to ensure their SaaS Security over the entire holiday season.
Access Control settings are particularly important to retailers as they typically have a lot of employees, in many types of roles and responsibilities, from operations and infrastructure to bookkeeping and finance. Retailers need to limit who can enter an application and the privileges those users will have once inside the app. Access and visibility to sensitive data should only go to those who require it to perform their job functions. Creating role-based access and monitoring employees then ensures that they have an appropriate level of access based on their role is a key step in reducing the risk level.
One additional area worth reviewing is access granted to former employees. Former employees should almost always be deprovisioned as part of the offboarding process. When applications are connected to an SSO and access is only through that SSO, the offboarding is automatic. Unfortunately, many retailers have apps that either sit outside the SSO or allow employees to log in locally. In those circumstances, employees must have their access removed manually from each application.
This is also a time of year when people receive emails to their corporate email addresses for end-of-year sales and promotions. Threat actors use this as an opportunity to carry out phishing attacks, making it all the more important to harden anti-phishing controls within the SaaS stack.
Pricing information is one of the most sensitive pieces of information retailers have. While web crawlers may have access to published prices, it’s of paramount importance to protect future pricing strategies and plans. During the holiday season, when competitors are looking for every pricing and promotion advantage, securing this information behind serious data leakage protection is a top priority.
When available, turn on encryption settings to prevent unauthorized users from viewing your critical data. Turn off the ability to share or email files outside the organization and require some form of user authentication before users can access boards, spreadsheets, and databases.
Protecting customer information from leaks should be another high priority for retailers. Nothing will drive customers away from your website than reports of personal information, such as PII (Personal Identifiable Information) and payment information, being leaked. Harden security settings to prevent unauthorized data leaks from the application.
One additional area of concern is mobile users. These devices are often unmanaged, and when used to access corporate SaaS applications, they can be used to provide threat actors with an entranceway into the application. Users should be directed to only use managed devices when accessing corporate applications.
Unfortunately, we live in an era of insider threats. In Adaptive Shield’s annual survey, 43% of respondents said they had experienced corporate espionage or an insider attack within their SaaS stack. Preventing these types of attacks are notoriously difficult, as authorized users log in with verified credentials and their nefarious activities are all within the parameters of their access.
For retailers, monitoring user activity is one way to detect threats before they turn into full-blown breaches. Monitoring and analyzing user behavior allows organizations to identify these threat actors by detecting anomalies in their behavior. By analyzing behavioral anomalies, which might include accessing data during unusual times or downloading an unusual amount of data, retailers can uncover insider threats and protect themselves.
Some retailers may monitor these settings and behaviors manually or with older technologies like CASBs. Neither of those approaches are likely to be effective. SaaS settings can change without notice, and it's far too easy to miss the signs of threats to the application.
SaaS Security Posture Management (SSPM) tools, like Adaptive Shield are the only effective way for retailers to secure their whole SaaS stack. They automatically and continuously monitor settings, even over the busy holiday season, to detect and identify misconfigurations, unauthorized access, and users that need to be fully deprovisioned.
Using an SSPM, retailers can move ahead confidently, knowing that every tenant of their applications in every country they operate is secure. They can update strategies, retain customer data, and monitor users to prevent insider attacks.


Effective marketing operations today are driven by the use of Software-as-a-Service (SaaS) applications. Marketing apps such as Salesforce, Hubspot, Outreach, Asana, Monday, and Box empower marketing teams, agencies, freelancers, and subject matter experts to collaborate seamlessly on campaigns and marketing initiatives.
These apps serve as the digital command centers for marketing professionals. They house essential go-to-market strategies, and are often connected to live payment systems authorized to spend substantial budgets. Ensuring their security is a complex task, given the multitude of applications, application owners, configurations within each app, users, interconnected apps and more. In this article, we explore the top Marketing SaaS application use cases, from external users and publicly shared links to connected apps and credit cards — and how to ensure the security and integrity of the data stored within them.
Marketing departments frequently grant administrative or high-access permissions to agency and freelance partners who need access to sensitive reports and data in order to perform. However, managing these external users can be a daunting task. It's vital to closely monitor their permissions and trim them down to the minimum necessary level. Additionally, there's often a gap between the time an employee leaves an agency and when the agency notifies the client. During this period, former employees can retain their access.
Collaboration with agencies often requires sharing files, project management boards, and folders with various team members. Using one set of public links for all users is a tantalizing option, as it cuts down on administrative tasks every time a new user is introduced into the project.
However, this approach can inadvertently expose sensitive assets to former agency employees or other unintended recipients, as public links can be used by anyone.
Marketing budgets often involve significant sums of money, and this financial data is highly sensitive. It's not uncommon for external agencies to manage these budgets, and if left unsecured, it could lead to malicious activities like unauthorized data access or the running of negative campaigns. Organizations need to ensure that access configurations are tightly controlled, with Identity Threat Detection & Response (ITDR) mechanisms sending alerts when users exhibit anomalous behavior.
Marketing departments rely heavily on prospect and customer data, which is stored and analyzed in SaaS databases like Customer Relationship Management (CRM) systems, Marketing Automation Hubs, and Sales Development Representative (SDR) tools.
Protecting this sensitive data is highly important and requires robust access controls, multi-factor authentication (MFA), and constant monitoring of internal user behavior.
Marketing teams utilize a wide array of connected applications to support their daily operations. These range from calendar apps, to video conferencing plugins, design, project management tools and ad optimization apps. Each of these applications requests different levels of permissions to access company data, some of which are quite intrusive. Organizations need visibility to quantify the risk from these applications.
SaaS apps hold the key to productive and efficient work. Any potential data leak or breach is not only a problem for the organization at large, but especially for the Marketing department, who retains the ultimate responsibility for ensuring the brand. Any reputational damage, especially if caused by a MarTech solution, would bring severe impact.
SaaS Security Posture Management (SSPM) platforms enable security teams to work collaboratively with Marketing and ensure the security of these applications. SSPMs monitor and manage internal and external users, ensure tight access controls across the SaaS stack, and safeguard sensitive data. The right SSPM solution will ensure that no operational workflows are disrupted and that all marketing stakeholders remain efficient and productive.


Earlier this week, ServiceNow announced on its support site that misconfigurations within the platform could result in “unintended access” to sensitive data. For organizations that use ServiceNow, this security exposure is a critical concern that can result in a major data leakage of sensitive corporate data.
ServiceNow is a cloud-based platform used for automating IT service management, IT operations management, and IT business management for customer service, as well as HR, security operations, and a wide variety of additional domains. This SaaS application is considered to be one of the top business-critical applications due to its infrastructural nature, extensibility as a development platform, and access to confidential and proprietary data throughout the organization.
Simple List is an interface widget that pulls data that is stored in tables and uses them in dashboards. The default configuration for Simple List allows the data in the tables to be accessed remotely by unauthenticated users. These tables include sensitive data, including content from IT tickets, internal classified knowledge bases, employee details, and more.
These misconfigurations have actually been in place since the introduction of Access Control Lists in 2015. To date, there were no reported incidents as a result. However, considering the recent publication of the data leakage research, leaving it unresolved can now expose companies more than ever.
It’s important to point out that this issue was not caused by a vulnerability in ServiceNow’s code but by a combination of configurations that exist throughout the platform.
This issue stems from security controls in a ServiceNow Access Control List (ACL) widget called Simple List, which puts records into easily readable tables. These tables organize information from multiple sources and have configurations with a default setting of Public Access.
Because these tables are the core of ServiceNow, the issue isn’t contained within a single setting that can be fixed. Potentially, this needs to be remediated in multiple locations within the application in combination with the usage of the UI widget, and throughout all tenants. To further complicate the issue, changing a single setting could break existing workflows connected to the Simple List tables, causing severe disruption of existing processes.
On the other hand, leaving these tables and applications exposed could have major security implications now that this issue has received so much attention.
We encourage all ServiceNow customers to review the recent guidance published by ServiceNow in their knowledge base article – General Information | Potential Public List Widget Misconfiguration.
To summarize, exposure assessment and remediation measures shall include:
Organizations that use a SaaS Security Posture Management (SSPM) solution are able to gain visibility into ServiceNow’s configurations and remediate the issue based on the recommendations.

To help organizations secure ServiceNow, Adaptive Shield is offering a free ServiceNow assessment for this issue. After a quick validation of your org, our Security research team will send you a report detailing any exposure your portals may have from this misconfiguration.
Click here to request the complimentary assessment.


Overpermissioning is one of the seven deadly SaaS sins. It paves a path straight to data leakage and catastrophic data breaches, and unnecessarily stretches resources that would be better served addressing other cyber threats.
This phenomenon happens for any number of reasons. Some admins decide to grant users all access so they aren’t bothered by future requests to increase access or to ensure productivity isn’t disrupted because a team member can’t access a key resource. In other cases, admins create multiple high-privilege accounts within their team to ensure access if the regular admin is OOO.
To truly secure SaaS data, organizations need to right-size their permissions, and develop a policy that follows the principle of least privilege.
When you consider that every user account makes up the perimeter of the app’s security fence, limiting access to individual accounts makes a lot of sense. Should high-privileged account credentials be compromised, the results could be disastrous.
A skilled threat actor that accesses a high-privilege account can move laterally through the application to accomplish its nefarious agenda.
The principle of least privilege maintains that users should only have access to the data, resources, and applications required to do their job. By right-sizing permission levels to the needs of the user, organizations limit their single points of exposure. Threat actors are limited to the permissions of the compromised account.
Customizing permission sets that match the needs of employees is not always easy. While almost all SaaS applications offer some form of role-based access control, these settings should be fine-tuned through the application’s configurations to meet the precise needs of the organization.
Roles should be defined for each application, making it easy for SaaS admins to assign the right level of access for each employee that uses the app.
Administrators also must be mindful of privilege creep. This takes place when employees are granted increased permissions while a co-worker is away or while working on a specific project, and then forgotten about.
Another common occurrence of privilege creep happens in Salesforce. When users are unable to access a specific file, they often fill out a ticket requesting access to the information they need. There are hundreds of different settings controlling access within that application. When administrators are unsure which configuration needs to change to provide access, they often grant the user View All Data rights. This high level of access is far greater than that which the user needs, and unnecessarily puts the company’s data at risk. Unfortunately, this type of overpermissioning is rarely closed.
When SaaS applications have too many admins, it becomes nearly impossible to maintain control over the application. Anyone with admin access can change settings to meet their needs at the moment, without realizing the implication of their actions.
Most admins are business users focused on getting the most value out of the application, or at least, focused on getting the job done quickly. If they feel that MFA is slowing down productivity, or want to share files with “Anyone with Link,” they have the means to make those changes.
While their intentions may be good, the consequences of removing MFA or allowing anyone to download a file can lead to serious issues, including data leakage or SaaS ransomware. The importance of right-sizing permissions and limiting the number of admins simply cannot be overstated.
SSPMs play an important role in right-sizing permissions. They identify high-permission users, and can alert security teams when the number of users with high permissions crosses a specific threshold.
Many SSPMs contain user inventories, which provide all the user data security teams need to help design right-sizing policies. While SSPMs are not Identity and Access Management (IAM) tools and shouldn’t be used as a replacement for them, they do provide governance over IAM solutions, ensuring that they are functioning as designed.
These automated tools help ensure that users aren’t overpermissioned, and maintain the overall safety of the data within the SaaS stack


The great thing about SaaS applications is that they are quick to install and ready from the start to get employees using them for their endless business needs. They easily integrate with third-party applications to increase functionality and make it easier for employees to get their job done. The downside, of course, is this integration creates a security risk for the SaaS stack and organization at large.
What kinds of security risks?
Dive into it with Eliana V.
In this video, you’ve learned about the risks and realities that third-party apps pose to organizations as they expand the organization’s attack surface. There is an automated solution to identify connected apps, enabling the security team to minimize risks and mitigate threats.
If you are interested in more SaaS security topics, check out the SaaS Security On Tap channel.


SaaS applications are the backbone of modern businesses, constituting a staggering 70% of total software usage. Applications like Box, Google Workplace, and Microsoft 365 are integral to daily operations. This widespread adoption has transformed them into potential breeding grounds for cyber threats. Each SaaS application presents unique security challenges, and the landscape constantly evolves as vendors enhance their security features. Moreover, the dynamic nature of user governance, including onboarding, deprovisioning, and role adjustments, further complicates the security equation.
With great convenience comes great responsibility, as securing these SaaS applications has become a top priority for Chief Information Security Officers (CISOs) and IT teams worldwide.
Effectively securing SaaS applications requires a delicate balance between robust security measures and enabling users to perform their tasks efficiently. To navigate this complex terrain, this article excerpts a step-by-step guide to establish a robust SaaS security strategy – from planning to execution and performance measurement.
Before embarking on a SaaS security journey, it's imperative to understand your organization's specific landscape and security needs. While applications like Salesforce and Microsoft 365 may contain more critical data, even smaller, niche apps used by various teams can store sensitive information that must be protected.
Consider the regulatory and compliance requirements applicable to your business. Industries such as finance adhere to SOX, while healthcare organizations must comply with HIPAA. Understanding your regulatory environment is essential for shaping your security strategy.
Additionally, prioritize user access and data privacy. Implementing the principle of least privilege (POLP) ensures users have access only to the data required for their roles, reducing the risk of data breaches and unauthorized access. If your apps handle personally identifiable information (PII), ensure your security program aligns with privacy laws.
Here is some basic info you should collect for each app:

To be most effective, your SaaS security program must integrate tightly into the existing infrastructure. It must connect with the organization's Identity Provider (IdP) for effective user governance and your single sign-on (SSO) provider to make it more difficult for unauthorized users to access the SaaS stack. These integrations enhance the protection of your applications and make it easier for security professionals to do their job.
It's also important to integrate your SaaS security tools with existing SOC, SIEM, and SOAR tools. The SOC team can analyze alerts and quickly make a determination as to the mitigation required. Meanwhile, SIEM can manage events while SOAR can orchestrate remediations, deprovision users, and automate many of the mitigations needed to secure the SaaS stack.
SaaS security is a collaborative effort involving multiple stakeholders. Business units manage SaaS applications with a focus on productivity, while the security team's priority is data protection. Bridging the gap between these groups and deciphering the unique language of each SaaS application's settings is challenging.
Effective SaaS security demands collaboration and compromise between these parties to mitigate risks without hindering productivity.
Creating a successful SaaS security program requires clear goals and key performance indicators (KPIs) to measure progress. Begin with a pilot program focused on critical applications managed by different departments. Establish a timeline for the pilot, typically around three months, and set realistic improvement goals.
A posture score, measured on a scale of 0-100%, can help gauge security effectiveness. Aim to maintain a score above 80% at the conclusion of a three-month pilot program and target a long-term score of 90-100%.
Start by securing high-risk, low-touch items in collaboration with app owners. Close communication is crucial to understanding the impact of security changes on workflows and processes. Address high-risk security checks impacting a small number of employees first. Utilize Security Posture Management solutions to guide remediation efforts based on application, security domain, or severity.
Some organizations choose to improve posture one application at a time. Others improve posture by domain across multiple applications, while still others choose to remediate issues by severity regardless of the application. Whichever model you choose, it is important to develop a process to help you move systematically through your applications.
Frequent meetings with stakeholders involved in remediation are essential, especially during the pilot phase. As the posture stabilizes, adjust the frequency of these meetings to ensure sustained security.
Continue onboarding and monitoring additional applications to enhance the security posture of your entire SaaS stack.
Embrace the principle of least privilege (POLP) to restrict user access to essential tools and data. Deprovision users who no longer require access to minimize risks associated with active accounts. Regularly monitor external users, particularly those with admin rights, to safeguard app data.
By adhering to these principles and following a structured approach, organizations can establish a robust SaaS security program. Remember, SaaS security is an ongoing process, and continuous adaptation and improvement are key to staying ahead of evolving threats in the digital landscape.
Excerpt from The Hacker News article published Sept 12, 2023.


In today's digital landscape, organizations are increasingly relying on software-as-a-service (SaaS) applications to drive their operations. However, this widespread adoption has also opened the doors to new security risks and vulnerabilities.
The SaaS security attack surface continues to widen. It started with managing misconfigurations and now requires a comprehensive approach to handling the entire SaaS ecosystem. This includes the continuous monitoring and management of user access, roles and permissions, 3rd party apps installed by users, risks deriving from SaaS user devices and Identity Threat Detection & Response (ITDR).
There are a variety of reasons that SaaS security is so complex today. Firstly, there are a diverse range of applications, each having its own UI and terminology. And those environments are dynamic, from SaaS vendors understanding the importance of security and continually enhancing their applications with modern security measures to the ever-evolving user governance required such as onboarding, deprovisioning, adjustments in user access, etc.. These controls are effective only when continuously governed, for each app and each user. If that’s not enough, these apps are managed by dispersed business departments, making it almost impossible for the security team to implement their security policies.
When it comes to dealing with SaaS threats, existing threat detection and identity management methods don’t go far enough. Today’s SaaS environments are complex and ITDR capabilities within these landscapes require deep knowledge and proven expertise.
To address the Identity Threat Detection & Response challenge within the SaaS ecosystem, Adaptive Shield has developed a powerful solution that detects and responds to identity-related security threats based on key Indicators of Compromise (IOCs) and User and Entity Behavior Analytics (UEBA). These indicators provide forensic signs of a potential breach, such as malware, data breaches, unusual behavior, and other suspicious events.
ITDR is designed to tackle various SaaS-related threats, including password-based attacks, IP behavior anomalies, OAuth-based attacks, unauthorized document access, unusual user agent activities, and more. By offering a comprehensive suite of protective measures, organizations must proactively defend their SaaS stack and ensure the integrity of their sensitive data.
Adaptive Shield’s ITDR is built on the foundation of a deep understanding of SaaS characteristics and Identity Governance within this landscape, based on its broadest coverage of SaaS applications in the market, encompassing over 130 applications.
As a means of prevention and first layer of defense, SSPM operates as the security layer in the Identity Fabric to establish robust user governance. This includes excessive permissions, access entitlement, user deprovisioning, and more, across the entire SaaS stack. Adaptive Shield provides organizations with deep and consolidated visibility and control of user accounts, roles, permissions, privileged users, and activities.
As a second layer of threat protection, Adaptive Shield’s ITDR capabilities provide extensive coverage in detecting anomalies and Tactics, Techniques, and Procedures (TTPs). By focusing on context and creating user and company profiles, it increases the accuracy of these detection alerts. Additionally, understanding expected behavior patterns and considering factors such as user access, permissions, and devices, enables the solution to better understand and prioritize alerts.


Identification of common tactics and techniques that adversaries use to compromise systems, steal data, or disrupt operations. By understanding these TTPs, ITDR improves incident response capabilities through:
Indicator of Compromise (IOC) Detection: Collection of evidence indicating that the organization's SaaS apps are under attack or have been compromised. IOCs can include data from IP addresses, domain names, URLs and more.
User and Entity Behavior Analytics (UEBA): Detection of behavioral anomalies, Adaptive Shield’s ITDR can identify threat actors as they navigate through the organization’s applications, offering proactive threat detection.
Enhance incident response capabilities and improve threat detection and mitigation by aligning observed or potential attack techniques with the MITRE ATT&CK framework.
Get alerts in multiple channels such as email, Slack, or Teams, indicating potential security incidents or suspicious activities that require immediate investigation or response.
Seamlessly integrate with your existing Security Operations Center (SOC) and Security Orchestration, Automation, and Response (SOAR) tools, improving threat correlation and incident response efficiency.
Get actionable recommendations and step-by-step guidance to address and mitigate vulnerabilities, weaknesses, or compromises in the event of a security incident.
When securing your SaaS environments, ensure your security platform goes beyond identity threat detection and response. Your solution should include a range of capabilities that strengthen your overall security management and offer a holistic prevention model for securing the SaaS Identity Fabric:
Read more about the different SaaS Security use cases
With unparalleled insights and an array of features, Adaptive Shield empowers organizations to protect their SaaS stack, prevent data breaches, and safeguard their SaaS data from emerging threats.
.png)
.png)
Over the last three years, Simple Storage Service (S3) buckets in Amazon Web Services (AWS) have leaked a lot of information. An American publishing company for educational content exposed grades and personal information for 100,000 students. A consumer ratings and review website exposed 182 GB worth of data covering American and Canadian senior citizens. Thousands of UK consultants had their passport scans, tax documents, background checks, job applications, and other personal information exposed.
Go back further in time, and S3 has leaked social security numbers, driver’s license information, military secrets, and more. S3 buckets have been considered the leakiest buckets in the world. Until now.
Over the past few months, analysts have started referring to GitHub as the new S3 bucket. This is due to multiple pieces of sensitive data leaking from GitHub repositories, including private repositories that were accidentally exposed to the public due to a misconfiguration. Twitter and Slack have both had code leak out of their GitHub repository. GitHub is known for containing sensitive secrets like 0Auth tokens, API keys, usernames and passwords, encryption keys, and security certificates.
The reasons are many. Sometimes, users make a mistake and accidentally expose private repositories. Other times, the fault is applications that request – and are granted – too much access. Another common scenario centers on a lack of control of who can change repositories and the users who have access to advanced settings.
User mistakes are the common denominator across almost every GitHub leak. The application, in a vacuum, is remarkably secure. However, when used in practice developers often hand over the keys to their repositories.
When publicly sharing repositories, users receive a warning message recommending that they revert the setting back and not allow wide access to the code. However, users tend to ignore those types of warnings. One click of the button later, and the repository is public, and the headlines are waiting to write themselves.
A few years ago, the issues caused by leaky S3 buckets were a driving force in the development and growth of CSPM solutions. This response helped improve cloud security. Leaks coming from GitHub and other repository apps are having a similar effect on SaaS security. They have raised awareness of the need for SaaS security, and have helped businesses upgrade their security profile.
Securing GitHub and preventing them from leaking source code and other information isn’t a particularly complex task. It requires an SSPM to monitor the application’s configurations and share settings. SSPMs provide automated, 24/7 monitoring, and they alert security team members and developers when settings are changed.
There are several high-risk settings to keep an eye on. Two-factor authentication should always be required, protecting the source code from password spray attacks or phishing attacks. Public GitHub pages should be closely watched. Public repositories should be closed to the public; if information needs to be shared with outside users, it should be shared with specific users who need to authenticate themselves before accessing the repository. GitHub keys should be rotated, and be deactivated over a reasonable amount of time.
These configurations are just some of the steps savvy organizations should take to plug their GitHub leaks. Controlling access, implementing data leakage protection, and monitoring key management help shore up the applications, and keep source code and other data safe.


Companies store an incredibly large volume of data and resources within SaaS apps like Box, Google Workplace, and Microsoft 365. SaaS applications make up 70% of total company software usage, and as businesses increase their reliance on SaaS apps, they also increase their reliance on security solutions.
SaaS security is not a new problem, however, the attack surface has widened. It started with managing misconfigurations and now goes far beyond. Today, it takes a holistic approach that includes the continuous monitoring and management of user access, roles and permissions, 3rd party apps installed by users, risks deriving from SaaS user devices and Identity Threat Detection & Response (ITDR).
Securing numerous potential attack vectors for each user becomes a challenge when dealing with a diverse range of applications, each having its own unique characteristics. Additionally, the environment is dynamic, from SaaS vendors recognizing the importance of security and continually enhancing their applications with robust security measures to the ever-evolving user governance required (onboarding, deprovisioning, adjustments in roles and permissions). These controls are effective only when properly configured by the organization, for each app and each user, on an ongoing basis. If that’s not enough, these applications are managed by various business departments, making it impractical for the security team to exercise complete control.
The objective in SaaS security is finding the balance between securing applications while still enabling users to do their jobs efficiently.
Below we explain each attack vector and line of defense for a strong SaaS ecosystem security lifecycle.
Misconfigured SaaS settings are one of the leading causes of SaaS data breaches. Security teams have no visibility into security-related aspects of these apps that in most cases are managed by the business departments. To further complicate the picture, each SaaS application uses its own language for settings. This prevents security teams from developing an easy-to-use guide for business teams directing their security efforts. With companies easily averaging over 100 applications, each with hundreds of configurations and multiple users, deciphering and managing security settings is no easy task.
Adaptive Shield integrates with more than 130 SaaS applications to monitor and manage security misconfigurations through in-depth security checks and auto/step-by-step remediation.

Image 1: Bird’s-eye view of the security posture by app

Image 2: List of security checks categorized by app, domain, severity, numbers of users, etc.
Identity Threat Detection and Response (ITDR) capabilities feature a set of security measures designed to detect and respond to identity-related security threats based on key Indicators of Compromise (IOCs). These IOCs provide forensic signs of a potential breach, such as malware, data breaches, unusual behavior, and other suspicious events. ITDR closes the gap between continuous identity governance and identity threat detection within the SaaS ecosystem, covering Tactics, Techniques, and Procedures (TTPs) and unusual User & Entity Behavior Analytics (UEBA) such as account takeover through compromised identities.
When it comes to SaaS threats, existing threat detection and identity management methods don’t go far enough. Today’s SaaS environments are complex and ITDR capabilities within these landscapes require deep knowledge and proven expertise in the way SaaS applications are designed.
Adaptive Shield’s engines cross-reference and analyze in-context TTPs and suspicious events from multiple sources, enabling the accurate detection of very complex and subtle threats.
As a means of prevention and first line of defense, SSPM should operate as the security layer in the identity fabric to establish robust user governance. This includes excessive permissions, access entitlement, user deprovisioning, and more, across the entire SaaS stack. Adaptive Shield provides organizations with deep and consolidated visibility and control of user accounts, roles, permissions, privileged users, and activities.
Identity governance use cases include:

Image 3: View of User Inventory broken down by privileges and user-specific security checks.

Image 4: View of Threat Center and activity information
To improve app functionality, many users integrate third-party apps into the core SaaS stack. These integrations take place without the knowledge of the security team and often ask for intrusive permission scopes, such as the ability to read, write, and delete data. While many of these applications are harmless, if taken over by a threat actor they can cause significant damage.
Adaptive Shield detects every connected third-party application, as well as identifies their scopes. Security teams can then review the information, and make an informed decision on whether to continue using the application.
3rd party app use cases include:

Image 5: View of 3rd-party connected apps with their severity levels and accessed scopes.
The login-anywhere nature of SaaS enables users to access sensitive corporate systems using unmanaged and compromised devices. These devices, which may contain malware, can be exploited to capture access credentials and tokens that can be used by threat actors. This is particularly high-risk when being done by an admin with broad access within the application.
Your SaaS security tool must review device data, and associate each device with a user. When high-privilege users access SaaS apps on a device that contains critical vulnerabilities, it pours the entire application at risk. Managing that risk is a key element of maintaining a secure SaaS stack.

Image 6: View of the SaaS User Device Inventory
Device-to-SaaS Risk Management includes:
Click here to request a short demo and get started with Adaptive Shield


Brick-and-mortar retailers and e-commerce sellers may be locked in a fierce battle for market share, but one area both can agree on is the need to secure their SaaS stack. From communications tools to order management and fulfillment systems, much of today's critical retail software lives in SaaS apps in the cloud. Securing those applications is crucial to ongoing operations, chain management, and business continuity.
Breaches in retail send out seismic shockwaves. Ten years later, many still remember one national retailer that had 40 million credit card records stolen. Those attacks have continued. According to Verizon's Data Breach Investigations Report, last year saw 629 cybersecurity incidents in the sector. Clearly, retailers must take concrete steps to secure their SaaS stack.
And yet, securing applications is complicated. Retailers tend to have multiple tenants of apps, which leads to confusion over which instances of the application were already secured and which are vulnerable to attack. They also have high employee turnover rates, and must quickly deprovision employees as they move on to other opportunities.
Retailers tend to use multiple tenants of the same app to manage different regions within the chain and different product lines across the chain. Consider a scenario where a retailer has fifty different instances of their CRM or ticketing system. Each tenant must be independently secured, following the retailer's guidelines.
While some instances of that application are undoubtedly secure, others present themselves more as a black hole, where no one in the company really knows what's happening. Some instances may have SSO, require MFA, and provide limited role-based access, while other instances may allow all users to login locally with only a single factor.
When most organizations discuss SaaS security, the concern is on protecting data. While that holds true for retailers as well, many retailers have tied their operations to SaaS apps. ServiceNow has reimagined retail experience, enabling retailers to better solve issues, manage their supply chains, and streamline operations.
Risks in apps like these would be catastrophic for a retailer. They could lose visibility and control of their entire supply chain, ordering system, and franchise support platform. This isn't an inconvenience; now that many retailers have completed their digital transformation they must make securing the applications powering operations a top priority.
According to the US Chamber of Commerce, nearly 70% of all retail jobs are unfilled, and surveys indicate that 74% of retail workers are planning to switch jobs this year. Those numbers indicate a transient workforce that needs rapid onboarding and even faster deprovisioning from company SaaS applications.
Many of these processes are automated. However, SaaS applications that are not integrated with the company's Identity Provider (IdP) software retain the employee's access to those apps. Additionally, employees with local access to apps often lose the ability to login with SSO but are still able to directly enter applications.
As part of any retail SaaS security program, attention must be paid to former employees. Revoking access immediately helps reduce the likelihood of data leaks, breaches, and other cyber attacks.
SaaS Security Posture Management (SSPM) enables companies to quantify the risk to their SaaS applications and take the steps needed to secure the stack. SSPMs monitor each tenant of an application independently in one single pane of glass, enabling security teams to identify under-protected applications and take the steps needed to prevent unauthorized access. To further enhance security, SSPMs help users find the most secure tenant and use it as a baseline for securing the other tenants.
SSPMs also monitor users. It can search users to identify those that need to be deprovisioned, and guide the security team on how to best remove access. Meanwhile, SSPMs threat detection capabilities can issue an alert when threat actors have breached the application.
By implementing an SSPM program, retailers can control and protect their SaaS stack, and take advantage of the benefits that come from their digital transformation.


It's easy to think high-tech companies have a security advantage over other older, more mature industries. Most are unburdened by 40 years of legacy systems and software. They draw some of the world's youngest, brightest digital natives to their ranks, all of whom consider cybersecurity issues their entire lives.
Perhaps it is due to their familiarity with technology that causes them to overlook SaaS security configurations. During the last Christmas holiday season, Slack had some private code stolen from its GitHub repository. According to Slack, the stolen code didn't impact production, and no customer data was taken.
Still, the breach should serve as a warning sign to other tech companies. Stolen tokens allowed threat actors to access the GitHub instance and download the code. If this type of attack can happen to Slack on GitHub, it can happen to any high-tech company. Tech companies must take SaaS security seriously to prevent resources from leaking or being stolen.
Slack's misfortune with GitHub wasn't the first time a GitHub breach occurred. Back in April, a stolen OAuth token from Heroku and Travis CI-maintained OAuth applications were stolen, leading to an attacker downloading data from dozens of private code repositories.
MailChimp, a SaaS app used to manage email campaigns, experienced three breaches over 12 months spanning 2022-23. Customer data was stolen by threat actors, who used that data in attacks against cryptocurrency companies.
SevenRooms had over 400 GB of sensitive data stolen from its CRM platform, PayPal notified customers in January that unauthorized parties accessed accounts using stolen login credentials, and Atlassian saw employee data and corporate data exposed in a February breach.
Clearly, tech companies aren't immune to data breaches. Protecting their proprietary code, customer data, and employee records that are stored within SaaS applications should be a top priority.
A strong SaaS posture is important for any company, but it is particularly important for organizations that store their proprietary code in SaaS applications. This code is especially tempting to threat actors, who would like nothing more than to monetize their efforts and ransom the code back to its creators.
Tech companies also tend to rely on a large number and mix of SaaS applications, from collaboration platforms to sales and marketing tools, legal and finance, data warehouses, cybersecurity solutions, and many more – making it even more challenging to secure the entire stack.
Tech employees heavily depend on SaaS apps to do their day-to-day work; this requires security teams to strictly govern identities and their access. Moreover, these users tend to log into their SaaS apps through different devices to maintain efficiency, which may pose a risk to the organization based on the device's level of hygiene. On top of this, tech employees tend to connect third-party applications to the core stack without thinking twice, granting these apps high risk scopes.
The high-tech industry is known for periods of hyper-growth, followed by downsizing. Over the past few months, we've seen Facebook, Google, Amazon, Microsoft, LinkedIn, Shopify and others announce layoffs.
Deprovisioning employees from SaaS applications is a critical element in data security. While much of the offboarding of employees is automated, SaaS applications that are not connected to the company directory don't automatically revoke access. Even those applications that are connected may have admin accounts that are outside the company's SSO. While the primary SSO account may be disconnected, the user's admin access through the app's login screen is often accessible.
At the same time, the industry is ripe with mergers and acquisition announcements. As a result of M&As, the acquiring company needs to create a baseline for SaaS security and monitor all SaaS stacks of merged or acquired companies, while enabling business continuity. Whether the hyper growth is organic or through an M&A, organizations need to be able to ensure access is right-sized for their users, at scale and rapidly.
The majority of data breaches impacting tech companies stem from stolen credentials and tokens. The threat actor enters the system through the front door, using valid credentials of the user.
Identity Threat Detection and Response (ITDR) picks up suspicious events that would otherwise go unnoticed. An SSPM (SaaS Security Posture Management) solution with threat detection engines in place will alert when there is an Indicator of Compromise (IOC). These IOCs are based on cross-referencing of activities such as user geolocation, time, frequency, recurring attempts to login, excessive activities and more.
Maintaining a high SaaS security posture is challenging for high tech companies, who may mistakenly believe they are equipped and well trained to prevent SaaS attacks. SaaS Security Posture Management is essential to preventing SaaS breaches, while an SSPM with ITDR capabilities will go a long way toward ensuring that your SaaS data is secure.


As SaaS adoption continues to grow in the business landscape, it brings emerging security challenges that high-tech and telecom companies must grapple with.
A particularly attractive target for cybercriminals, the telecom industry allows attackers to inflict maximum damage with little effort. The combination of interconnected networks, customer data, and sensitive information allows cybercriminals to inflict maximum damage through minimal effort.
When it comes to the high-tech industry, there is a common misconception that these companies have an advantage, compared to older and established industries that are weighed down by decades of legacy systems and software. However recent breaches, such as the Slack Github attack, have highlighted how the more modern tech companies are also at risk when it comes to SaaS security.
While high-tech and telecom companies operate in different industries, they face common challenges when it comes to SaaS security. The key to choosing and implementing a comprehensive solution is by first recognizing the shared struggles such as the complexity of configurations, third-party app risks, and deprovisioning.
Securing the vast and complex network of SaaS apps, devices, and applications while ensuring smooth operations is not a simple feat. To keep the attack surface limited, organizations need to correctly configure all settings, continuously. In addition to the multitudes of settings, each SaaS app has unique terminology, UI, etc. It is the security team's job to learn every app's "language". With organizations deploying more and more apps everyday, the need for clear and contextualized visibility across all SaaS apps configurations has never been greater.
Both high-tech and telecom companies heavily rely on third-party apps to help boost efficiency and productivity in their day-to-day operations. When these third-party apps are integrated, they are granted permissions known as scopes. While some permissions may be completely harmless, others have the ability to expose an organization's most sensitive data. Security teams need to have visibility into both the number of connected apps and the permissions granted to effectively assess and manage the risk of a third-party app.
The high-tech industry is known for periods of hyper-growth, followed by downsizing. Meanwhile, Telecom companies are among the largest employers in the world with turnover rates hovering at about 18%. Companies operating in either of these sectors are especially exposed when proper deprovisioning lags. Proper deprovisioning ensures that former employees, especially those who are being removed from their job, have access to sensitive data revoked.
While much of the offboarding of employees is automated, SaaS applications that are not connected to the company directory don't automatically revoke access. Even applications that are connected may have admin accounts that are outside the company's SSO. While the primary SSO account may be disconnected, the user's admin access through the app's login screen is often accessible.
Both industries must find a balance between SaaS security and usability. On one hand, robust security measures protect sensitive data, prevent unauthorized access, and mitigate threats. On the other hand, user experience and productivity should not be sacrificed in the pursuit of stringent security measures. Organizations need to educate employees to create a solid understanding of security best practices. This can be achieved through security awareness programs and regular training workshops. Creating this balance is heavily dependent on the collaboration between app owners and security teams.
An SaaS Security Posture Management (SSPM) solution can play a vital role in securing SaaS applications for both telecom and high-tech companies. By providing comprehensive visibility and control over the SaaS environment, an SSPM enables organizations to effectively manage security risks. Consistent security across multiple SaaS applications reduces complexity and minimizes the risk of misconfigurations. By leveraging the capabilities of an SSPM, telecom and high-tech companies can enhance their SaaS security posture, protect sensitive data, and confidently adopt new SaaS apps while mitigating risks.


The Cloud Security Alliance (CSA), the world’s leading organization dedicated to defining standards, certifications, and best practices to help ensure a secure cloud computing environment, today released the findings of its latest survey, SaaS Security Survey Report: 2024 Plans & Priorities. Commissioned by Adaptive Shield, the leading SaaS Security Posture Management (SSPM) company, the survey gathered responses from 1,000-plus C-level security executives and professionals from all over the world, with the majority from North American enterprises.
“Many recent breaches and data leaks have been tied back to SaaS apps. We wanted to gain a deeper understanding of the incidents within SaaS applications, and how organizations are building their threat prevention and detection models to secure their SaaS ecosystem," said Hillary Baron, lead author and Senior Technical Director for Research, Cloud Security Alliance. “This explains why 71% of respondents are prioritizing their investment in security tools for SaaS, most notably turning to SaaS Security Posture Management (SSPM) as the solution to secure their entire SaaS stack.
“The attack surface in the SaaS ecosystem is widening and just as you would secure a cloud infrastructure with Cloud security posture management, organizations should secure their SaaS data and prioritize SaaS security,” asserts Maor Bin, CEO and co-founder of Adaptive Shield. “In last year’s survey, 17% of respondents said they were using SSPM. This year that figure has soared, with 80% currently using or planning to use an SSPM by the end of 2024. This dramatic growth is fueled by the fact that 55% of organizations stated they recently experienced a SaaS security incident, which resulted in ransomware, malware, data breaches, and more. Threat prevention and detection in SaaS is critical to a robust cybersecurity strategy spanning SaaS Misconfigurations, Identity and Access Governance, SaaS-to-SaaS Access, Device-to-SaaS Risk Management, and Identity Threat Detection & Response (ITDR).”
Among the survey’s key findings:
The survey gathered more than 1,000 responses from IT and security professionals from various organization sizes, industries, locations, and roles.


The telecom industry has always been a tantalizing target for cybercriminals. The combination of interconnected networks, customer data, and sensitive information allows cybercriminals to inflict maximum damage through minimal effort.
It's the breaches in telecom companies that tend to have a seismic impact and far-reaching implications — in addition to reputational damage, which can be difficult to measure, telecoms are often at the receiving end of government fines for their cybersecurity and privacy failures.
There are few industries in the world that collect as much sensitive data as telecom companies. In recent years, telecom companies have accelerated their digital transformation, shedding legacy systems and reducing costs. These changes, coupled with the need for stronger collaboration with third-party vendors, have led them to SaaS applications to handle their CRM.
Today, telecoms are using SaaS apps for billing, HR, call management, field operations management, tracking call center effectiveness, and hundreds of other applications. While these apps facilitate communication and help improve processes, the sheer size of these companies requires extra security precautions to be taken, particularly in the areas of collaboration and identity management.
Demographics, behaviors, purchase history, family data, mobile preferences, and browsing history are just a few of the data points that are collected in a global Telecom.
This data is analyzed, packaged, and shared with mobile advertisers. The advertisers are given access to the telecom's SaaS apps, where they can mine for data and develop powerful marketing and advertising campaigns.
However, the partnership between telecoms and their vendors requires app settings to be configured in a way that allows external access while preventing unwanted visitors from seeing, copying, and downloading data.
When configurations drift, they can expose personal data to a far greater audience and put the telecom at risk of breaches.
Telecom partnerships extend to other telecoms. Roaming charges need to be shared between GSM providers for billing purposes, while MVNOs build their entire business model on the telecom's network. This data is captured and stored within SaaS applications, and it may be vulnerable at the point where it is shared between operators.
Telecom companies are among the largest employers in the world. With turnover rates hovering at about 18%, a telecom with 200,000 employees can expect 36,000 employees to leave the company every year, or about 140 per workday.
Much of the employee deprovisioning process is automated. HR removes the employee from the company directory, which triggers processes that shut down their email, network access, SSO access, and other identity-based access points.
Some SaaS applications are connected to the company directory, but many are not. They require additional efforts to deprovision. An admin on a SaaS application, for example, may have multiple logins to the SaaS – one through the SSO and one with a username and password to allow access in the event of an SSO outage. While the SSO access may be automatically revoked, oftentimes in SaaS applications, the secondary access remains active.
Former employees, especially those who are being removed from their job, need their access revoked immediately to prevent the likelihood of data leaks, breaches, and other cyber attacks.
A strong SaaS posture is a must-have for any company. Communication service providers, however, are a tantalizing target to threat actors and need to take their threat detection capabilities to the next level.
SaaS threat detection involves reviewing data from the entire SaaS stack to identify indications of compromise (IOC). These signs of malware, data breaches and other suspicious events within the SaaS ecosystem can direct the security team to any compromised account, and allow them to mitigate the threat.
SaaS Security Posture Management (SSPM) is the first line of SaaS defense. Telecom operators can use the tool to manage their sensitive configurations. Its round-the-clock monitoring of all settings will alert the security team in the event of drift, and its remediation guidelines will show app owners how to secure their data.
SSPMs are also used to monitor users. It can search user rolls from across the SaaS stack to find former employees that need to be deprovisioned, and guide users on how to best remove access. Meanwhile, SSPM's threat detection capabilities can alert the security team when they are facing an imminent threat.
With an effective SSPM in place, telecom operations can use their SaaS applications with confidence, knowing that their data is secure.


CASBs and SSPM are complementary solutions that focus on different aspects of SaaS data security. CASBs apply corporate policies relating primarily to identity, permissions, and data encryption while SSPM protects data from each individual SaaS app based on the usage and settings within each application including identity, permissions, data encryption, and much more.
CASBs have been around for over a decade, continually adapting to meet the needs of cloud and SaaS security. CASBs focus on applying corporate policies to cloud-based entities, and have a wide range of uses.
Traditional CASBs act like a firewall, where all connectivity to SaaS applications passes through a CASB proxy server where it is monitored and all actions are approved. Next gen CASBs connect to SaaS apps through APIs, giving them more access and increasing their SaaS monitoring functionality.
CASBs enable organizations to apply policy across all corporate users, covering things like password rules, SSOs, and permissions, as well as monitoring and applying the way data moves from place to place.
In contrast to CASB’s ability to apply broad corporate policies across all applications, SSPM secures the configurations of each individual application. CASBs function as a broker, viewing the SaaS application from the outside. They track information and users as they access select SaaS applications. SSPMs, in contrast, survey the landscape from within the entire SaaS stack, with protections customized for each application.
This is an important distinction. Salesforce, which is used by the sales team, and Workday, which is used by the HR team, are both SaaS applications but are used by different teams in different ways. The developers of each application also used different languages and strategies while designing security features for each application. Applying a one-size-fits-all CASB-like policy to address security concerns of these two applications simply wouldn’t work. It requires the delicate, individualized touch only an SSPM can provide.
SSPM provides full visibility into business-critical SaaS applications and enables the security team to gain control of every security element. From maintaining continuous hygiene of all security controls to detecting threats within the SaaS ecosystem, SSPMs enable the management and response to any configuration drift or threat.
SSPMs enable organizations to maintain a high SaaS security posture. It checks for misconfigurations, connected third-party applications, identity and access governance, and monitors user devices and their hygiene score. CASBs, however, can only manage some misconfigurations that relate to identity management, permission scopes, and data encryption. CASBs also lack the visibility needed to see third-party applications that are integrated into the SaaS stack.
SSPMs are also capable of threat detection stemming from misconfigurations, third-party applications, and vulnerable user devices in real time.
SSPMs also allow organizations to respond to threats and configuration drifts in real time to mitigate risk. They provide remediation steps, alerts, and ticket creation to help security teams protect SaaS data.
SSPMs and CASBs do have some overlap between them, but the two solutions complement each other. Both are part of a rich, cloud security fabric necessary to protect sensitive data. CASBs focus on applying corporate policies relating to identity, permissions, and encryption. SSPMs complement those efforts by protecting the data and securing access within the individual SaaS application based on usage and configuration settings.
CASBs are proxy-based solutions. They inspect traffic, as well as identify malicious activity and data exfiltration from an in-line perspective of a governed user. SSPMs extend that coverage to external users, contractors, partners, third-party applications, and IoT devices.
CASBs are effective at detecting users who access more data than they should or access data that they should not be seeing. SSPMs add additional protection by identifying misconfigurations that could lead to data becoming publicly accessible without user registration or user creation.
SSPMs are significantly less expensive than CASBs and have a far simpler setup, allowing organizations to protect their entire SaaS stack rather than just a few critical applications. Furthermore, SSPMs can identify non-IdP users that sit outside the organization, and identify user devices with poor security hygiene, capabilities that complete CASB.


Cloud Security Posture Management (CSPM) and SaaS Security Posture Management (SSPM) are frequently confused. The similarity of the acronyms notwithstanding, both security solutions focus on securing data in the cloud. In a world where the terms cloud and SaaS are used interchangeably, this confusion is understandable.
This confusion, though, is dangerous to organizations that need to secure data that exists within cloud infrastructures like AWS, Google Cloud, and Microsoft Azure, as well as data within SaaS applications like Salesforce, Microsoft 365, Google Workspace, Jira, Zoom, Slack and more.
Assuming that either your CSPM or SSPM will secure your company resources that live off-premises is misplaced trust in a security tool that was only designed to secure either your cloud or your SaaS stack.
It's absolutely vital for decision makers to understand the difference between CSPM and SSPM, the value derived from each solution, and that both complement each other.
CSPMs monitor standard and customized cloud applications that are deployed by the customer in a public cloud environment for security and compliance posture. Additionally, they usually provide compliance monitoring, DevOps, and dynamic cloud integration functionality.
Businesses use cloud platforms for many things. Whether it is being used as Infrastructure-as-a-Service (IaaS), which allows businesses to manage elements such as networks, servers, and data storage, or platforms which facilitate the hosting, building, and deploying of customer-facing applications, cloud platforms contain critical business components.
For example, a company might use an IaaS to host its e-commerce website. By using a cloud provider, they have the flexibility to scale their web traffic capacity based on traffic flows. Peak times of day or seasons might increase their capacity, while fewer resources would be needed during off-peak or off-season times.
Within that site, a company might have a separate app that enables customers to prove their identity (know your customer process – KYC). That customer is stored in a container, where the app can access the information as needed, and then authorize the user within the website.This is a common practice of separating different elements of a service (e-commerce, in this case) into different apps, containers, servers, and networks. Such separation, which is enabled by using an IaaS, provides flexibility, better performance, customization, and potentially better security. But all this comes at a cost of great complexity and expanding the attack surface
CSPMs are tasked with monitoring the security posture of the cloud services hosted in IaaS. In practical terms, this means scanning cloud settings and identifying any misconfigurations that could introduce elements of risk to the service. In circumstances where using a complex architecture, using containers in a Kubernetes system, the configurations are particularly complex, and securing them without a CSPM can lead to configuration drifts that expose data to the public.
SSPMs, like Adaptive Shield, integrate with a company's applications, like Salesforce, Jira, and Microsoft 365, to provide visibility and control to the security teams and app managers for their SaaS stack. Such SaaS (Software-as-a-Service) apps are not hosted in the company's network or cloud infrastructure, rather they are hosted by the software provider.
Security teams have a unique challenge in securing SaaS applications. Each SaaS application uses a different topology for its settings. Security teams can't issue a one-size-fits-all directive on SaaS app configurations, while they need to secure many apps.
SaaS applications store a tremendous volume of company data and resources. Customer data, financial reports, marketing plans, employee profiles, and more are all stored within different SaaS apps. This makes sharing and collaboration simple but also acts as a beacon to threat actors who wish to monetize or sabotage company resources.
SSPMs deliver visibility into the settings of each application, providing a security score and alerting security teams and app owners when there are high-risk misconfigurations.
SSPMs extend their coverage into apps that are easily onboarded by employees. SSPMs provide security teams with a list of connected applications, as well as the permission scopes that have been granted to the app.
Security teams are also concerned about users, especially privileged users, accessing SaaS applications using a compromised device. SSPMs provide a user inventory and device inventory. These inventories display users, the apps they are associated with, their permission scopes, and the hygiene of the devices they are using to access SaaS applications.
Clearly, CSPMs and SSPMs are integral pieces of a robust cloud security platform. Any company using multiple SaaS applications with multiple users needs an SSPM solution to protect its data. At the same time, any company using cloud services like Azure, GCP, or AWS would be putting its operations at risk without a CSPM solution.
CSPMs allow organizations to identify their misconfigured networks, assess data risk, and continually monitor cloud events in their cloud environment. SSPMs help organizations identify and remediate misconfigurations, manage third-party applications, detect configuration drifts, manage users, and comply with universal or industry standards.
The two security tools each cover valuable use cases. CSPMs identify vulnerable cloud configuration settings, provide compliance for security frameworks, monitor cloud services, and manage changes that are made to their logs.
SSPMs have similar use cases, but in the SaaS environment. They offer continuous 24/7 visibility into misconfiguration management, and enable security teams to monitor SaaS-to-SaaS access. It offers compliance reports from the entire stack, rather than individual applications, and can help IT teams optimize their SaaS license spending. It manages risk from users and devices, as it ensures that only authorized personnel have access to the SaaS data.
SSPMs are also used to monitor CSPM applications. As the CSPM is a SaaS solution, SSPMs can ensure the CSPM configurations are set correctly, review connected third-party applications, and provide user governance.
Working together, SSPMs and CSPMs ensure the security of your off-premise data by providing visibility and remediation actions that close vulnerabilities and reduce risk.


Access control is the key to your SaaS kingdom. It determines who has access, their permission levels, and the steps they need to take to enter into the system.
Access control is the center of your SaaS security foundation, which is why it accounts for 59% of all SaaS configurations. Of the 13,000 configurations Adaptive Shield checks out of the box, over 7,500 address access control.
Access control is a multi-level domain, with layers of security elements all intended to prevent unauthorized users and threat actors from accessing your data. This first line of defense requires oversight and nuanced approach to balance SaaS usability and availability with security.
Access control configurations impact every employee within the company with access to specific apps. Employees from different teams may require different areas of access, while employees with a team may need different levels of access.
In an app like Salesforce, IT admins need administrative access. Some sales personnel may need access to marketing costs, while others might also need access to reports. On the sales team, sales reps should only have access to their leads, while sales managers should have access to all the leads within their department or domain.
Creating these types of role-based access profiles is complex, and it’s tempting to over-permission users. The configuration settings may appear overwhelming, which is why we’re sharing some foundational settings within Salesforce, Microsoft 365, and Google Workspace for an effective access control policy.
Salesforce is the leading CRM in the market. It contains an immense amount of sensitive information, and protecting that data is of paramount importance. Comprehensive user authentication policies are vital to ensuring security.
Connecting Salesforce to your organization’s SSO/IDP solution is one of the core ways to ensure and enforce access control. Over 80% of the Salesforce instances our research team reviewed have enabled SSO. However, only 2% of those organizations required users to login through SSO.
A surprising 98% of organizations allow their users to access Salesforce using a basic username and password authentication. This misconfiguration enables threat actors to capture usernames and passwords through sophisticated phishing attacks or other means. Once that username is compromised, threat actors have access to a wealth of customer and pipeline data.
Here are some other Access Control configuration benchmarks that you can use to measure your security posture against.


Microsoft 365 documents, presentations, spreadsheets, and email are among a company’s most valuable resources. Sharepoint servers contain files, making it easy for employees to collaborate on critical projects. The data within Microsoft 365 demands robust access control. Here are Access Control benchmarks to measure your company against.
Legacy authentication protocols in M365 may be undermining your entire security setup. Security teams can implement SSO, harden password policies, require MFA, and keep Azure Active Directory updated and well maintained – and still find themselves exposed.
Legacy authentication protocols within M365 means usernames and passwords are often stored on the device. These login credentials are sent at every request, increasing the likelihood of those access credentials being compromised especially if sent without Transport Layer Security (TLS).
Basic authentication, while necessary for companies using legacy software, is unable to enforce MFA and is superseded by modern authentication. These include IMAP, OAB, Exchange ActiveSync (EAS), and others.
As a result, over 80% of the M365 instances we reviewed had at least one legacy authentication protocol enabled, and over 50% had two or more. 10% have almost all legacy authentication protocols enabled, and many of them are used daily.

As a result, over 80% of the M365 instances we reviewed had at least one legacy authentication protocol enabled, and over 50% had two or more. A surprising 10% have almost all legacy authentication protocols enabled, and many of them are used daily.

Like M365, Google Workspace uses legacy authentication protocols, such as IMAP and POP. In addition, it uses some high-risk configurations that are unique to Google Workspace. App Passwords are a special tool used to connect third party applications to a SaaS stack. App Passwords can provide access into an application, and they don’t require MFA for authentication.
App Passwords were created to allow external apps to integrate with Google Workspace as the equivalent of an API key. However, they allow users to bypass MFA and SSO.
To strengthen an organization’s security and reduce risk, app passwords should never be used by super admins. Regular users can use App Passwords, as long as the passwords are monitored and rotated appropriately.


Access Control is a significant security function and creates the first line of defense of an organization’s SaaS security policy. In turn, security teams are responsible for strengthening and ensuring an organization’s access control.
Security teams can begin creating a strong foundation of access control by:
Up next in our Benchmark for SaaS Apps Series is Data Leakage Protection, the practice of detecting and preventing data breaches, exfiltration, or unwanted destruction of sensitive data.


As organizations work toward securing their SaaS apps, security teams are looking for benchmarks that can help guide their efforts. SaaS ecosystems are growing quickly, and without some standardized tool to measure success, most security teams lack the data to know where they stand.
In our Benchmarks for SaaS Apps series, we’ll share benchmark data for five high-impact security domains. These domains contain thousands of settings, spanning organizational users, applications, and instances. When configured correctly, they limit data access to authorized users, protect against SaaS ransomware, and limit potential breaches.
Each article in this series will cover high-risk configurations in Google Workspace, Microsoft 365, and Salesforce, as well as provide data that can be applied to every app in your SaaS stack.
The top five security domains in SaaS are:
Adaptive Shield cybersecurity experts and researchers extracted anonymized data from hundreds of tenants and apps within the Adaptive Shield system.
First up in the series is Access Control!


Collaboration sits at the essence of SaaS applications. The word, or some form of it, appears in the top two headlines on Google Workspace's homepage. It can be found six times on Microsoft 365's homepage, three times on Box, and once on Workday. Visit nearly any SaaS site, and odds are 'collaboration' will appear as part of the app's key selling point.
By sitting on the cloud, content within the applications is immediately shareable, making it easier than ever to work with others.
However, that shareability is a two-sided coin. On the flip side are often sensitive links sitting on public-facing websites that can be easily accessed. The exposure caused by leaked documents can cause tremendous harm, from competitors trying to gather corporate secrets to whistleblowers sharing internal information with reporters or legislators. As integral as collaboration is to SaaS, sharing links creates a high-risk situation, and real-life breaches, that can be mitigated through the right processes.
There are essentially two ways to share files and documents out of a SaaS application, although the terminology used by M365, Salesforce, Google Workspace, and Box is slightly different. The file owner can either make the resource available to specific users or make it available to "anyone with a link".
Sharing the file with specific users can be cumbersome and time-consuming. As the file gets passed to different stakeholders, the file owner needs to add every user as they need it. When working with an outside vendor, that requires coordination with the vendor contact to understand who will be working with the file. Each user's email address needs to be added individually, and if someone is missed, the file owner needs to go back into the sharing settings and add them.
Sharing a file with anyone who has the link is much less cumbersome. The document owner can copy the link, send it to the vendor, and not have to think about document management any longer. Additionally, often people request access from a private account (for example, their gmail email) instead of a business-monitored email account. This could be due to the fact that sometimes external vendors only have a private domain, or it could be they are also logged in to their private account and so they accidentally request access to it.
However, as tempting as it is to share the link freely, doing so primes the document to being leaked. There is no controlling what happens to the file once the link is shared, and users can access the file from any account. The degree of risk that the file can be leaked increases exponentially.
New York City school officials learned the dangers of link sharing the hard way. In 2021, school officials confirmed a data leak that contained sensitive information of over 3,000 students and 100 staff members in the NYC public school system. The data was exposed when a student gained access to a Google Drive.
That story came on the heels of a Microsoft Sharepoint breach, during which a student doing homework stumbled onto a draft document discussing when schools would reopen during COVID-19. The letter included details of testing policies, quarantine policies, and other information that the school system was not ready to release. This data was exposed due to unsecured document-sharing settings.
It isn't just school officials who need to be careful with their shared links. In 2021, an armed forces unit asked soldiers to fill in a Google form relating to their COVID-19 vaccines. Each soldier entered their name and ID number, and answered questions relating to coronavirus.
However, the author of the Google Form allowed respondents to review the results. Anyone with the link had access to the soldiers' names and ID numbers. The data was listed chronologically, making it easy to group specific soldiers by their unit. This data was accessible to anyone with a browser and link. After being alerted, the military unit removed the form, but it's impossible to know how far the data leaked.
According to TechCrunch, in 2019 security researchers found dozens of companies were leaking sensitive corporate and customer data that was saved in Box. Using a script to scan for box accounts, researchers found over 90 companies – including Box – with data that was visible to anyone with the link.
Companies, which included Amadeus, Apple, Edelman, and Herbalife, exposed customer names and contact information, project proposals, donor names, patient information, and more. This information could have easily been protected had companies used the access controls available within the platform.
The data contained in SaaS apps lives on the cloud, but it doesn't need to be exposed to anyone with a link. Security-conscious organizations should follow these guidelines to ensure their data remains secure.
Share files with specific users – Requiring users to login before they can access the data drastically reduces the likelihood of data falling into the wrong hands
Add expiration dates to shared links – Most documents and files are shared and eventually forgotten about, putting companies in a position where they don't even know that they are exposed. By adding an expiration date to the link, that oversight won't come back to hurt the company.
Password protect all links – Add an additional layer of data security by requiring password protection on all external-facing files
Create a Resource Inventory – List all corporate resources in a single place that includes each file's share settings, providing security teams with a single view that enables them to evaluate risk and exposure.
Every unprotected link has the potential to expose data. As the link sharer, it is impossible to know the hygiene of the recipient's device, whether they will share the link with others, or even whether they provide others with access to their email account. Securing links is one of the main ways of protection available to limit this risk.
Another approach to protecting against links being overly shared is the automated method, through use of an SSPM solution. An SSPM, like Adaptive Shield, helps organizations protect against data loss by identifying which resources are being publicly shared and are at risk. It can also identify resources that are shared without an expiration date, or are set to allow guests to share the item. Once the security team is aware of the attack surface, they can remediate and secure the link as needed.
.png)
.png)
It’s that time of the year, when RSA brings together leaders and visionaries from across the cybersecurity world. During these four days, visitors gain insight, join conversations, and experience solutions that make an impact on their business and career. From live sessions and parties to games and demos galore, RSA packs it all. That being said, there’s a lot to choose from and only so many hours in the day. That's why we have gathered a list of the top 7 activities for the SaaS security aficionados to hit at RSA 2023.
Book an in-person meeting with our experts at RSA here.
With the world of cybersecurity changing so rapidly, it’s often difficult to keep up with new attack vectors and terminology. Two vastly different topics but often referred to interchangeably are IAM and identity security. That's why Derek Melber, VP of Product Engagement and Outreach at QOMPLX is hosting a roundtable to dive deeper into the difference between the two.
Microsoft’s Principal Product Manager, Shinesa Cambric, takes to answering the question: Is it possible to apply Zero Trust to billions of consumer identities while simultaneously addressing the challenges of growing a business and preventing fraud? Through this case study, attendees will learn about the challenges faced and lessons learned when balancing user experience and protection while simultaneously introducing friction to prevent and detect malicious actors.
Adaptive Shield is bringing the Fun Fair all the way to RSA at booth #1449. Our experts will demonstrate the Adaptive Shield Platform and cover use cases like misconfiguration management, SaaS-to-SaaS access discovery and control, Device-to-SaaS user risk management, Identity and Access Governance, and Identity and Threat Detection and Response (ITDR).
Vulnerabilities in the attack surface are everywhere, yet most of today’s approach to threat management is reactive-focused. Nico Popp, Chief Product Officer at Tenable, criticizes the emphasis placed on detecting and containing threats instead of preventing them in the first place. This session will delve into how exposure management delivers unified visibility, context-driven prioritization, and risk-based metrics as the foundation for tomorrow’s preventive security.
In the past ten years, organizations have adopted and come to depend on SaaS apps and other technologies to keep their businesses successful. However as business tools evolve, so does their risk. David Foote, Chief Analyst and Research Officer at Foote Partners, dives into the challenges of the conventional thinking about the ‘Future of Work’, presenting an alternative view from deep insights gained from 4,100 employers.

Everyone deserves a little fun at the end of a hard day’s work which is why Adaptive Shield is the title sponsor of the FOMO party. This afterparty will have great music and scrumptious food. The FOMO party is definitely the place to be. Don’t miss your chance to attend THE afterparty at RSA, register now.
It’s a known fact that everyone is moving to the cloud. The conversation has shifted from the “battle” to the transformation of the cloud. The largest benefit of moving to the cloud is security, and the advantages are clear compared to the on-premise environments. This session, led by Orcale’s Senior Vice President David Cross, will cover not only the advantages, but more importantly how to compare and evaluate the on-premise security posture to the next generation SaaS cloud environment in a detailed framework.
For anyone attending RSA interested in SaaS security, or even those who are not, these 7 activities are sure to provide insights into today's market and available solutions. Make sure to visit booth #1449 to experience the Adaptive Shield Fun Fair and try your hand to win a carnival-worthy prize. Also, schedule a meeting with one of our experts for a customized look into how you can gain control over your SaaS stack . We look forward to seeing you there!


Microsoft is a primary target for threat actors, who scour Microsoft applications for weaknesses. Our security research team at Adaptive Shield recently discovered another new attack vector caused by a vulnerability within Microsoft’s OAuth application registration that allows attackers to leverage Exchange's legacy API to create hidden forwarding rules in Microsoft 365 mailboxes.
To understand this new attack vector, you must understand the key components therein. These include hidden forwarding rules and SaaS-to-SaaS app access, all of which amount to a malicious SaaS rootkit that can infiltrate users' accounts and control their mailboxes — without the users' knowledge.
Inbox rules are actions that occur based on preset conditions within a Microsoft mailbox. Users or admins can use forwarding rules to trigger protocols based on different attributes of the user's inbox.
Hidden forwarding rules (Figure 1) were first discovered by Compass Security’s Damian Pflammater in 2018. He covered the discovery and Microsoft’s response in a blog post titled “Hidden Inbox Rules in Microsoft Exchange.” These rules are fully functional and can be seen on the backend. However, they are not visible common interfaces such as email clients, an admin dashboard, or an API (Figure 2).


SaaS-to-SaaS app access, also referred to as third-party app access, describes the conditions under which one app can connect to another app and, in doing so, gain access and permission to different information and settings. The OAuth 2.0 mechanism simplifies the process of authentication and authorization between consumers and service providers through a seamless process that allows users to quickly verify their identities and grant permissions to the app. The app is then allowed to execute code and perform logic within its environment behind the scenes.
In many instances, these apps are completely harmless and often serve as a valuable business tool. In other instances, these apps can act as malware, similar to an executable file.

With this SaaS rootkit, threat actors can create malware that lives as a SaaS app and can infiltrate and maintain access to a user’s account while going unnoticed.
While bad actors can't find Exchange Legacy scopes that can be used to add programmatically online hidden forwarding in the Microsoft UI, they can add them through a terminal script.
The attacker's job is simple: Create an app that looks credible, add the legacy scope protocols removed from the UI to the app (exploiting the vulnerability that the Adaptive Shield team uncovered), and send an offer to users to connect to it. The user will see an OAuth app dialog box on the official Microsoft site, and many will likely accept it (Figure 4).

Once a user accepts, the bad actor receives a token that grants permission to create forwarding rules and hides them from the user interface like a rootkit.
An attack through these hidden forwarding rules should not be mistaken for a one-off attack but, rather, the start of a new attack method through SaaS apps.
In 2022, Adaptive Shield contacted Microsoft about the issue, Microsoft in response said that the issue has been flagged for future review by the product team as an opportunity to improve the security of the affected product.
There's no bullet-proof way to eliminate SaaS rootkit attacks but there are a few best practices that can help keep organizations more protected.
Hidden forwarding rules are still a threat, even more so when they appear through the trusted Microsoft website. The traditional controls that were created to stop malware have struggled to keep up with the evolution of malware and the new attack vector that can exploit any SaaS app, from M365 to Salesforce to G-Workspace, etc. Organizations should utilize native security configurations to control the OAuth application installations across SaaS apps to protect users from malicious attacks like these.


The National Institute of Standards and Technology (NIST) is one of the standard-bearers in global cybersecurity. The U.S.-based institute’s cybersecurity framework helps organizations of all sizes understand, manage, and reduce their cyber-risk levels and better protect their data. Its importance in the fight against cyberattacks can’t be overstated.
While NIST hasn’t directly developed standards related to securing the SaaS ecosystem, they are instrumental in the way we approach SaaS security.
NIST recently released its Guide to a Secure Enterprise Network Landscape. In it, they discuss the transformation from on-premise networks to multiple cloud servers. Access to these servers, and the accompanying SaaS apps, is through both secure and unsecured devices and locations across disparate geography.
The move to the cloud has effectively obliterated the network perimeter. As a result, companies have increased their attack surface and are experiencing an escalation of attacks that span across network boundaries.
Rather than focus on network-centric security, security must take a three-pronged approach. The user, endpoint, and application are keys to protecting data. This new paradigm emphasizes the importance of identity, location, and contextual data associated with the user, device, and service.
Today’s security tools need to scale to meet the volume, velocity, and variety of today’s applications. They need to integrate seamlessly with SaaS applications and provide coverage for the entire SaaS stack.
To be effective, these tools need to minimize human intervention for monitoring and remediation. Automation is critical for an ecosystem that demands secure configurations for each user account that has access to the application. Large organizations may have millions of configurations to secure across their entire SaaS stack; closing them manually is an impossible task.
SaaS security tools must be able to integrate with all the apps on the stack and identify each application through the SaaS app’s APIs. Once connected, it must monitor the security configurations, staying alert to any changes. This configuration drift can have severe consequences, as it exposes SaaS applications by removing the safeguards put in place to prevent unauthorized access. It needs to continuously monitor applications, and issue alerts as risk increases.

Effective SaaS security tools use contextual data to detect threats to the application and its data. These threats can come from humans and machines and may have access to the system using verified credentials.
Contextual data from across the SaaS stack can help identify paradoxical travel, spikes in failed authentication attempts from the same IP address for multiple accounts, or attempts where automated tools test weak and common passwords against known user names. It can also recognize malicious third-party applications that are significantly overprivileged for their functionality.

In the world of SaaS, the devices represent the network perimeter. Accessing SaaS applications with devices that have poor hygiene can put all the data at risk. Compromised devices can hand over login credentials to threat actors, who can leverage that into breaching and stealing data.
Effective SaaS security tools partner with endpoint security providers to ensure that the devices that access SaaS apps have an up-to-date operating system, all software has been updated, and any patches have been applied.

While devices may be the perimeter, user ID is the barrier preventing unfettered access to company data. Access should be given using a zero-trust approach. All access should be granted through an SSO connected to an enterprise-managed IdP. Organizations should reinforce this entryway with a phishing-resistant MFA authenticator.

Effective SSPM platforms are built on robust security checks that review each SaaS configuration to ensure they are optimized for protection. Typically, security setting recommendations are influenced heavily by NIST’s cybersecurity approach, and their guidance enables SSPM vendors to monitor and track usage, users, and behaviors, as well as identify threats.


Spoiler Alert: Organizations with 10,000 SaaS users that use M365 and Google Workspace average over 4,371 additional connected apps.
SaaS-to-SaaS (third-party) app installations are growing nonstop at organizations around the world. When an employee needs an additional app to increase their efficiency or productivity, they rarely think twice before installing. Most employees don't even realize that this SaaS-to-SaaS connectivity, which requires scopes like the ability to read, update, create, and delete content, increases their organization's attack surface in a significant way.
Third-party app connections typically take place outside the view of the security team, are not vetted to understand the level of risk they pose.
Adaptive Shield's latest report, Uncovering the Risks & Realities of Third-Party Connected Apps, dives into the data on this topic. It reviews the average number of SaaS-to-SaaS apps organizations have, and the level of risk they present. Here are the top 5 findings.
The report focuses on Google Workspace and Microsoft 365 (M365), as it paints a clear picture of the scope of applications that are integrating with the two applications.
On average, a company with 10,000 SaaS users using M365 has 2,033 apps connected to its suite of applications. Companies of that size using Google Workspace have more than three-times the amount, averaging 6,710 connected applications.
Even smaller companies aren't immune. The report found that companies using M365 average 0.2 applications per user, while those using Google Workspace average 0.6 applications per user.
In contrast to most growth curves, the research shows that the number of apps per user doesn't level off or plateau once reaching a critical mass of users. Rather, the number of applications continues to grow with the number of users.
As seen in figure 1, companies using Google Workspace with 10,000-20,000 employees average nearly 14,000 unique connected applications. This continued growth is shocking to security teams, and makes it nearly impossible for them to manually discover and manage the high volume of applications.

When third-party apps integrate with core SaaS apps, they gain access using an OAuth process. As part of this process, applications request specific scopes. These scopes hand over a lot of power to the apps.

Among high-risk scopes, 15% of M365 applications request the authority to delete all files that the user can access. It gets even scarier in Google Workspace applications, where 40% of high-risk scopes receive the ability to delete all Google Drive files.
As shown in this permission tab, the application explicitly requests permission to see, edit, create, and delete all Google Docs documents, Google Drive files, Google Slides presentations, and Google Sheets spreadsheets.
For security teams accustomed to controlling the data, permission sets like these are unsettling. Considering that many applications are created by individual developers who may not have prioritized security in their software development, these permissions provide threat actors with everything they need to access and steal or encrypt company data. Even without a threat actor, a bug in the software can have disastrous consequences for a company's data.
While the report deep dives into the big two SaaS apps, it does also release research into Salesforce (and Slack). Salesforce averages 41 integrated apps per instance. The implication of this is noteworthy.
Salesforce is primarily used by a small subset of the company. In that regard, it's similar to Workday, Github, and ServiceNow, which are used by HR, developers, and finance teams. A typical company with 10,000 employees has over 350 SaaS applications in its stack, many of which are used by smaller departments like the apps discussed here.
Assuming Salesforce is typical of similar applications, those 350 apps integrating with 40 apps each adds an additional 14,000 third-party applications into the equation.
One of the more interesting takeaways was the high volume of high-risk apps connecting to Microsoft compared to Google Workspace. Apps request high-risk permissions from M365 39% of the time; Google Workspace apps only request high-risk permissions 11% of the time. In terms of real numbers, an average installation in a company with 10,000 SaaS users using M365 will have 813 high-risk apps, while Google Workspace will have 738 apps that are considered high-risk.
In all likelihood, this disparity is caused due to the app creation process. Google requires apps requesting high-risk (it calls them Restrictive) permissions to be reviewed. The review process is far easier for those requesting medium, or sensitive, permissions. Microsoft doesn't label requested scopes with severity levels. This lack of oversight makes it much easier for apps that connect with M365 to request high-risk scopes.
The overall takeaway from reading the report is the immense challenge of securing SaaS software. It's clear that security teams need visibility into the thousands of apps being connected to the SaaS stack, and make a cost-benefit analysis for each high-risk connected app.
SaaS security solutions, like Adaptive Shield, provide security teams with the visibility needed to see connected applications and their scopes, among other important SaaS security capabilities. Armed with this information, security teams will be in a far better position to harden their applications' security posture and prevent data from falling into the wrong hands.


Tel Aviv, February 27, 2023—Adaptive Shield, the leading SaaS Security company, today announced the release of its SaaS-to-SaaS Access Report. According to the research, employees are granting thousands of third-party apps access to the two most dominant workspaces, Microsoft 365 (M365) and Google Workspace. With no oversight or control from security teams, companies have no way to quantify the risk that these SaaS-to-SaaS connections present to their businesses.
While these SaaS-to-SaaS connections provide enhanced features that boost workflow efficiency, they also give permission for apps to read, update, create, delete, or otherwise engage with corporate and personal data. In its report, Adaptive Shield identifies how many SaaS apps are being connected to the core SaaS stack, specifically M365 and Google Workspace and business-critical apps such as Salesforce and Slack, the types of permissions being granted to these applications, and the risk level these apps present.
According to the research, companies with 10,000 SaaS users average 2,033 applications connected to M365 and 6,710 connected to Google workspace. For the companies using Google Workspace, that figure jumps to an average of 13,913 connected apps for 10,000 - 20,000 SaaS users.
While the risk level for permissions varies from one app to the next, Adaptive Shield researchers found that 39% of apps connected to M365 and 11% to Google Workspace have ‘high-risk’ permission access. Additional details on these include
“The simple app-to-app connectivity that makes SaaS apps vital productivity tools also makes them significantly dangerous,” said Maor Bin, CEO of Adaptive Shield. “While it’s clearly unrealistic to expect businesses to curb their reliance on SaaS apps, they cannot allow this adoption to go unchecked. To eliminate these risks companies must develop policies for integrating apps, prioritize employee training, and deploy monitoring solutions that help over-taxed security teams identify and eliminate high-risk permission sets before it’s too late.”
While these challenges are most prominent in M365 and Google Workspace, they are not exclusive to these apps. As part of this effort, Adaptive Shield examined two other business-critical apps, Slack and Salesforce. The research shows that organizations have an average 222 SaaS-to-SaaS apps for Slack and another 41 apps for Salesforce.
A final area of research are app categories that are connected most frequently. According to the research, email applications are far and away the number one connected category followed by apps related to file and document management, communications and meetings, and calendars and scheduling.
The Adaptive Shield full report, 2023 SaaS-to-SaaS Access Report: Uncovering the Risks & Realities of Third-Party Connected Apps, is available now.


When SaaS applications started growing in popularity, it was unclear who was responsible for securing the data. What's far murkier, however, is where the data responsibility lies on the organization's side. For large organizations, this is a particularly challenging question. They store terabytes of customer data, employee data, financial data, strategic data, and other sensitive data records online.
SaaS data breaches and SaaS ransomware attacks can lead to the loss or public exposure of that data. Depending on the industry, some businesses could face stiff regulatory penalties for data breaches on top of the negative PR and loss of faith these breaches bring with them.
Finding the right security model is the first step before deploying any type of SSPM or other SaaS security solution.
There are several different groups of players involved in the SaaS security ecosystem.
SaaS App Owners – When business units subscribe to SaaS software, someone from within the business unit is typically responsible for setting up and onboarding the application. While they may have some help from IT, the application is their responsibility.
They choose settings and configurations that align with their business needs, add users, and get to work. SaaS App Owners recognize the need for data security, but it isn't their responsibility or something they know very much about. Some mistakenly assume that data security is only the responsibility of the SaaS vendor.
Central IT – In most large organizations, Central IT is responsible for things like infrastructure, hardware, and passwords. They manage IDP and servers, as well as oversee help desk activities. SaaS applications typically do not fall under their direct domain.
Central IT is more familiar with security requirements than the average employee, but it isn't their primary concern. However, it is important to keep in mind that they aren't security professionals.
Security Teams – The security team is the natural fit for implementing security controls and oversight. They are tasked with creating and implementing a cybersecurity policy that applies across the organization.
However, they have several challenges inhibiting their ability to secure applications. For starters, they are often unaware of SaaS applications that are being used by the company. Even for applications that they are aware of, they lack access to the configuration panels within the SaaS stack, and aren't always aware of the unique security aspects associated with each application. Those are controlled and maintained by the SaaS App Owners and Central IT.
GRC Teams – Compliance and governance teams are tasked with ensuring that all IT meets specific security standards. While they don't play a specific role in securing corporate assets, they do have oversight and need to determine whether the company is living up to its compliance responsibilities.
SaaS Vendor – While the SaaS vendor is absolved from any responsibility to secure the data, they are the team that built the security apparatus for the SaaS application, and have a deep knowledge of their application and its security capabilities.
Securing the entire SaaS stack requires close collaboration between the security experts and those managing and running their individual SaaS applications. We developed this RACI chart to share our perspective on the departments that are responsible, accountable, consulted, and informed for the different tasks involved in securing SaaS data.
Bear in mind, this table is not one size fits all, but a framework based on the way we see many companies handling their SaaS security roles. It should be adapted to the needs of your organization.

Developing the RACI matrix is important, but without the right tools in place, implementing security responsibilities becomes a near-impossible task.
Adaptive Shield’s SSPM platform facilitates clear communication between the security team and app owners. This communication includes alerts when misconfigurations occur that weaken the individual app’s security posture and when threats are detected by our IAM governance tools.
Communication is channel agnostic, so users can receive messages and alerts over email, Slack, Splunk, or the messaging platform of choice. All security-related notifications include remediation steps, providing app owners and central IT with a clear understanding of the steps required to mitigate the risk.
Within the platform, app owners have visibility and access to the app or apps under their control. They can see the status of their security settings, their security score, their users, third-party SaaS applications that are connected to their app, and the devices being used to access their SaaS app.
App owners and central IT are also able to dismiss a security alert due, either because it doesn’t apply or due to business needs, and consult with the security team on risk.
It’s easy for SaaS application security to be overlooked. It sits outside the view of the security team and is managed by competent professionals whose responsibilities don’t include security.
However, the data contained within the SaaS applications are often the lifeblood of an organization, and failure to secure the data can have disastrous consequences.
Fully protecting the data from exposure requires a cross-team effort and commitment from all parties involved, as well as a sophisticated SSPM platform built for SaaS in the real world.
.png)
.png)
Security teams can’t protect every byte within their digital footprint. Limited resources mean making choices, and so security teams run assessments to evaluate the value of their assets, the cost to protect those assets, and the damage to the company should an asset be breached or compromised.
In some industries, regulatory requirements shape those decisions, while other industries can be determined based on organizational needs.
The assessment frequently leaves SaaS applications, and the data they contain outside of the company’s protective shield. Organizations often believe the data stored within SaaS applications is less sensitive than other corporate IP and accept that the security tools built into the SaaS app are strong enough to provide adequate protection.
In a sense, those assessments are right. Most SaaS apps don’t contain the company's crown jewels, and nearly every SaaS application comes with a robust security tool set that should protect all the data within the SaaS app. Unfortunately, that view is leaving critical data exposed online, putting organizations at risk of data exposure, ransomware, and regulatory fines.
Companies store some of their most important data within SaaS applications.
Salesforce stores all company leads, its sales pipeline, and customer data. Sharepoint contains critical files and work product. Bamboo HR stores employee data. GitHub contains software code. Netsuite stores key financial documents. Google Workspace and Microsoft 365 contain files and email.
Organizations’ tech stacks are comprised of applications like these. Failing to secure the data would represent a significant loss to a company. Depending on the nature of the attack, all data stored within the application could be lost forever, shared with competitors, or held for ransom.
Generally speaking, there are three motivations for an attack on a SaaS app. Threat actors want to steal data, steal money, or sabotage a company. Each of these attack types manifests itself in different forms. A grab for data, for example, might involve threat actors remaining in the shadows while playing the long game, while a saboteur or ransomware attack would involve different styles of attack.
When SaaS applications are left unprotected organizations can quickly find themselves dealing with a large scale SaaS security incident.
Data theft often involves competitors accessing a SaaS application and downloading critical company information. Threat actors need to gain credentials to access the SaaS, and then move laterally to increase their access and find the intellectual property they crave. Once they find the data, they tend to download it slowly to avoid raising any security flag.
These attacks can be difficult to detect, considering that the perpetrators are often authorized or former employees. Companies that recently laid off employees or are involved in negative news stories are at higher risk of sabotage.
Like all SaaS apps, security begins with access management. Organizations should be especially careful with high-privilege dormant accounts, such as those accounts that were used for setup but have been dormant or accounts shared by multiple users. Access must also be removed for employees that have been let go.
These accounts, if left active, offer pathways to sensitive data without any way for security teams to know which current or former user is accessing them.
Most don’t usually associate ransomware with SaaS applications. Today, we are seeing an increase in these types of attacks. SaaS data is accessed through a user account or malicious app, and then encrypted pending the payment of a ransom.
These ransomware attacks often carry a secondary attack mode, particularly when the compromised SaaS app contains PII data or involves highly regulated industries. In addition to encryption, the threat actor threatens publishing the data online. In these nightmarish scenarios, organizations are motivated to pay the ransom to protect themselves from negative PR and regulatory penalties for failing to adequately protect the data they collected.
For the most part, the security configurations on SaaS applications are sufficient to secure the data contained within the application. In a perfect world, those configurations would be set once, securing the apps and the data within against nearly all threats.
However, SaaS configurations are often adjusted by users trying to enhance functionality or improve accessibility. Configuration drift leads to vulnerabilities, which creates an opening for threat actors to take advantage. Third-party applications, which are connected to SaaS applications and granted scopes enabling them to delete records, send emails, and add new data, increase the attack surface.
Lacking visibility, the security team has no way of knowing whether SaaS applications have retained their secure posture over time, or whether a malicious third-party application has been inadvertently connected to a business-critical application.
SaaS Security Posture Management (SSPM) with SaaS threat detection automates security checks and provides the visibility needed for every third-party app. It enables security teams to detect threats against data and respond appropriately against imminent threats. Adding SSPM to your security stack is vital in securing SaaS-based critical data.


The move to SaaS and other cloud tools has put an emphasis on Identity & Access Management (IAM). After all, user identity is one of the only barriers standing between sensitive corporate data and any unauthorized access.
The tools used to define IAM make up its identity fabric. The stronger the fabric, the more resistant identities are to pressure from threat actors. However, those pressures are only increasing. Decentralized IT, evolving threats, and zero-trust tools are pushing many IAM tools to their limits.
To maintain their effectiveness, IAM are shifting to operating as an agile, interconnected identity fabric rather than just siloed IAM tools. The demands of today's IT operating environment are forcing IAM to support decentralized IT environments while still providing centralized management and governance for its users.
Interestingly, many of the identity fabric principles they define are currently found in leading SSPM tools. It's important to note that identity fabric isn't composed of a single tool. Rather, a number of different tools, including directories, authentication, and threat detection, come together to form an enforceable IAM perimeter.
The scope of identity fabric includes any human, machine, or application that is granted access to your applications and data. Looking at this through an SSPM lens, your platform should be able to track all access to your SaaS applications and alert you whenever dangerous or suspicious entities or malicious applications access your SaaS stack.
This extends beyond humans and covers the devices they use to access their data. As we look ahead into the near future, it also includes connected devices which may require access to perform their tasks.
Traditional IAM solutions were siloed. Over time, organizations recognized the need to centralize IAM to enable governance and policy management that applied to the entire network.
Today's work environment demands both centralized control and decentralized enforcement so that SaaS applications adhere to the same identity policies that are required to access other corporate assets.
SSPM plays a key role in identity fabric, centralizing identity governance in a single user inventory that is applied to all SaaS apps using data from within each SaaS that goes beyond traditional IAM solutions.
Identity security must be adaptive, ongoing, risk-aware, resilient, and use-case appropriate. SSPM platforms contribute to an organization's overall identity fabric by reviewing compliance against industry standards and ensuring that all identity-centric security checks are configured correctly.
SaaS environments are incredibly dynamic, and require identity tools with the flexibility and agility to keep up with demands. SSPMs are remarkably adept at staying on top of SaaS identity-based changes, supporting new users and new applications.
SSPM plays a critical role in identity-based threat detection. While individual SaaS apps lack sign-in context, SSPM captures user login information from all applications. It provides a tremendous level of context to better understand user behaviors that may threaten SaaS security.
SSPMs can also track user behavior based on user identification, looking for behavioral patterns. When it detects suspicious anomalies in behavior, such as downloading large volumes of data, it also triggers an alert to the SOC team.
Third-party applications are often granted privileges that could compromise data privacy. SSPMs use identity-based tools to recognize these applications and alert security teams when they are engaging in high-risk behavior.
The core strength of an SSPM, like Adaptive Shield's, lies in the visibility it provides to security teams and application owners. Its ability to identify misconfigurations, shadow IT applications, and devices make it an integral part of any SaaS-centric security strategy.
However, its ability to identify and track users makes it an important thread in identity fabric. Its broad scope across multiple applications, centralized location, and ability to flag suspicious behaviors and associate them with an identity cannot be understated. Organizations looking to stitch together a robust, resilient identity fabric would be well served to explore the identity governance benefits inherent in SSPM.
This is an excerpt from an article that was published in The Hacker News on Jan 23, 2023.


Earlier this year, threat actors infiltrated Mailchimp, the popular SaaS email marketing platform. They viewed over 300 Mailchimp customer accounts and exported audience data from 102 of them. The breach was preceded by a successful phishing attempt and led to malicious attacks against Mailchimp's customers' end users.
Three months later, Mailchimp was hit with another attack. Once again, an employee's account was breached following a successful phishing attempt.
While the identity of the Mailchimp accounts that had been compromised wasn't released, it's easy to see how user permission settings could have played a role in the attack. Once threat detectors breached the system, they had the access needed to utilize an internal tool that enabled them to find the data they were looking for. The attack ended when security teams were able to terminate user access, although data which had already been downloaded remained in the threat actor's hands.
Introducing user permissions, through role-based account control (RBAC), could have severely limited the damage caused by the breach. Had the rule of least privilege been applied, it's likely that the breached account would not have afforded access to the internal tools that were used in the attack. Furthermore, reduced access might have completely prevented the attack or limited the number of affected accounts to far fewer than the 100 which were ultimately compromised.
SaaS user permissions allow app owners to limit a user's resources and actions based on the user's role. Called RBAC, it is the permission set that grants read or write access, assigns privileges to high-level users, and determines access levels to company data.
The rule of least privilege is an important security concept that provides the least amount of access needed for users to perform their job functions. In practice, it reduces the attack surface by limiting high-level access to a few privileged individuals. If a low-privilege user account is breached, the threat actor would have less access to sensitive data contained within the application.
App administrators frequently grant full access to team members, particularly when dealing with a small user group. As business users rather than security professionals, they don't always recognize the degree of risk in granting those access permissions. Furthermore, they prefer to give full authorization rather than be asked for specific permissions later on.
Unfortunately, this approach can put sensitive data records at risk. User permissions help define the exposed data in the event of a breach. By protecting data behind a permission set, threat actors that access a user identity are limited to the data available to their victim.
Loose user permissions also make it easier for threat actors to carry out automated attacks. Having multiple users with wide API permissions makes it easier for cybercriminals to breach a SaaS app and either automate ransomware or steal data.
User access reviews are essentially audits that look at users and their access. They show security team members and app owners the degree of access each user has and allows them to adjust permission levels as needed.
This is important, as it helps identify users who may have switched roles or teams within the company but retained an unnecessary level of permissions, or alerts security teams regarding employees whose actions have deviated from normal behaviors to include suspicious behavior. Furthermore, it helps identify former employees who still have access and high-privilege permissions.
Access Reviews should take place at predetermined intervals, ensuring that unnecessary permissions are identified within a set time frame.
User permissions are often a misunderstood security feature. It protects organizations from both external attacks and internal data-sharing errors.
An SSPM solution enables effective user permission management, giving security personnel and app owners the confidence to know the extent of any user permission and see that user's SaaS security hygiene. This real-time view of users is far more effective than User Access Audits, which only present a snapshot view of the users' permissions at a specific moment in time.


Nissan North America is informing customers of a data breach that occurred at a third-party service provider. The security incident was reported to the Office of the Maine Attorney General on January 16, 2023, and it was disclosed that almost 18,000 customers were affected by the breach. According to the notification, Nissan received notice of the data breach from one of its software development vendors on June 2022. The vendor had received customer data from Nissan to use in developing and testing software solutions, which was inadvertently exposed due to a poorly configured cloud-based public repository.
Nissan took immediate action to secure the exposed repository and launched an internal investigation. It was determined that an unauthorized person had likely accessed the data. The exposed data includes full names, dates of birth, and Nissan account numbers, but does not include credit card details or Social Security numbers. Nissan says that to this date, there has been no evidence that any of this information has been misused.
There are two key lessons to learn from the incident. The first is the recurring lesson about the importance of securing repository access (such as GitHub, GitLab, Bitbucket, and more). Just last week we published a blog post covering the breach of Slack’s GitHub repositories. In the case of the 3rd party vendor Nissan used, the issue is even simpler than the previous ones –- organizations must make sure that private repositories used for code development and testing stay private, and only open repositories (such as sharing back to the community) should be public. Security teams must constantly monitor and evaluate which repositories are open, and who should have access to other repositories. Any changes to the visibility of a repository should be alerted, logged, and evaluated by the security team.

Figure 1. Changing repository settings in Github
The second is the use of real customer data for development and testing purposes. This should be discouraged, and instead, use synthetic data mimicking the real data. In my previous blog post, Not All Sandboxes Are for Children: How to Secure Your SaaS Sandbox this was discussed in depth. The main problem is that many times, for no good reason, test environments are not considered as important to secure and keep good configuration hygiene compared to a production environment. But time and time again this is shown to be an Achilles' heel. Many times real data is used in such environments and combined with low security and minimum safeguards, leads to data leakage.
The impact of such a breach is considerable. Not only was sensitive customer data stolen, but Nissan needed to publicly send out notifications, report it to the Office of the Maine Attorney General, and also gave all the affected customers a one-year membership of identity protection services through Experian for free.
You can protect your organization by securing your repository and making sure all repositories that need to be private stay private. Additionally, treat test environments just like production environments from a security standpoint. These are measures that, if done correctly, and with the aid of automatic tools, can keep your organization and customer data secure.


On average, organizations report using 102 business-critical SaaS applications, enabling operations of most departments across an organization, such as IT and Security, Sales, Marketing, R&D, Product Management, HR, Legal, Finance, and Enablement. An attack can come from any app, no matter how robust the app is.
Without visibility and control over a critical mass of an organization's entire SaaS app stack, security teams are flying blind. This is why it's important that all SaaS apps across the organization be managed at scale.
While this breadth of coverage is critical, each app has its own characteristics, UI, and terminology. Mitigating these threats requires a deep understanding of all security controls its configurations.
Security teams need to map out the entire SaaS ecosystem within the organization, including the core SaaS apps and the numerous additional apps that employees connect to without checking or informing the security team.
Each of these apps needs to be governed in Identity & Access, ensuring:
If these checks are not enough for security teams to handle, they also need to check the device posture of all their SaaS users to map risks.
SaaS Security Posture Management (SSPM) is the only solution that can automate misconfiguration management, monitor SaaS-to-SaaS access, harden identity and access governance, and manage SaaS risks stemming from user devices — for all apps and all users.


Over the last year, we’ve seen increasing evidence of an upcoming recession. Interest rate hikes and inflation, energy uncertainty, and the war in Ukraine are all harbingers of rough times ahead. CNBC reported that more than 50,000 employees from Twitter, Meta, Amazon, Salesforce, and other tech companies lost their jobs in November. While no one knows exactly what 2023 will bring to the labor market, organizations need to be prepared for potential downsizing.
Removing user access for employees who no longer require access to company SaaS applications should be fairly straightforward. Most companies will disable users from their active directory and expect those users to be automatically removed from every application they have access to.
That works well when the SaaS app was set up with an SSO. However, many SaaS apps aren’t set up with an SSO. When users are removed from the IDP, they retain their login credentials.
Furthermore, many high-privilege users have extra accounts that are not managed within the IDP. This particularly applies to admins and app owners. Those users retain their high-privilege access, which can put all the data within the application at risk.
When SaaS applications are created, the install team typically creates multiple testing user accounts that are not associated with an IDP. These accounts are granted various levels of access, depending on the functionality or activity being tested. Often, these accounts are given names that are easy to remember, and since the account may be shared by multiple users, passwords are often a simple phrase or number pattern that is easy to share and remember. After setup is completed, these accounts are dormant but can be used to provide access.
Additionally, teams will often share a single user license among multiple employees. Again, these accounts are frequently high-privilege with easy-to-remember passwords, simplifying the team’s ability to get their work done.
These dormant and shared high-privilege accounts represent a significant threat during periods of downsizing. Former employees can use them to easily access corporate SaaS apps and sabotage or steal corporate IP. During periods of downsizing, security should be tightened to include reviewing permissions of these types of accounts, rotating passwords, and limiting shared accounts to situations where it is the only option.
User accounts are also frequently given to external users. As teams collaborate with vendors and partners, it’s more efficient to provide access to the system rather than have employees copy, paste, and email data to their partners. While some accounts are limited through RBACs, often times partner and vendor accounts have full access.
These external user accounts always create a degree of risk for organizations. However, when employees are let go and vendors lose their connection to the company, the risk level increases. Unaffiliated third-party vendors and partners may share data with competitors The only thing standing between company data and the public internet are login credentials. Company and customer data may be stolen, leaked, or shared with competitors.
User inventories provide a complete account of each user in every SaaS system. These were easy to assemble when everything was done on-premises. However, the transition to the cloud and SaaS applications has decentralized user data and limited the view of security personnel.
An effective user inventory would enable security teams and SaaS app owners to find and disable these types of accounts, eliminating the threat they pose following layoffs.
The inventory should be the single source of truth for everything a security team needs to know about a user. It should include login names the user may use on different applications, mulitple login names a high-privilege user might have for a single app, the applications that they can access, and the level of privilege they have within the application. It is vital to disable every access credential once an individual is no longer part of the organization.
However, the user inventory also needs to include test accounts, shared accounts, and external user accounts. Security personnel should be able to see which accounts are not using corporate IDP, the last date the account accessed the system, and access roles that are available to the user account. With that information in hand, security teams and app owners can make an informed decision as to whether these accounts represent a threat and need their access removed or limited.
Downsizing can be traumatic for a company and its employees, but is usually done to protect the long-term interests of the organization. Ensuring that data remains safe throughout this challenging period is not an easy task, but with the right tools in place, security teams and app owners can ensure the integrity and security of their SaaS.


Earlier today, a story broke that GitHub repositories of Slack were breached over the holiday weekend. Slack detected the breach after noticing suspicious activity, and in their investigation found that stolen Slack employee tokens were the source of the breach.
As a result of the attack, private Slack code repositories were downloaded, but no customer data was exposed.
While Slack is in the news today, they are definitely not the first, and will not be the last. Among the numerous breaches thus far, the Dropbox breach consisting of 130 Dropbox GitHub repositories is noteworthy. This was done using credentials that were stolen in a phishing attack, the current method of choice for bad actors. This also was discovered by noticing suspicious activity. GitHub itself has fallen victim to a breach that resulted in stolen repositories using stolen OAuth user tokens issued to two third-party OAuth integrators – Heroku and Travis-CI.
These breaches show how important it is to secure repositories. This is even more true in the modern cloud-based world where repositories are hosted within SaaS platforms for managing Git – such as GitHub, GitLab, Bitbucket, and others. These repositories are the keys to the kingdom. Sometimes repositories include databases of customers, patients, assets, and other sensitive data. This type of breach is a disaster for any company.
Once accessed, the attacker has an intimate understanding of how the product was built and can use that information to compromise the product in follow-up attacks.
To protect against such attacks, organizations should follow these security measures:

As seen in the incidents mentioned above, monitoring is key. Make sure to enable audit logs and consume them to gain visibility to user actions, in addition to having tools, like a SaaS Security Posture Management solution (SSPM), for threat detection.
These are just some of the many methods, tools, and configurations that should be used to secure access to a repository. In addition, employees should be trained to detect phishing and keep their credentials safe and secure.
A breach of a repository in a Git SaaS is not a force majeure. With proper security tools and training the risk can be reduced drastically.


Business leaders may fear an upcoming recession, but they fear falling behind their competitors even more. PwC’s November Pulse Survey found that 35% of executives are planning an acquisition or divestiture within the next 12-18 months. M&A has proven itself to be a key to business resurgence, strategic growth, and capability expansion.
One area that’s often overlooked during M&A due diligence is a target company’s SaaS landscape. These applications, which host tremendous amounts of sensitive company and customer data on the cloud, are often left unsecured through misconfigurations, orphan user accounts, and third-party applications with high permission sets.
While SaaS applications are secured by the app developer, the data within them can be easily exposed. Most large organizations have over 40 million toggles, switches, and checkboxes across their SaaS landscape that have to be set correctly to prevent data breaches, ransomware attacks, and malware.
Connecting an acquisition target’s SaaS stack to an SSPM can be done easily through existing APIs. Once connected, it takes just minutes to see the target’s SaaS hygiene and evaluate whether risk levels for the data within SaaS apps.
Merging two companies together is always high risk. By connecting an SSPM and looking under the SaaS hood, security analysts can offer their perspective on the merger and the level of risk they are taking on.
Getting ready for M&A? See how Adaptive Shield can protect you from SaaS surprises. Schedule a demo today.


With 2022 coming to a close, there is no better time to buckle down and prepare to face the security challenges in the year to come. This past year has seen its fair share of breaches, attacks, and leaks, forcing organizations to scramble to protect their SaaS stacks. March alone saw three different breaches from Microsoft, Hubspot, and Okta.
With SaaS sprawl ever growing and becoming more complex, organizations can look to four areas within their SaaS environment to harden and secure.
Enterprises can have over 40 million knobs, check boxes, and toggles in their employees’ SaaS apps. The security team is responsible to secure each of these settings, user roles and permissions to ensure they comply with industry and company policy.
Not only because of their obvious risk or misalignment with security policies, misconfigurations are overwhelmingly challenging to secure manually. These configurations can change with each update, and their complexity is compounded by the many compliance industry standards. Adding to that challenge, SaaS app owners tend to sit in business departments outside the security team’s scope and are not trained or focused on the app’s security.
Security teams should onboard a SaaS Security Posture Management (SSPM) solution, like Adaptive Shield, that provides full visibility and control across a critical mass of SaaS apps in the SaaS stack. The solution must identify both global app settings and platform-specific configurations within each app. Security teams should be able to use the solution to gain context into security alerts and gain answers to questions like: Which users are subject to a certain misconfiguration? Are they admins? Is their MFA enabled? By having these answers at their fingertips, security teams can enforce company and industry policies to remediate potential risks from any misconfiguration.
Another growing security challenge derives from the increasing volume of apps connected to the company’s SaaS environment. On average, thousands of apps are connected without the approval or knowledge of the security team. Employees connect these apps, often to boost productivity, enable remote work and to better build and scale company's work processes.
However, when connecting apps to their workspaces, employees are prompted to grant permissions for the app to access. These permissions include the ability to read, create, update, and delete corporate or personal data, not to mention that the app itself could be malicious. By clicking "accept," the permissions they grant can enable threat actors to gain access to valuable company data. Users are often unaware of the significance of the permissions they’ve granted to these 3rd-party apps.
Falling in the Shadow IT domain, security teams must be able to discover 3rd party apps and identify which pose a risk. From access scopes requested by these apps, to authorized users and cross referencing, the security team should be able to measure the level of access to sensitive data across the organization’s stack. An SSPM solution like Adaptive Shield, can arm the security team with this type of discovery and control in addition to providing advanced reporting capabilities for effective and accurate risk assessments to drive actionable measures.
Security teams must deal with threats from users accessing their SaaS applications from personal, unsecured devices. Accessing a SaaS app via an unmanaged device poses a high level of risk for an organization, especially when the device owner is a highly privileged user. Personal devices are susceptible to data theft and can inadvertently pass on malware into the organization’s environment. Lost or stolen devices can also provide a gateway for criminals to access the network.
Security teams need a solution that enables them to manage SaaS risks originating from compromised devices. An SSPM solution like Adaptive Shield can identify privileged users such as admins and executives, calculate user-risk levels, and recognize which endpoint devices need to be more secured.

Every SaaS app user is a potential gateway for a threat actor, as seen in the most recent Uber MFA Fatigue attack. Processes to ensure proper users’ access control and authentication settings are imperative, in addition to validation of role-based access management (as opposed to individual-based access) and establishing an understanding of access governance. Identity and access governance helps ensure that security teams have full visibility and control of what is happening across all domains.
Security teams need to monitor all identities to ensure that user activity meets their organization’s security guidelines. IAM Governance enables the security team to act upon arising issues by providing constant monitoring of the company’s SaaS Security posture as well as its implementation of access control.
Gartner called SaaS Security Posture Management (SSPM) in the “4 Must-Have Technologies That Made the Gartner Hype Cycle for Cloud Security, 2021” for solutions that continuously assess security risk and manage the SaaS applications’ security posture. With an SSPM platform organizations can harden their SaaS security to identify and remediate issues faster and prevent future attacks. Security teams can introduce best practices for SaaS security that extend beyond Misconfiguration Management to cover SaaS-to-SaaS Access, Device-to-SaaS User Risk levels, and Identity & Access Management Governance.


This past month, Adaptive Shield partnered with Panorays (a SaaS-based third-party security risk management platform) to produce a joint webinar Pinpoint Your SaaS App Risks: From Evaluation to Usage. These two security experts, Maor Bin, CEO of Adaptive Shield, and Demi Ben Ari, CTO OF Panorays, discussed the evolution of third-party apps, the tools used to secure them, and the best practices and processes for using these tools. Here are some of the highlights and key takeaways.
Click here to watch the full recorded webinar.
Maor Bin, CEO & Co-Founder at Adaptive Shield, brings over 16 years of experience in the cyber security industry. Before founding Adaptive Shield, Maor served as a cybersecurity intelligence officer in the IDF and later led SaaS Threat Detection Research at Proofpoint.
Demi Ben Ari, CTO & Co-Founder at Panorays, is a software engineer, entrepreneur, and international tech speaker. He has over 10 years of experience in building systems both from the field of near real-time applications and big data distributed systems.
Demi Ben Ari: “The SaaS stack that you are using today is really your new attack surface”
As illustrated in Figure 1, the supply chain has become more complicated and complex due to many changes in the industry.

It's clear that 3rd party apps like Salesforce, Slack, and Monday are critical to businesses and have become an inseparable part of employee’s day to day. It’s also clear that proper risk assessment and security for these apps is vital.
Demi takes a moment to discuss how this risk is understood in today’s market:
“Think that today when we were speaking about third-party breaches that people speak about and echo in the media… it isn't really an attack, right? There is a vulnerability exposed to the world and a lot of hackers and a lot of malicious actors actually try to exploit them with the spray and pray attack. So most of it is not even really targeted.”
This signifies two things. The first being that most breaches are happening simply as a result of apps being poorly secured. The second is understanding that attackers are continuing to explore new means to access and exploit organization's data and this can be true for both targeted and non-targeted organizations, meaning hardening security settings for every app cannot be overstated.
For example, Salesforce is crucial to today's business but in order to operate, the app houses sensitive information that if leaked could potentially ruin a business. The 2022 SaaS Security Survey Report shows that while the investment in SaaS applications is growing, the investment in security tools and staff is lagging behind, as seen in Figure 2.

Organizations need a new tool set to secure the onboarding of new apps and other developments in their SaaS landscape. However, the process needed for organizations to secure their 3rd party apps goes far beyond just implementation; organizations need to evolve their security protocols to include a continuous and repetitive means of evaluating and hardening app security.
Demi: “We spoke about identification and how to know all the vulnerabilities, but it’s a process, and the process does not finish at ‘I'm installing something and this magic box will solve all of my problems’...the continuous monitoring aspect is really crucial.”
Maor Bin: “We need to understand first of all what we need to do to create this [continuous assessment] process internally to work in a secure fashion.” Maor outlines the process of initial and continuous SaaS security assessment into three levels – discovering and assessing risks, obtaining and maintaining hygiene, and managing threats.

Figure 3 outlines the entire process that security teams should be conducting and repeating in order to keep their SaaS stack secure. While the details of this process should be customized to each organization's size, needs, and resources, the overall methodology is the key to create a continuously secure SaaS environment.
The first step in securing one’s SaaS ecosystem is having comprehensive and robust discovery processes to learn of the potential apps’ digital footprint. Security teams need to understand where they have visibility and, more importantly, where they don't. Addressing blind spots should be a top priority to ensure risk can be discovered and reduced.
Then, throughout the onboarding process, from users, their permissions, and their devices, security teams can be hyper aware of all the moving parts that should be checked. Organizations also need to be able to identify and discover SaaS-to-SaaS applications, including ones that are connected without the security team’s knowledge. Today's workforce depends on apps that easily connect with the user's workspace.These 3rd-party applications, which can number in the thousands for larger organizations, all must be monitored and overseen by the security team.
Once the initial assessment is complete, security teams must maintain (or increase) the level of hygiene. Security teams should focus on closing gaps that exist in their posture to remediate faster and reduce risk. This requires that security teams evaluate configurations, compliance requirements, and other changes in their SaaS estate not just once, but repeatedly.
The final step is threat management. Security teams must identify misconfigurations or vulnerabilities in a device or user that is causing risk and quickly remediate the issue.
Gartner recently named a new security discipline called Identity Threat Detection and Response (ITDR). ITDR incorporates detection mechanisms that investigate suspicious posture changes and activities, and responds to attacks to restore the integrity of the identity infrastructure.
ITDR incorporates strong SaaS Security IAM Governance methodologies and best practices that are found in SaaS Security Posture Management solutions (SSPM). This enables security teams to gain continuous and consolidated visibility of user accounts, permissions, and privileged activities across the SaaS stack, such as:
Regardless of how secure an organization's SaaS posture is, new threats continue to emerge and security teams need the right tools to combat them.
Maor Bin: “We need to understand the privacy policy for these 3rd party applications. We have a process for it when it comes to endpoint, which we call application control, and everybody understands that they need to do it for their endpoints…but when it comes to 3rd party apps, things are falling between the cracks.”
Demi Ben Ari: “It always starts from visibility and onboarding. Eventually when you end up with continuous monitoring, it’s also continuously onboarding all of these third-party engagements, and this can be on multiple layers.”
Salesforce can be used as an example of these layers and is considered the first layer. Next, a user may install 5 plug-in applications from the app exchange – apps that may not even be verified by a security expert – creating the second layer, also called SaaS-to-SaaS access or 3rd party app access. This second layer alone already introduces dozens of granted permissions into your environment, multiplying the attack surface. It doesn't stop there – an app connected in the second layer may have its own connected plug-ins which in turn create the third layer and so on and so forth. Security teams must have an assessment process for onboarding the entire entity from the core apps to all its plugins.
Maor iterates: the first step is to identify and discover all these applications and then understand what other apps are connected. History has taught us that many breaches happen as a result of attackers gaining access to small supported apps as opposed to the core SaaS workspace.
Maor: “The idea, when we talk about security, is not just protecting one application or a handful of applications, it’s protecting your entire stack”.
The high volumes of apps, users, and settings makes maintaining a secure SaaS stack a near impossible challenge. Security teams need all-around visibility into different aspects of their SaaS stack while simultaneously implementing and maintaining continuous security assessments. SaaS Security Posture Management (SSPM) solutions enable security teams to gain complete control over their SaaS stack and significantly aid in implementing the continuous process of assessment.
SSPM combat the challenges existing in the SaaS landscape through:


Forrester, a research and advisory company, offers organization’s a variety of services including research and consulting. Their reports help professionals understand their customer’s behavior, concerns, and interests to help organizations make more informed decisions. Their Trend Report ‘Embrace A Paradigm Shift In SaaS Protection: SaaS Security Posture Management’ looks at the increased use of SaaS apps and the value of an SSPM solution. This blog will summarize key takeaways from the report.
Click here to read the full report.
“Organizations’ cloud-first or on-premises augmentation strategies caused an explosive, decentralized, and uncontrolled growth of SaaS application use. Consequently, the increase in the number of cloud assets has also increased overall IT risks.”
The ease with which SaaS apps can be adopted is remarkable, but it has become a double-edged sword. The cloud has enabled organizations to store and manage near endless data and scale their operations, but it has opened the doors for relentless attackers and new attack vectors. Organizations have dozens to over a hundred different SaaS apps critical to maintaining day-to-day operations, each with nuanced access patterns from sharing, uploading, downloading, sorting, searching, and filtering activities.
Access patterns and activities, when looked at individually, may appear harmless. However when looked at as part of a bigger picture, security teams can often quickly identify risk by spotting unusual behavior, suspicious geolocations movements, and uncommon access requests. Organizations not only gain visibility into different domains and activities but also monitor data movement to and from SaaS apps to help detect threats.
The skills shortage and gap between application owners and security teams only adds to the challenge. The report found that even the largest organizations interviewed stated that they lack the resources needed to fully understand the connectivity between SaaS apps and their security implications. Organizations are in dire need of a security solution, such as an SSPM, which is able to provide visibility and understanding into these apps.
In turn, an effective SSPM needs to be able to integrate with all their apps to support the organization's security policies and goals. Contextualized visibility into each app helps security teams prioritize configuration weaknesses and increase time and efficiency to remediation across multiple attack surfaces.
“SSPM solutions differ in breadth and depth of SaaS app coverage”
Simply put, not all SSPM solutions are created equal. SSPMs can vary in the amount of apps they support, the thoroughness of their security checks, and the range of their capabilities. Forrester describes needed functionalities within the organization’s chosen SSPM solution:

At Adaptive Shield, we like to boil it down to four main use cases: misconfiguration management, SaaS-to-SaaS access discovery, device-to-SaaS user management, and identity and access management governance. An SSPM will present detailed and dedicated security checks within each of these use cases.
The 2023 SaaS Security Posture Management Checklist covers all the critical features and capabilities to look out for when evaluating a solution.
“SSPM solutions can make recommendations on how to trim business users’ privileges without impeding their user experience (i.e., they continue to have access to data and the SaaS application functionality that they need to do their jobs without access to data they do not need).”
An SSPM’s user inventory is one of many critical features. A user inventory helps security teams gain visibility of users, their privileges, and user-specific failed security checks. By gaining in-depth knowledge of user permissions and behavior, security teams can identify inactive users, overprivileged admins, and other user-specific threats. SSPMs can help trim unnecessary user privileges without limiting access to the data needed to complete their work.
The report outlines the following identity and access management related SaaS settings that SSPM solutions can enforce.
It's not surprising that SaaS apps do not properly guard organization’s data and are susceptible to data breaches. SSPM solutions provide relief to security experts by offering data protection features such as:


Every SaaS app user and login is a potential threat; whether it’s bad actors or potential disgruntled former associates, identity management and access control is crucial to prevent unwanted or mistaken entrances to the organization’s data and systems.
Since enterprises have thousands to tens of thousands of users, and hundreds to thousands of different apps, ensuring each entrance point and user role is secure is no easy feat. Security teams need to monitor all identities to ensure that user activity meets their organization’s security guidelines.
Identity and Access Management (IAM) solutions administer user identities and control access to enterprise resources and applications. As identities became the new perimeter, making sure this area is governed by the security team is vital.
Gartner has recently named a new security discipline called Identity Threat Detection and Response (ITDR) that incorporates detection mechanisms that investigate suspicious posture changes and activities, and responds to attacks to restore the integrity of the identity infrastructure.
ITDR incorporates strong SaaS Security IAM Governance methodologies and best practices that are found in SaaS Security Posture Management solutions (SSPM), enabling security teams to gain continuous and consolidated visibility of user accounts, permissions, and privileged activities across the SaaS stack, such as:
Whether you are a CISO, IT or on the Governance, Risk and Compliance (GRC) team, this article will cover the role of Identity and Access Management Governance as part of the organization’s SaaS security program.
IAM Governance enables the security team to act upon arising issues by providing constant monitoring of the company’s SaaS Security posture as well as its implementation of access control.
There are a few critical prevention domains where an SSPM can manage Identity and Access Management Governance: 1) Misconfigurations 2) Vulnerabilities 3) Exposure.
IAM controls need to be properly configured on a continuous basis. The IAM configurations should be monitored for any suspicious changes and ensure that the appropriate steps are taken to investigate and remediate when relevant.
For example, an organization can enable MFA across the organization and not require it. This gap in policy enforcement can leave the organization at risk — and an SSPM can alert the security team about this gap.
The SSPM solution can utilize patching or compensating controls to address commonly exploited vulnerabilities in the identity infrastructure such as the SaaS user’s device. For example, a privileged CRM user can present a high risk to the company if their device is vulnerable. To remediate potential threats that stem from devices, security teams need to be able to correlate SaaS app users, roles, and permissions with their associated devices' hygiene. This end-to-end tactic enables a holistic zero-trust approach to SaaS security.
Another critical vulnerability stems from authentication protocols that the password access is limited to a single-factor authentication method, such as with legacy protocols like IMAP, POP, SMTP and Messaging API (MAPI). An SSPM can identify where these protocols are in place across the organization’s SaaS stack.
The SSPM helps to reduce the attack surface by identifying and mitigating places of exposure. For example, removing unnecessary or excessive privileges or allowing an external admin for a business-critical app. (See figure 1.)

Additionally, 3rd party app access, also known as SaaS-to-SaaS access can leave an organization exposed. Users connect one app to another app to either provide enhanced features or user’s information (e.g contacts, files, calendar, etc). This connection boosts workflow efficiency and as a result, employees’ workspaces are connected to multitudes of different apps. However, the security team is most often in the dark about which apps have been connected to their organization’s ecosystem, unable to monitor or mitigate any threats.
IAM is a method for hardening access control, whereas IAM Governance in SSPMs offer continuous monitoring of these features to ensure security teams have full visibility and control of what's happening in the domain.


When creating a Sandbox, the mindset tends to be that the Sandbox is considered a place to play around, test things, and there will be no effect on the production or operational system. Therefore, people don’t actively think they need to worry about its security. This mindset is not only wrong, but extremely dangerous.
When it comes to software developers, their version of sandbox is similar to a child’s playground — a place to build and test without breaking any flows in production. Meanwhile, in the world of cybersecurity, the term ‘sandbox’ is used to describe a virtual environment or machine used to run suspicious code and other elements.
Many organizations use a Sandbox for their SaaS apps — to test changes without disrupting the production SaaS app or even to connect new apps (much like a software developer’s Sandbox). This common practice often leads to a false sense of security and in turn a lack of thought for its security implications. This article will walk you through what is a SaaS sandbox, why it is vulnerable, and how to secure it.
A cybersecurity sandbox allows separation of the protected assets from the unknown code, while still allowing the programmer and app owner to see what happens once the code is executed. The same security concepts are used when creating a SaaS Sandbox — it duplicates the main instance of SaaS including its data. This allows playing around with the SaaS app, without influencing or damaging the operational SaaS — in production.
Developers can use the sandbox to test the API, install add-ons, connect other applications, and more — without worrying about it affecting the actual users of the organization. Admins can change configurations, test SaaS features, change roles, and more. This allows the user to better understand how the changes to the SaaS will go before implementing it on an operational, and critical, SaaS instance. This also allows time to create guidelines, train staff, build workflows, and more.
All in all, using a Sandbox is a great concept for all software and SaaS usage; but like all great things in the world of SaaS, the problem is that there is a major security risk lurking within.
A large private hospital inadvertently revealed data of 50,000 patients when they built a demo site (i.e a Sandbox) to test a new appointment-setting system. They used the real database of the medical center, leaving patients' data exposed.
Often a Sandbox is created using real data, occasionally even a complete clone of the production environment, with its customizations. Other times, the Sandbox is directly connected to a production database. If an attacker manages to penetrate the Sandbox because of lax security, they will gain access to troves of information. (This leakage of information can be problematic especially if you are an EU company or processing EU data because of GDPR. If you are processing medical information in the USA or for a USA company, you can be in violation of HIPPA.)
Even organizations that use synthetic data, which is recommended for all companies, can still be at risk for an attack. An attacker can use the Sandbox for reconnaissance to gain insight on how an organization sets up its security features and its possible weak spots. Since the Sandbox reflects to some degree how the operational system is configured, an attacker can use this knowledge to penetrate the production system.
The solution for the problem of the non-secure Sandbox is rather simple – secure the Sandbox step-by-step as if it was a production system.
Step 1. Manage and control access to a Sandbox and limit users’ access to the Sandbox. For example, not every user that has access to production should also have access to the Sandbox. Controlling which users can create and access a Sandbox is the first step for keeping your SaaS environment secure.
Step 2. Implement the same security settings that are configured within the operational system to the Sandbox version; from requiring MFA to implementing SSO and IDP. Many SaaS apps have additional security features that are tailor-made for that specific SaaS app and should be mirrored in the Sandbox. For example, Salesforce has unique security features such as: Content Sniffing Protection, Default Data Sensitivity Levels, Authentication Through Custom Domain, and so on.
Step 3. Remove production data and replace it with synthetic (i.e. made up) data. Sandboxes are typically used for testing changes in configurations, processes, flows (such as APEX), and more. They don’t require real data for testing changes - any data with the same format can be sufficient. Therefore, avoid copying the production data and use Data Mask instead.
Step 4. Keep your Sandbox inline with security improvements done in the production environment. Often a Sandbox is neither refreshed or synced on a day-to-day basis, leaving it vulnerable to threats that were minimized in the production. To reduce risk and to make sure your Sandbox is serving its purpose, a Sandbox should be synced every day.
Security teams can also implement and utilize SSPM (SaaS Security Posture Management) solutions, to automate their SaaS security processes and address the challenges detailed above, to monitor and prevent threats from infiltrating the SaaS sandbox. An SSPM enables security teams to identify, analyze, and prioritize misconfigurations in the Sandbox and across the whole SaaS app stack, as well as provide visibility to 3rd party apps with access to the core apps, Device-to-SaaS User posture management and more.
This is an excerpt from an article that was published in The Hacker News on Oct 20, 2022.


“SaaS applications have native security controls as part of their offering which makes them security products themselves — that security teams now need to manage”.
Asserted by Adaptive Shield’s CEO, Maor Bin partnered with Okta’s VP of Strategy, Stephen Lee in the Security Boulevard Webinar: SaaS Security Trends, Challenges, and Solutions for 2022. This joint webinar discusses the struggles that security professionals face today and how organizations can address the risks stemming from key attack areas. This blog highlights some of the dialogue between these two industry thought leaders.
(For the whole webinar, click here.)
Organizations use dozens to hundreds of apps throughout different departments and with each app comes a sea of configurations to set and secure, not once but constantly. Over time, apps have updates and new security settings or new users with different permissions levels to add or adjust. Security teams need to invest many resources to continuously be on the lookout for misconfigurations and quickly remediate them.
The challenge of managing configurations goes beyond the sheer volume to the intricacies of understanding each app.
Stephen Lee: “If you look at the SaaS applications out there and you go to that security tab or that user management tab – they all look different. Sometimes, you almost have to be that specific app expert to be able to know what to do.”
Maor Bin: “That's one of the reasons for the challenge of securing your SaaS estate – you have so many applications and each one is different from the other one.”
Different apps may have the same or similar security settings but the names of these settings and how to access them can differ vastly. Security teams who are trying to manually secure each configuration have to be an expert on every single app to secure them, which is a far from realistic request.
Stephen Lee: “One beautiful thing about SaaS applications is that it's very easy to integrate with them. [However] once you've shared the power with the downstream applications or clients that are talking to it and then it all becomes ‘who is the weakest link?’ and that becomes a potential security hole.”
SaaS-to-SaaS access has become a balance between the convenience of having end users be able to easily integrate and use these applications (that boost productivity and remote work) and the ability for security teams to have the necessary visibility to secure and monitor these apps.
The risks from SaaS-to-SaaS app access stem from the connection process; the app requests permissions in the user’s workspace and oftentimes, the app is asking for high-risk permissions (the app could also be malicious itself, unbeknownst to the user). Typically defined as allowing an app to gain access to user data (e.g. read/write permissions and more), high-risk permissions, and any unknown app, should only be granted access after the secure team has been able to fully vet it and have a system in place to monitor it.
The 2022 SaaS Security Survey Report demonstrates just how prevalent of a concern 3rd party app access is for today’s CISOs and security professionals.

Maor Bin: “The challenge is not only misconfigurations and native security controls within SaaS applications but what actually happens after you login, what happens within your device…and get a better understanding of what's going on with your users. So for example: if you see you have a Office 365 admin and this user has 3 critical vulnerabilities on their device, it’s obviously a huge problem because this isn't just a regular SaaS user accessing the SaaS applications but it's an admin with privileged roles.”
When individuals with advanced privilege levels use devices that are unsecured, they expand the attack surface with what amounts to an open gateway.
With today's modern workforce working from home, cafes, or even abroad, security teams need to secure all the devices the employees are using. Personal devices are vulnerable to data theft and can inadvertently pass on malware that was downloaded for personal use into the organization’s environment. Lost or stolen devices can also provide a gateway for criminals to access the network.
Stephen Lee: “You can hire the best IT folks and you can hire the best app admins, the best Security Experts… but things do happen. I think it’s not about how to prevent it from happening; I think it’s a lot about mitigation, mitigating the risk…This is relevant to not just a small company with 50 people all the way up to large Enterprises.”
“There's a lot of stuff happening outside of what Okta is able to manage…For us, I’m excited to see how Adaptive Shield can help solve these problems.”
In order to cover the many attack surfaces of SaaS apps, an SSPM solution can enable security teams to gain control of the core misconfiguration management use case; and go beyond to the added layers of SaaS-to-SaaS access, device-to-SaaS user risk, and identity and access management governance.
If you’d like to learn more, contact one of our experts here.


The ease with which SaaS apps can be deployed and adopted today is remarkable, but it has become a double-edged sword. On the one hand, apps are quickly onboarded, employees can work from anywhere, and there is little need for operational management. On the other hand, there are pain points that stem from the explosion of SaaS app usage, explained by the "3 V" s:
Named by Gartner as a MUST HAVE solution in the "4 Must-Have Technologies That Made the Gartner Hype Cycle for Cloud Security, 2021," SaaS Security Posture Management (SSPM) solutions come to answer these pains to provide full visibility and gain control of the company's SaaS security posture.
As one might expect, not all SSPM solutions are created equal. The Misconfiguration Management use case sits at the core of SSPM. However, there are more advanced use cases that tackle the emerging and growing challenges existing in the SaaS landscape.
When comparing SSPM options, here are some key features and capabilities to look out for (excerpted from the complete guide):
Run comprehensive security checks to get a clear look into your SaaS estate, at all the integrations, and all the domains of risk.
First and foremost for an SSPM's core solution, is the SSPM's ability to integrate with all your SaaS apps.
The other vital component to a core SSPM solution is the expanse and depth of the security checks. Each domain has its own facets for the security team to track and monitor.
Combat threats with continuous oversight and fast remediation of any misconfiguration
Remediating issues in business environments is a complicated and delicate task. The core SSPM solution should provide deep context about each and every configuration and enable you to easily monitor and set up alerts. This way vulnerabilities are quickly closed before they are exploited by cyberattacks.
SSPM vendors like Adaptive Shield provide you with these tools, which allow your security team to communicate effectively, shut down vulnerabilities, and protect your system.
Your SSPM solution should be easy to deploy and allow your security team to easily add and monitor new SaaS applications. Top security solutions should integrate easily with your applications and your existing cybersecurity infrastructure, to create a comprehensive defense against cyber threats.
In an effort to improve productivity, employees often extend the functionality of their primary SaaS applications by connecting them to a secondary SaaS app, or otherwise known as 3rd-party app access. These rights include the ability to read, create, update, and delete corporate or personal data. This access is granted in seconds, usually far outside the view of the IT and security teams, and significantly increases an organization's attack surface.
However, users rarely realize they've handed over significant permission rights to the new 3rd-party application. These 3rd-party applications, which can number in the thousands for larger organizations, all must be monitored and overseen by the security team.
To prevent secondary apps from providing an unauthorized gateway into your system, your SSPM solution should be equipped with the following capabilities:
Even before employees were routinely working from home, user devices posed a risk to corporate networks. Security teams had no visibility into the owners of different devices and couldn't ensure that the devices were secure. When individuals with advanced privilege levels use devices that are unsecured, they expand the attack surface with what amounts to an open gateway.
Track and monitor all device-to-SaaS user risk to eliminate surprise vulnerabilities
Associating Devices with Users
Over time, the number of users with access to different parts of an enterprise's system increases. While some users may move on, oftentimes they remain in the system and retain the same privileges that they had. Threat actors or disgruntled associates of the company can use these credentials to gain access to unauthorized areas of the system. Security teams need a tool to identify and disconnect these users from multiple environments and applications within the company. They also need to monitor every SaaS login and ensure that user activity meets security guidelines.
Identify all users with access to any system or application within the environment:
User Authorizations
Identifying Users
The Right SSPM solution PREVENTS your next attack.
SSPM is similar to brushing one's teeth: it's a foundational requirement needed to create a preventative state of protection. The right SSPM provides organizations continuous, automated surveillance of all SaaS apps, alongside a built-in knowledge base to ensure the highest SaaS security hygiene.
Get the complete guide along with the printable checklist here.


The International Organization for Standardization (ISO) sets standards across various industries. As an internationally recognized standards organization, its two information technology security standards - ISO 27000:2018 and ISO 27001:2013 - can be used to help build out a strong security posture.
SaaS security is critical to ISO compliance in the modern business world. However, with all the non-stop developments in the organization's SaaS stack, from updating and modifying configurations to discovering SaaS-to-SaaS access and securing devices etc., it can become overly burdensome for a security team to handle. SSPM solutions come to answer this pain by providing proactive, deep, continuous and automated monitoring & management capabilities. (SSPM solutions can also offer security checks per compliance framework so the security team can easily see where their posture is compliant or needs remediation.)
This blog will take a deep dive into understanding the ISO compliance standards, with its two recent yet different versions, and how SSPM can help security teams ensure ISO compliance.
Simply put: ISO 27000:2018 gives you goals to accomplish while ISO 27001:2013 outlines the steps you have to take to achieve those outcomes.
ISO 27000 sets out the following fundamental principles of your security program:
ISO 27001 focuses on best practices and establishing an Information Security Management System (ISMS) that consists of policies and procedures. It includes five processes for achieving these security fundamentals:
A lot of this sounds fairly vague, and it is. ISO takes a risk-based approach to establishing an ISMS, but that doesn’t mean you’re on your own.
The first three clauses give you the basic terminology and scoping. It’s clauses four through ten that start to get into some more detail. These are:
Again, this is fairly high-level, even though ISO gives detailed definitions within the clauses. The real work of getting ISO compliant is found in Annex A which lists 114 controls aligned to ten clauses.
The problem with understanding the importance of SaaS security within the ISO context is that ISO never specifically mentions SaaS apps. Since it acts as a risk-based framework, you need to start by identifying the risks that SaaS apps pose, then put the controls around them.
Going into all the controls listed in ISO 27001 would be too long for this post. However, you can get a general sense of how SaaS security - and SaaS Security Posture Management (SSPM) - fits into your ISO compliance plans with a few examples.
Under Access Control, you need to ensure that all users are assigned the appropriate access needed to complete their job functions.
Ensuring SaaS security under this requirement can be challenging because you need to make sure that you meet the following sub-requirements:
Permission drifts occur when a user has certain permissions as part of a group membership, but then gets assigned a specific permission that is more privileged than what the group has. Over time many users get extra permissions. This undermines the idea of provisioning using groups.
SSPM gives you a way to govern users’ cloud access by:
Operations security is the process of ensuring correct and secure operations for all information processing facilities. In cloud environments, managing operations security becomes more difficult because you often lack visibility.
Ensuring SaaS security under this requirement can be challenging because you need to make sure that you meet the following sub-requirements:
OAuth is an extremely common action that users take, but implementation mistakes can lead to attacks. You need to make sure that you have the appropriate documented operating procedures for onboarding new applications that use OAuth. Further, cybercriminals can use misconfigurations, like the sending OAuth application phishing emails, as part of their ransomware attacks.
SSPM gives you the ability to run continuous security checks for all SaaS apps in use, in addition to the SaaS-to-SaaS access, so that you can:
This requirement focuses on avoiding legal, statutory, regulatory, or contractual obligations.
Ensuring SaaS security under this requirement can be challenging because you need to make sure that you meet the following sub-requirements:
Default configurations can lead to PII leaks as seen in the 2021 Power Apps portal issue that Microsoft fixed. Knowing what default configurations create a compliance violation and monitoring to ensure that you fix issues is key to compliance.
SSPM can help you get compliant by:


Imagine this: a company-wide lockout to the company CRM, like Salesforce, because the organization's external admin attempts to disable MFA for themselves. They don't think to consult with the security team and don't consider the security implications, only the ease which they need for their team to use their login.
This CRM, however, defines MFA as a top-tier security setting; for example, Salesforce has a "High Assurance Login Value" configuration and immediately locks out all users as a safety precaution. The entire organization hits a standstill and is frustrated and confused.
Deeply concerning, this is not a one-off event, admins for business-critical SaaS apps often sit outside the security department and have profound control. Untrained and not focused on security measures, these admins are working towards their departmental KPIs. For instance, Hubspot is usually owned by the marketing department, likewise, Salesforce is often owned by the business department, etc. Business departments own these apps because it's what allows them to do their job efficiently. However, the paradox lies in the fact that it's the security team's responsibility to secure the organization's SaaS app stack and they cannot effectively execute this task without full control of the SaaS app.
The 2022 SaaS Security Survey Report, conducted by CSA and Adaptive Shield, delves into the reality of this paradox, presenting data from CISOs and security professionals today. This article will explore important data points from the respondents and discuss what the solution for security teams could be.
Across a typical organization, a wide array of SaaS apps are used (see figure 1), from cloud data platforms, file sharing and collaboration apps to CRM, project and work management, marketing automation, and a whole lot more. The need for each and every SaaS app fills a certain niche role required by the organization. Without the use of all these SaaS apps, a business could find itself lagging or taking more time to achieve its KPIs.

The 2022 SaaS Security Survey Report reports that 40% of these apps are managed and owned by non-security teams, such as sales, marketing, legal, etc. (see in figure 2). While the security and IT teams are reported to be the main destination for SaaS app management, it's the 40% of business departments also taking part and having full access that complicates the threat landscape.
Security teams can't take away this ownership as the business applications' owners need to maintain a high level of access to their relevant SaaS apps for optimal use. Yet, without in-depth knowledge of security or the vested interest (a security KPI that reflects on their work product), it's not reasonable for the security team to expect that the business owner will ensure a high level of security in their SaaS.

When asked the main reason for misconfiguration-led security incidents (figure 3), respondents of the survey report cited these as their top four: (1) There are too many departments with access to security settings; (2) Lack of visibility to security settings when they are changed (3) Lack of SaaS security knowledge; (4) Misappropriated user permissions. All of these reasons, either overtly or implied, can be attributed to the SaaS App Ownership Paradox.

The leading cause of security incidents caused by misconfigurations is having too many departments with access to security settings. This goes hand in hand with the next cause – lack of visibility when security changes are changed. A business department may make changes to an app setting to optimize its ease of use without consulting with or notifying the security department.
In addition, misappropriated user permissions can easily stem from a business department owner at the helm who is not paying careful attention to the app's security. Often users are granted privileged permissions that they don't even need.
With this shared responsibility model, the only efficient way to bridge this communication gap is through a SaaS Security Posture Management platform (SSPM). With an SSPM solution, owned and managed by the organization's security team, the security team can gain complete visibility of all the company's SaaS apps and their security settings, including user roles and permissions.
Organizations can take it one step further and have the app owners join the SSPM platform so they can actively control and oversee all configurations in their owned apps. By using a scoped admin capability (figure 4) the security team can grant the app owners access to the apps they own and can remediate security issues, with their supervision and direction.

There's no way to eliminate business departments' access to SaaS app security settings, and while users across the organization should be educated on basic SaaS security in order to reduce the risk that may occur from business departments, it doesn't always happen or it's just not enough. Organizations need to implement a solution that helps avoid these situations by enabling visibility and control for the security team, including alerting on configuration drifts and audit logs that provide insight into actions within the SaaS apps and scoped admins.


TEL AVIV, Israel - Sept 13 2022 - Adaptive Shield, the leading SaaS Security Posture Management (SSPM) company, today announced a partnership with Tenable, the Cyber Exposure Management company, to provide a consolidated posture management solution that correlates the risk of SaaS users and their endpoints.
While SaaS providers build in security features, it is the company’s responsibility to continuously cover all attack surfaces: from misconfigurations to identifying SaaS apps connected to the core SaaS app, while also detecting and remediating SaaS threats stemming from user devices with poor hygiene.
By correlating Tenable’s rich vulnerability insights within Adaptive Shield’s SaaS security posture technology, security teams will gain context and visibility to easily see and manage the risks that come from SaaS users and their associated devices. This partnership enables organizations to enrich their understanding of device and user posture and their influence on one another.
“When mitigating the SaaS attack surface, vulnerability management is an integral part of SaaS security hygiene, especially when it comes to privileged users and their device posture,” said Maor Bin, Co-Founder and CEO of Adaptive Shield. “By partnering with Tenable, we are proud to advance a new standard for organizations to protect their SaaS stack.”
“Understanding exposure and risk across SaaS deployments has never been more important than in today’s cloud-first world,” said Ray Komar, vice president of technical alliances, Tenable. “We’re excited to bring Adaptive Shield into our technology ecosystem, providing customers with increased visibility and context across their attack surface.”
For the full solution brief, take a look at our resources.
The original PR was released through Business Wire on Sept 13, 2022.


Another day, another attack method.
GIFShell attack technique enables bad actors to exploit several Microsoft Teams features to act as a C&C for malware, and exfiltrate data using GIFs without being detected by EDR and other network monitoring tools. The technique assumes an already-compromised target.
Discovered by Bobby Rauch, the main component of this attack allows an attacker to create a reverse shell that delivers malicious commands via base64 encoded GIFs in Teams, and exfiltrates the output through GIFs retrieved by Microsoft's own infrastructure.
How does it work?
As reported by Lawrence Abrams in BleepingComputer, Microsoft agrees that this attack method is a problem, however, it “does not meet the bar for an urgent security fix.” They “may take action in a future release to help mitigate this technique.” Microsoft is acknowledging this research but asserting that no security boundaries have been bypassed.
While Rauch claims that indeed “two additional vulnerabilities discovered in Microsoft Teams, a lack of permission enforcement and attachment spoofing”, Microsoft argues, "For this case… these all are post exploitation and rely on a target already being compromised.” Microsoft is asserting that this technique is using legitimate features from the Teams platform and not something they can mitigate currently.
In accordance with Microsoft's assertions, indeed this is the challenge many organizations face — there are configurations and features that threat actors can exploit if not hardened. A few changes to your tenant’s configurations can prevent these inbound attacks from unknown Teams tenants.
There are security configurations within Microsoft that if hardened can help to prevent this type of attack.
Microsoft Teams by default allows for all external senders to send messages to users within that tenant. Many organization admins likely are not even aware that their organization allows for External Teams collaboration. You can harden these configurations:

Endpoint security tools are your first line of defense against suspicious activity such as accessing the device's local teams log folder which is used for data exfiltration in GIFShell. You can ensure your entire organization's devices are fully compliant and secure by using your XDR / EDR / Vulnerability Management solution, like CrowdStrike or Tenable.
You can even go a step further and integrate an SSPM (SaaS Security Posture Management) solution, like Adaptive Shield, with your endpoint security tools to gain visibility and context to easily see and manage the risks that stem from these types of configurations, your SaaS users and their associated devices.


The ease with which SaaS apps can be deployed and adopted is remarkable, but it has quickly become a double-edged sword. On one hand, the availability of SaaS tools enables employees to work from anywhere. For IT and security teams however, the adoption of SaaS apps has become a daunting endeavor.
CISOs and security professionals have cited SaaS misconfigurations as a leading cause (up to 63%!) of security incidents in the past year. Misconfigurations are brought on by many different factors, the top three can be summed up into the three V’s:
There is an inherent paradox in SaaS security: Most SaaS app owners and admins, the ones responsible to manage the app’s security settings and have profound control, are individuals who sit outside the security department. Business departments own these apps because it's what allows them to do their job efficiently. However, these individuals are untrained and not focused on security measures; these admins are working towards their departmental KPIs. For instance, Hubspot is usually owned by the marketing department, likewise, Salesforce is often owned by the business and/or Sales department, etc. Yet, it’s the security team's responsibility to secure the organization's SaaS app stack and they cannot effectively execute this task without full control and visibility of the SaaS app. The security teams often end up in the dark about the security protocols in place — and need to proactively check in with the numerous app owners to see the configurations and remediate any issues.
If you break it down by the numbers, a typical enterprise has hundreds to thousands of SaaS apps. Each app has as many as hundreds of global settings such as which files can be shared, whether MFA is required, if recording is allowed in video conferencing, and more. Multiply this number by thousands – or tens (or even hundreds) of thousands – of employees.
Security teams must familiarize themselves with each application’s specific set of rules and configurations and ensure they are compliant with their company’s policies. With hundreds of app setups and tens of thousands of user roles and privileges, this quickly becomes an unsustainable scenario. Not to mention the SaaS-to-SaaS apps that are being added to the organization’s ecosystem without the security team’s knowledge.
The SaaS app environment is dynamic and continuously evolving. Employees consistently are added or removed, new apps onboarded with permissions and configurations set, reset, changed and/or updated. There are also continuous, compliance updates to meet industry standards and best practices (NIST, SOC2, MITRE, etc.) that need to be checked. Security teams need to continuously ensure that all configurations are correctly configured company-wide, with no exceptions. Considering the high volume of apps and configurations, as mentioned in the first ‘V’, this translates to hundreds of hours of continuous work and effort that is just not sustainable.
Companies aren’t about to slow down their adoption of SaaS apps and with each new app integration comes a series of new configurations to secure. To regain control, organizations need a solution that can resolve all the challenges brought on by these 3 Vs: Volume, Velocity, and Lack of Visibility.
Organizations can ease the burden of misconfiguration management by implementing an automated solution, such as SSPM, that offers:
Misconfiguration management is one of the crucial areas security teams need to secure, but not the only area that secures an organization’s SaaS stack. Other key areas include SaaS-to-SaaS Access and Discovery and Device-to-SaaS User Management. The right SSPM solution will allow security teams to not only gain control of their misconfigurations but also these additional use cases to ensure an organization’s overall SaaS security.


According to Okta's Business of Work report, large companies use 187 different SaaS apps on average, and this number is only growing—Gartner reports that end-user spending on SaaS will reach more than $171 billion in 2022.
As this investment trend continues, new critical SaaS challenges emerge beyond the classic use case of misconfiguration and user permissions management, such as SaaS-to-SaaS access and device-to-SaaS-user posture management. This blog will give a brief overview of the trends in SaaS security.
An Unrelenting Volume Of Misconfigurations
Core SaaS offerings such as Office 365, Slack, Zoom and Salesforce, as well as the myriad of other SaaS apps that companies have deployed, are vital to a business's day-to-day operations. While these benefits are widely recognized, many companies are just now beginning to learn about the risk they introduce to the company.
Case in point, while app providers build in native security settings and configurations designed to protect businesses, the solutions can only be as secure as their weakest security control. This means that it is up to the organization to correctly configure all settings, continuously.
While that may seem straightforward, many don't consider how apps are like snowflakes when it comes to their build and security configurations—each has unique terminology, UI, etc. It is the security team's job to learn every app's "language." While that might not seem insurmountable, consider that many enterprises today have thousands of employees relying on hundreds of apps. This creates a chaotic SaaS environment where manual audits become impossible and unsustainable.
SaaS-to-SaaS Access Discovery and Control
Another growing SaaS challenge stems from SaaS-to-SaaS apps connected to the company’s core SaaS applications, also known as SaaS-to-SaaS supply chain. Today, employees are frequently prompted to give permission for one SaaS app to connect with another, and, for the most part, they oblige. That's where the problem begins. Today most users view this scenario from a productivity perspective—if they connect their SaaS apps, it will allow them to work more efficiently and ultimately help the business achieve its goals.
Every day, people give apps permission to connect with their Google Workspace or M365 environment (for example). By just clicking "accept," they give these apps permission to provide a new avenue for threat actors to gain access to valuable company data.
Now imagine this practice is happening throughout a business's workforce unbeknownst to the security team. The security team needs to see:
1. The SaaS apps that are being granted access to business-critical apps.
2. Which of these apps pose the most risk by the level of scopes (permissions) being given.
3. Which users, most especially the privileged users, granted them.
The security team needs to be equipped to decide whether to revoke access to these apps to the core SaaS apps, protecting the business yet still ensuring that the employee maintains the functionality required to do their job.
Device-To-SaaS Posture Management: The SaaS Security Zero-Trust Approach
In today’s hybrid working world, security teams must contend with threats of users accessing their SaaS applications from unsecured devices. While accessing a SaaS app via a mobile device helps boost productivity, it adds another challenge to the security team. It can pose a high level of risk for an organization, especially when the device owner is a highly privileged user.
To remediate potential threats, security teams need to be able to correlate SaaS app users, roles and permissions with their associated devices' hygiene. This end-to-end tactic enables a holistic zero-trust approach to SaaS security that is only now coming into the picture.
The Whole SaaS Security Picture
The bottom line is that checking for misconfigurations and misappropriated user roles and permission within business-critical SaaS apps is the classic SaaS Security Posture Management (SSPM). However, if the organization adopts a zero-trust approach, it is worth considering SaaS-to-SaaS access and device-to-SaaS-user monitoring and management an integral part of SSPM.
This is an excerpt from an article that was published in Forbes Council on August 10, 2022.


Typically, when threat actors look to infiltrate an organization’s SaaS apps, they look to SaaS app misconfigurations as a means for entry. However, employees now use their personal devices, whether their phone or personal laptop, etc. to get their jobs done. If the device’s hygiene is not up to par, it increases the risk for the organization and widens the attack surface for bad actors. And so, Endpoint (Device) Protection — through EDR, XDR, and vulnerability management solutions – has arisen as a critical factor in SaaS Security.
The challenge in remediating the threats posed by endpoints and devices lies in the ability to correlate between the SaaS app users, their roles, and permissions with their associated devices' compliance and integrity levels. This end-to-end approach is what's needed for the organization to implement a holistic, zero-trust approach for their SaaS Security.
Not a simple feat, however, automated SaaS Security Posture Management solutions, like Adaptive Shield, can now provide visibility that correlates the SaaS user and their associated devices with the device’s hygiene score.
How do you classify high-risk devices in the context of SaaS security?
Devices that are owned, or used by users with high levels of permissions to the company’s core SaaS apps. For example, someone who has high levels of access to the company’s CRM can present a high risk to the company if their device is vulnerable and this needs to be remediated immediately. These high-risk devices serve as a critical threat vector to an organization’s SaaS environment.
Security teams should continuously map devices to their users and their associated permissions to get a handle on which devices/users pose the highest risk.
As mentioned, the more privileged the user, the higher their device is at risk. To gain deep observability into the user, app and device posture, security teams need to check the hygiene of their users’ devices, for example up-to-date OS configurations, and any vulnerabilities. With that assessment and score in hand, security teams can map and monitor the user’s SaaS app access (in addition to, of course, securing the SaaS apps themselves).
Once these cross references are in place and accessible, organizations can enable “soft” enforcement enhancements, through policies and organizational best practices. This way security teams can monitor risks and threats without severely limiting the user.
Zero-trust is a concept much batted about in cybersecurity vernacular today. While many consider it a buzzword, its meaning represents an important approach that can not be emphasized enough. To wholly secure the organization’s SaaS stack, end-to-end, and continuously, calls for a holistic and automated solution.
Adaptive Shield has been built to resolve not only the need for management of the SaaS app configurations themselves, but also the devices the organization’s employees use. (Not to mention third party app access — and you can read more about that here.) When integrated with MDM (mobile device management) solution, Adaptive Shield will pull the device data and map the device to the owner.

By looking at the device posture while conducting a SaaS security assessment, organizations can achieve a holistic zero trust approach.


It's no secret that SaaS-to-SaaS apps can boost productivity, enable remote and hybrid work and are overall, essential in building and scaling a company's work processes.
It's an innocuous process much like clicking on an attachment was in the earlier days of email -- people don't think twice when connecting an app they need with their Google workspace or M365 environment, etc. Simple actions that users take, from creating an email to updating a contact in the CRM, can result in several other automatic actions and notifications in the connected platforms.
As seen in the image below, the OAuth mechanism makes it incredibly easy to interconnect apps and many don't consider what the possible ramifications could be. When these apps and other add-ons for SaaS platforms ask for permissions' access, they are usually granted without a second thought, not realizing that these addition connections present more opportunities for bad actors to gain access to their company's data.

How Do SaaS-to-SaaS Apps Work?
OAuth 2.0 has greatly simplified authentication and authorization, and offers a fine-grained delegation of access rights. Represented in the form of scopes, an application asks for the user's authorization for specific permissions. An app can request one or more scopes. Through approval of the scopes, the user grants these apps permissions to execute code to perform logic behind the scenes within their environment. These apps can be harmless or as threatening as an executable file.
There are four recommended ways to help secure a company's SaaS stack. Here's what a security team can share with employees and handle themselves to mitigate SaaS-to-SaaS app access risk.
The first step in cybersecurity always comes back to raising awareness. Once the employees become more aware of the risks and dangers that these OAuth mechanisms present, they will be more hesitant to use them. Organizations should also create a policy that enforces employees to submit requests for third party apps.
Security teams should gain visibility into every business critical app and review all the different third party apps that have been integrated with their business-critical SaaS apps - across all tenets. One of the first steps when shrinking the threat surface is gaining an understanding of the full environment.
Once the security team knows which third party apps are connected, they should map the permissions and the type of access that each third party app has been given. From there they will be able to see which third party app presents a higher risk, based on the higher level of scope. Being able to differentiate between an app that can read versus an app that can write will help the security team prioritize which needs to be handled first.
In addition, the security team should map which users granted these permissions. For example, a high-privileged user, someone who has sensitive documents in their workspace, who grants access to a third party app can present a high risk to the company and needs to be remediated immediately.
SaaS Security Posture Management solutions can automate the discovery of 3rd party apps. The right SSPM solution, like Adaptive Shield, has built-in logic that maps out all the 3rds party apps with access to the organization's SSPM integrated apps. This visibility and oversight empowers security teams so whether a company has a 100 or 600 apps, they can easily stay in control, monitor and secure their company's SaaS stack.
To secure a company's SaaS stack, the security team needs to be able to identify and monitor all that happens within their SaaS ecosystem. SaaS-to-SaaS access is just one use case in the SaaS Security Posture Management picture (take a look at the next addition in the series, SaaS-Device user protection).
Most existing cybersecurity solutions still do not offer adequate protection or a convenient way to monitor a company's SaaS stack, let alone the communications between their known apps and platforms, leaving companies vulnerable and unable to effectively know or control which parties have access to sensitive corporate or personal data.
Organizations need to be able to see all the configurations and user permissions of each and every app, including all the SaaS-to-SaaS apps that have been granted access by users. This way security teams can retain control of the SaaS stack, remediate any issues, block any apps using too many privileges and mitigate their risk.


It’s not a new concept that Office 365, Salesforce, Slack, Google Workspace or Zoom, etc. are amazing for enabling the hybrid workforce and hyper productivity in businesses today. However, there are three main challenges that have arisen stemming from this evolution: (1) While SaaS apps include a host of native security settings, they need to be hardened by the security team of the organization. (2) Employees are granting 3rd party app access to core SaaS apps which pose potential threats to the company. (3) These SaaS apps are accessed by different devices without their device hygiene score even being checked.
It’s not an easy task to have every app setting properly configured — at all times. The challenge lies within how burdensome this responsibility is — each app has tens or hundreds of security settings to configure, in addition to thousands of user roles and permission in a typical enterprise, compounded by the many compliance industry standards and frameworks that organizations strive to follow.
The complexity to secure SaaS apps is only increased by the fact that often the SaaS app owner sits outside the security team, in the department that most uses the app (think Sales has CRM app, Marketing has automation app) — and they are untrained and not focused on the security upkeep of the app. It all amounts to just how burdensome and unrealistic it is to expect security teams to be able to stay in control of the organization’s SaaS stack.
OAuth 2.0 has greatly simplified authentication and authorization, and offers a fine-grained delegation of access rights. Represented in the form of scopes, an application asks for the user's authorization for specific permissions. An app can request one or more scopes. Through approval of the scopes, the user grants these apps permissions to execute code to perform logic behind the scenes within their environment. These apps can be harmless or as threatening as an executable file.
When it comes to local machines and executable files, organizations already have control built in that enables security teams to block problematic programs and files. It needs to be the same when it comes to SaaS apps.
From first entry through to the device posture, security teams need to be able to identify and manage the risks coming from SaaS users and their associated devices. A device with a low hygiene score poses a high risk depending on which apps this employee is using. In the case of a highly privileged user, an unsecured device can pose an even higher level of risk for an organization. The security team needs the ability to correlate SaaS app users, their roles and permissions with their associated devices’ compliance and integrity level. This end-to-end approach enables a holistic zero-trust approach to SaaS security that is only now coming into the picture.
That’s why Gartner named SaaS Security Posture Management (SSPM) as a MUST HAVE solution to continuously assess security risks and manage the SaaS applications' security posture in the “4 Must-Have Technologies That Made the Gartner Hype Cycle for Cloud Security, 2021.” Other cloud solutions don’t offer preventative coverage. For example, a CASB solution is event-driven; CASB will alert the organization to a SaaS leak or breach only once it has occurred.
Our SSPM solution comes into play to enable security teams to identify, analyze, and prioritize misconfigurations as well as provide visibility to 3rd party apps with access to their core apps and Device-to-SaaS-User posture management.
This is an excerpt from an article that was published in The Hacker News on July 11, 2022.


Tel Aviv – July 6, 2022, Adaptive Shield today announced that its SaaS Security Posture Management (SSPM) platform has been recognized as a Trust Award finalist in the Best Cloud Security Posture Management Solution category for the 2022 SC Awards. Now in its 25th year, the SC Awards are cybersecurity’s most prestigious and competitive program where finalists are recognized for outstanding solutions, organizations, and people driving innovation and success in information security.
“Adaptive Shield and other Trust award finalists reflect astonishing levels of innovation across the information security industry and underscore vendor resilience and responsiveness to a rapidly evolving threat landscape,” said Jill Aitoro, Senior Vice President of Content Strategy at CyberRisk Alliance. “We are so proud to recognize leading products, people and companies through a trusted program that continues to attract both new entrants and industry mainstays that come back year after year.”
“Company reliance on cloud-native applications continues to accelerate, and with that come a host of new security challenges, especially managing configurations across hundreds of unique apps. To remediate SaaS issues and fully realize the benefits of these investments, businesses are turning to SaaS Security Posture Management (SSPM) solutions,” said Maor Bin, co-founder and CEO of Adaptive Shield. “We are thrilled to be named a finalist in the ‘Best Cloud Security Posture Management Solution category.’ This recognition validates the incredible work of our team and the platform’s success in delivering businesses the visibility needed to regain control of their entire SaaS environment.”
The 2022 SC Awards were the most competitive to date, with a record 800 entries received across 38 categories - a 21% increase over 2021. Entries for the SC Awards were judged by a world-class panel of industry leaders, from sectors including healthcare, financial services, manufacturing, consulting, and education, among others.
Winners will be announced during SC Awards week, scheduled to begin on August 22, 2022. A Meet the Winners networking reception celebration will take place during InfoSec World 2022, September 27th in Orlando, Florida.
About CyberRisk Alliance
CyberRisk Alliance (CRA) is a business intelligence company serving the high growth, rapidly evolving cybersecurity community with a diversified portfolio of services that inform, educate, build community, and inspire an efficient marketplace. Our trusted information leverages a unique network of journalists, analysts and influencers, policymakers, and practitioners. CRA’s brands include SC Media, SecurityWeekly, ChannelE2E, MSSP Alert, InfoSec World, Identiverse, Cybersecurity Collaboration Forum, its research unit CRA Business Intelligence, and the peer-to-peer CISO membership network, Cybersecurity Collaborative. Click here to learn more.
The original PR was released through Businesswire on July 6, 2022.


Adaptive Shield is officially On the Radar in Omdia's report for an innovative solution making a big impact in the SaaS security space.

In the report, Rik Turner, Senior Principal Analyst at Omdia, discusses accelerated cloud adoption, the rapid increase in threats, and ongoing shortage of skilled security professionals, that is driving the cybersecurity world towards more proactive approaches, after a decade in which reactive (detect and respond) ones held sway.
Rik Turner specializes in cybersecurity technology rents, IT security compliances, and call recording. His reports offer insights and analysis on the market evolution to help users determine what kind of technology and vendor they should pursue. Prior to joining Omdia RIk worked as an IT journalist, specializing in networking and security.
Rik Turner begins his analysis of Adaptive Shield with:
Adaptive Shield's SSPM Platform combines proactive, continuous, and automated monitoring capabilities with a built-in knowledge base of compliance standards and benchmarks. Once in place, it delivers visibility into the whole SaaS ecosystem, sending an alert whenever it detects a security misconfiguration. Security issues can be fixed automatically, or a ticket can be created for the customer’s security team, with detailed remediation steps.
By taking a close up look at the platform, Rik examines how the uses application programming interfaces (APIs) to query the apps and build a picture of the customer’s SaaS estate, highlighting misconfigurations, mistakes in set-up, and excessive access permissions.
The customer’s security team is provided with a user interface in which they can view how effectively each of their security controls, such as access control or their endpoint security platform, is addressing the vulnerabilities Adaptive Shield is detecting, with the ability to filter their view by app, security control, or compliance requirement, for instance.
With every SaaS application is a world unto itself each with its own API, Rik emphasizes the importance of an SSPM solution that is able to integrate a variety of apps. SaaS security
As Rik sees it, while Adaptive Shield is currently staying within the walls of the SSPM market segment, it plans to broaden its offering and enhance SaaS security by looking at the device posture of the app user and 3rd party app discovery. He predicts part of this will come through partnerships with other security vendors, such as those in endpoint security and vulnerability management. As the SSPM market continues to grow, so is it expected of Adaptive Shield.


The old days of buying new software, installing it on the company servers, and making sure everything works is gone. All hail the new IT king - SaaS platforms. Ready to go from the start, no installation needed, no hardware involved, and easy to connect the organization and its users. An IT department haven of sorts. Yet the ease of connection should not create a false sense of security. Every SaaS platform’s settings need to be hardened to protect the company's assets. While the settings are built-in natively, configurations are not always enabled by default, and are critical for SaaS security.
The responsibility to ensure the SaaS app settings are set correctly falls on the shoulders of the security team who are already overburdened with work. This blog post aims to ease that burden by providing a basic SaaS security checklist to make sure the basics are covered. I do want to stress the importance of tightening all security configurations. This list is not all encompassing, and there are other configurations that need to be checked that are SaaS-app specific.
One of the most important tools to secure a SaaS platform, and sadly one of the least properly set up tools, is SSO.
Single Sign On, SSO, is a powerful tool for taking care of one of the biggest problems in the SaaS world - too many passwords and access control. Every employee has access to dozens of SaaS platforms, and each and every one requires a username and password. This is a security disaster waiting to happen with users recycling passwords, writing them down on post-it notes, and saving them on the computer in an insecure manner.
SSO enables you to avoid all of this, and just connect using the organization's SSO. As the name suggests, Single Sign On eliminates this to a single place to log into. Every organization should have an SSO, and that SSO should be connected to each new SaaS integration app used by the organization.
Now add to the SSO an IdP (Identity provider) / Federation where supported, and you are set to have a much easier life managing any SaaS platform. This allows your users to be managed and for you to control access to the different SaaS apps from one central point.
Multi Factor Authentication (MFA), previously known as Two Factor Authentication (2FA), is a critical security feature, necessary not only for organizations, but also for private accounts. MFA is a simple concept, requiring in a log-in to not only provide a password but also a second form of authentication such as a physical key, SMS, authentication app, and others. The reason for adding this second layer of protection is first and foremost the importance of not basing the whole security of an account on a single point of failure. The second reason is that passwords are not the best form of authentication. Users recycle passwords, use easy to guess or brute force passwords, write them down on pieces of paper, and other human behavior that can compromise the password. Therefore, adding an additional layer of security is very much needed.
Not all SaaS apps allow you to connect them to an SSO, and sometimes you’ll want to allow some users to bypass SSO. Admins, for example, should be allowed to bypass SSO so they can manage the SaaS app at all times, especially if there is an SSO failure. When you allow users to bypass SSO, or don’t use SSO at all - a strong password policy and adding MFA becomes your first line of defense.
The SSO is another place that needs special care. Since, of course, there is no SSO for the SSO app, the access to the SSO account needs MFA and a strong password policy. This is the key to the kingdom, and should be secured appropriately.
When deciding on the additional factor to use for MFA, it is recommended to avoid using SMS (and use instead a physical key or an authenticator app). The reason for this is that it is relatively easy to intercept and fake SMS messages. Attacks on the SS7 protocol that are used, among other purposes, for SMS are well documented and have been used for attacking accounts that use SMS for MFA.
A strong password policy sounds like a simple matter. Force 8 characters, upper case, lower case, number, special character, and rotate the password every 90 days. This is what most enterprises do, yet this is not usually the default of a SaaS integration, and therefore should be configured to match your organization's password policy. Setting up a strong password policy can help minimize security risks of an account breach. Together with MFA, it is an extremely good protection measure.
If your organization does not have a password policy, or is in a position to change it, we recommend following the updated recommendation of NIST, the US National Institute of Standards and Technology, which is well known in the security world as the leader in recommendations and standards. NIST recommends, based on the NIST Special Publication 800-63B, the following password policy:
Users will recycle passwords, write them down, and choose easy passwords to brute force if they are forced to switch passwords frequently. It is better to have a very strong password, and change it only if there is a chance it was compromised.
Combinations of numbers, special characters, and lower-upper cases usually follow the format of “Password1!”. This is easy to brute force. Much better to use a very long password that is easy to remember - such as “MyPetAlligatorAteMySchoolHomework”. Use a minimum of 8 characters, but consider forcing at least 12 and encourage users to have 16 characters for their passwords. The example above is 33 characters long but extremely easy to remember and very hard to brute force (entropy of roughly 150 bits).
Don’t allow a user to endlessly try to put in the correct password. This is usually a brute force attempt. Or just a really hard password to remember. In any case, it shouldn’t be allowed. We recommend limiting it to no more than 10 attempts.
Screen new passwords against published passwords, dictionaries, the name of the user, and other easy to brute force. Many SaaS providers already have such tools available to enforce.
Another important aspect of setting up a SaaS app in your organization is planning the governance scheme. Many times this is ignored, and then all users get very high privilege roles and scopes. This is a major security and privacy risk, since it only takes one highly privileged account to be breached, and then the whole SaaS tenant is at risk.
It is recommended to use the principle of least privileged access needed. This mindset and security policy is one that is practiced wherever sensitive information is to be found. The idea is that every user should get exactly the role and scopes needed to perform his or her work, and nothing else. If an employee does not need admin access, they shouldn’t receive such a role.
Yet it is important not to go on the extreme with this philosophy. Every organization should have at least 2 org admins for each SaaS. This allows continuity in case one of the admins has a problem with accessing the SaaS. Also, it is recommended that the bigger the tenant is, the more admins are added to help monitor the SaaS and assist users where needed. It is difficult to strike the balance between too few admins to manage the account and too many that there is a security risk. The key way to deal with this is to continually monitor the amount of admins, and have at least an annual review of all admins and decide what the limit should be.
Well done. You set up the SaaS app, all is working, hardened, and ready to go. But how do you know your SaaS security posture will stay secure overtime? Configurations can be changed, privileged roles granted, extra scopes given, data exposed and many other disastrous changes to the SaaS settings, you put so much effort into securing. The solution for this is to set up continuous monitoring for the SaaS, often called an Audit Trail. Make sure it is configured to record any security related change in the system. Then make sure alerts are set up so you don’t need to review the logs every day of every SaaS app that you have. With an SSPM solution like Adaptive Shield, your security team can continuously monitor their SaaS security posture and receive real-time alerts when configuration drifts happen.
Finally, it is recommended to send all the logs to a central source, such as SEIM. This allows you to monitor all the SaaS apps from one plane of glass. Also, it allows you to keep an independent source of truth regarding what has happened in your SaaS. This is very important if there is a breach, since it allows you to understand how this happened, when, and how the SaaS was affected.


After 2 years of virtual events, RSA Conference 2022 in San Francisco brought back face-to-face interaction. And wow, what an experience! From live sessions and parties to games and demos galore, RSA was packed with it all. Here’s a recap of Adaptive Shield at RSA.
Our CEO, Maor Bin took the stage at RSA to speak about a new SaaS vulnerability discovered by Adaptive Shield security researchers, within Microsoft’s OAuth application registration. Bin took the audience through a live demo of the vulnerability and demonstrated how it allows anyone to leverage the Exchange’s legacy API to create hidden forwarding rules in O365 mailboxes. But it didn’t stop there.

Bin’s Session was followed by a Birds of a Feather talk where he and a handful of security experts dove deeper into the vulnerability and its implications.

The CSA panel was made up of our CEO Maor Bin, CSA Global Vice President of Research John Yeoh, A10 Networks Vice President of Product Management Mikko Disini, Lacework Global Field CTO Chris Pedigo, and Orca Security Chief Executive Officer and Co-Founder Avi Shua. These leaders in cyber security discussed the risks organizations face in today’s digital world and whether security teams are properly supporting business transformation decisions. The panel dove into questions like, what are the challenges when tracking cloud and other digital assets, etc. It goes without saying that this session was insightful and thought provoking.
During RSA, Cyber Defense Magazine celebrated its 10th year of Global Infosec Awards. Cyber Defense Magazine shares cutting edge knowledge, real world stories and awards on the best ideas, products and services in the information technology industry.
We were thrilled to have Adaptive Shield named a winner of the 2022 Global InfoSec Awards as the Next Gen in SaaS/Cloud Security.
Over the 4 days at RSA our booth greeted many friendly faces. Our experts were always up and ready to chat with visitors and talk about SaaS security, SSPM, and give a live demo of the Adaptive Shield platform.

Everyone that visited our booth had the chance to play our game “How Fast Can You Fix Your SaaS Stack?”, where we tested people’s speed and knowledge to see who could configure 20 settings in under 30 seconds.
Players that got a score of 85% or higher got their pick from an assortment of games or toys, and our grand prize winner, Erick Binti, with a perfect score of 100% received a mini Apple speaker.

Our partner Torq joined us at our booth to give a demo of our paired solution. Torq is a no-code platform that’s purpose-built for security automation. Together with Adaptive Shield, Torq streamlines the deprovisioning process through automation, lifts the burden of manually auditing and deactivating accounts, and provides continuous visibility and control to increase the organization’s SaaS security posture.

To top off the hard day's work, Adaptive Shield co-sponsored the FOMO party with a live performance from the band, Incubus. With rock-out music, glowing bracelets, and tasty food, the FOMO party was definitely the place to be.


RSA 2022 was a great way to bring back in-person events and we are looking forward to seeing what next year has in store.



The SaaS app attack surface has widened and recent research shows that up to 63 percent of organizations have dealt with security incidents because of a SaaS misconfiguration. Lack of visibility, thousands of configurations for the security team to monitor and remediate, and too many departments with access are the leading causes of SaaS misconfigurations. There are unrealistic expectations on security teams and app owners (who sit outside the security team) to manually handle every app, configuration, and user role.
Gartner created the SSPM category in 2020 to address these challenges to refer to tools that enable security teams to have full and continuous visibility of SaaS security settings and configurations. Up until this category emerged, Cloud Security Posture Management (CSPM) and Cloud Access Security Broker (CASB) were considered able to secure the Saas stack. However, CSPM focuses on infrastructure-as-a-service security solutions, where SSPM is specifically catered to SaaS app technology. Meanwhile, while CASB and SSPM are both designed to address security issues within SaaS applications, CASB falls short as it identifies incidents after they happen. SSPM offers organizations a SaaS-specific, preventative solution that allows them to gain full visibility of their SaaS stack security.
According to our 2022 SaaS Security Survey completed in conjunction with CSA (Cloud Security Alliance), SSPM has become the top priority with 62% of companies currently using or planning to implement in the coming 24 months.
From the breadth of applications supported to the depth of its security checks, an SSPM provides organizations continuous, automated surveillance of all SaaS apps, alongside a built-in knowledge base to ensure the highest SaaS security hygiene. When comparing SSPM solutions there's a few key features to keep in mind to make sure your business is getting the best SaaS security.
When evaluating different SSPM the first thing to look out for is its ability to integrate all your needed SaaS apps. Every organization uses at least a handful of SaaS apps if not hundreds, each with their own unique settings. Any app can pose a risk and smaller apps often serve as a gateway for an attack, this is why it’s crucial to have every app to be fully integrated. As a rule of thumb, look for an SSPM with a minimum of 30 integrations that are adaptable and able to run checks on every data type to protect against misconfigurations.
The other vital component to an effective SSPM is the expanse and depth of the security checks. Every SaaS app has its list of domains to monitor, such as: identity and access management, malware protection, data leakage protection, auditing, access control for external users, and so on.
This goes hand in hand with continuous monitoring and remediation. Part of an SSPM’s job is to not only detect the threats but to combat them. Remediating issues in business environments is a complicated and delicate task. The best SSPM solution should provide context about each configuration, enable you to easily monitor, and set up alerts. When alerts do happen, the platform should map out remediation. This way, when misconfigurations do happen, a business is left vulnerable for a minimal window of time.
Part of what enables an SSPM solution to provide full visibility is its user and device inventory. User inventory takes into account all the different SaaS apps used by different employees and the level of access which they have. When a user fails a security check, security teams are immediately notified to enable a seamless user management and investigation across all SaaS apps. Device inventory allows security teams to see which devices have access to company SaaS apps and manage the risk based on the device hygiene score.
An effective SSPM maps out the security controls of major compliance frameworks such as SOC 2, ISO 27001 and NIST Special Publication 800-53, in order to provide in-depth security checks by app, user, severity or any other metric indicating misconfigurations. When misconfigurations or failed security checks do happen, security teams are not only alerting immediately, they also get a step-by-step remediation description to see exactly how to fix the SaaS misconfiguration
Another aspect that is growing in importance on the SaaS security landscape is that of 3rd party app access. Users don't think twice about connecting an app with their Google Workspace or M365 but these automatic actions are becoming a threat in the corporate cybersecurity landscape. That being said, 3rd party app access is also a key feature that helps boost companies’ productivity and enable remote work. Adaptive Shield, for example, gives security teams visibility into these business-critical apps and reviews the permission and access levels of different 3rd party apps being integrated to reduce the severity of a threat.
We are honored that Gartner has named Adaptive Shield a 2022 Gartner Cool Vendors™ in Application Security: Protection of Cloud-Native Applications. We believe that this is a powerful step not just for Adaptive Shield, but for the field of SaaS Security Posture Management (SSPM).


When it comes to keeping SaaS stacks secure, IT and security teams need to be able to streamline detection and remediation of misconfigurations in order to best protect their SaaS stack from threats. However, while companies adopt more and more apps, their increase in SaaS security tools and staff has lagged behind, as found in the 2022 SaaS Security Survey Report.
The survey report, done in collaboration with CSA, dives into how CISOs today are managing the growing SaaS app attack surface and the steps they are taking to secure their organizations. While there are 7 significant takeaways from the report, this blog takes a closer look at the 5th finding - how the use of an SSPM reduces the amount of time it takes to to detect and remediate SaaS misconfigurations.
The report finds that at least 43% of organizations have experienced a security incident as a result of a SaaS misconfiguration, however with another 20% being “unsure”, the real number could be as high as 63%. These numbers are particularly eye-opening when compared to the 17% of organizations experiencing security incidents due to an IaaS misconfiguration. Bearing this in mind, the question follows: how fast are SaaS misconfigurations detected and how long does it take to remediate the issue? In order to answer these questions, it's important to make a distinction between organizations that have implemented an SSPM solution and those that have not.
For organizations that are yet to onboard an SSPM, the IT and security teams can only manually check the apps’ many configurations to secure their SaaS stack. This means security teams need to not only be on top of remediating misconfigurations but also conducting regular security checks in order to manually detect any of these misconfigurations. The longer either of these actions take to be completed, the longer the company is exposed to threats.
One of the major problems for organizations’ security teams is the overwhelming amount of manual work. Companies today are reliant on dozens upon dozens of business-critical apps each with hundreds of configurations, which then need to be set according to the hundreds to thousands of employees.
Nearly half (46%) of the survey respondents, as seen in figure 2, check their SaaS security monthly or less frequently, and another 5% don’t check at all. It seems that security teams are overwhelmed with the workload, and are struggling to stay on top of all the settings and permissions. As organizations continue to adopt more and more apps, their gap of visibility into all configurations grows.

When a security check fails, security teams must then go in and understand why exactly the check failed and the best course of action to fix it. Approximately 1 in 4 organizations, as seen in figure 3, take one week or longer to resolve a misconfiguration when remediating manually. Overall, security teams trying to manage their SaaS security are not only overwhelmed but are also in turn leaving the organization exposed for a longer period of time.

Organizations using SSPM are able to conduct security checks more often and remediate misconfigurations within a shorter time frame. An SSPM enables security teams to conduct frequent checks in compliance with both industry standards and company policy. The 2022 SaaS Security Survey Report found that the majority of these organizations (78%) run security checks once per week or more often, as seen in figure 4.

When a misconfiguration is detected, 73% of organizations using an SSPM resolved it within a day, and 81% resolved it within the week, as seen in figure 5. A good SSPM solution however will not only evaluate failed security checks caused by misconfigurations, but will also assess risk and configuration weakness — and provide exact instruction on how to remediate the issue.

SSPM not only reduces the workload on security teams, but also eliminates the need for them to be experts on each SaaS app and its settings. The data presented in the 2022 SaaS Security Survey Report highlights the drastic differences between companies using SSPM and those not, showing how valuable SSPM is to SaaS security detection and remediation.


Every year the leaders and entrepreneurs of the cybersecurity world come together for four days for the annual RSA Conference. During these four days, visitors gain insight, join conversations, and experience solutions that could make an impact on their businesses and careers.
Finally, after many years of the event being virtual, RSA is back in its physical form. This year's conference will feature numerous presentations from industry leaders offering unique insights and fresh perspectives on the world of cloud and SaaS security. We have gathered a list of the 13 top talks taking place at RSA 2022.
Pete Chronis, SVP,CISO, ViacomCBS
Ami Luttwak, Chief Technology Officer & Co-Founder, Wiz
John Yeoh, Global Vice President of Research, Cloud Security Alliance
Tuesday, Jun. 7, 2022 9:40 AM - 10:30 AM PT
The shared responsibility model is broken. As companies fail to keep up with cloud complexity, vendors and cloud providers each continue to maintain inconsistent sets of cloud misconfigurations to track. This panel of experts will debate the need for extending the current CVE model to become more cloud friendly and discuss how CSA is leading the charge.
Maor Bin, CEO and co-founder of Adaptive Shield
Wednesday, Jun. 8, 2022 1:15 PM - 2:05 PM PT
Adaptive Shield security experts found a new SaaS vulnerability within Microsoft’s OAuth application registration. This vulnerability allows anyone to leverage the Exchange’s legacy API to create hidden forwarding rules in O365 mailboxes. This talk will demo the OAuth registration process in Microsoft as well as the use of the new vulnerability.
Mary Yang, Chief Marketing Officer, LookingGlass Cyber Solutions
Monday, Jun. 6, 2022 10:50 AM - 11:40 AM PT
For many organizations, reducing their attack surface has become a critical goal. Yet vulnerabilities and vectors continue to be exploited. Organizations are left asking themselves what they can do to get a better handle on their attack surface? This Birds of a Feather will dive into not only the growing challenges but also the best practices for managing one’s attack surface.
Tal Darsan, Manager, Managed Cybersecurity Services, Cato Networks
Etay Maor, Sr. Director Security Strategy, Cato Networks
Monday, Jun. 6, 2022 2:20 PM - 3:10 PM PT
Network based threats have evolved and are finding new ways to evade security solutions. This session will take a look at different case studies and techniques that organizations can use when implementing network based threat hunting and show how teams can face cloud native threats with a cloud native security approach.
Michael Coden, Senior Advisor, Boston Consulting Group
Colin Troha, Managing Director, Boston Consulting Group
Tuesday, Jun. 7, 2022 8:30 AM - 9:20 AM PT
The concept of work has shifted from office buildings to something that can be done anywhere at any time. Point products, VPN, and “trusted” network zones no longer provide the protection they once did. In fact, now they introduce risk. Securing hybrid work requires a fundamental change that challenges traditional security approaches and exposes legacy architectures.
Rohit Joshi, SecDevOps Engineer, SAP
Joseph McCrea, DevSecOps Engineer, SAP
Wednesday, Jun. 8, 2022 8:30 AM - 9:20 AM PT
When migrating to public cloud, organizations introduce new attack surfaces which are usually the exploitation of misconfigured resources. It raises the question: how are threats detected in a cloud that contains millions of resources? This talk will discuss the journey from security policy documentation to scanning and detecting security compliance violations in product infrastructure from the start of the development life cycle.
Petko Stoyanov, Global CTO, Forcepoint
Wednesday, Jun. 8, 2022 1:15 PM - 2:05 PM PT
The security industry has reached a breaking point. The never ending line of technologies are doing the same thing over and over. Analysts have agreed that true platforms are the new path forward. This session offers insights on what distinguishes “real” platforms and how they’re making security simpler.
Nir Ohfeld, Senior Security Researcher , Wiz
Shir Tamari, Head of Research, Wiz
Wednesday, Jun. 8, 2022 1:15 PM - 2:05 PM PT
A new risk for cloud users has arised that relates to software being run by the cloud providers within the customer cloud. A chain of critical vulnerabilities found in Azure built-in VM agents affecting almost every customer using Azure. The question addressed in this talk then becomes: who owns the fix?
Sander Vinberg, Threat Research Evangelist, F5
Wednesday, Jun. 8, 2022 1:15 PM - 2:05 PM PT
This presentation features the 5th annual Application Protection report from the F5 Labs team. The session will focus on the trends and data from multiple angles and help provide an overall picture of the application security threat landscape. The session will dive deep into application-related security breaches and cloud security with some never-before-seen data.
Maor Bin, CEO and Co-Founder of Adaptive Shield
John Yeah, Global Vice President of Research, CSA
Mikko Disini, Vice President of Product Management, A10 Networks
Avi Shua, Chief Executive Officer and Co-Founder, Orca Security
Jun. 6, 2022 9:45 AM - 10:30 AM PT
The last few years have shown an accelerated adoption of cloud products and services. Many organizations have moved quickly towards digital transformation in order to stay engaged with customers and employees and keep pace with the competition. What are the challenges when tracking cloud and other digital assets? Are businesses measuring the risk associated with these assets? The panel discusses the cybersecurity risks organizations face in today’s digital world and whether security teams are properly supporting business transformation decisions.
Tanya Janca, Founder and CEO, We Hack Purple
Monday, Jun. 6, 2022 8:30 AM - 9:20 AM PT
As security teams become vastly outnumbered, many organizations have responded with different program scaling methods, including building security champions programs. Which leads to questions: How does a security champions program work? How are champions selected? This talk outlines the path for success, touching on recruitment, engagement, teachings, recognition, reward, and more.
Christopher Romeo, CEO, Security Journey
Monday, Jun. 6, 2022 9:40 AM - 10:30 AM PT
Many people have a Security Champion program, but not all of them are effective. This session will map out the qualities of an elite Security Champion program in the DevSecOps world, for those who don’t have a program and those whose programs need a reboot.
Steven Lipner, Executive Director, SAFECode
Tony Sager, Senior VP and Chief Evangelist, Center for Internet Security
Monday, Jun. 6, 2022 2:20 PM - 3:10 PM PT
Many concepts discussed in software supply chain security are derived from old-fashioned material goods supply chains. The word "chain" is a broken metaphor for security. The "web" of software supply would be more appropriate. This session will present and discuss alternative models from other industries that developers should use. These are a mix of standards, some testing, and some enforcement.
These 13 talks can be a great kick off, inspiring middle, or a sweet ending to your RSA experience so make sure to pencil them into your schedule.
Claim your $150 discount on a conference ticket and make sure to visit us at booth #1655 in the Moscone South Expo for great prizes and fun games. We look forward to seeing you there!



“How many people do you know that clean their house once a quarter? …you have to keep a certain level of hygiene both in your house and your SaaS stack.”
Uttered by our CEO, Maor Bin, in a webinar with Omdia Senior Principal Analyst, Rik Turner about the growing need to take a proactive, automated approach to SaaS security. Here are some highlights from the webinar - catch the whole webinar in full here.
Rik Turner begins the webinar by reflecting on the emergence of SaaS apps in the early 1990s leading up to 2010. “The world of SaaS apps grew rapidly and for good reason,” Rik explains, “SaaS is so easy that once you’ve adopted it, someone in the next business unit comes and says ‘oh you guys are using that? That looks great’ and next thing you know half the company is using something that nobody in IT even sanctioned.” Security teams need control and visibility to all the configurations of the company’s SaaS apps in use.
By 2014, Cloud Access Security Broker (CASB) had reared its head as a powerful cloud security solution to address the above mentioned issue. CASBs proved effective in helping restore visibility to the IT and security teams, however, as a reactive solution, there was still no preemptive approach for giving visibility to all the (mis)configurations across the growing SaaS app stack. It wasn't long after that Gartner brought SSPM into the playing field with its SaaS specific security solution.
An SSPM’s job is to maintain continuous hygiene across a SaaS stack by continuously monitoring all the SaaS security risks and automatically identifying if all the native security controls are correctly configured. By doing so, SSPM offers businesses a preventative SaaS security solution.
The webinar pulls findings from the 2022 SaaS Security Survey Report to demonstrate the current state and perception of SSPM. Rik Turner highlights the significant correlation between SaaS misconfigurations and security incidents, showing that up to 63% of security incidents are caused by a SaaS misconfiguration.

“This kind of datapoint isn't very surprising. We are always talking about how configurations are the number one attack vectors. They’re the number one threat for companies when we’re talking about cloud security. These small mistakes can lead to very, very serious problems - account takeover, data leakage, and more,” asserts Bin.
SaaS apps have changed the way security and IT teams think about security. Gone are the days of security teams being experts on every company program or system. It becomes impossible for security teams to be familiar with the in and outs of every SaaS app. The fact of the matter is that while companies have quickly implemented new SaaS apps, they have lagged behind when growing their security teams and tools. There is a reported 81% increase in SaaS apps but only a 73% increase in security tools and a lesser 55% increase in security staff. This is causing security teams to be overburdened which in turn creates a cycle of companies leaving themselves exposed.

Simply put, security teams today don't have the capacity to manually configure every SaaS setting in an effective way. Nearly half of the security teams today attempting to do so are only checking their SaaS security settings monthly or less often — 15% are checking quarterly.
Meanwhile as Rik Turner points out, companies that have embraced SSPM have provided security teams with deep visibility into their SaaS stack security allowing them to deal with the misconfiguration threats.

Businesses and organizations are inseparable from the use of their SaaS apps. Bin and Turner address these issues and more in the full webinar, giving further insight to how the world of SaaS is growing and how SSPM is taking a proactive approach to securing businesses’ SaaS stacks.
“As these numbers show, once you introduce an SSPM, it dramatically improves an organization’s ability to detect and remediate these misconfigurations.” Turner.


Last year, we spearhead our first annual SaaS Security Survey Report, where the findings illuminated the SSPM landscape and where the market was holding. In the 2022 SaaS Security Survey Report, in collaboration with CSA, we examine the state of SaaS security in today’s enterprises and see how much the market and the overall space of SSPM has matured in just one year. This report gathers anonymous responses from 340 CSA members, CISOs and security professionals, to examine not only the growing risks in SaaS security but also how these different organizations are currently working to secure themselves. While there are many takeaways from the survey, these are our top seven.
Demographics
Before diving into the findings, here is some quick background information on the anonymous respondents. The majority (71%) of respondents were located in the Americas, another 17% from Asia, and 13% from EMEA. Of these participants 49% influence the decision making process while 39% run the process itself. The survey examined organizations from a variety of industries, such as telecommunications (25%), finance (22%), and government (9%). For more details regarding the demographics, please refer to full report.

Since 2019, SaaS misconfigurations have become a top concern for organizations, with at least 43% of organizations reporting they’ve dealt with one or more security incidents caused by a SaaS misconfiguration. However, since many other organizations state they are unaware if they had experienced a security incident, the number of SaaS misconfigured-related incidents could be as high as 63%. These numbers are striking when compared to the 17% of security incidents caused by IaaS misconfigurations.

So what exactly is the cause of these SaaS misconfigurations? While there are several factors to consider, the survey respondents narrow it down to the two leading causes – having too many departments with access to SaaS security settings (35%), and a lack of visibility into the changes in the SaaS security settings (34%). These are two related issues, neither of which are surprising given that lack of visibility was rated a top concern when adopting SaaS applications, and that on average organizations have multiple departments with access to security settings. One of the leading reasons for the lack of visibility is the fact that too many departments have access to security settings and many of these departments don't have proper training and focus on security.

It’s well-known that businesses are adopting more apps – this past year alone, 81% of respondents say that they have increased their investments in business-critical SaaS applications. On the other hand, investment in security tools (73%) and staff (55%) for SaaS security is lower. This dissonance represents an increasing burden on the existing security teams to monitor SaaS security.

46% of organizations that manually monitor their SaaS security are conducting checks only once a month or less, while 5% don't conduct checks at all. After discovering a misconfiguration, it takes additional time for security teams to resolve it. Approximately 1 in 4 organizations take one week or longer to resolve a misconfiguration when remediating manually. This lengthy timing leaves organizations vulnerable.


The flip side of the coin for finding #4 is that the organizations that have implemented an SSPM can more quickly and accurately detect and remediate their SaaS misconfigurations. The majority of these organizations (78%) utilize an SSPM to check their SaaS security configurations once a week or more. When it comes to resolving the misconfiguration, 81% of organizations using an SSPM are able to resolve it within a day to a week.


Third party apps, also called no-code or low-code platforms, can boost productivity, enable hybrid work, and are overall essential in building and scaling a company’s work processes. However, many users quickly connect 3rd party apps without considering what permissions these apps are requesting. Once accepted, the permissions and subsequent access granted to these 3rd party apps could be harmless or as malicious as an executable file. Without visibility into the SaaS-to-SaaS supply chain employees are connecting to their organization’s business-critical apps, security teams are blind to many potential threats.

Despite the category being introduced to the market two years ago, it is fast maturing. When assessing four cloud security solutions, SSPM receives an average rating of “somewhat familiar”. Furthermore, 62% of respondents report that they are already using an SSPM or plan to implement one in the coming 24 months.

The 2022 SaaS Security Survey Report offers insights into how organizations are using and protecting their SaaS applications. It is without a doubt that as companies continue to adopt more business-critical SaaS apps, there is more risk. To face this challenge head on companies should begin securing themselves through two best practices:
These kinds of best practices will provide support to security teams without preventing them or any other departments from doing their work.
.png)
.png)
We are excited to announce that Gartner has named us a 2022 Gartner Cool Vendors™ in Application Security: Protection of Cloud-Native Applications.
.png)
According to the Gartner report, “Digital business initiatives have accelerated, and this, in turn, has accelerated development of cloud-native applications. This creates challenges in terms of securing these applications.”
At a time when companies run nearly every facet of their business in the cloud, we provide deep visibility into a business’s entire SaaS ecosystem. Through proactive, continuous, and automated monitoring capabilities, our solution sends detailed alerts at the first sign of a security misconfiguration and proactive fixes for all global settings and user privileges.
“We’re honored to be named by Gartner and included alongside these other Cool vendors,” said Maor Bin, CEO and co-founder of Adaptive Shield. “Business adoption of cloud-native applications is growing and introducing new vulnerabilities in the SaaS Stack that must be addressed. This challenge is reflected in our newly released 2022 SaaS Security Survey conducted in conjunction with CSA (Cloud Security Alliance). According to the research, up to 63% of organizations have experienced security incidents due to SaaS misconfigurations which have made SSPM solutions a top priority.”
Read the full report to see a breakdown of what exactly makes Adaptive Shield a Cool Vendor.


During the last week of March, three major tech companies - Microsoft, Okta, and HubSpot - reported significant data breaches. DEV-0537, also known as LAPSUS$, performed the first two. This highly sophisticated group utilizes state of the art attack vectors to great success. Meanwhile, the group behind the HubSpot breach was not disclosed. This blog will review the three breaches based on publicly disclosed information and suggest best practices to minimize the risk of such attacks succeeding against your organization.
On March 21, 2022, HubSpot reported the breach which happened on March 18. Malicious actors compromised a HubSpot employee account that the employee used for customer support. This allowed malicious actors the ability to access and export contact data using the employee’s access to several HubSpot accounts.
With little information regarding this breach, defending against an attack is challenging, but a key configuration within HubSpot can help. This is the “HubSpot Employee Access” control (shown in the figure below) in HubSpot’s account setting. Customers should disable this setting at all times, unless they require specific assistance, and then immediately turn it off after completing the service call.

A similar setting appears in other SaaS applications and should be disabled there as well. Employee access is typically recorded in Audit Logs, which should be reviewed regularly.
Okta subcontracts some of its customer support to the Sitel Group. On January 21, an Okta security team member received an alert that a new MFA factor was added to a Sitel Group employee account from a new location.
An investigation revealed that a Sitel support engineer’s computer was compromised using a remote desktop protocol. This known vulnerability is normally disabled except when specifically needed — which helped Okta investigators narrow the timeframe for the attack to a five-day window between Jan. 16-21, 2022.
Due to the limited access support engineers have to their system, the impact on Okta customers was minimal. Support engineers don’t have access to create or delete users or download customer databases. Their access to customer data is quite limited as well.
On March 22, DEV-0537, which is more commonly known as LAPSUS$, shared screenshots online. In response, Okta released a statement saying, “there are no corrective actions our customers need to take.” The following day the company shared details of its investigation, which included a detailed response timeline.
While this breach was limited in the damage it caused, it offers three important security lessons.
See Cloudflare's investigation of the January 2022 Okta compromise for a good example of a response to such a breach.
On March 22, Microsoft Security shared information relating to an attack it suffered at the hands of DEV-0537. Microsoft had a single account compromised, which resulted in source code being stolen and published.
Microsoft assured its users that the LAPSUS$ attack didn’t compromise any of their information, and further stated that there was no risk to any of their products due to the stolen code.
Microsoft did not specifically share how the breach was carried out, although it did alert readers that LAPSUS$ actively recruits employees at telecoms, major software developers, call centers, and other industries to share credentials.
The company also offered these suggestions for securing platforms against these attacks.
For a full list of Microsoft’s recommendations, see this note.
Securing SaaS platforms is a major challenge, and as seen this week, even global enterprises need to stay on top of their security. Malicious actors continue to evolve and improve their attack methods, which forces organizations to constantly be on the lookout and prioritize their SaaS security.
Strong passwords and SSO solutions are no longer enough by themselves. Companies need advanced security measures, such as strong MFA, IP allow lists, and blocking unnecessary support engineer access. An automated solution like SaaS Security Posture Management (SSPM) can help security teams stay on top of these issues.
The importance of device security in SaaS is another takeaway from these attacks. Even a fully secured SaaS platform can be compromised when a privileged user accesses a SaaS app from a compromised device. Leverage a security solution that combines device security posture with SaaS security posture for full, end-to-end protection.
The challenge of securing SaaS solutions is complex and beyond burdensome to complete manually. SSPM solutions, like Adaptive Shield, can provide automated SaaS security posture management, with configuration control, endpoint posture management, and 3rd party application control.


It’s without a doubt that the SaaS app attack surface has been continuing to grow as businesses have become more reliant on apps to organize and run their business-critical operations. To better understand how teams are dealing with their SaaS security posture, Adaptive Shield partnered with the leading organization dedicated to promoting best practices for ensuring cyber security, Cloud Security Alliance (CSA), to develop the 2022 SaaS Security Survey Report.

The goals of the study was to understand the current state SaaS security through investigating the following key areas of interest:
The 2022 SaaS Security Survey Report offers insight into the industry knowledge, attitudes, and options regarding SaaS security and related misconfigurations.
Maor Bin, CEO and co-founder of Adaptive Shield says:
“This survey shines a light on what CISOs and cybersecurity managers are looking for and need when it comes to securing their SaaS stack — from visibility, continuous monitoring and remediation to other ever-growing, critical use cases such as 3rd party application control and device posture monitoring. The SSPM market is maturing rapidly — and this type of zero-trust approach for SaaS is where the SSPM market is going. ”
CSA gathered responses anonymously from 340 CSA members from IT and security professionals from various organization sizes, industries, locations, and roles. (Sponsored by CSA Corporate Members, the study’s content development and editing rights remained absent of added influence.)
Among the survey’s key findings:
The survey concludes by suggesting key methods of improving SaaS security to help organizations implement the preventive measures that could secure them from the next breach.
If you want to see all the details, like more of organizations top SaaS security concerns, their policy when dealing with unsanctioned SaaS applications, and different methods for monitoring SaaS security configurations, download the full survey.


In the busy enterprise computing environment, user onboarding and offboarding is a fact of daily life.
When employee counts range into five figure territory — and entire networks of contractors have to be accounted for as well — it’s easy to lose track of who’s, literally, coming and going. Oftentimes, there are “offboarding” steps that are forgotten about — disabling or removing the user from Active Directory or IAM is not sufficient as the user may have local credentials on some of the SaaS platforms or other sensitive systems. Leaving these users’ access in place exposes organizations to unauthorized data access.
When it comes to taking old users off systems - deprovisioning - there are a few best practices that should be borne in mind and followed.
Keep an Inventory. It’s essential that IT teams keep an up to date record, at all times, of all users with access to company systems. A channel of communication with human resources should be established for keeping abreast of events impacting the user inventory such as employee terminations. To be effective from a security standpoint, these systems need to be capable of scrutinizing both internal and external users. The vendor landscape can be constantly shifting.
Always be on the lookout: In addition to keeping track of intended system users, IT teams need to have a capability for user discovery that accounts for the full breadth of systems they may be accessing - both those in legacy environments, like on-premises systems, and in the mushrooming cloud environment.
Rigorous access control: It’s imperative that IT teams develop onboarding and offboarding protocols that account for the full extent of privileged employee computing access. If an employee has access to 3 internal systems and 30 cloud-hosted ones, then clearly limiting access to those on-premises will leave a gaping information hole that they will retain access to.
The meticulous mapping and security work that this process demands from a security team is vast. Adaptive Shield can streamline this process — a simple query in Adaptive Shield’s user inventory can reveal the user posture of the deprovisioned users’ accounts across the entire SaaS stack
When it comes to deprovisioning these accounts, automation tools like Torq - a no-code security automation platform - give security teams an easy way to integrate Adaptive Shield’s capabilities into an automated deprovisioning workflow. This vastly simplifies the process, reducing the amount of time it takes to fully deprovision users, and ensuring that no accounts are left active.

In Figure 1, you can see a potential workflow where:
This workflow is just one example of how Adaptive Shield’s integration with Torq streamlines the deprovisioning process through automation, lifts the burden of manually auditing and deactivating accounts, and provides continuous visibility and control to increase the organization’s SaaS security posture.


With 2021 drawing to a close and many closing their plans and budgets for 2022, the time has come to do a brief wrap up of the SaaS Security challenges on the horizon. Here are the top 3 SaaS security posture challenges as we see them.
The Mess of Misconfiguration Management
The good news is that more businesses than ever are using SaaS apps such as GitHub, Microsoft 365, Salesforce, Slack, SuccessFactors, Zoom, and many others, to enable employees to maintain productivity under the most challenging of circumstances. As for the bad news, many companies are having a hard time adequately addressing the ever-changing security risks of each app.
This challenge begins with a simple miscalculation—businesses are tasking security teams with ensuring that the security configurations for each app is set correctly. While that may seem like the logical choice, these apps are like snowflakes, no two are the same, including their specific settings and configurations. This is exacerbated by SaaS environments that contain hundreds of apps. Add it all up and what’s left is an unrealistic burden being placed squarely on the shoulders of security teams. These teams do not have the superhuman computing power to be able to monitor thousands of configurations and user permissions daily to secure the organization’s SaaS app stack, without a SaaS Security Posture Management (SSPM) solution.
Users, Privileged Users Everywhere
One only has to consider the typical employee, untrained in security measures, and how their access or privileges increase the risk of sensitive data being stolen, exposed, or compromised. The ease with which SaaS apps can be deployed and adopted is remarkable — and with employees working everywhere, the need for strengthened governance for privileged access is clear.
This has been a long time coming; the shifts in the working climate have further accelerated the process, yet SaaS adoption has been gaining ground for years. Organizations today need the capability to reduce risk caused by over-privileged user access and streamline user-to-app access audit reviews by gaining consolidated visibility of a person’s accounts, permissions, and privileged activities across their SaaS estate.
Ransomware through SaaS
When threat actors decide to target your SaaS applications, they can use more basic to the more sophisticated methods. Similar to what Kevin Mitnick in his RansomCloud video, a traditional line of a business email account attack through a SaaS application follows this pattern:
This is a specific type of attack through SaaS, however, other malicious attacks through OAuth applications can occur in an organization’s environment.
Final Thoughts
Gartner named this domain as one of the “4 Must-Have Technologies That Made the Gartner Hype Cycle for Cloud Security, 2021.
With a SaaS Security Posture Management (SSPM) platform, like Adaptive Shield, you can prevent such attacks and automate the prioritization and remediation processes to fix any misconfiguration issues as they happen.


There is often confusion between Cloud Access Security Brokers (CASB) and SaaS Security Posture Management (SSPM) solutions, as both are designed to address security issues within SaaS applications. CASBs protect sensitive data by implementing multiple security policy enforcements to safeguard critical data. For identifying and classifying sensitive information, like Personally Identifiable Information (PII), Intellectual Property (IP), and business records, CASBs definitely help.
However, as the number of SaaS apps increase, the amount of misconfigurations and possible exposure widens and cannot be mitigated by CASBs. These solutions act as a link between users and cloud service providers and can identify issues across various cloud environments. Where CASBs fall short is that they identify breaches after they happen.
When it comes to getting full visibility and control over the organization’s SaaS apps, an SSPM solution would be the better choice, as the security team can easily onboard apps and get value in minutes — from the immediate configuration assessment to its ongoing and continuous monitoring. By fixing these configuration weaknesses and misconfigurations in the SaaS stack, the security team is actually preventing a leak or breach.
To fully understand why SSPM is the ideal solution for today’s SaaS environment, it’s best to take a look at the challenges that accompany these deployments.
Today eighty-five percent of InfoSecurity professionals cite SaaS misconfigurations as one of the top three risks facing today’s organizations. The challenge stems from what we like to call the three V’s of SaaS Security:
SaaS app providers build in robust security features that are designed to protect company and user data, yet whether the features are implemented correctly are another matter.
The configurations and enforcement fall under the responsibility of the organization utilizing the app.
A SaaS Security Posture Management solution, like Adaptive Shield, is critical to the security of today’s enterprise. Gartner predicts SSPM will increase its impact over the next five to ten years. With its ability to effectively manage this chaotic SaaS environment, SSPM can continuously assess and manage the security risk and posture of SaaS apps and prevent configuration errors and advanced attacks. While CASBs do address an organization’s security gaps at the SaaS layer, they are, as mentioned earlier, primarily reactive, focusing on the detection of breaches once they have occurred.
When it comes to preventing misconfigurations, proactive identification is key, making SSPM the best option to ensure a secure and safe SaaS environment.
This was first published in The Hacker News on November 1, 2021.


Microsoft 365 (M365), formerly called Office 365 (O365), is Microsoft’s cloud strategy flagship product with major changes ahead, such as the deprecation of their legacy authentication protocols. Often stored on or saved to the device, Basic Authentication protocols rely on sending usernames and passwords with every request, increasing the risk of attackers capturing users’ credentials, particularly if not TLS protected. Basic Authentication, while necessary for companies using legacy software, is unable to enforce MFA and is superseded by Modern Authentication.
The legacy settings have been on Microsoft’s radar to fix for years. In 2018, Microsoft announced it would introduce a series of changes — and ultimately deprecation — to its authentication controls as a means to help organizations mitigate the risk. These changes were set to take place over a number of years, and in September 2021, they announced that they will begin to permanently disable Basic Auth in all tenants, regardless of usage, with the exception of SMTP Auth by late 2022.
In order to enable a smooth transition from these legacy protocols to a modern environment, Adaptive Shield has created a step-by-step guide to help you reduce risk and reinforce your organization’s M365 security. Adaptive Shield has also developed and released a PowerShell script that creates a unified report to map out the organization’s posture to know which users have legacy protocols enabled — for you to copy-paste. This blog covers the broad strokes of the guide from the discovery techniques and blocking access processes while showing you how to handle special exclusions.
To download the full guide with all the scripts, click here.
To secure the organization’s deployment, the first step is knowing what types of basic authentication protocols exist. Within Microsoft, the considered basic/legacy protocols include:
These authentication protocols do not support modern authentication mechanisms like multi-factor authentication (MFA), which means that enabling MFA won't suffice.
To enhance security and mitigate risk, organizations must find all the users and services that use the legacy protocols, migrate to use modern protocols, and block the basic ones. This whitepaper will take you through the discovery and blocking process, in addition to sharing instructions for additional controls, like Mailbox services and Conditional Access policies, that can reinforce your Microsoft 365 security posture.
Before shutting down all legacy protocols within the organization, it is important to identify users and services that are using basic authentication. Rather than reduce productivity and generate user frustration, it is important to let users know that the system is being upgraded, which will help avoid business interruptions and promote a painless transition to modern protocols.
The are a few ways to learn about your organization’s posture using these methods:
Running the PowerShell script acts as a good starting point to map out the user and service landscape that needs to be mitigated.
After running a few Powershell cmdlets, the Adaptive Shield team created this PowerShell script (See complete guide for the script ) to merge them all into one unified report. The script generates a file: BasicProtocolsReport.csv. This file will show users and their legacy protocol statuses. Each protocols' status is tested against Authentication Policy, Mailbox services, and Transport config. Below is the list of the full payload:
Create a report with Conditional Access (see figure 1) which simulates the users and services that would be affected if you were to block basic authentication protocols. This report gives you visibility into the users and services actually using the legacy protocols.
Suggested run time for this report is three months, over a business quarter, to catch any idle users, and sporadic or time-scheduled services.

Figure 1: Generate a user and services report over a 3-month period
Reviewing the report and cross referencing it with the PowerShell script results will help you to have a better picture of legacy protocols in use, lowering the possibility of missing services or users that still have basic authentication protocols in play.
The Azure AD sign-in logs are another useful way to know your posture. Diving into the logs and filtering "Client app" can reveal sign-ins performed with legacy authentication clients.

Figure 2: Reveal sign-ins performed with legacy authentication clients
Just note that the Azure sign-in logs’ retention is up to 30 days and you may end up missing users and services if this is the only tactic used.
After carefully investigating and discovering all of the usage of basic authentication protocols, it is time to block them.
There are a few well-known approaches to blocking authentication protocols, a popular one being using the Conditional Access policies.
However, there are drawbacks to using Conditional Access as the first line of defense.
Conditional Access policies are processed post first-factor authentication. This means that the credentials can be compromised (as feedback will still be provided to the client, an advantage in a brute force attack for instance), so the mailbox might not have been breached but the attacker can try the validated password on other systems.
Start at the source. Microsoft has a dedicated feature for blocking basic authentication protocols, making it easy to control using the Admin console.
Go to the Office Admin center -> Settings -> Org Settings -> Modern authentication and uncheck all of the basic authentication protocols (make sure that modern authentication is checked). See Figure 3.

Figure 3: All basic authentication protocols are unchecked
Changing settings in the admin center creates a new authentication policy and sets it as the organization's default policy.
Use PowerShell to validate:
$default_policy = Get-OrganizationConfig | Select DefaultAuthenticationPolicy;
Get-AuthenticationPolicy $default_policy.DefaultAuthenticationPolicy;

You can set exceptions and assign different authentication policies to specific users using PowerShell commands:
New-AuthenticationPolicy -Name "Engineering Group" -AllowBasicAuthImap
Set-User -Identity <UserIdentity> -AuthenticationPolicy <PolicyIdentity>
This example creates a new authentication policy named Engineering Group that allows basic authentication with IMAP and assigns it to a user.
Authentication policies are a must but not enough to stop the threat risk of these legacy protocols alone. The authentication policy covers legacy clients, mailbox protocols such as IMAP and SMTP, and other clients such as PowerShell. However, like Conditional Access, even though the service is blocked, some clients will still provide feedback (allowing certain cyber attacks to succeed in gleaning a password for application in other SaaS apps). To avoid this incriminating feedback, completely turn off the service.
Shutting down a service can only be done for mailboxes, which covers six protocols out of the 13. Blocking the authentication policy covers the rest.
Disabling a mailbox service (or enabling in case of exclusion) can be done using the UI per user.
Go to the Office Admin center -> Users -> Active users -> select a user (with mailbox) -> Mail tab -> Manage email apps and uncheck the basic authentication protocols: POP, IMAP, SMTP. See figure 4.
Note that SMTP, MAPI over HTTP, and Mobile (Exchange ActiveSync) support both basic and modern authentication.

Figure 4. Basic authentication protocols are unchecked
There is no SMTP bulk edit multiple mailboxes (POP and IMAP bulk edit can be found in the classic Exchange Admin Center).
Transport config controls the entire Exchange organization, and one of its capabilities is to turn off the SMTP service (both basic and modern).
Use PowerShell command to disable SMTP globally.
Set-TransportConfig -SmtpClientAuthenticationDisabled $true
In order to block basic authentication protocols for all mailboxes or subset use Powershell cmdlets:
$Users = Get-CASMailbox -ResultSize unlimited
$Users | foreach {Set-CASMailbox -Identity $_ -SmtpClientAuthenticationDisabled $true -ActiveSyncEnabled $false -ImapEnabled $false -MapiEnabled $false -PopEnabled $false -OWAEnabled $false}
There are cases which you might consider to exclude and allow legacy protocols. For example, a manager who is using an older device or a script that was developed using the legacy protocols and now needs to be redeveloped might require an exclusion.
In these cases, it is strongly recommended to:
Managing SaaS configurations in an enterprise is complicated and this guide is meant to help ease the pain and smooth the transition from the M365 legacy protocols to a modern environment. The process has multiple steps and requires continuous oversight. From discovery of the legacy authentication protocols opened and used by users and business processes to blocking access and implementing and managing the exclusions, security teams need to dive in, remediate and manage every problematic use of the authentication protocol.
In large-scale environments, where changes always happen and configurations are in the thousands, it is recommended to manage SaaS misconfigurations with an automated SaaS Security Posture Management solution (SSPM).
Learn how an SSPM solution can automate this process for you.


It might sound dramatic to call ransomware a “scourge on business,” but the reality is that more companies are impacted every day. Some of these attacks hit the news cycle, but many don’t. As you look to protect yourself against the ever-burgeoning threat landscape, securing your Software-as-a-Service (SaaS) application stack is more important than ever.
You love your SaaS apps. They enable your business to support collaboration and offer better customer experiences. Unfortunately, threat actors love your SaaS apps just as much.
SaaS applications transmit and store a lot of sensitive data. Whether it’s your enterprise resource planning (ERP) or customer relationship management (CRM) solution or your organization's user directory and collaboration workspace, you’re putting a lot of sensitive information in the cloud.
And threat actors know this.
Most of the successful attacks on cloud services stem from misconfiguration, mismanagement and mistakes. Despite robust native controls, the configuration vulnerabilities are up to the company’s security team to monitor and protect. (I recount some of the top misconfiguration events where one seemingly innocuous configuration exposed the organization to massive repercussions here.)
In this blog, I’m going to take you through a SaaS ransomware attack and discuss the 3 steps to protect yourself from being a victim.
When threat actors decide to target your SaaS applications, they can use more basic to the more sophisticated methods. Similar to what Kevin Mitnick in his RansomCloud video, a traditional line of a business email account attack through a SaaS application follows this pattern:


This is a specific type of attack through SaaS, however, other malicious attacks through OAuth applications can occur in an organization’s environment.
With the multitude of SaaS apps global settings compounded by the amount of users and permissions for each app, it is near impossible to run manual, continuous monitoring and security checks for each and every SaaS in use. To further complicate matters, SaaS owners often do not sit within the security team but in the departments that most utilize the SaaS. This creates a situation where the security team has no visibility or control over the organization’s SaaS estate, leaving the playing field open for infiltration.
The first step to securing your SaaS ecosystem is to look for and remediate any misconfigurations that increase your risk of being the victim of a ransomware attack.
Many organizations don’t regularly review their SaaS configurations. For example, according to our 2021 SaaS Security Survey Report, while most companies are worried about their SaaS application security configurations, less than one third of companies consistently check them.
Among the types of misconfigurations, you should review regularly are:
(For more in depth information on important configurations to monitor, check out this blog.)
Another important aspect in misconfiguration monitoring is the dispersal of SaaS responsibility. One of the biggest challenges companies face when trying to secure their SaaS landscape is that the people in charge of security aren’t part of the security team.
According to our 2021 SaaS Security Survey Report, 52% of organizations delegate security setting management to the SaaS application owner. These owners sit outside the security department’s day-to-day activities, meaning that the security team may not know what’s going on.
Your security team should have a single location where everyone can collaborate and maintain governance of the entire SaaS estate. Not only for compliance purposes, but to ensure complete observability and protection for the company’s SaaS security posture.
Just because you can see something, doesn’t mean you’re really observing it. If you’ve ever stepped on a LEGO brick left on the floor, you know that someone saw it. However, no one observed it, meaning no one considered that painful middle-of-the-night walk to get a glass of water.
The same is true with SaaS misconfigurations. Even with the best dashboards, seeing doesn’t equate to deeply observing and correlating data. You need to really observe the potential security gaps in your SaaS landscape so that you can take meaningful, purposeful action.
Your team is in a race against cybercriminals, and you want to win - or at least limit the potential damage. The best way to prevent misconfigurations from leading to a ransomware attack vector is to identify and prioritize your remediation strategies.
While all misconfigurations can be a security weakness, not all are the same level of risk. Some of the highest priority remediation configurations to look to correct are:
(You can read up on other easily missed configurations in this blog.)
With the right automation, protecting yourself against these high-risk vulnerabilities doesn’t need to be burdensome.
Ransomware isn’t going anywhere. Even more stressful, cybercriminals work together and have a collective set of resources for trying to find new ways to exploit vulnerabilities.
With Adaptive Shield’s SaaS Security Posture Management (SSPM) platform, you can identify misconfigurations before they allow an attack, and automate the prioritization and remediation processes to prevent any misconfiguration issues.


August 24th, The Hacker News reported about a massive leak of 38 million records from upwards of a thousand web apps. These records included Microsoft’s own employee information (a.o. home addresses, social security numbers and vaccination status) which were left exposed online for anyone to find. Governmental bodies from places such as Maryland and New York City, as well as private companies such as American Airlines and Ford were said to also have been impacted.
Researchers from UpGuard found that the exposure came from a default permission setting on Microsoft's Power Apps platform. Power Apps is a Microsoft-powered development platform that enables individuals to build low-code business apps, for mobile and web use.
One of the options of Power Apps is to enable OData (Open Data Protocol) APIs for retrieving data from Power Apps lists. When an individual would enable the OData feed on the “OData Feed” list settings tab, they had to also activate the “Enable Table Permissions” option on the “General” list settings tab unless they wanted to make the OData feed public. This was due to the default configuration of disabled table permissions. Table permissions enabled, would in fact prevent anonymous data access, but lists ignore these permissions and any custom table permissions unless the individual would activate the table permissions for the list.

According to the Microsoft documentation: To secure a list, you must configure Table Permissions for the table for which records are being displayed and also set the Enable Table Permissions Boolean value on the list record to true.”

When the Table List configurations are not set correctly and the OData feed is enabled, anonymous users can access list data freely, leaving the company exposed.
As a result of the research and report made in June 2021, Microsoft has made changes to Power Apps portals such that table permissions are enabled by default.
This type of leak is not a one-off unfortunately, and as the amount of apps abound and compound with the amount of configurations, organizations need a better way to keep track and ensure SaaS app security.
SaaS Security Posture Management (SSPM) solutions have risen to the top of the cybersecurity dialogue, as SSPM automated solutions enable companies to continuously monitor and remediate all SaaS apps’ configurations, no matter how seemingly minor, and ensure the company is compliant with industry standards and internal policies.
An SSPM solution alerts an organization when misconfigurations leave them exposed, and helps to prevent the next leak or breach.


On the surface, Salesforce seems like a classic Software-as-a-Service (SaaS) platform. Someone might even argue that Salesforce invented the SaaS market. However, the more people work with the full offering of Salesforce, the more they realize that it goes beyond a traditional SaaS platform’s capabilities. For example, few people talk about managing the security aspects of Salesforce Release Updates. By understanding what Release Updates are, why they pose a security risk, and how security teams can mitigate risk, Salesforce customers can better protect sensitive information.
Since Salesforce does not automatically update its platform, it does not follow the traditional SaaS model. For example, most SaaS platforms have two types of releases, security and product improvements. Urgent security updates are released as soon as a security vulnerability is known, and product improvements are released on fixed dates, such as quarterly or monthly. As part of the SaaS model, the vendor automatically updates the platform.
The update and patching policy benefits the customer and the SaaS provider. The customers don’t need to worry about updating the system so they can focus on the core aspects of their business. Meanwhile, the SaaS provider does not need to develop multiple update versions or worry about the most recent version installed by the customer.
Better yet, the SaaS provider does not need to worry that customers will experience a security breach because it automatically installs the security patch for everyone. It just makes everyone's life easier, and is one of the reasons that SaaS platforms are immensely popular.
Salesforce works differently, very differently. They use a hybrid system that is similar in some ways to traditional software that requires the customer to apply updates until EOL and a modern SaaS platform. Salesforce offers regular seasonal service updates and security updates as needed. However, neither update is implemented automatically.
Salesforce gives admins a “grace period” where they can choose to update the platform. At the end of this period, Salesforce pushed the update through automatically.
For example, Salesforce introduced the Enforce OAuth Scope for Lightning Apps security update in Summer 2021. The provider recommends that organizations apply it by September 2021. However, Salesforce will not enforce it until Winter 2022. This is an important security update, but customers do not need to install it immediately.
While Salesforce encourages admins to run through a checklist and apply the updates, it realizes that customers rely on the platform’s flexibility and that changes can impact the customizations, like custom developments and integrations.
Since any update can be catastrophic for an organization, Salesforce gives customers time to review the update’s content and prepare the organization's Salesforce before activating the changes.
The Salesforce Security Updates are, as the name suggests, for security purposes. They are published to fix a security issue, prevent attacks, and strengthen the security posture of a Salesforce tenant. Therefore, customers should install them as soon as possible.
Once Salesforce publishes an update, the vulnerability it is patching becomes general knowledge. This knowledge means the weakness is equal to a common vulnerability or exposure (CVE) but without the assigned number. Bad actors can easily get access to all the information regarding the exposure and create an attack vector that utilizes the published vulnerability. This places all organizations that have not enforced the security update vulnerable to an attack.
Since most attacks are based on known, published, 1-day vulnerabilities, waiting to apply the update creates a data breach risk. All bad actors use 1-day attacks, from script kids to professional ransomware hackers since weaponizing them is much easier than looking for an unknown vulnerability. Most bad actors look for low-hanging fruits - organizations without updated software or that have lax security.
This is why security professionals call the period from vulnerability until the organization enforcing a security update the golden window for attacks. For that reason, it is critical to update all software to the latest stable version and install security updates as soon as possible.
This is not just a hypothetical or interesting story. In October of 2020, security researcher Aaron Costello discovered that access control permission settings in Salesforce may allow unauthenticated users ("guest users") to access more information than intended by using cumulative weaknesses in Salesforce including
Salesforce suggested security measures for guest users, objects, and APIs, while also pushing Security Updates in the following Winter ‘21 and Spring ‘21 releases. Among the Security Updates were Remove View All Users Permission from Guest User Profiles and Reduce Object Permissions for Guest Users.
Both suggestions directly address the security threat’s root cause. Problematically, this was too little too late because bad actors had known about the vulnerability since October 2020. By the time Salesforce pushed the updates to the different tenants, the admins needed to manually activate the updates. This means that a customer might have been at risk for anywhere from 6 - 9 months before fixing the vulnerability themselves.
While Salesforce provides value to organizations, its approach to managing security updates makes it a unique type of SaaS. Additionally, it is an extremely complex system, with thousands of configurations. While many don’t seem important to security, they can actually impact a Salesforce tenant’s posture.
Therefore, the CISO or security team need to be involved more than they normally would when managing Salesforce. They need to:
Fortunately, the category of SaaS Security Posture Management (SSPM) tools address these tasks, and Adaptive Shield is a market-leading solution in this category to enable optimal SaaS security posture automatically.
Adaptive Shield understands the complexity of securing Salesforce, among many other SaaS platforms, as Adaptive Shield provides an enterprise’s security teams complete control of their organizations' SaaS apps with visibility, detailed insights and remediation across all SaaS apps.
The platform helps Salesforce admins, CISOs, and security teams track and monitor the settings and configuration updates with security checks that ensure that the Salesforce tenant is configured and secured properly. This includes monitoring permissions, “@AuraEnabled” methods, API security, and authentication.
Adaptive Shield also provides clear priority-based mitigation information so admins and security teams can swiftly secure the Salesforce tenant to maintain a strong security posture. The Adaptive Shield platform makes the task of securing a Salesforce tenant from cumbersome, complex, and time-consuming — to an easy, clear, quick, and manageable experience. This prevents such vulnerabilities as the example above by breaking the chain of misconfigurations and unenforced updates.
Find out more about how to prevent misconfiguration risks in your Salesforce tenent
This was first published on August 5, 2021 in The Hacker News.


In response to malicious actors targeting US federal IT systems and their supply chain, the President released the “Executive Order on Improving the Nation’s Cybersecurity (Executive Order).” Although directed at Federal departments and agencies, the Executive Order will likely have a ripple effect through the Federal technology supply stream. Private companies and enterprises will look to the Executive Order to build their best practices. At a high level, the Executive Order includes information sharing requirements, a push toward cloud and Zero Trust architectures, and enhancing transparency throughout the software supply chain.
The bulk of the Executive Order focuses on administrative tasks associated with it, including redefining contract language, setting timelines, and defining agency roles and responsibilities. For enterprises that don’t supply technology to the federal government, the Executive Order may feel unimportant. In reality, several of the basic tenets could be used by companies operating outside the federal IT supply chain, including:
The text of the Executive Order is long and comes with all the regulatory jargon associated with a law. Breaking it down into bite size chunks gives a good overview, though.
The short, succinct point of this one is that “everyone needs to play nicely and stop hiding behind contracts.” In a nutshell, the Executive Order looks to create a more meaningful information sharing opportunity for agencies and vendors when threat actors find and exploit a vulnerability.
Although this one mostly speaks for itself, the requirements in the Executive Order created a bit of a panic across the federal space because a lot of the timelines are super short. For example, within 60 days, federal agencies need to:
Finally, within 180 days, they all need to adopt multi-factor authentication (MFA) and encryption both at-rest and in-transit. With agencies adopting Software-as-a-Service (SaaS) applications to modernize their IT stacks, identity and access control configurations, including multi-factor authentication, act as a primary risk mitigation strategy.
Without even needing to list the recent supply chain hacks and breaches, this is the least surprising of all the requirements. Surprising very few people, this section includes several key bullet points:
For agencies, this is going to take a bit of work. For enterprises, this is likely a harbinger of things to come. The problem is that while the Executive Order is a great start, the two primary requirements for putting Zero Trust into effect, MFA and encryption, don’t really close all cloud security gaps.
According to the 2021 Data Breach Investigations Report (DBIR) misconfigurations remain a primary threat vector for cloud architectures. The increased use of Software-as-a-Service (SaaS) applications actually trigger two different attack patterns:
According to the DBIR, the basic web application attacks include things like credential theft and brute force attacks. Meanwhile, the Miscellaneous Errors subset also included things like cloud-based file storage being placed onto the internet with no controls. These attack vectors show the importance of SaaS security management to cloud security as a whole. Many enterprises lack visibility into their configurations, and the proliferation of SaaS applications makes manual configuration monitoring nearly impossible. As enterprises continue on their digital transformation journey, configuration monitoring and management will only become more difficult.
Cloud security, even with a focus on establishing a Zero Trust Architecture, needs to incorporate SaaS application security. As agencies and enterprises in their supply chain incorporate SaaS apps, the security risk that misconfigurations pose needs to be addressed.
As agencies and enterprises start looking for solutions, enhancing SaaS security should be on the “proactive steps to take” list.
Doing the business of your business requires a lot of applications, especially across remote workforces. Despite a potentially long purchase cycle, adding applications to your stack is relatively easy. Your IT team creates some connections to your cloud infrastructure using APIs, then adds the users. People can get down to business.
Managing SaaS app security for the long term is the big challenge. You have a lot of applications, and each one has unique configurations and language. No organization can have an expert in every application language and configuration. If you can integrate all your applications into a single platform that creates a standardized approach to configurations, you’re taking the first step down the long and winding road to securing your cloud infrastructure.
While Journey might say “don’t stop believin,’” a Zero Trust Architecture means not believing anyone or anything until they provide the right proof. For example, MFA doesn’t work on a system that uses legacy authentication protocols like IMAP and POP3. If you need to secure your SaaS stack and meet these short timelines, you need visibility into all user access, especially Privileged Access holders like super admins or service accounts.
Enterprises need unified policies across all SaaS applications, ensuring continuous compliance. This means the ability to analyze every user’s access across all your SaaS platforms by role, privilege, risk level, and platform with the ability to mix and match as you search so you have the insights you need, when you need them.
The hardest part of SaaS security is that it continuously changes, like employees sharing documents with third-parties or adding new non-company users to collaboration platforms. The problem is that the Executive Order and most other compliance mandates assume that you oughta know about your risk posture because you’re continuously monitoring your security.
You need always-on SaaS security that provides real-time risk identification, context-based alerts, and risk prioritization.
No single human being can manage SaaS security manually.
Manually managing the risks arising from so many users, so many applications, and so many locations will leave the IT department running on espresso and energy drinks and unfortunately, most likely, missing a critical risk.
Automating the SaaS security process in a single cloud-based platform is the most efficient way to manage the process. SaaS platform management solutions meet your security where it lives, in the cloud, so you can automate your security at cloud-speed, reduce risk, and strengthen your security and compliance posture.
Adaptive Shield provides full visibility into one of the most complex issues in cloud security. This SaaS security posture management solution enables enterprises to continuously monitor for misconfiguration risks across the SaaS estate: from configurations that cover malware, spam and phishing to suspicious behavior, and incorrectly configured user permissions.
Adaptive Shield aligns technical controls with CIS Benchmarks and can map controls’ compliance to NIST 800-53 as well as other frameworks.
The Adaptive Shield SaaS security platform management solution also natively connects with Single-Sign On (SSO) solutions, like Azure, Ping and Okta, to help track MFA use across the organization.
With SaaS applications becoming the rule rather than the exception for modern businesses, cloud security relies on continuously monitoring for risky SaaS misconfigurations.
Find out more about how to prevent misconfiguration risks in your SaaS app estate
This was first published on June 14, 2021 in The Hacker News.


The data is in. According to IBM Security’s 2020 Cost of a Data Breach Report, there is a 50% increase in cloud usage for enterprises across all industries. The number of threats targeting cloud services, predominantly collaboration services like Office 365, has increased 630%. Moreover, 75% of respondents report that discovery and recovery time from data breaches has significantly increased due to remote work during the pandemic. Although organizations can save over $1 million if they discover a breach in the first 30 days, the average reported response time was a whopping 280 days.
In the remote-work world, SaaS apps have become an enticing vector-of-choice for bad actors. Just think of the typical employee, working off-site, untrained in security measures, and how their access or privileges increase the risk of sensitive data being stolen, exposed, or compromised. However, it doesn’t have to be that way — a company’s SaaS security posture can be strengthened and SaaS configuration weaknesses can be avoided. SaaS Security Posture Management (SSPM), as defined by Gartner, is critical to the security of today’s enterprise.
As Gartner’s own Tom Croll asserts in 3 Steps to Gartner’s SaaS Security Framework (December 2020):
“Increasingly, business-critical data is being processed by applications that exist entirely outside the corporate network, making traditional controls ineffective. New controls are needed to address these new realities,” He continues, “SSPM tools allow enhanced controls to further protect data stored in the most commonly used SaaS applications. Core capabilities include monitoring the configuration of native SaaS security settings, reporting non-compliance and auto-remediating violations to maintain alignment with multiple compliance frameworks.”
There are many offerings in cloud security, but the SSPM solution is the only one that assesses the company’s SaaS security posture in a customized and automated manner, tailored to the specifications of each application and to company policy. And it's not a one-time assessment — it is an ongoing process that monitors and reinforces the company’s SaaS security.
Yet this foundational security step is often overlooked, for a variety of reasons. Many people don’t realize that there are two sides to securing company SaaS apps. While SaaS providers build in a host of security features designed to protect company and user data, it is ultimately beyond their control. Just as in any other part of the network, the IT or security team is responsible for protecting and managing the data, configurations, user roles, and privileges, regardless of their location.
For enterprise organizations, ensuring that all the SaaS apps are configured properly and have the correct user roles and privileges is not only a never-ending, time-consuming endeavor but an impossible one.
Dynamic and ever-changing — The SaaS environment is dynamic and continually updating. As employees are added or removed and new apps onboarded, permissions and configuration must be reset, changed, and updated. In addition, continuous, compliance updates and security configurations are needed to meet industry standards and best practices (NIST, MITRE, etc.), and security teams need to continuously ensure that all the configurations are enforced company-wide, no exceptions. With a typical enterprise having an average of 288 SaaS applications, this involves hours of continuous work and effort and is not sustainable.
Each app is a world unto itself — Each SaaS application has its own security configurations for compliance, like which files can be shared, whether MFA is required, whether recording is allowed in video conferencing, and more. The security team has to learn each application’s specific set of rules and configurations and ensure they are compliant with their company’s policies. As they are not the ones using the apps on a daily basis, they are rarely familiar with the settings, making it even harder to optimize the configuration.
Configuration management overload — The number of apps, configurations, user roles, and privileges that an organization needs to manage and monitor grows with every onboarded app. If you break it down into numbers, a typical enterprise has hundreds of SaaS apps. Each app has up to hundreds of global settings, not to mention enterprises that have thousands to tens (even hundreds) of thousands of employees. Security teams have to learn hundreds of app setups and monitor thousands of settings and tens of thousands of user roles and privileges — an impossible and unsustainable scenario.
No clear visibility or direct management— Most SaaS apps are purchased and implemented in the departments that utilize them most, for example, an automation SaaS solution generally sits in marketing, a CRM in sales, and cloud computing, productivity and collaboration tools in IT. These SaaS apps hold critical data on the company’s clientele and business projects. The SaaS owners are often not trained in security or vigilant in the continuous needs of configuration and posture. The security team ends up being in the dark about the security protocols in place and more importantly, are not focused on the exposure or risk.
In the remote-work world, organizations are even more vulnerable to SaaS security configuration weaknesses. Luckily, security teams can now turn to SSPM solutions like Adaptive Shield, to automate their SaaS security processes and address the challenges detailed above.
In business-critical apps, such as Salesforce, Office 365, G-Suite, and Zoom, the right SSPM solution can provide deep visibility and remediation for potential vulnerabilities in a company’s SaaS security posture, from misconfigurations and misappropriated privileges to suspicious SaaS usage. They are also adept at following the trail of policy changes and violations, making it possible to identify the source of accidental, intentional, or malicious alterations. These SSPMs are built to streamline and improve the security team’s efficiency, reducing their workload and stress, while increasing protection from potential exposures or breaches.
With no-code technology, Adaptive Shield enables security teams to easily see, monitor, and remediate all their company’s SaaS (mis)configuration and user role information for an endless array of SaaS apps: from video conferencing platforms, customer support tools, HR management systems, dashboards and workspaces to content, file-sharing applications, messaging applications, marketing platforms, and more.
Learn more about how Adaptive Shield prevents misconfigurations and vulnerabilities in your SaaS estate that could lead to a leak or breach.
This post was first published in The Hacker News on April 5, 2021.


When I want to know the most recently published best practices in cyber security, I visit The National Institute of Standards and Technology (NIST). From the latest password requirements (NIST 800-63) to IoT security for manufacturers (NISTIR 8259), NIST is always the starting point. NIST plays a key role as a US standard-setter, due to the organization’s professionalism and the external experts who help to create NIST documents.
The NIST Cybersecurity Framework (CSF) was initially released in 2014 and last updated in 2018. The Framework enables organizations to improve the security and resilience of critical infrastructure with a well-planned and easy to use framework.
The continuing growth in SaaS, and the major changes to the work environment due to COVID-19 bring new security challenges. Although the CSF was written and updated while SaaS was on the rise, it is still geared towards the classic legacy critical infrastructure security challenges. However, by adapting the CSF to modern, SaaS-based work environments, organizations can better respond to new risks.
I personally love this Framework, but truth be told, when one reads the Framework in-depth, its complexity is apparent, and following it can be difficult. This article will review the CSF’s key elements, point out its key merits, and suggest implementations for SaaS security.
The NIST CSF lays out five functions of security, then splits them into categories and subcategories. The subcategories contain the actual controls. For each subcategory, the CSF includes a list of cross-references to well known standards and frameworks such as ISO 27001, COBIT, NIST SP 800-53, and ANSI/ISA-62443.
These cross-references help organizations implement the CSF and map it to other frameworks. For example, security managers or other team members can use the references to justify their decisions no matter what security standard the company needs to comply with.
In a single document, the Framework combines a host of approaches to dealing with cyber security threats. This includes:
The framework has a five stage core structure: Identify, Protect, Detect, Respond and Recover. I’m going to break them down into bullets for you.

NIST defines this function as follows: "Develop the organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities". Within this function, NIST includes the following control categories:
NIST defines this function as follows: "Develop and implement the appropriate safeguards to ensure delivery of critical infrastructure services". Within this function, NIST includes the following control categories:
NIST defines this function as follows: "Develop and implement the appropriate activities to identify the occurrence of a cybersecurity event". Within this function, NIST includes the following control categories:
NIST defines this function as follows: "Develop and implement the appropriate activities to take action regarding a detected cybersecurity event". Within this function, NIST includes the following control categories:
NIST defines this function as follows: "Develop and implement the appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity event". Within this function, NIST includes the following control categories:
While definitely a model in best practices, the Framework is a challenge to implement.
A company using SaaS services may wonder how this is relevant for them. They may think that compliance is the SaaS provider’s responsibility. However, a deeper look into it shows that many SaaS providers have security measures in place, and the user is responsible for using them.
For example, admins should not allow any connections via HTTP to a SaaS service. They should only allow secure, HTTPS, connections.
This may seem like a small subcategory, but underneath there is a behemoth. Data leaks are extremely difficult to prevent. SaaS application adoption makes this harder because people can share and access them from anywhere in the world.
An admin or member of the CISO office should take special care of this threat. DLP in SaaS can include security measures such as:
As an enterprise scales its workforce and SaaS adoption, this subcategory becomes more challenging. Managing 50,000 users over just five SaaS means that the security team needs to manage 250,000 identities. This problem is real and complicated.
Even more challenging, each SaaS has a different way to define identities, view them, and secure identities. Adding to the risk, SaaS applications don’t always integrate with each other which means users can find themselves with different privileges across different systems. This then leads to unnecessary privileges that can create a potential security risk.
The NIST CSF is an industry standard for cybersecurity today, yet to implement it with typical manual practices and processes is an uphill battle. So why not automate?
Adaptive Shield is a SaaS Security Posture Management (SSPM) solution which can automate the compliance and configuration checks across the SaaS estate. Adaptive Shield enables security teams to easily see and fix configuration weaknesses quickly, ensuring compliance with company and industry standards, from NIST CSF, as well as other compliance mandates such as SOC 2 and the CSA Cloud Controls Matrix.
To learn more about extending automated visibility and control across your SaaS applications, speak to our experts today.


Remember when cybersecurity was mostly about firewalls, VPNs, and antivirus software? Those days are long gone. Now one of the most prevalent places for exploitation has to do with misconfigurations found in an organization's SaaS apps.
If you are in IT, you might have come across the following scenario: an admin of a business-critical SaaS app adds every user as an admin. Or they have used their admin privileges to turn off MFA because it’s too annoying and disrupts the workflow.
A recently published report found that 68% of enterprises consider cloud platform misconfigurations as the biggest threat to their cloud security. Another research from Cloud Security Alliance, 2021 State of Cloud Security, indicates that security misconfigurations are the main contributor for 22% of security incidents, second only to cloud provider issues (26%).
The list of possible misconfigurations, whether intentional or by mistake, can be endless. And unfortunately, these SaaS misconfigurations can lead to severe repercussions.
There are some exploited misconfigurations that are being used time and time again. Here are five examples from real-world attacks.
In May 2019, Salesforce self-sabotaged its security parameters by breaching itself. A scheduled update on Salesforce’s development systems disrupted the access permissions settings, giving employees of the organizations using the platform full access to Salesforce’s data.
The error not only allowed external users access to view or read sensitive information but also to ‘write’ permissions.
Salesforce fixed the error in access security controls but at the same time, accidentally created one of the biggest outages in the company’s history to take down access to 100 cloud instances.
60% of Microsoft Office 365 and G Suite tenants have been targeted with IMAP-based password-spraying attacks, according to researchers. The attackers target the legacy and insecure IMAP protocol to bypass MFA settings and compromise cloud-based accounts providing access to SaaS apps. It’s reported that Citrix was one such target in an ironic twist as they specialize in federated architectures, yet the FBI suggested that the attackers gained a foothold with password spraying and then bypassed additional layers of security.
The use of legacy protocols such as POP or IMAP, make it difficult for system administrators to set up and activate MFA. “Attacks against Office 365 and G Suite cloud accounts using IMAP are difficult to protect against with multi-factor authentication, where service accounts and shared mailboxes are notably vulnerable,” researchers say.
Security researcher Avinash Jain found a single security misconfiguration in the JIRA collaboration tool that opened up many Fortune 500 companies as well as NASA to a potential leak of corporate data and personal information. This information disclosure was the result of an authorization misconfiguration in Jira’s Global Permissions settings.
When the filters and dashboards for the projects/issues are created in JIRA, then by default the visibility was set to “All users” and “Everyone” respectively. Instead of sharing roadmap tasks etc. internally, it shared them publicly.
In March 2019, several companies unwittingly exposed sensitive corporate and customer data when their employees shared public links to files in their Box enterprise storage accounts.
Although data stored in Box enterprise accounts are private by default, users can share files and folders with anyone — if this user role configuration is enabled. The public sharing allows the any employee in the company to make the company’s data publicly accessible with a single click.
Security firm Adversis found that others outside an enterprise network can also discover these links. According to Adversis, Box admins should have reconfigured the default access for shared links to “people in your company” to reduce accidental exposure of data to the public.
This misconfiguration allowed Box users to expose a multitude of private information like passport photos, bank account and Social Security numbers, passwords, employee lists, financial data, invoices, and receipts.
There is a global setting in Zoom for the company to configure what happens when meetings are recorded. Can they be downloaded locally or only in the company’s protected cloud? Do they need a password or can they be saves without?
According to former NSA researcher Patrick Jackson, thousands of private Zoom recordings were exposed online when many recordings stored in Amazon Web Services (AWS) S3 buckets without passwords were found. The private videos ranged from elementary school remote classes, featuring the faces of students, to private therapy sessions, and business meetings including financial details.
The global setting to enforce password protection for recordings was critical in keeping these videos safer.
The absence of strong SaaS specific security measures allows attackers to take advantage — companies need deep visibility into their SaaS estate to monitor all settings, user permissions and configurations.
There are many solutions in cloud security, but the new category of SaaS Security Posture Management (SSPM), can assess a company’s SaaS security posture in a customized and automated manner that is tailored to the specifications of each application and aligns with company policy. And it’s not a one-time assessment; it is a continuous process that monitors and reinforces the company’s SaaS security.
The right SSPM solution, like Adaptive Shield, provides deep visibility and remediation for potential vulnerabilities in a company’s SaaS security posture, from misconfigurations and misappropriated privileges to suspicious SaaS usage. SSPMs are built to streamline and improve the security team’s efficiency, reducing their workload and stress while increasing protection for the company against any potential exposure or breach..
Now is the time to gauge your current SaaS security strength and to find out how to fortify your enterprise’s SaaS security posture.
This was first published in InfoSecurity Magazine on May 20, 2021.


It’s never quiet in the era of cybercrime — and becoming the more common vector for bad actors and infiltration is within the company’s SaaS security posture.
With the SaaS market growing at 30% per year and with Deloitte and others predicting that post-covid, the SaaS model will be even more widespread, it is safe to say that SaaS configuration weakness will be all the more exploited. One only has to consider the typical employee, untrained in security measures, and how their access or privileges increase the risk of sensitive data being stolen, exposed, or compromised. SaaS Security Posture Management (SSPM), as defined by Gartner, is critical to the security of today’s enterprise.
I like to refer to this as the BIG misunderstanding. Many don’t realize that there are two sides to securing company SaaS apps. While SaaS providers build in a host of security features designed to protect company and user data, it is ultimately beyond their control. Just as in any other part of the network, the IT or security team are the ones responsible for protecting and managing the data, configurations, user roles and privileges, regardless of their location.
For enterprise organizations, ensuring that all the SaaS apps are configured properly and have the correct user roles and privileges is not only a never-ending, time-consuming endeavor, but an impossible one.
Here is a rundown of the main issues security teams face that make SaaS security complex, laborious and just...hard.
Organizations vulnerable to SaaS security configuration weakness can now turn to solutions that automate their SaaS security posture.
As Gartner’s own Tom Croll asserts in 3 Steps to Gartner’s SaaS Security Framework (Dec 2020):
“Increasingly, business-critical data is being processed by applications that exist entirely outside the corporate network, making traditional controls ineffective. New controls are needed to address these new realities.
SSPM tools allow enhanced controls to further protect data stored in the most commonly used SaaS applications. Core capabilities include monitoring the configuration of native SaaS security settings, reporting non-compliance and auto-remediating violations to maintain alignment with multiple compliance frameworks.”
There are many solutions in cloud security, yet it’s only the SSPM solution that assesses the company’s SaaS security posture in a customized and automated manner, tailored to the specifications of each application and company policy. And it's not a one-time assessment; it is a continuous process that monitors and reinforces the company’s SaaS security.
The right SSPM solution, like Adaptive Shield, can provide deep visibility and remediation for potential vulnerabilities in a company’s SaaS security posture, from misconfigurations and misappropriated privileges to suspicious SaaS usage. SSPMs are built to streamline and improve the security team’s efficiency, reducing their workload and stress, while increasing protection for the company against any potential exposure or breach.
This was first published in Security Boulevard on March 12, 2021.


In the era of hacking and malicious actors, a company's cloud security posture is a concern that preoccupies most, if not all, organizations.
Yet even more than that, it is the SaaS Security Posture Management (SSPM) that is critical to today's company security. Recently Malwarebytes released a statement on how they were targeted by Nation-State Actors implicated in SolarWinds breach. Their investigation suggested abuse of privileged access to Microsoft Office 365 and Azure environments.
Often left unsecured, it's SaaS setting errors like misconfigurations, inadequate legacy protocols, insufficient identity checks, credential access, and key management that leave companies open to account hijacking, insider threats, and other types of leaks or breaches in the organization.
Gartner has defined the SaaS Security Posture Management (SSPM) category in 2020's Gartner Hype Cycle for Cloud Security as solutions that continuously assess the security risk and manage SaaS applications' security posture. Many don't realize that there are two sides to securing company SaaS apps.
While SaaS providers build in a host of security features designed to protect the company and user data, potential vulnerabilities and configuration weakness still arise stemming from the company's management of those configurations and user roles.
At best, security teams spend their days manually checking and fixing setting after setting, only needing to go back and do it all again when there are software updates, new users added or new apps onboarded. At worst, organizations turn a blind eye to the threats they are exposed to and operate in ignorance -- unable to protect themselves from what they cannot see.
The right SSPM solution can provide visibility, detection, and remediation for the company's SaaS security posture and save security teams a significant amount of time, reduce workload and stress. Clearly, the right SSPM solution cannot come fast enough.
SSPM solutions, like Adaptive Shield, provide proactive, continuous, automated surveillance of all SaaS applications. With a built-in knowledge base to ensure the highest level of SaaS security available today, Adaptive Shield is set up for security teams to easily and intuitively use -- and it takes just five minutes to deploy.

The reality is that the company is only as safe as the weakest SaaS security configuration or user role. And the possibility that there are SaaS configuration errors and misappropriated user roles and privileges is high.
To mitigate the risks, get more information on how to ensure your company's SaaS security.
This was first published in The Hacker News.


If you’re a security professional, by now, you've already heard about the epic Solorigate or Sunburst breach.
The massive hack was exposed in mid-December 2020 (ah 2020; the “gift” that just keeps on giving…) and compromised numerous high-profile companies and government organizations. Security giant FireEye first discovered the widespread breach which resulted in obtaining code developed by the company’s Red Team to simulate cyber attacks, as well as breaching and exfiltrating data from many other organizations.
While this sophisticated, multi-stage breach is still under investigation, federal institutions along with the international cybersecurity community already have a pretty good idea about how this breach occurred; in a nutshell, the adversary (allegedly a nation-state actor) managed to first submit malicious source code into Solarwinds Orion product suite, one of the most prevalent IT monitoring solutions. The malicious code created a backdoor inside that product and once installed in a customer network, the compromised server contacted its command and control center in order to receive instructions. These instructions were capable of privilege escalation, downloading and executing payloads, moving laterally throughout the network, and compromising other assets.
The topics of how exactly Sunburst/Solorigate spread across networks and how organizations can detect it have already been covered in many great articles (here’s Microsoft analysis and recommendations). In this article, we are going to touch upon the root-cause for Solorigate to provide infosec and corporate security teams some practical recommendations on how they can better secure their source code management platforms.
Traditionally, source code management platforms are owned and managed day-to-day by development teams and the reality is that security aspects and controls are, at times, deprioritized. This breach serves as a painful eye-opener -- corporate security teams must take a stand and emphasize the critical nature of security with their respective counterparts--and then, make sure they do everything possible to harden and secure their source code and version control platforms.
Version control platforms have greatly matured in recent years and now natively offer many controls which can be easily implemented and don’t require any additional tools. For the purpose of this article, we’ve used controls available in GitHub and its respective terminology, since this is one of the most prevalent source code platforms. Nevertheless, most of these controls are also available in some shape or form in other products.
Aside from the immediate impact Solorigate has had on many organizations, as well as the tremendous efforts that are being made to identify and recover from this breach, we truly believe that this a learning opportunity; as Winston Churchill said, “Never let a good crisis go to waste.”
While most organizations face far less sophisticated attacks than nation-state backed ones, attacks are always growing more complex and advanced. This is why it’s critical to get back to the basics, such as applying preventive security measures, hardening all sensitive platforms, and continuously monitoring them, to reduce the chances of getting breached. And while we’ve only examined one facet of the Solorigate breach and a single attack vector out of many, we should all take this opportunity to do what we can to contain the blast radius of such breaches, if and when they occur.
Check out how Adaptive Shield can help you protect your SaaS apps using continuous monitoring of their configurations.


Airports are among the most secure buildings in the world. Whether it’s London’s Heathrow, The Windy City’s O'Hare, or any other airport across the globe, what’s certain is that they deploy an impressive array of scanning equipment, facial recognition tools, physical security teams, and artificial intelligence systems to keep operations flowing smoothly and prevent threats.
But the real foundation to airport security is the architectural design of the building itself and protocols that are in place. The most sophisticated scanners and the most diligent TSA agents are totally worthless if people who aren't scheduled to fly are granted direct access to the departure gates. Or if the service corridors for staff are accessible to shoppers in the duty free section.
Now imagine having to secure multiple airports simultaneously, where the people inside may be both pilots and passengers of different airlines. And then--and hear me out on this--imagine that all the corridors, walls, and stairways are constantly shifting in relation to each other (think Heathrow meets Hogwarts!). Gate 22 used to be in this hallway--but now, without a moment’s notice, it’s in a different terminal; The emergency exit should obviously be closed at all times--but suddenly, all the passengers are using it freely. In this confusing scenario, the carefully designed management protocols have been broken down, eventually creating a situation in which anyone can access whatever area they choose.
Similar to those magically-shifting airport corridors, both admins and regular users can intentionally or unintentionally make major/minor changes to settings which end up enabling risky permissions or disabling key security features.
Despite each application’s countless security and user-related settings, with the addition of custom code, configurations, integrations, 3rd party users and apps, there’s a lot of room for things to go wrong. And so, it should come as no surprise that a leading cause of security incidents in SaaS applications is due to misconfigurations on the part of the organization using the platform--not due to security weaknesses in the platform itself.
For example:
Like the most bustling airports in the world, SaaS environments are inherently chaotic and fragmented. But with the proper toolset, specifically developed to address the unique management challenges of the SaaS application space, security teams can proactively take charge of their landscape.
What’s your current SaaS security posture? Find out today!


Enterprises depend on SaaS applications for countless functions, like collaboration, marketing, file sharing and more. But problematically, they often lack the resources to configure those apps to prevent cyberattacks, data exfiltration, and other risks.
Catastrophic and costly data breaches result from SaaS security configuration errors. The Verizon 2020 Data Breach Investigations Report found that errors are the second largest cause of data breaches, accounting for about one in three breaches. Of those, misconfigurations are by far the most common, which often result in the exposure of databases or file system contents directly on a cloud service.
Businesses tend to be as vulnerable as the weakest security settings they have enabled for their SaaS applications. To illustrate, Adaptive Shield’s team has discovered SaaS setting errors that leave companies open to one-click corporate espionage, exposing their entire cloud, along with massive amounts of video conferencing data in this new WFH era.
IT security teams must do more to protect their organizations from risks caused by poorly configured SaaS apps. Here are five SaaS configuration errors we see all the time that you should be checking on and correcting as needed.
Although SaaS platforms have dozens or even hundreds of built-in security configuration controls, it is the responsibility of the client to set them correctly. Security teams are overwhelmed trying to manage thousands of settings across all their apps.
Adaptive Shield analyzes, identifies, and prioritizes weaknesses in SaaS applications and provides ongoing monitoring, to enable continuous security for all global settings and user privileges. Adaptive Shield solves SaaS misconfiguration challenges like the ones listed above and thousands more by providing automated, complete control of SaaS application security.
Our mission is to give security teams one common platform to effortlessly manage their SaaS app security. Want to learn more about what we do and how we can help your organization use SaaS applications with greater confidence? Visit us at https://www.adaptive-shield.com/.


SaaS vendors are continuously improving their native security controls, with the intention of preventing misconfigurations that can lead to dangerous consequences. In practicality, this means that if a SaaS provider has reason to believe a user’s mailbox has been hacked, the user will receive an alert directly to their inbox notifying them of the suspicious activity.
While this approach works well when there’s a user associated with said mailbox, what happens if a mailbox doesn't have an owner? Or what if the user attached to this mailbox has no license? In such cases, no one ever gets those alerts.
At first glance, this might not seem like a problem; if there’s no owner and no licence, then there’s no actual risk, right? Unfortunately, this isn't the case. In every enterprise, there are hundreds of mailboxes that fit these exact criteria. Yet these same mailboxes often contain valuable information, such as financial data, intellectual property, business information, security events, and more.
There are various reasons an email account may not be associated with one particular user. One common example is that of shared mailboxes, often used in organizations to provide multiple users with access to the same emails. Shared mailboxes are commonly used in departments such as accounts receivable, the SOC, and customer support, where multiple people need to operate the same mailbox. At Adaptive Shield, we see approximately one shared mailbox per every 20 employees, making this a relatively common phenomenon. In general, shared mailboxes have no specific owner and there is no licence--and very often, these mailboxes are used to send and receive emails containing highly sensitive data.
Threat actors are constantly looking for mailboxes to take over, either for spam-related activities, or to launch highly convincing BEC (Business Email Compromise) scams that can eventually lead to destructive financial outcomes. Shared mailboxes present attackers with an easy entry point into organizations and usually have the following inherent problems:
Add enabled legacy protocols to the mix, and you’ve got a great recipe for a long standing take-over campaign.
Auditing is not enabled by default. You’ll need to change this configuration to detect who can access another user’s mailbox.
Keep in mind that admins are always adding members to shared mailboxes, and as such, it’s highly recommended to enable this setting. There are several measures you can take to reduce your attack surface and prevent breaches in the first place, as well as to adopt a defense-in-depth approach, in case such breaches have already occurred. While the first logical step would be to disable access for all users, there are many instances where this simply isn't practical. Below, we’ll define a more user-friendly approach that still provides access to these mailboxes while strengthening security posture.
To start, in Office 365, it is possible to login to a shared mailbox, as every shared mailbox has a corresponding user account. The obvious solution to prevent this would be to enable multi-factor authentication--but in this case, that’s not an option because the user has no license. If you try to access the mailbox through the UI, you won’t see much. But using authentication methods such as IMAP, EWS, etc, will allow you to access all emails within the shared mailbox.
Microsoft recommends blocking sign-in for the shared mailbox account; According to their documentation, “The account has a password, but it's system-generated (unknown). You aren't supposed to use the account to log in to the shared mailbox. But what if an admin simply resets the password of the shared mailbox user account? Or what if an attacker gains access to the shared mailbox account credentials? This would allow the user account to log in to the shared mailbox and send email. To prevent this, you need to block sign-in for the account that's associated with the shared mailbox."
So that should, in theory, take care of sign-in. But what If, for some reason, you still want to allow direct access? Make sure to reduce the attack surface by disabling legacy protocols such IMAP and adopt a defense-in-depth approach by preventing shared mailbox users from accessing Powershell (which would be enabled by default) and other unnecessary privileges. In addition, take care of shared mailbox access, as users with permissions to the group mailbox can “send as” or “send on behalf” of the mailbox email address, if the administrator has given that user permissions to do so.
Then discover and map the permissions of a shared mailbox’s members and monitor actions performed by non-owners with permissions. And of course, as we all know, life is not always a straight line. In order to review non-owner actions, you’ll have to enable mailbox auditing, since in some organizations, mailbox auditing is not enabled for all users. Last and most important, go and check if your organization has shared mailboxes right away to understand your own risk.
Attackers are always on the lookout for ways to breach organization and enhanced SaaS Security Posture Management (SSPM) is no longer just a “nice to have” for enterprises. At Adaptive Shield, we help organizations proactively prevent SaaS misconfigurations, like the issues presented in this article and related to shared mailboxes, and SaaS misconfigurations in other apps (e.g. Salesforce, Zendesk, Zoom, etc) that can lead to security risks.


Account Takeovers (ATOs) are a major threat to organizations around the world. This common form of attack occurs when a cyber criminal uses legitimate credentials to gain unauthorized access to user accounts. Once inside, the attacker may steal data (PII or sensitive corporate data), steal money, and perform fraud campaigns. Each year, organizations lose millions of dollars in account takeover attacks.
But to start, let’s understand how attackers get their hands on legitimate credentials; Though there are many ways attackers can acquire credentials, there are a few main methods used:
Once the attacker has the credentials and makes their way inside, takeovers can go unnoticed for a great deal of time--and sometimes, they are never even discovered. This malicious actor on the inside can put your data and reputation in danger and can leave your organization in violation of regulations such as CCPA and GDPR.
There are many reasons that account takeover attacks are a popular attack method. But a main driver currently is the prevalence of SaaS applications used across organizations today. These platforms hold a wealth of critical corporate data, which has made them a favorite target for attackers looking to launch account takeovers. Office 365, for example, with its 180 million users and easy access to communication channels and stored data, has become a preferred attack vector. In fact, according to Microsoft’s own stats, Office 365 experiences more than 300 million fake sign-in attempts--per day. Attackers use the stolen credentials to gain access and launch attacks from inside the application.
But it's not just MS’s productivity platform that is targeted--In 2019, the ever-popular Slack was found to be harboring a security flaw that allowed attackers to initiate automated account takeovers. And not only are they easy to execute, they turn a great profit; with as little as $100, the attacker can acquire the stolen credentials and brute force or credential stuffing tools needed to pull off massively damaging attacks.
Organizations and the SaaS platforms themselves invest a huge amount of money and resources into trying to prevent account takeover attacks. But the very same elements that make SaaS applications so useful for organizations--access to vast amounts of storage and simplified communication and collaboration--continue to make them appealing targets for account takeovers.
There are some defenses organizations use to try prevent these attacks:
Fortified Password Hygiene - Using stronger, better passwords seems like a decent place to start when thinking about how to fortify account security. But here’s the thing about passwords; We all know that for a password to be secure it must be a long, random, and difficult-to-guess string of letters or words. People just aren't wired for randomness and what we think is hard to guess is often a piece of cake for an attacker. And according to Google, nearly 66% of people reuse passwords from account to account and there’s a very high likelihood that other accounts belonging to the same user will be accessible with the same passwords. Moreover, with the right tools, as mentioned above, even the most random and unique passwords can, in time, be cracked.
Multi-factor Authentication (MFA) and Single Sign On (SSO) - These two preventive measures are tightly coupled and both play an important role in preventing account takeover attacks since they provide extra layers of security to the main login method i.e., the web interface. But there are many legacy authentication protocols that don't support MFA and almost all SaaS platforms have ways to bypass SSO governance for the purpose of resiliency, making these methods less than 100% effective.
Continuous Monitoring of Accounts - A common approach to prevent account takeovers is constant monitoring for potential signs of a breach, such as suspicious logins from new browsers, devices, and locations; multiple password reset attempts in close succession; the implementation of new and questionable mailbox settings and configurations; the turning off of MFA, etc. But by nature, these attacks look like normal user behavior and thus, these behaviors may fly under the radar of continuous monitoring solutions.
To prevent account takeovers, you need to get full and automated control over your SaaS applications. With SaaS security posture management, you can detect weaknesses in real time and address them before attackers have the opportunity to make use of them by:
With Adaptive Shield, you can fine tune your SaaS native security controls to understand the full picture and see all the gaps and loopholes that exist to prevent account takeovers across all your applications. By extending visibility across your entire stack, you can fix issues immediately and keep your organization from experiencing the damaging impact of ATOs. To learn more about extending automatic control across your SaaS applications, get in touch with us today.


As security professionals who have spent more than a few years in the industry, we know a good challenge when we see one. That's why we started Adaptive Shield--to address the critical issue of proactively maintaining continuous security for the myriad of SaaS applications used in organizations across the globe.
Today, organizations have anywhere from 35-to literally hundreds of SaaS applications running. Slack, Office 365, Zoom, Zendesk, Salesforce, Hubspot, etc. These applications are at the core of modern enterprises, to the point where running a business without them would be nearly impossible, with the cost and time-saving benefits they provide enabling growth while conserving resources. SaaS applications are easy to use, scalable, and now, they even come with an impressive array of native security controls to secure sensitive corporate data.
The problem is that even with the built-in security controls, organizations still experience security breaches due to misconfigurations in their SaaS applications. With so many settings, controls, and policies to manage and track in these platforms, things fall through the cracks ALL THE TIME, resulting in huge security holes.
The thing is that ensuring SaaS applications are continuously configured properly is very tedious and you need to know what you're doing across tons of different applications. Any business-critical SaaS platform has dozens of different security and user related settings; Do the math and you’ll quickly see that trying to maintain them on your own is basically impossible. Moreover, when you consider that applications like Salesforce have security guides that are hundreds of pages long and are constantly being updated, it’s clear that trying to prevent misconfigurations is a losing proposition.
A recent example of this; A global enterprise had a misconfiguration in a leading business software platform that enabled anonymous access to anyone, exposing full employee lists, emails, schedules, dashboards--leaving them wide open to potential threats.
Organizations have tried to address the issue with varying degrees of success over the years using different tools. For example, Cloud Access Security Brokers (CASBs) address security issues in SaaS applications. But they are reactive, primarily focusing on the detection of breaches once they have occurred, which doesn’t help proactively prevent misconfigurations in the first place. And Cloud Security Posture Management tools (CSPM) only address IaaS and PaaS Security use cases. The other “approach” some organizations take is that of doing nothing at all.
Without an automatic approach to maintaining security settings and controls, organizations don't stand a realistic chance of getting total control of their SaaS applications. Trying to maintain consistent policies across all applications, understand which applications involve which security features, and account for each one’s specific methods is all just too complicated and time consuming--and leaves room for mistakes.
The emerging category of tools called SaaS Security Posture Management (SSPM) addresses this need. We founded Adaptive Shield to automatically enable optimal security posture. At Adaptive Shield, we do SaaS application security management adaptively across any type of SaaS application--including video conferencing platforms, customer support tools, HR management systems, dashboards and workspaces, content and file sharing applications, messaging applications, marketing platforms, and more. It assesses posture in a customized and automated manner, tailored to the specific circumstances of the application. And it’s not just a one-time assessment; Once policies are set, they are continuously monitored and enforced.
Adaptive Shield:
Just like those little robotic vacuum cleaners that keep things consistently clean and free of dust without the need for oversight, Adaptive Shield extends continuous automatic hygiene across your SaaS applications.
According to Gartner, by 2025, nearly 99% of security failures in the cloud will be human-driven. And complex SaaS environments only serve to make circumstances more complicated. Our goal is to remove the confusion and make SaaS security maintenance simple and sustainable, giving you the tools to effortlessly protect your organization.


On March 11th, 2020, the World Health Organization recognized the global outbreak of COVID-19 as a pandemic. In times like these, many companies encourage or mandate their employees to work from their homes to ensure they remain healthy and safe.
During mandatory Work From Home situations, business communication and productivity are major factors of success. Making sure employees can communicate with one another becomes crucial.
Like any technology, video conferencing apps (like Zoom, Webex, Bluejeans, Hangouts) come with default configurations, which can at times expose organizations to cybersecurity risks. As a security admin or user, you might want to change some of these defaults.
SaaS cybersecurity risks associated with default configurations: Exposing sensitive corporate data to unauthorized or external users, Publicly exposing user details and making them easier for adversaries to collect and Unintentionally propagating malware by using inadequate file-sharing capabilities.
Enterprise users need to have this in mind and change these default configurations to ensure they are using conferencing systems in a secure fashion.
Below you can find some highlights of what our team of cybersecurity experts at Adaptive Shield thinks are the most important security features you need to take care of when setting up a video conferencing app, with specific instructions for Zoom.
Have safe and secure collaboration sessions.

Prevent users from recording a meeting to a local file
1. Go to Zoom's Settings page
2. Account Management > Account Settings > Recording
3. Turn off Local recording
Enforce password protection for shared Cloud Recordings
1. Go to Zoom's Settings page
2. Account Management > Account Settings > Recording
3. Turn on Require password to access shared cloud recordings
4. Check Require a password to access the existing cloud recording
Make sure all messages and files are encrypted locally and on transit
1. Go to Zoom's Settings page
2. IM Management > IM Settings
3. Under Security Turn on Enable end-to-end chat encryption
Prevent the download of Cloud Recordings
1. Go to Zoom's Settings page
2. Account Management > Account Settings > Recording
3. Turn off Cloud recording downloads
4. Make sure Only the host can download cloud recordings is unchecked

Enable SSO / 2 Factor Authentication for all users
1. Go to Zoom's Settings page
* SSO can be enabled for paid users only:
2. Advanced > Single Sign-On
3. Turn on Enable Single Sign-On
* If your organzation doesn't use SSO, or you're not a paying user:
2. Advanced > Security
3. Turn on Sign in with Two-Factor Authentication
Make sure only authenticated users can view Cloud Recordings
1. Go to Zoom's Settings page
2. Account Management > Account Settings > Recording
3. Turn on Only authenticated users can view cloud recordings
4. Under Authentication Options, make sure you specify which authenticated users can access the Cloud Recordings
Choose an unguessable Meeting ID (e.g. many users pick their personal telephone number as their permanent Meeting ID)
1. Go to Zoom's Settings page
2. Make sure Personal Meeting ID isn't guessable, you can edit it by pressing Edit
Consider setting a password for meeting access
1. Go to Zoom's Settings page
2. Account Management > Account Settings > Meeting
3. Turn on Require a password when scheduling new meetings
4. Check Require a password for meetings which have already been scheduled
5. Turn on Require password for participants joining by phone

Prompt participants for consent to be recorded when recording starts
1. Go to Zoom's Settings page
2. Account Management > Account Settings > Recording
3. Turn on Recording disclaimer
4. Check both Ask participants for consent when a recording starts and Ask host to confirm before starting a recording
Start meetings with video turned off :)
1. Go to Zoom's Settings page
* Admins can change this setting globaly through:
2. Account Management > Account Settings > Meeting
* Users can change it locally through:
2. Settings
3. Turn off Host Video
4. Turn off Participants video* It's always possible to turn video on and off during meetings
Enable a chime to play when participants enter a meeting
1. Go to Zoom's Settings page
2. Account Management > Account Settings > Meeting
3. Turn on Play sound when participants join or leave

Consider instructing your users to share files using sharing platforms such as OneDrive/Box/Dropbox, where you have more control and built-in security mechanisms. If you choose to do this, you should prevent file sharing in meetings and DMs
1. Go to Zoom's Settings page
2. IM Management > IM Settings
3. Turn off File transfer
4. Continue to Account Management > Account Settings > Meeting
5. Turn off File transfer
In case you want to allow file sharing in meetings and DMs, you should at least prevent users from sharing executable file types
1. Go to Zoom's Settings page
2. IM Management > IM Settings
3. Turn on File transfer
4. Check Only allow specified file types, specify executables file types and press Save
5. Continue to Account Management > Account Settings > Meeting
6. Turn off File transfer
7. Check Only allow specified file types, specify executables file types and press Save


The US National Institute of Standards and Technology (NIST) cybersecurity framework is one of the world's most important guidelines for securing networks. It can be applied to any number of applications, including SaaS.
One of the challenges facing those tasked with securing SaaS applications is the different settings found in each application. It makes it difficult to develop a configuration policy that will apply to an HR app that manages employees, a marketing app that manages content, and an R&D app that manages software versions, all while aligning with NIST compliance standards.
However, there are several settings that can be applied to nearly every app in the SaaS stack. In this article, we'll explore some universal configurations, explain why they are important, and guide you in setting them in a way that improves your SaaS apps' security posture.
Role-based access control (RBAC) is a key to NIST adherence and should be applied to every SaaS app. There are two types of permissions within a SaaS application. Functional access covers things like creating accounts and navigating the application. Data access permissions, on the other hand, govern which users can retrieve and modify data. The admin account (or the super-admin account in some apps) is the most sensitive within the app, as it has full access to both types of permissions.
For threat actors, breaching an admin account is akin to winning the lottery. They have access to everything. Organizations must do everything within their power to maintain control over these accounts. This control is managed through configurations and best practices.
It's important to have a minimum of two admins for every application. This redundancy makes it difficult for an admin to act alone against the best interests of the organization, as admins can monitor each other for any signs of a breach.
However, each admin increases the application's attack surface. Organizations must strike a balance between having enough admins to adequately service the application while limiting exposure. An automated review of the number of admins should trigger alerts when the number of admins is outside the preferred range.
External admins introduce a new layer of uncertainty into SaaS security. Because they sit outside the organization, the security team can't control the password policies or authentication tools that they use.
For example, should a threat actor try to log into your application and click Forgot Password, there is no way to know whether the threat actor can breach the external admin's email account. That lack of oversight of external users could lead to a deep breach of your SaaS application, which is why NIST advises against having external admins. Depending on the application, either block external admins from getting admin privileges or identify external users with admin rights and remove those privileges.
For companies that hire an external IT company or outsource to MSSPs, those individuals should not be considered external. However, they should continue to monitor for other external users being given admin permissions.
To comply with NIST standards, all admin user accounts should be required to access the application using multi-factor authentication (MFA), such as a one-time password (OTP). MFA requires users to present a minimum of two forms of ID before it authenticates the user. A threat actor would need to compromise two authentication systems, increasing the level of difficulty of the compromise and reducing the risk to the account. Make sure to set MFA for admins as required (we also recommend MFA for all users, but it is a must-have for admins).
SaaS data leaks pose significant risks to organizations and their users, potentially compromising sensitive information stored within cloud-based applications. SaaS applications are marketed as collaboration tools. However, the configurations that enable users to work together can also compromise files and data. NIST, for its part, advocates monitoring the permissions of every resource.
A visible calendar can expose employees to socially engineered phishing attacks, while shared repositories can lead to a company's internal source code being shared publicly. Email, files, and boards all contain sensitive data that should not be accessible to the public. While the following configurations are often called something different in each application, almost any app that stores content will have this type of control.
The difference between Share with All and Share with a User is profound. When items are shared with all, anyone with a link can access the materials. Share with a User, in contrast, adds an additional authentication mechanism, as the user needs to log in before accessing the material.
To reduce the content that is exposed, app admins should disable sharing over public URLs ("Anyone with the link"). In addition, some applications allow users to revoke access to URLs that have already been created. When available, organizations should be sure to toggle that setting to on.
Many applications allow authorized users to invite external users to the application. However, most applications don't implement an invite expiration date. In those circumstances, invites sent years prior can provide access to a threat actor who has just breached an external user's email account. Enabling an auto-expiration date on invites eliminates that type of risk.
It's worth noting that in some apps, configuration changes are retroactive, while others will only take effect moving forward.
Passwords are the first line of defense against unauthorized access. NIST advocates for a strong and well-managed password policy, which is essential to protect sensitive user data, confidential business information, and proprietary assets stored within the cloud-based infrastructure. The uniqueness, complexity, and regular updating of passwords are critical aspects of a robust security posture.
Passwords serve as a fundamental element in a layered security approach, complementing other security measures such as multi-factor authentication (MFA) and encryption. Compromised passwords can be a gateway for malicious actors to exploit vulnerabilities in the SaaS environment. The effective management of passwords enhances the overall resilience of SaaS systems, contributing to a more secure and trustworthy digital ecosystem for both businesses and their users.
In a spray attack, threat actors enter a username and common password terms, hoping to get lucky and access the application. Requiring MFA is the recommended way to prevent password spray attacks. For those that don't insist on employees using MFA as part of the authentication process, many apps allow organizations to ban words from being used as passwords. This list of words would include terms like password1, letmein, 12345, and the names of local sports teams. Additionally, it would include terms like the user's name, company products, partners, and other business terms.
Going into the configurations and adding a custom banned words list can significantly reduce the risk of a successful password spray attack.
Most SaaS applications allow the organization to customize password complexity. These range from allowing any password to requiring alphanumeric characters, capital and lowercase letters, symbols, or a password length. Update the password requirements in the app to match your organization's policy.
If your organization doesn't have a password policy, consider following NIST guidelines:
It may seem unlikely that threat actors spend their time looking for misconfiguration that they can exploit. Yet, that is exactly what the Russian state-sponsored group Midnight Blizzard did when it breached Microsoft this year. If misconfigurations can happen at Microsoft, it's worth reviewing to make sure that your applications are all secure.


The National Institute of Standards and Technology (NIST) is one of the standard-bearers in global cybersecurity. The U.S.-based institute’s cybersecurity framework helps organizations of all sizes understand, manage, and reduce their cyber-risk levels and better protect their data. Its importance in the fight against cyberattacks can’t be overstated.
While NIST hasn’t directly developed standards related to securing the SaaS ecosystem, they are instrumental in the way we approach SaaS security.
NIST recently released its Guide to a Secure Enterprise Network Landscape. In it, they discuss the transformation from on-premise networks to multiple cloud servers. Access to these servers, and the accompanying SaaS apps, is through both secure and unsecured devices and locations across disparate geography.
The move to the cloud has effectively obliterated the network perimeter. As a result, companies have increased their attack surface and are experiencing an escalation of attacks that span across network boundaries.
Rather than focus on network-centric security, security must take a three-pronged approach. The user, endpoint, and application are keys to protecting data. This new paradigm emphasizes the importance of identity, location, and contextual data associated with the user, device, and service.
Today’s security tools need to scale to meet the volume, velocity, and variety of today’s applications. They need to integrate seamlessly with SaaS applications and provide coverage for the entire SaaS stack.
To be effective, these tools need to minimize human intervention for monitoring and remediation. Automation is critical for an ecosystem that demands secure configurations for each user account that has access to the application. Large organizations may have millions of configurations to secure across their entire SaaS stack; closing them manually is an impossible task.
SaaS security tools must be able to integrate with all the apps on the stack and identify each application through the SaaS app’s APIs. Once connected, it must monitor the security configurations, staying alert to any changes. This configuration drift can have severe consequences, as it exposes SaaS applications by removing the safeguards put in place to prevent unauthorized access. It needs to continuously monitor applications, and issue alerts as risk increases.

Effective SaaS security tools use contextual data to detect threats to the application and its data. These threats can come from humans and machines and may have access to the system using verified credentials.
Contextual data from across the SaaS stack can help identify paradoxical travel, spikes in failed authentication attempts from the same IP address for multiple accounts, or attempts where automated tools test weak and common passwords against known user names. It can also recognize malicious third-party applications that are significantly overprivileged for their functionality.

In the world of SaaS, the devices represent the network perimeter. Accessing SaaS applications with devices that have poor hygiene can put all the data at risk. Compromised devices can hand over login credentials to threat actors, who can leverage that into breaching and stealing data.
Effective SaaS security tools partner with endpoint security providers to ensure that the devices that access SaaS apps have an up-to-date operating system, all software has been updated, and any patches have been applied.

While devices may be the perimeter, user ID is the barrier preventing unfettered access to company data. Access should be given using a zero-trust approach. All access should be granted through an SSO connected to an enterprise-managed IdP. Organizations should reinforce this entryway with a phishing-resistant MFA authenticator.

Effective SSPM platforms are built on robust security checks that review each SaaS configuration to ensure they are optimized for protection. Typically, security setting recommendations are influenced heavily by NIST’s cybersecurity approach, and their guidance enables SSPM vendors to monitor and track usage, users, and behaviors, as well as identify threats.


Healthcare has been cautious in moving toward cloud technologies and SaaS applications. Concerns over privacy and the need to comply with HIPAA regulations had left them stuck using on-premises software solutions. However, COVID forced healthcare organizations to develop telehealth models. Patients increasingly wanted digital access to their records, and healthcare organizations recognized the need to meet interoperability mandates.
As patient and industry needs continue to evolve, more healthcare organizations have adopted SaaS apps, evidenced by a predicted SaaS global healthcare market growth of 19.5% between 2021 and 2028. As the industry embraces this shift to the cloud, healthcare security professionals need to understand how SaaS security impacts their Health Insurance Portability and Accessibility Act (HIPAA) compliance posture.
Across the industry, healthcare organizations leverage SaaS applications to streamline patient care and administrative tasks. Meanwhile, the industry faces unique security and compliance concerns.
Cybercriminals target the healthcare industry because they can use protected health information (PHI) in various ways. Some examples of how they use this valuable data include:
Between tight budgets and the cybersecurity skills gap, the healthcare industry often lacks the resources needed to implement security. IT budgets often focus on technologies that enable patient care and administrative functions. Simultaneously, the limited number of skilled security professionals often means that healthcare organizations struggle to find and retain the talent they need.
In January 2022, Congress signed a HITECH Amendment into law that requires the Department of Health and Human Services (HHS) to create standards, guidelines, best practices, methodologies, procedures, and processes for protecting ePHI. In response, the HHS Office for Civil RIght (OCR) recommended the Health Industry Cybersecurity Practices: Managing Threats and Protecting Patients (HICP) publication and the National Institute of Standards and Technology Standards (NIST) Cybersecurity Framework (CSF).
HICP outlined the following ten most effective Cybersecurity Practices:
As healthcare organizations adopt more SaaS applications, their security teams find that manually managing HIPAA compliance becomes overwhelming. For example, many organizations struggle with:
As the healthcare industry adopts more SaaS applications, security professionals need to manage the three primary HIPAA compliance pain points associated with them:
SSPM solutions enable covered entities and business associates to monitor their SaaS environments and enforce security policies.
SSPM solutions solve the IT, security, and privacy SaaS misconfiguration challenges by offering:
Implementing the right SSPM solution enables covered entities and business associates to enforce security configurations across their SaaS ecosystem. As organizations research SSPM solutions, they need to consider the technology’s capabilities and functionalities. With the right SSPM, organizations gain continuous, automated surveillance of all SaaS apps and the documentation supporting their HIPAA compliance posture.


The International Organization for Standardization (ISO) sets standards across various industries. As an internationally recognized standards organization, its two information technology security standards - ISO 27000:2018 and ISO 27001:2013 - can be used to help build out a strong security posture.
SaaS security is critical to ISO compliance in the modern business world. However, with all the non-stop developments in the organization's SaaS stack, from updating and modifying configurations to discovering SaaS-to-SaaS access and securing devices etc., it can become overly burdensome for a security team to handle. SSPM solutions come to answer this pain by providing proactive, deep, continuous and automated monitoring & management capabilities. (SSPM solutions can also offer security checks per compliance framework so the security team can easily see where their posture is compliant or needs remediation.)
This blog will take a deep dive into understanding the ISO compliance standards, with its two recent yet different versions, and how SSPM can help security teams ensure ISO compliance.
Simply put: ISO 27000:2018 gives you goals to accomplish while ISO 27001:2013 outlines the steps you have to take to achieve those outcomes.
ISO 27000 sets out the following fundamental principles of your security program:
ISO 27001 focuses on best practices and establishing an Information Security Management System (ISMS) that consists of policies and procedures. It includes five processes for achieving these security fundamentals:
A lot of this sounds fairly vague, and it is. ISO takes a risk-based approach to establishing an ISMS, but that doesn’t mean you’re on your own.
The first three clauses give you the basic terminology and scoping. It’s clauses four through ten that start to get into some more detail. These are:
Again, this is fairly high-level, even though ISO gives detailed definitions within the clauses. The real work of getting ISO compliant is found in Annex A which lists 114 controls aligned to ten clauses.
The problem with understanding the importance of SaaS security within the ISO context is that ISO never specifically mentions SaaS apps. Since it acts as a risk-based framework, you need to start by identifying the risks that SaaS apps pose, then put the controls around them.
Going into all the controls listed in ISO 27001 would be too long for this post. However, you can get a general sense of how SaaS security - and SaaS Security Posture Management (SSPM) - fits into your ISO compliance plans with a few examples.
Under Access Control, you need to ensure that all users are assigned the appropriate access needed to complete their job functions.
Ensuring SaaS security under this requirement can be challenging because you need to make sure that you meet the following sub-requirements:
Permission drifts occur when a user has certain permissions as part of a group membership, but then gets assigned a specific permission that is more privileged than what the group has. Over time many users get extra permissions. This undermines the idea of provisioning using groups.
SSPM gives you a way to govern users’ cloud access by:
Operations security is the process of ensuring correct and secure operations for all information processing facilities. In cloud environments, managing operations security becomes more difficult because you often lack visibility.
Ensuring SaaS security under this requirement can be challenging because you need to make sure that you meet the following sub-requirements:
OAuth is an extremely common action that users take, but implementation mistakes can lead to attacks. You need to make sure that you have the appropriate documented operating procedures for onboarding new applications that use OAuth. Further, cybercriminals can use misconfigurations, like the sending OAuth application phishing emails, as part of their ransomware attacks.
SSPM gives you the ability to run continuous security checks for all SaaS apps in use, in addition to the SaaS-to-SaaS access, so that you can:
This requirement focuses on avoiding legal, statutory, regulatory, or contractual obligations.
Ensuring SaaS security under this requirement can be challenging because you need to make sure that you meet the following sub-requirements:
Default configurations can lead to PII leaks as seen in the 2021 Power Apps portal issue that Microsoft fixed. Knowing what default configurations create a compliance violation and monitoring to ensure that you fix issues is key to compliance.
SSPM can help you get compliant by:
.png)
.png)
An accountant and a security expert walk into a bar… SOC2 is no joke.
Whether you're a publicly held or private company, you are probably considering going through a Service Organization Controls (SOC) audit. For publicly held companies, these reports are required by the Securities and Exchange Commission (SEC) and executed by a Certified Public Accountant (CPA). However, customers often ask for SOC2 reports as part of their vendor due diligence process.
Out of the three types of SOC reports, SOC2 is the standard to successfully pass regulatory requirements and signals high security and resilience within the organization — and is based on the American Institute of Certified Public Accountants (AICPA) attestation requirements. The purpose of this report is to evaluate an organization's information systems relevant to security, availability, processing integrity, confidentiality, and privacy — over a period of time (roughly six to twelve months).
As part of a SOC2 audit, it is necessary to conduct security checks across the company's SaaS stack that will look for misconfigured settings such as detection and monitoring to ensure continued effectiveness of information security controls and prevent unauthorized/ inappropriate access to physical and digital assets and locations.
If you're beginning or on a SOC2 audit journey, then an SSPM (SaaS Security Posture Management) solution can streamline the process and shorten the time it takes to pass a SOC2 audit successfully, fully covering your SaaS Security posture.
When external auditors engage in a SOC 2 audit, they need to compare what you're doing to a long list of established requirements from AICPA TSC. The "Common Controls" fall into five groups:
Within each common control are a set of sub controls that turn the overarching standard into actionable tasks.
Passing a SOC 2 audit takes a lot of time, effort, and documentation. During a SOC2 audit, you not only need to show that your controls work during the audit period, but you also need to show that you have the ability to continuously monitor your security.
Going through the entire TSC framework is too long for a blog post. However, a quick look into a couple of controls of Logical and Physical Access (CC6) and System Operations (CC7) gives you an idea of what some of the controls look like and how you can utilize an SSPM to ease the SOC2 audit.
This section sets out the types of controls needed to prevent unauthorized or inappropriate access to physical and digital assets and locations. Managing user access permissions, authentication, and authorization across the SaaS estate poses many challenges. In fact, as you look to secure your cloud apps, the distributed nature of users and managing the different access policies becomes increasingly challenging.
Under CC6.1 control, entities need to:
The department that utilizes a SaaS app is often the one that purchases and implements it. Marketing might implement a SaaS solution for monitoring leads while sales implements the CRM. Meanwhile, each application has its own set of access capabilities and configurations. However, these SaaS owners may not be trained in security or able to continuously monitor the app's security settings so the security team loses visibility. At the same time, the security team may not know the inner workings of the SaaS like the owner so they may not understand more complex cases which could lead to a security breach.
An SSPM solution, maps out all the user permissions, encryption, certificates and all security configurations available for each SaaS app. In addition to the visibility, the SSPM solution helps correct any misconfiguration in these areas, taking into consideration each SaaS app's unique features and usability.
In CC.6.2 control, entities need to:
Permission drifts occur when a user has certain permissions as part of a group membership, but then gets assigned a specific permission that is more privileged than what the group has. Over time many users get extra permissions. This undermines the idea of provisioning using groups.
Classic deprovisioning issues, an SSPM solution can spot inactive users and help organizations to quickly remediate, or at the very least, alert the security team to the issue.
Under CC.6.3 control, entities need to:
You might be managing 50,000 users across five SaaS applications, meaning the security team needs to manage a total of 250,000 identities. Meanwhile, each SaaS has a different way to define identities, view them, and secure identities. Adding to the risk, SaaS applications don't always integrate with each other which means users can find themselves with different privileges across different systems. This then leads to unnecessary privileges that can create a potential security risk.
An SSPM solution allows visibility into user privileges and sensitive permission across all connected SaaS apps, highlighting the deviation from permission groups and profiles.
This section focuses on detection and monitoring to ensure continued effectiveness of information security controls across systems and networks, including SaaS apps. The diversity of SaaS apps and potential for misconfigurations makes meeting these requirements challenging.
In CC7.1 control, entities need to:
It is unrealistic to expect from the security team to define a "configuration standard" that complies with SOC2 without comparing against a built-in knowledge base of all relevant SaaS misconfigurations and to continuously comply with SOC2 without using an SSPM solution.


When I want to know the most recently published best practices in cyber security, I visit The National Institute of Standards and Technology (NIST). From the latest password requirements (NIST 800-63) to IoT security for manufacturers (NISTIR 8259), NIST is always the starting point. NIST plays a key role as a US standard-setter, due to the organization’s professionalism and the external experts who help to create NIST documents.
The NIST Cybersecurity Framework (CSF) was initially released in 2014 and last updated in 2018. The Framework enables organizations to improve the security and resilience of critical infrastructure with a well-planned and easy to use framework.
The continuing growth in SaaS, and the major changes to the work environment due to COVID-19 bring new security challenges. Although the CSF was written and updated while SaaS was on the rise, it is still geared towards the classic legacy critical infrastructure security challenges. However, by adapting the CSF to modern, SaaS-based work environments, organizations can better respond to new risks.
I personally love this Framework, but truth be told, when one reads the Framework in-depth, its complexity is apparent, and following it can be difficult. This article will review the CSF’s key elements, point out its key merits, and suggest implementations for SaaS security.
The NIST CSF lays out five functions of security, then splits them into categories and subcategories. The subcategories contain the actual controls. For each subcategory, the CSF includes a list of cross-references to well known standards and frameworks such as ISO 27001, COBIT, NIST SP 800-53, and ANSI/ISA-62443.
These cross-references help organizations implement the CSF and map it to other frameworks. For example, security managers or other team members can use the references to justify their decisions no matter what security standard the company needs to comply with.
In a single document, the Framework combines a host of approaches to dealing with cyber security threats. This includes:
The framework has a five stage core structure: Identify, Protect, Detect, Respond and Recover. I’m going to break them down into bullets for you.

NIST defines this function as follows: "Develop the organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities". Within this function, NIST includes the following control categories:
NIST defines this function as follows: "Develop and implement the appropriate safeguards to ensure delivery of critical infrastructure services". Within this function, NIST includes the following control categories:
NIST defines this function as follows: "Develop and implement the appropriate activities to identify the occurrence of a cybersecurity event". Within this function, NIST includes the following control categories:
NIST defines this function as follows: "Develop and implement the appropriate activities to take action regarding a detected cybersecurity event". Within this function, NIST includes the following control categories:
NIST defines this function as follows: "Develop and implement the appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity event". Within this function, NIST includes the following control categories:
While definitely a model in best practices, the Framework is a challenge to implement.
A company using SaaS services may wonder how this is relevant for them. They may think that compliance is the SaaS provider’s responsibility. However, a deeper look into it shows that many SaaS providers have security measures in place, and the user is responsible for using them.
For example, admins should not allow any connections via HTTP to a SaaS service. They should only allow secure, HTTPS, connections.
This may seem like a small subcategory, but underneath there is a behemoth. Data leaks are extremely difficult to prevent. SaaS application adoption makes this harder because people can share and access them from anywhere in the world.
An admin or member of the CISO office should take special care of this threat. DLP in SaaS can include security measures such as:
As an enterprise scales its workforce and SaaS adoption, this subcategory becomes more challenging. Managing 50,000 users over just five SaaS means that the security team needs to manage 250,000 identities. This problem is real and complicated.
Even more challenging, each SaaS has a different way to define identities, view them, and secure identities. Adding to the risk, SaaS applications don’t always integrate with each other which means users can find themselves with different privileges across different systems. This then leads to unnecessary privileges that can create a potential security risk.
The NIST CSF is an industry standard for cybersecurity today, yet to implement it with typical manual practices and processes is an uphill battle. So why not automate?
Adaptive Shield is a SaaS Security Posture Management (SSPM) solution which can automate the compliance and configuration checks across the SaaS estate. Adaptive Shield enables security teams to easily see and fix configuration weaknesses quickly, ensuring compliance with company and industry standards, from NIST CSF, as well as other compliance mandates such as SOC 2 and the CSA Cloud Controls Matrix.
To learn more about extending automated visibility and control across your SaaS applications, speak to our experts today.


Media firms in the business of image and reputation don’t want to get bad publicity. With regulations requiring companies to report data breaches, information companies handling personal data must take extra cybersecurity caution.
Take for example the case study of a European-headquartered global media and information services company with an annual revenue of over $10 billion. The growing adoption of cloud-based SaaS collaboration tools was making it a challenge for security teams to stay on top of emerging data leakage threats.
More of the organization’s sensitive and valuable data was moving to the cloud with business-critical SaaS applications being used across teams and departments. The firm was also acquiring small enterprises. Every acquisition increased the number of applications and geographically distributed SaaS tenants added even more complexity.
After discovering a series of internal data breach incidents involving data stored in SaaS applications, the company decided to look for an automated SaaS security posture management solution that would enable its security team to monitor and manage risk in its SaaS stack, efficiently and effectively.
The firm evaluated multiple SaaS Security Posture Management (SSPM) solution vendors, choosing the Adaptive Shield solution considering among other things that it supported the industry’s widest portfolio of SaaS applications.
Forrester Consulting conducted a Total Economic Impact™ (TEI) study commissioned by Adaptive Shield to assess the ROI and benefits of the organization’s SSPM investment. In the cost-benefit analysis, the company achieved benefits worth $2.18 million over three years with a 201% ROI, and a return on investment in less than six months.
The study, as follows, covers the customer journey, starting from the SaaS challenge to the successful implementation of an SSPM solution.
Before the adoption of Adaptive Shield’s SSPM, the case study found that the media company’s security team lacked the necessary knowledge and skills to identify and mitigate risk in the controls and settings of SaaS applications. Since the security team had limited familiarity with each application, they could not oversee each application’s configuration. As a result, they could not ask the business unit application owners the right security configuration questions. On the other hand, with their newfound SaaS independence, app owners with “the keys to the kingdom” were reluctant to participate in new initiatives brought by the security team. Moreover, they were neither educated nor equipped enough to exercise security.
“We started seeing some small incidents resulting from SaaS misconfiguration, so we needed to do something about it… [It] was a wake-up call for us that we really need to look at all the configurations at scale,” the chief security officer of the company said in an interview with Forrester for the study.
So clearly the traditional manual approach to managing SaaS security was failing, leading the firm to search for an automated solution that could provide visibility and control into its SaaS applications throughout the organization.
During the SSPM acquisition and rollout process, the company experienced a quick and significant improvement in its SaaS security posture score.
An immediate benefit was the quick reduction in the number of data breach incidents. Before implementing SSPM the firm had experienced six incidents in a year. With the launch of the solution, the number began to decline rapidly, going down to 3 in the second year, and projected to be one or less by the third year.
Before implementing Adaptive Shield, the company’s SaaS security posture score was 40%. During the proof-of-concept (POC) phase, the security team found issues in their SaaS configurations and fixed them.
“When we look at the security score trends, we observed a significant increase over time,” the CSO said.
The score improved rapidly to 70% in the first year, 85% in the second year, and was on track to reach 95% after three years. The total projected improvement in the overall score was 55%.
The substantial improvement in the overall security posture score was attributed to SSPM capabilities to deliver visibility, remediation guidance, and ongoing monitoring.
A major contribution to overall security posture was improvement in misconfiguration detection efficiency. Automating the traditional manual approach to SaaS configuration management and remediation improved the efficiency of the process. The combined effort by the security and business teams spent on configurations for each application’s traditional annual risk assessment was reduced by 70 percent, from 100 hours to 30 hours per application.
By deploying Adaptive Shield, the organization was also able to significantly expand the number of monitored applications over three years from 20 to 60.
An additional benefit was a savings of 90% in labor efforts in managing the firm’s compliance goals and priorities. Before the adoption of Adaptive Shield, the security team spent 2400 hours a year implementing compliance rules, with the time spent decreasing to 240 per year, for a 90% savings.
The study also found the SSPM opened conversations between security and business owners, enhancing collaboration and trust between business and security teams that saved company time.
In addition to quantifiable improvements, the company was interested in understanding the qualitative results of its investment in SSPM.
The study found that the solution helped the organization overcome the overall challenges introduced by the democratization of SaaS security and secure SaaS data. It enabled it to maintain a holistic view of SaaS-related inventory.
The security team gained a powerful tool to manage the inventory of SaaS applications, connected applications, users, and user devices, and track the status of SaaS subscriptions.
SSPM helped the organization achieve continuous compliance, avoiding any interruptions to business operations, and staying ahead of any SaaS security trends.
The Adaptive Shield solution also detected suspicious activities from new devices and new IP addresses.
The frequency of SaaS attacks is only growing and SaaS incidents are continuously exposing organizations to data leaks, breaches, compliance failures, and other potential disruptions in business operations.
This case study demonstrates how Adaptive Shield helped a media organization improve SaaS security and streamline security operations.
This article was originally published in Cyber Defense News.
To learn more about the study and 2024 SaaS security trends, join the webinar with CISO and renowned cybersecurity advocate, Matthew Rosenquist, and Adaptive Shield CEO & Co-founder, Maor Bin. February 20th, 2024 at 2pm EST. Register Now



The dynamic landscape of cybersecurity is witnessing a paradigm shift, with the SaaS Security Posture Management (SSPM) market emerging as a critical and pivotal player in safeguarding organizations against evolving cloud-based threats. As a clear must-have solution, Forrester has now brought to market their SSPM Wave, laying out their assertions and designating the top providers in the space.
Proud to be named a Strong Performer, Forrester’s Wave Report acknowledges Adaptive Shield’s capabilities and details each vendor’s current offering, strategy and market presence.
Within this blog post, I analyze the report, highlighting some of its findings and opening avenues for discussion. I believe Forrester’s vendor positioning might raise questions and this might be due to criteria such as proxy-based tech that is considered to be a pure CASB capability, cost saving features that are typically found in SMPs, heavy weighting of secondary criteria the same as primary SSPM capabilities, and due to the Innovation criteria that is measured solely based on the company size.
A core criteria for an SSPM solution, configuration drift detection is explained as the SaaS app owner or admin's functional, intuitive, and simplified ability to configure known good baselines, set up configuration drift notifications, view affected user lists post-configuration changes, and configure both vendor-supplied and client organization-specific risk score definitions, rules, and remediation steps.
Forrester recognizes that Adaptive Shield received the highest score possible in the Configuration Drift Detection criterion in that all recommended baseline configurations are available in the UI of the Security Checks feature. These configurations are mapped to best practices, frameworks, and compliance standards. The Adaptive Shield solution provides the ability to receive configuration drift notifications via multiple channels such as Slack, Teams, Emails, or any ticketing system of choice. The notification can be app-specific and drift-specific. The affected user list after a configuration change appears in the Security Check feature under the "Affected" tab and also under "Alerts".
In custom Security Checks the user of the platform can add/edit the score, rule and remediation plan manually. In out-of-the-box Security Checks, the user can change the risk score and other variables to match a custom logic.
Forrester explains SaaS App Configuration Templates to involve the customer SSPM administrator's functional, intuitive, and simplified ability to use and configure various compliance templates, customize vendor-supplied templates, cross-reference individual configuration artifacts with compliance templates, utilize natural language misconfiguration impact and remediation descriptions, and configure reports on findings and differences between templates and actual app configurations.
Forrester acknowledges that Adaptive Shield received the highest possible score in the SaaS app Configuration Templates. Adaptive Shield’s Security Checks are mapped to all the industry compliance frameworks (ISO 27000 series, SOC2, NIST CSF, CIS, etc.) — and are available out-of-the-box for users to benchmark against. The platform also provides its own frameworks and customers have the flexibility to customize them- whether by adding rules, dismissing checks or defining parameters. In addition, the Security Checks feature allows users to see the configuration deltas between the different Templates and AS-IS of both passed and failed checks. On top of these capabilities, the Landscape view presents the increase or decrease in posture score based on the recent changes.
The remediation guides are in English, descriptive and user-friendly, encouraging app owners to easily remediate. There is also a journal feature that enables users to communicate through the platform on each check. The “Posture Overtime” feature shows any change in configurations, gathering logs from the past 180 days.
Forrester defines IAM administration as involving the functional, intuitive, and user-friendly configuration of user graphs, inactive admin user detection, authentication monitoring, high-risk business user-centric views, and fine-grained user permission management in applications.
Adaptive Shield’s robust User Inventory received the highest possible score for a strong Identity Security Posture where each SaaS user has consolidated information on what SaaS app he has access to, permissions, roles, groups, and more. This also presents the failing user checks and how to remediate. In the Security Check feature, there are specific checks for access to sensitive data and settings in the system. There are out-of-the-box security checks that check for inactive admins. These can be changed to fit company policies within a preset or custom timeframe. This information is also available in the User Inventory via filters and custom security checks.
Scale, as defined by Forrester, is determined by the largest number of SaaS applications handled at a single, direct, in-production, paying customer organization as of June 30, 2023.
Adaptive Shield collaborates with hundreds of F1000 and Large Enterprises, our innovative tech and infrastructure enables us to support enterprises at scale and has been recognized as superior compared to other vendors.
Within a few of the criteria listed by Forrester, I had a few questions by either the criteria, the definition of the criteria or the evaluation itself. Below are the items that raised the most questions for me.
In Forrester reports, the category weights are meant to prioritize key features and capabilities of a technology, but in this Wave, it seems that primary and secondary categories have been mixed. Why? SSPM, at its core, enables security teams to monitor and manage their SaaS stack. Items like configuration drifts, compliance frameworks and breadth of app integrations sit at its very heart. Taking a look at the categories and the weighting associated with each in this report, one can misunderstand the core features of an SSPM solution.
The Innovation criteria is solely based on technical employee headcount. The rating is calculated based on the absolute number of technical headcount, clearly disadvantageous to emerging vendors as opposed to larger vendors. Many would argue that the success of an emerging vendor lies in their innovation, agility, and ability to disrupt the norm also based on their tech, vision, research and more. This might explain why all emerging SSPM companies were given a lower rating, influencing their position in the Wave overall — as this criteria was given one of the highest category weights at 14%.
Respecting Forrester’s definition of innovation, perhaps it would be more logical to calculate the ratio of technical headcount vs overall headcount instead of the absolute number of technical headcount.
Forrester includes Shadow IT detection capabilities and remediation, OAuth grants discovery, automatic bulk revocation of grants, identification of managed and unmanaged applications, and proxy-based shadow IT discovery for the report scoring.
Adaptive Shield’s 3rd Party App Inventory shows all 3rd party apps discovered, including OAuth apps, and the user who granted the OAuth consent, among many other important details. The 3rd Party App Inventory detects unsanctioned apps that are connected to apps integrated within the Adaptive Shield platform. With over 140 apps out-of-the-box integrations and the ability to connect custom apps, Adaptive Shield customers have deep visibility into their large network of apps, sanctioned or unsanctioned, from within the solution.
Important to note is that Adaptive Shield does not support proxy-based shadow IT discovery, like a CASB. SSPM, being a modern solution, is API based. In fact, one of the reasons SSPM technology emerged was to intentionally shift away from control via proxy.
Another point of interest not mentioned in Forrester’s definition, is the innovative element to show API keys. Adaptive Shield’s 3rd Party App Inventory also presents API Key information, a new and important feature for this capability.
While Forrester's Wave report is a valuable resource for assessing solutions, my analysis has uncovered areas where we concur, and where we differ. I believe it's crucial for stakeholders to evaluate the report with a clear understanding of the details and delve into the above discussion to judge for themselves.
I’m thankful to Forrester for bringing this important sector of SSPM to front-of-mind, and ultimately, your organization's specific requirements and direct experience with the solution should guide your decision-making process, ensuring a tailored fit for your organization's SaaS Security needs.


The Cloud Security Alliance (CSA), the world’s leading organization dedicated to defining standards, certifications, and best practices to help ensure a secure cloud computing environment, today released the findings of its latest survey, SaaS Security Survey Report: 2024 Plans & Priorities. Commissioned by Adaptive Shield, the leading SaaS Security Posture Management (SSPM) company, the survey gathered responses from 1,000-plus C-level security executives and professionals from all over the world, with the majority from North American enterprises.
“Many recent breaches and data leaks have been tied back to SaaS apps. We wanted to gain a deeper understanding of the incidents within SaaS applications, and how organizations are building their threat prevention and detection models to secure their SaaS ecosystem," said Hillary Baron, lead author and Senior Technical Director for Research, Cloud Security Alliance. “This explains why 71% of respondents are prioritizing their investment in security tools for SaaS, most notably turning to SaaS Security Posture Management (SSPM) as the solution to secure their entire SaaS stack.
“The attack surface in the SaaS ecosystem is widening and just as you would secure a cloud infrastructure with Cloud security posture management, organizations should secure their SaaS data and prioritize SaaS security,” asserts Maor Bin, CEO and co-founder of Adaptive Shield. “In last year’s survey, 17% of respondents said they were using SSPM. This year that figure has soared, with 80% currently using or planning to use an SSPM by the end of 2024. This dramatic growth is fueled by the fact that 55% of organizations stated they recently experienced a SaaS security incident, which resulted in ransomware, malware, data breaches, and more. Threat prevention and detection in SaaS is critical to a robust cybersecurity strategy spanning SaaS Misconfigurations, Identity and Access Governance, SaaS-to-SaaS Access, Device-to-SaaS Risk Management, and Identity Threat Detection & Response (ITDR).”
Among the survey’s key findings:
The survey gathered more than 1,000 responses from IT and security professionals from various organization sizes, industries, locations, and roles.


Microsoft is a primary target for threat actors, who scour Microsoft applications for weaknesses. Our security research team at Adaptive Shield recently discovered another new attack vector caused by a vulnerability within Microsoft’s OAuth application registration that allows attackers to leverage Exchange's legacy API to create hidden forwarding rules in Microsoft 365 mailboxes.
To understand this new attack vector, you must understand the key components therein. These include hidden forwarding rules and SaaS-to-SaaS app access, all of which amount to a malicious SaaS rootkit that can infiltrate users' accounts and control their mailboxes — without the users' knowledge.
Inbox rules are actions that occur based on preset conditions within a Microsoft mailbox. Users or admins can use forwarding rules to trigger protocols based on different attributes of the user's inbox.
Hidden forwarding rules (Figure 1) were first discovered by Compass Security’s Damian Pflammater in 2018. He covered the discovery and Microsoft’s response in a blog post titled “Hidden Inbox Rules in Microsoft Exchange.” These rules are fully functional and can be seen on the backend. However, they are not visible common interfaces such as email clients, an admin dashboard, or an API (Figure 2).


SaaS-to-SaaS app access, also referred to as third-party app access, describes the conditions under which one app can connect to another app and, in doing so, gain access and permission to different information and settings. The OAuth 2.0 mechanism simplifies the process of authentication and authorization between consumers and service providers through a seamless process that allows users to quickly verify their identities and grant permissions to the app. The app is then allowed to execute code and perform logic within its environment behind the scenes.
In many instances, these apps are completely harmless and often serve as a valuable business tool. In other instances, these apps can act as malware, similar to an executable file.

With this SaaS rootkit, threat actors can create malware that lives as a SaaS app and can infiltrate and maintain access to a user’s account while going unnoticed.
While bad actors can't find Exchange Legacy scopes that can be used to add programmatically online hidden forwarding in the Microsoft UI, they can add them through a terminal script.
The attacker's job is simple: Create an app that looks credible, add the legacy scope protocols removed from the UI to the app (exploiting the vulnerability that the Adaptive Shield team uncovered), and send an offer to users to connect to it. The user will see an OAuth app dialog box on the official Microsoft site, and many will likely accept it (Figure 4).

Once a user accepts, the bad actor receives a token that grants permission to create forwarding rules and hides them from the user interface like a rootkit.
An attack through these hidden forwarding rules should not be mistaken for a one-off attack but, rather, the start of a new attack method through SaaS apps.
In 2022, Adaptive Shield contacted Microsoft about the issue, Microsoft in response said that the issue has been flagged for future review by the product team as an opportunity to improve the security of the affected product.
There's no bullet-proof way to eliminate SaaS rootkit attacks but there are a few best practices that can help keep organizations more protected.
Hidden forwarding rules are still a threat, even more so when they appear through the trusted Microsoft website. The traditional controls that were created to stop malware have struggled to keep up with the evolution of malware and the new attack vector that can exploit any SaaS app, from M365 to Salesforce to G-Workspace, etc. Organizations should utilize native security configurations to control the OAuth application installations across SaaS apps to protect users from malicious attacks like these.


Spoiler Alert: Organizations with 10,000 SaaS users that use M365 and Google Workspace average over 4,371 additional connected apps.
SaaS-to-SaaS (third-party) app installations are growing nonstop at organizations around the world. When an employee needs an additional app to increase their efficiency or productivity, they rarely think twice before installing. Most employees don't even realize that this SaaS-to-SaaS connectivity, which requires scopes like the ability to read, update, create, and delete content, increases their organization's attack surface in a significant way.
Third-party app connections typically take place outside the view of the security team, are not vetted to understand the level of risk they pose.
Adaptive Shield's latest report, Uncovering the Risks & Realities of Third-Party Connected Apps, dives into the data on this topic. It reviews the average number of SaaS-to-SaaS apps organizations have, and the level of risk they present. Here are the top 5 findings.
The report focuses on Google Workspace and Microsoft 365 (M365), as it paints a clear picture of the scope of applications that are integrating with the two applications.
On average, a company with 10,000 SaaS users using M365 has 2,033 apps connected to its suite of applications. Companies of that size using Google Workspace have more than three-times the amount, averaging 6,710 connected applications.
Even smaller companies aren't immune. The report found that companies using M365 average 0.2 applications per user, while those using Google Workspace average 0.6 applications per user.
In contrast to most growth curves, the research shows that the number of apps per user doesn't level off or plateau once reaching a critical mass of users. Rather, the number of applications continues to grow with the number of users.
As seen in figure 1, companies using Google Workspace with 10,000-20,000 employees average nearly 14,000 unique connected applications. This continued growth is shocking to security teams, and makes it nearly impossible for them to manually discover and manage the high volume of applications.

When third-party apps integrate with core SaaS apps, they gain access using an OAuth process. As part of this process, applications request specific scopes. These scopes hand over a lot of power to the apps.

Among high-risk scopes, 15% of M365 applications request the authority to delete all files that the user can access. It gets even scarier in Google Workspace applications, where 40% of high-risk scopes receive the ability to delete all Google Drive files.
As shown in this permission tab, the application explicitly requests permission to see, edit, create, and delete all Google Docs documents, Google Drive files, Google Slides presentations, and Google Sheets spreadsheets.
For security teams accustomed to controlling the data, permission sets like these are unsettling. Considering that many applications are created by individual developers who may not have prioritized security in their software development, these permissions provide threat actors with everything they need to access and steal or encrypt company data. Even without a threat actor, a bug in the software can have disastrous consequences for a company's data.
While the report deep dives into the big two SaaS apps, it does also release research into Salesforce (and Slack). Salesforce averages 41 integrated apps per instance. The implication of this is noteworthy.
Salesforce is primarily used by a small subset of the company. In that regard, it's similar to Workday, Github, and ServiceNow, which are used by HR, developers, and finance teams. A typical company with 10,000 employees has over 350 SaaS applications in its stack, many of which are used by smaller departments like the apps discussed here.
Assuming Salesforce is typical of similar applications, those 350 apps integrating with 40 apps each adds an additional 14,000 third-party applications into the equation.
One of the more interesting takeaways was the high volume of high-risk apps connecting to Microsoft compared to Google Workspace. Apps request high-risk permissions from M365 39% of the time; Google Workspace apps only request high-risk permissions 11% of the time. In terms of real numbers, an average installation in a company with 10,000 SaaS users using M365 will have 813 high-risk apps, while Google Workspace will have 738 apps that are considered high-risk.
In all likelihood, this disparity is caused due to the app creation process. Google requires apps requesting high-risk (it calls them Restrictive) permissions to be reviewed. The review process is far easier for those requesting medium, or sensitive, permissions. Microsoft doesn't label requested scopes with severity levels. This lack of oversight makes it much easier for apps that connect with M365 to request high-risk scopes.
The overall takeaway from reading the report is the immense challenge of securing SaaS software. It's clear that security teams need visibility into the thousands of apps being connected to the SaaS stack, and make a cost-benefit analysis for each high-risk connected app.
SaaS security solutions, like Adaptive Shield, provide security teams with the visibility needed to see connected applications and their scopes, among other important SaaS security capabilities. Armed with this information, security teams will be in a far better position to harden their applications' security posture and prevent data from falling into the wrong hands.


Tel Aviv, February 27, 2023—Adaptive Shield, the leading SaaS Security company, today announced the release of its SaaS-to-SaaS Access Report. According to the research, employees are granting thousands of third-party apps access to the two most dominant workspaces, Microsoft 365 (M365) and Google Workspace. With no oversight or control from security teams, companies have no way to quantify the risk that these SaaS-to-SaaS connections present to their businesses.
While these SaaS-to-SaaS connections provide enhanced features that boost workflow efficiency, they also give permission for apps to read, update, create, delete, or otherwise engage with corporate and personal data. In its report, Adaptive Shield identifies how many SaaS apps are being connected to the core SaaS stack, specifically M365 and Google Workspace and business-critical apps such as Salesforce and Slack, the types of permissions being granted to these applications, and the risk level these apps present.
According to the research, companies with 10,000 SaaS users average 2,033 applications connected to M365 and 6,710 connected to Google workspace. For the companies using Google Workspace, that figure jumps to an average of 13,913 connected apps for 10,000 - 20,000 SaaS users.
While the risk level for permissions varies from one app to the next, Adaptive Shield researchers found that 39% of apps connected to M365 and 11% to Google Workspace have ‘high-risk’ permission access. Additional details on these include
“The simple app-to-app connectivity that makes SaaS apps vital productivity tools also makes them significantly dangerous,” said Maor Bin, CEO of Adaptive Shield. “While it’s clearly unrealistic to expect businesses to curb their reliance on SaaS apps, they cannot allow this adoption to go unchecked. To eliminate these risks companies must develop policies for integrating apps, prioritize employee training, and deploy monitoring solutions that help over-taxed security teams identify and eliminate high-risk permission sets before it’s too late.”
While these challenges are most prominent in M365 and Google Workspace, they are not exclusive to these apps. As part of this effort, Adaptive Shield examined two other business-critical apps, Slack and Salesforce. The research shows that organizations have an average 222 SaaS-to-SaaS apps for Slack and another 41 apps for Salesforce.
A final area of research are app categories that are connected most frequently. According to the research, email applications are far and away the number one connected category followed by apps related to file and document management, communications and meetings, and calendars and scheduling.
The Adaptive Shield full report, 2023 SaaS-to-SaaS Access Report: Uncovering the Risks & Realities of Third-Party Connected Apps, is available now.


Forrester, a research and advisory company, offers organization’s a variety of services including research and consulting. Their reports help professionals understand their customer’s behavior, concerns, and interests to help organizations make more informed decisions. Their Trend Report ‘Embrace A Paradigm Shift In SaaS Protection: SaaS Security Posture Management’ looks at the increased use of SaaS apps and the value of an SSPM solution. This blog will summarize key takeaways from the report.
Click here to read the full report.
“Organizations’ cloud-first or on-premises augmentation strategies caused an explosive, decentralized, and uncontrolled growth of SaaS application use. Consequently, the increase in the number of cloud assets has also increased overall IT risks.”
The ease with which SaaS apps can be adopted is remarkable, but it has become a double-edged sword. The cloud has enabled organizations to store and manage near endless data and scale their operations, but it has opened the doors for relentless attackers and new attack vectors. Organizations have dozens to over a hundred different SaaS apps critical to maintaining day-to-day operations, each with nuanced access patterns from sharing, uploading, downloading, sorting, searching, and filtering activities.
Access patterns and activities, when looked at individually, may appear harmless. However when looked at as part of a bigger picture, security teams can often quickly identify risk by spotting unusual behavior, suspicious geolocations movements, and uncommon access requests. Organizations not only gain visibility into different domains and activities but also monitor data movement to and from SaaS apps to help detect threats.
The skills shortage and gap between application owners and security teams only adds to the challenge. The report found that even the largest organizations interviewed stated that they lack the resources needed to fully understand the connectivity between SaaS apps and their security implications. Organizations are in dire need of a security solution, such as an SSPM, which is able to provide visibility and understanding into these apps.
In turn, an effective SSPM needs to be able to integrate with all their apps to support the organization's security policies and goals. Contextualized visibility into each app helps security teams prioritize configuration weaknesses and increase time and efficiency to remediation across multiple attack surfaces.
“SSPM solutions differ in breadth and depth of SaaS app coverage”
Simply put, not all SSPM solutions are created equal. SSPMs can vary in the amount of apps they support, the thoroughness of their security checks, and the range of their capabilities. Forrester describes needed functionalities within the organization’s chosen SSPM solution:

At Adaptive Shield, we like to boil it down to four main use cases: misconfiguration management, SaaS-to-SaaS access discovery, device-to-SaaS user management, and identity and access management governance. An SSPM will present detailed and dedicated security checks within each of these use cases.
The 2023 SaaS Security Posture Management Checklist covers all the critical features and capabilities to look out for when evaluating a solution.
“SSPM solutions can make recommendations on how to trim business users’ privileges without impeding their user experience (i.e., they continue to have access to data and the SaaS application functionality that they need to do their jobs without access to data they do not need).”
An SSPM’s user inventory is one of many critical features. A user inventory helps security teams gain visibility of users, their privileges, and user-specific failed security checks. By gaining in-depth knowledge of user permissions and behavior, security teams can identify inactive users, overprivileged admins, and other user-specific threats. SSPMs can help trim unnecessary user privileges without limiting access to the data needed to complete their work.
The report outlines the following identity and access management related SaaS settings that SSPM solutions can enforce.
It's not surprising that SaaS apps do not properly guard organization’s data and are susceptible to data breaches. SSPM solutions provide relief to security experts by offering data protection features such as:


Imagine this: a company-wide lockout to the company CRM, like Salesforce, because the organization's external admin attempts to disable MFA for themselves. They don't think to consult with the security team and don't consider the security implications, only the ease which they need for their team to use their login.
This CRM, however, defines MFA as a top-tier security setting; for example, Salesforce has a "High Assurance Login Value" configuration and immediately locks out all users as a safety precaution. The entire organization hits a standstill and is frustrated and confused.
Deeply concerning, this is not a one-off event, admins for business-critical SaaS apps often sit outside the security department and have profound control. Untrained and not focused on security measures, these admins are working towards their departmental KPIs. For instance, Hubspot is usually owned by the marketing department, likewise, Salesforce is often owned by the business department, etc. Business departments own these apps because it's what allows them to do their job efficiently. However, the paradox lies in the fact that it's the security team's responsibility to secure the organization's SaaS app stack and they cannot effectively execute this task without full control of the SaaS app.
The 2022 SaaS Security Survey Report, conducted by CSA and Adaptive Shield, delves into the reality of this paradox, presenting data from CISOs and security professionals today. This article will explore important data points from the respondents and discuss what the solution for security teams could be.
Across a typical organization, a wide array of SaaS apps are used (see figure 1), from cloud data platforms, file sharing and collaboration apps to CRM, project and work management, marketing automation, and a whole lot more. The need for each and every SaaS app fills a certain niche role required by the organization. Without the use of all these SaaS apps, a business could find itself lagging or taking more time to achieve its KPIs.

The 2022 SaaS Security Survey Report reports that 40% of these apps are managed and owned by non-security teams, such as sales, marketing, legal, etc. (see in figure 2). While the security and IT teams are reported to be the main destination for SaaS app management, it's the 40% of business departments also taking part and having full access that complicates the threat landscape.
Security teams can't take away this ownership as the business applications' owners need to maintain a high level of access to their relevant SaaS apps for optimal use. Yet, without in-depth knowledge of security or the vested interest (a security KPI that reflects on their work product), it's not reasonable for the security team to expect that the business owner will ensure a high level of security in their SaaS.

When asked the main reason for misconfiguration-led security incidents (figure 3), respondents of the survey report cited these as their top four: (1) There are too many departments with access to security settings; (2) Lack of visibility to security settings when they are changed (3) Lack of SaaS security knowledge; (4) Misappropriated user permissions. All of these reasons, either overtly or implied, can be attributed to the SaaS App Ownership Paradox.

The leading cause of security incidents caused by misconfigurations is having too many departments with access to security settings. This goes hand in hand with the next cause – lack of visibility when security changes are changed. A business department may make changes to an app setting to optimize its ease of use without consulting with or notifying the security department.
In addition, misappropriated user permissions can easily stem from a business department owner at the helm who is not paying careful attention to the app's security. Often users are granted privileged permissions that they don't even need.
With this shared responsibility model, the only efficient way to bridge this communication gap is through a SaaS Security Posture Management platform (SSPM). With an SSPM solution, owned and managed by the organization's security team, the security team can gain complete visibility of all the company's SaaS apps and their security settings, including user roles and permissions.
Organizations can take it one step further and have the app owners join the SSPM platform so they can actively control and oversee all configurations in their owned apps. By using a scoped admin capability (figure 4) the security team can grant the app owners access to the apps they own and can remediate security issues, with their supervision and direction.

There's no way to eliminate business departments' access to SaaS app security settings, and while users across the organization should be educated on basic SaaS security in order to reduce the risk that may occur from business departments, it doesn't always happen or it's just not enough. Organizations need to implement a solution that helps avoid these situations by enabling visibility and control for the security team, including alerting on configuration drifts and audit logs that provide insight into actions within the SaaS apps and scoped admins.


Another day, another attack method.
GIFShell attack technique enables bad actors to exploit several Microsoft Teams features to act as a C&C for malware, and exfiltrate data using GIFs without being detected by EDR and other network monitoring tools. The technique assumes an already-compromised target.
Discovered by Bobby Rauch, the main component of this attack allows an attacker to create a reverse shell that delivers malicious commands via base64 encoded GIFs in Teams, and exfiltrates the output through GIFs retrieved by Microsoft's own infrastructure.
How does it work?
As reported by Lawrence Abrams in BleepingComputer, Microsoft agrees that this attack method is a problem, however, it “does not meet the bar for an urgent security fix.” They “may take action in a future release to help mitigate this technique.” Microsoft is acknowledging this research but asserting that no security boundaries have been bypassed.
While Rauch claims that indeed “two additional vulnerabilities discovered in Microsoft Teams, a lack of permission enforcement and attachment spoofing”, Microsoft argues, "For this case… these all are post exploitation and rely on a target already being compromised.” Microsoft is asserting that this technique is using legitimate features from the Teams platform and not something they can mitigate currently.
In accordance with Microsoft's assertions, indeed this is the challenge many organizations face — there are configurations and features that threat actors can exploit if not hardened. A few changes to your tenant’s configurations can prevent these inbound attacks from unknown Teams tenants.
There are security configurations within Microsoft that if hardened can help to prevent this type of attack.
Microsoft Teams by default allows for all external senders to send messages to users within that tenant. Many organization admins likely are not even aware that their organization allows for External Teams collaboration. You can harden these configurations:

Endpoint security tools are your first line of defense against suspicious activity such as accessing the device's local teams log folder which is used for data exfiltration in GIFShell. You can ensure your entire organization's devices are fully compliant and secure by using your XDR / EDR / Vulnerability Management solution, like CrowdStrike or Tenable.
You can even go a step further and integrate an SSPM (SaaS Security Posture Management) solution, like Adaptive Shield, with your endpoint security tools to gain visibility and context to easily see and manage the risks that stem from these types of configurations, your SaaS users and their associated devices.


According to Okta's Business of Work report, large companies use 187 different SaaS apps on average, and this number is only growing—Gartner reports that end-user spending on SaaS will reach more than $171 billion in 2022.
As this investment trend continues, new critical SaaS challenges emerge beyond the classic use case of misconfiguration and user permissions management, such as SaaS-to-SaaS access and device-to-SaaS-user posture management. This blog will give a brief overview of the trends in SaaS security.
An Unrelenting Volume Of Misconfigurations
Core SaaS offerings such as Office 365, Slack, Zoom and Salesforce, as well as the myriad of other SaaS apps that companies have deployed, are vital to a business's day-to-day operations. While these benefits are widely recognized, many companies are just now beginning to learn about the risk they introduce to the company.
Case in point, while app providers build in native security settings and configurations designed to protect businesses, the solutions can only be as secure as their weakest security control. This means that it is up to the organization to correctly configure all settings, continuously.
While that may seem straightforward, many don't consider how apps are like snowflakes when it comes to their build and security configurations—each has unique terminology, UI, etc. It is the security team's job to learn every app's "language." While that might not seem insurmountable, consider that many enterprises today have thousands of employees relying on hundreds of apps. This creates a chaotic SaaS environment where manual audits become impossible and unsustainable.
SaaS-to-SaaS Access Discovery and Control
Another growing SaaS challenge stems from SaaS-to-SaaS apps connected to the company’s core SaaS applications, also known as SaaS-to-SaaS supply chain. Today, employees are frequently prompted to give permission for one SaaS app to connect with another, and, for the most part, they oblige. That's where the problem begins. Today most users view this scenario from a productivity perspective—if they connect their SaaS apps, it will allow them to work more efficiently and ultimately help the business achieve its goals.
Every day, people give apps permission to connect with their Google Workspace or M365 environment (for example). By just clicking "accept," they give these apps permission to provide a new avenue for threat actors to gain access to valuable company data.
Now imagine this practice is happening throughout a business's workforce unbeknownst to the security team. The security team needs to see:
1. The SaaS apps that are being granted access to business-critical apps.
2. Which of these apps pose the most risk by the level of scopes (permissions) being given.
3. Which users, most especially the privileged users, granted them.
The security team needs to be equipped to decide whether to revoke access to these apps to the core SaaS apps, protecting the business yet still ensuring that the employee maintains the functionality required to do their job.
Device-To-SaaS Posture Management: The SaaS Security Zero-Trust Approach
In today’s hybrid working world, security teams must contend with threats of users accessing their SaaS applications from unsecured devices. While accessing a SaaS app via a mobile device helps boost productivity, it adds another challenge to the security team. It can pose a high level of risk for an organization, especially when the device owner is a highly privileged user.
To remediate potential threats, security teams need to be able to correlate SaaS app users, roles and permissions with their associated devices' hygiene. This end-to-end tactic enables a holistic zero-trust approach to SaaS security that is only now coming into the picture.
The Whole SaaS Security Picture
The bottom line is that checking for misconfigurations and misappropriated user roles and permission within business-critical SaaS apps is the classic SaaS Security Posture Management (SSPM). However, if the organization adopts a zero-trust approach, it is worth considering SaaS-to-SaaS access and device-to-SaaS-user monitoring and management an integral part of SSPM.
This is an excerpt from an article that was published in Forbes Council on August 10, 2022.


Typically, when threat actors look to infiltrate an organization’s SaaS apps, they look to SaaS app misconfigurations as a means for entry. However, employees now use their personal devices, whether their phone or personal laptop, etc. to get their jobs done. If the device’s hygiene is not up to par, it increases the risk for the organization and widens the attack surface for bad actors. And so, Endpoint (Device) Protection — through EDR, XDR, and vulnerability management solutions – has arisen as a critical factor in SaaS Security.
The challenge in remediating the threats posed by endpoints and devices lies in the ability to correlate between the SaaS app users, their roles, and permissions with their associated devices' compliance and integrity levels. This end-to-end approach is what's needed for the organization to implement a holistic, zero-trust approach for their SaaS Security.
Not a simple feat, however, automated SaaS Security Posture Management solutions, like Adaptive Shield, can now provide visibility that correlates the SaaS user and their associated devices with the device’s hygiene score.
How do you classify high-risk devices in the context of SaaS security?
Devices that are owned, or used by users with high levels of permissions to the company’s core SaaS apps. For example, someone who has high levels of access to the company’s CRM can present a high risk to the company if their device is vulnerable and this needs to be remediated immediately. These high-risk devices serve as a critical threat vector to an organization’s SaaS environment.
Security teams should continuously map devices to their users and their associated permissions to get a handle on which devices/users pose the highest risk.
As mentioned, the more privileged the user, the higher their device is at risk. To gain deep observability into the user, app and device posture, security teams need to check the hygiene of their users’ devices, for example up-to-date OS configurations, and any vulnerabilities. With that assessment and score in hand, security teams can map and monitor the user’s SaaS app access (in addition to, of course, securing the SaaS apps themselves).
Once these cross references are in place and accessible, organizations can enable “soft” enforcement enhancements, through policies and organizational best practices. This way security teams can monitor risks and threats without severely limiting the user.
Zero-trust is a concept much batted about in cybersecurity vernacular today. While many consider it a buzzword, its meaning represents an important approach that can not be emphasized enough. To wholly secure the organization’s SaaS stack, end-to-end, and continuously, calls for a holistic and automated solution.
Adaptive Shield has been built to resolve not only the need for management of the SaaS app configurations themselves, but also the devices the organization’s employees use. (Not to mention third party app access — and you can read more about that here.) When integrated with MDM (mobile device management) solution, Adaptive Shield will pull the device data and map the device to the owner.

By looking at the device posture while conducting a SaaS security assessment, organizations can achieve a holistic zero trust approach.


When it comes to keeping SaaS stacks secure, IT and security teams need to be able to streamline detection and remediation of misconfigurations in order to best protect their SaaS stack from threats. However, while companies adopt more and more apps, their increase in SaaS security tools and staff has lagged behind, as found in the 2022 SaaS Security Survey Report.
The survey report, done in collaboration with CSA, dives into how CISOs today are managing the growing SaaS app attack surface and the steps they are taking to secure their organizations. While there are 7 significant takeaways from the report, this blog takes a closer look at the 5th finding - how the use of an SSPM reduces the amount of time it takes to to detect and remediate SaaS misconfigurations.
The report finds that at least 43% of organizations have experienced a security incident as a result of a SaaS misconfiguration, however with another 20% being “unsure”, the real number could be as high as 63%. These numbers are particularly eye-opening when compared to the 17% of organizations experiencing security incidents due to an IaaS misconfiguration. Bearing this in mind, the question follows: how fast are SaaS misconfigurations detected and how long does it take to remediate the issue? In order to answer these questions, it's important to make a distinction between organizations that have implemented an SSPM solution and those that have not.
For organizations that are yet to onboard an SSPM, the IT and security teams can only manually check the apps’ many configurations to secure their SaaS stack. This means security teams need to not only be on top of remediating misconfigurations but also conducting regular security checks in order to manually detect any of these misconfigurations. The longer either of these actions take to be completed, the longer the company is exposed to threats.
One of the major problems for organizations’ security teams is the overwhelming amount of manual work. Companies today are reliant on dozens upon dozens of business-critical apps each with hundreds of configurations, which then need to be set according to the hundreds to thousands of employees.
Nearly half (46%) of the survey respondents, as seen in figure 2, check their SaaS security monthly or less frequently, and another 5% don’t check at all. It seems that security teams are overwhelmed with the workload, and are struggling to stay on top of all the settings and permissions. As organizations continue to adopt more and more apps, their gap of visibility into all configurations grows.

When a security check fails, security teams must then go in and understand why exactly the check failed and the best course of action to fix it. Approximately 1 in 4 organizations, as seen in figure 3, take one week or longer to resolve a misconfiguration when remediating manually. Overall, security teams trying to manage their SaaS security are not only overwhelmed but are also in turn leaving the organization exposed for a longer period of time.

Organizations using SSPM are able to conduct security checks more often and remediate misconfigurations within a shorter time frame. An SSPM enables security teams to conduct frequent checks in compliance with both industry standards and company policy. The 2022 SaaS Security Survey Report found that the majority of these organizations (78%) run security checks once per week or more often, as seen in figure 4.

When a misconfiguration is detected, 73% of organizations using an SSPM resolved it within a day, and 81% resolved it within the week, as seen in figure 5. A good SSPM solution however will not only evaluate failed security checks caused by misconfigurations, but will also assess risk and configuration weakness — and provide exact instruction on how to remediate the issue.

SSPM not only reduces the workload on security teams, but also eliminates the need for them to be experts on each SaaS app and its settings. The data presented in the 2022 SaaS Security Survey Report highlights the drastic differences between companies using SSPM and those not, showing how valuable SSPM is to SaaS security detection and remediation.


“How many people do you know that clean their house once a quarter? …you have to keep a certain level of hygiene both in your house and your SaaS stack.”
Uttered by our CEO, Maor Bin, in a webinar with Omdia Senior Principal Analyst, Rik Turner about the growing need to take a proactive, automated approach to SaaS security. Here are some highlights from the webinar - catch the whole webinar in full here.
Rik Turner begins the webinar by reflecting on the emergence of SaaS apps in the early 1990s leading up to 2010. “The world of SaaS apps grew rapidly and for good reason,” Rik explains, “SaaS is so easy that once you’ve adopted it, someone in the next business unit comes and says ‘oh you guys are using that? That looks great’ and next thing you know half the company is using something that nobody in IT even sanctioned.” Security teams need control and visibility to all the configurations of the company’s SaaS apps in use.
By 2014, Cloud Access Security Broker (CASB) had reared its head as a powerful cloud security solution to address the above mentioned issue. CASBs proved effective in helping restore visibility to the IT and security teams, however, as a reactive solution, there was still no preemptive approach for giving visibility to all the (mis)configurations across the growing SaaS app stack. It wasn't long after that Gartner brought SSPM into the playing field with its SaaS specific security solution.
An SSPM’s job is to maintain continuous hygiene across a SaaS stack by continuously monitoring all the SaaS security risks and automatically identifying if all the native security controls are correctly configured. By doing so, SSPM offers businesses a preventative SaaS security solution.
The webinar pulls findings from the 2022 SaaS Security Survey Report to demonstrate the current state and perception of SSPM. Rik Turner highlights the significant correlation between SaaS misconfigurations and security incidents, showing that up to 63% of security incidents are caused by a SaaS misconfiguration.

“This kind of datapoint isn't very surprising. We are always talking about how configurations are the number one attack vectors. They’re the number one threat for companies when we’re talking about cloud security. These small mistakes can lead to very, very serious problems - account takeover, data leakage, and more,” asserts Bin.
SaaS apps have changed the way security and IT teams think about security. Gone are the days of security teams being experts on every company program or system. It becomes impossible for security teams to be familiar with the in and outs of every SaaS app. The fact of the matter is that while companies have quickly implemented new SaaS apps, they have lagged behind when growing their security teams and tools. There is a reported 81% increase in SaaS apps but only a 73% increase in security tools and a lesser 55% increase in security staff. This is causing security teams to be overburdened which in turn creates a cycle of companies leaving themselves exposed.

Simply put, security teams today don't have the capacity to manually configure every SaaS setting in an effective way. Nearly half of the security teams today attempting to do so are only checking their SaaS security settings monthly or less often — 15% are checking quarterly.
Meanwhile as Rik Turner points out, companies that have embraced SSPM have provided security teams with deep visibility into their SaaS stack security allowing them to deal with the misconfiguration threats.

Businesses and organizations are inseparable from the use of their SaaS apps. Bin and Turner address these issues and more in the full webinar, giving further insight to how the world of SaaS is growing and how SSPM is taking a proactive approach to securing businesses’ SaaS stacks.
“As these numbers show, once you introduce an SSPM, it dramatically improves an organization’s ability to detect and remediate these misconfigurations.” Turner.


Last year, we spearhead our first annual SaaS Security Survey Report, where the findings illuminated the SSPM landscape and where the market was holding. In the 2022 SaaS Security Survey Report, in collaboration with CSA, we examine the state of SaaS security in today’s enterprises and see how much the market and the overall space of SSPM has matured in just one year. This report gathers anonymous responses from 340 CSA members, CISOs and security professionals, to examine not only the growing risks in SaaS security but also how these different organizations are currently working to secure themselves. While there are many takeaways from the survey, these are our top seven.
Demographics
Before diving into the findings, here is some quick background information on the anonymous respondents. The majority (71%) of respondents were located in the Americas, another 17% from Asia, and 13% from EMEA. Of these participants 49% influence the decision making process while 39% run the process itself. The survey examined organizations from a variety of industries, such as telecommunications (25%), finance (22%), and government (9%). For more details regarding the demographics, please refer to full report.

Since 2019, SaaS misconfigurations have become a top concern for organizations, with at least 43% of organizations reporting they’ve dealt with one or more security incidents caused by a SaaS misconfiguration. However, since many other organizations state they are unaware if they had experienced a security incident, the number of SaaS misconfigured-related incidents could be as high as 63%. These numbers are striking when compared to the 17% of security incidents caused by IaaS misconfigurations.

So what exactly is the cause of these SaaS misconfigurations? While there are several factors to consider, the survey respondents narrow it down to the two leading causes – having too many departments with access to SaaS security settings (35%), and a lack of visibility into the changes in the SaaS security settings (34%). These are two related issues, neither of which are surprising given that lack of visibility was rated a top concern when adopting SaaS applications, and that on average organizations have multiple departments with access to security settings. One of the leading reasons for the lack of visibility is the fact that too many departments have access to security settings and many of these departments don't have proper training and focus on security.

It’s well-known that businesses are adopting more apps – this past year alone, 81% of respondents say that they have increased their investments in business-critical SaaS applications. On the other hand, investment in security tools (73%) and staff (55%) for SaaS security is lower. This dissonance represents an increasing burden on the existing security teams to monitor SaaS security.

46% of organizations that manually monitor their SaaS security are conducting checks only once a month or less, while 5% don't conduct checks at all. After discovering a misconfiguration, it takes additional time for security teams to resolve it. Approximately 1 in 4 organizations take one week or longer to resolve a misconfiguration when remediating manually. This lengthy timing leaves organizations vulnerable.


The flip side of the coin for finding #4 is that the organizations that have implemented an SSPM can more quickly and accurately detect and remediate their SaaS misconfigurations. The majority of these organizations (78%) utilize an SSPM to check their SaaS security configurations once a week or more. When it comes to resolving the misconfiguration, 81% of organizations using an SSPM are able to resolve it within a day to a week.


Third party apps, also called no-code or low-code platforms, can boost productivity, enable hybrid work, and are overall essential in building and scaling a company’s work processes. However, many users quickly connect 3rd party apps without considering what permissions these apps are requesting. Once accepted, the permissions and subsequent access granted to these 3rd party apps could be harmless or as malicious as an executable file. Without visibility into the SaaS-to-SaaS supply chain employees are connecting to their organization’s business-critical apps, security teams are blind to many potential threats.

Despite the category being introduced to the market two years ago, it is fast maturing. When assessing four cloud security solutions, SSPM receives an average rating of “somewhat familiar”. Furthermore, 62% of respondents report that they are already using an SSPM or plan to implement one in the coming 24 months.

The 2022 SaaS Security Survey Report offers insights into how organizations are using and protecting their SaaS applications. It is without a doubt that as companies continue to adopt more business-critical SaaS apps, there is more risk. To face this challenge head on companies should begin securing themselves through two best practices:
These kinds of best practices will provide support to security teams without preventing them or any other departments from doing their work.


It’s without a doubt that the SaaS app attack surface has been continuing to grow as businesses have become more reliant on apps to organize and run their business-critical operations. To better understand how teams are dealing with their SaaS security posture, Adaptive Shield partnered with the leading organization dedicated to promoting best practices for ensuring cyber security, Cloud Security Alliance (CSA), to develop the 2022 SaaS Security Survey Report.

The goals of the study was to understand the current state SaaS security through investigating the following key areas of interest:
The 2022 SaaS Security Survey Report offers insight into the industry knowledge, attitudes, and options regarding SaaS security and related misconfigurations.
Maor Bin, CEO and co-founder of Adaptive Shield says:
“This survey shines a light on what CISOs and cybersecurity managers are looking for and need when it comes to securing their SaaS stack — from visibility, continuous monitoring and remediation to other ever-growing, critical use cases such as 3rd party application control and device posture monitoring. The SSPM market is maturing rapidly — and this type of zero-trust approach for SaaS is where the SSPM market is going. ”
CSA gathered responses anonymously from 340 CSA members from IT and security professionals from various organization sizes, industries, locations, and roles. (Sponsored by CSA Corporate Members, the study’s content development and editing rights remained absent of added influence.)
Among the survey’s key findings:
The survey concludes by suggesting key methods of improving SaaS security to help organizations implement the preventive measures that could secure them from the next breach.
If you want to see all the details, like more of organizations top SaaS security concerns, their policy when dealing with unsanctioned SaaS applications, and different methods for monitoring SaaS security configurations, download the full survey.


The 2021 SaaS Security Survey report is a deep-dive on the state of SaaS security for today’s enterprises. It looks at the top risks that security professionals identify in their organizations, how CISOs feel about the security of an ever-growing SaaS-based environment, and how this concern impacts the approach they use for protecting and managing their cloud networks.
If you’re looking for an overview of the highlights of the report - you’re in the right place! Here are the key takeaways from this essential study, providing first-hand guidance and insight from 300 InfoSecurity professionals from the United States and Western Europe, in companies that range from 500 to more than 10,000 employees.
85% of today’s enterprises are aware that SaaS misconfigurations are a risk to their organization. This comes in at #3 in the list of cloud risks, after account hijacking and data leakage. Interestingly, many of the other risks that are on the list of threats can also arise due to misconfigurations, such as inadequate legacy protocols, insufficient identity checks, poor access controls for roles and credentials, or risky key management practices.

For example, if you don’t adequately govern information sharing with third-party SaaS providers, you could be opening yourself up to account hijacking. Similarly, a security misconfiguration in Jira led to data leakage for many Fortune 500 companies, including potentially disclosing email addresses and IDs, employee roles, current projects and milestones, and more.
If you factor in these cross-threats, where organizations admit they are worried about the “high risk” of insider threats, insufficient identity management, insecure APIs, and more - all of which can arise from misconfigurations, you can see how large the risk of SaaS misconfigurations really is.
The global SaaS market is estimated to continue to grow at a CAGR of more than 11% until 2025, with enterprises continuing to look for the benefits of fast time to market, subscription-based pricing, third-party expertise, and an interconnected ecosystem of best-of-breed players.
As organizations continue to onboard more applications, perhaps not enough thought is being placed on checking their corresponding security posture, which evolves every time a new SaaS application gains permissions and access to data, and every time this application updates.
91% of companies are checking the settings of their security applications at least quarterly, recognizing that configuration management is an important undertaking. Each application has its own interface, settings, permissions and data privileges, and these need a tight rein to ensure there aren’t glitches, configuration drift, or changes to employee access to consider.
However, the data uncovered that the more SaaS applications a company has under their roof, the less checks they will achieve. When a company has between 50-99 applications, just 12% of security teams manage to check permissions and configuration on a weekly basis. 40% of these companies are relying on quarterly checks, despite an agile working pipeline suggesting each of their apps will be updated every few weeks. In contrast, with under 10 apps to handle, the percentage of CISOs making weekly checks jumps to 35%.
This doesn’t change depending on how concerned the CISO in charge is about the security of their apps. Even when a CISO is worried about the security posture of between 75%-90% of their SaaS applications, if they have more than 50 apps to manage- they still fail to check them weekly more than 24% of the time.

The current best-case scenario is for CISOs that have confidence over the security of more than 90% of their apps, and even then - only 47% are managing to check them on a weekly basis. Overall, just 3% of companies check their SaaS applications for weaknesses and misconfigurations on a daily basis. A real-time view of all risks is simply out of reach for the majority of today’s enterprises.
It’s clear that regular checks of security settings for an ever-growing portfolio of SaaS applications is an impossible task. Security teams can’t stay on top of every new SaaS application, including how to navigate the settings, get comfortable with the UI, and understand its usage across the company.
Because of the scope of this challenge, we saw that respondents are regularly putting responsibility for checking and maintaining SaaS security into the hands of the SaaS owner. Unfortunately, these stakeholders often have little to no security background or skills, and may be Marketing managers, Product owners, or Sales personnel, to name just a few. This reality is happening in more than half of companies. The smaller the company size, the more of a problem this is, with less resources in place for security teams to take ownership over SaaS configuration and management.

According to Gartner, 99% of cloud security failures and the associated consequences are the customer’s fault. This tends to be understood as a concept related to the Shared Responsibility model. While your cloud provider will be held responsible for the underlying infrastructure of the cloud, your company holds full responsibility for applications, data, and settings of any information in the cloud.
While organizations might think they have outsourced security to their SaaS vendor, in reality the vendor can only offer security settings that work in a silo, targeted to their own product. With the best will in the world, they can’t take any ownership over the security of a multi-layered, complex environment that spans hundreds of applications and unknown quantities.
Gartner suggests that companies ask themselves, “Am I using the cloud securely?” rather than “Is the cloud secure?” In short - your cloud environment is only as secure as how you manage it.
With this fact in mind, the fact that more than half of today’s enterprises are delegating security process and management to the less-trained SaaS owner is problematic. If you consider that the area that they are delegating is what CISOs themselves call the highest cloud risk in their network, it becomes nothing less than negligent.
The report also uncovered that there is regularly an overlap in responsibility, where multiple stakeholders have access to the SaaS app settings. For example, the Security teams may have access, and perhaps they take overall responsibility for the security of the settings, but they also allow department heads to access and make changes to these apps, presumably for ease of use or quick changes. An example of this could be Marketing team leads holding control over the HubSpot account, or Sales owners being able to make changes in Salesforce. One out of four companies are currently working in this way, making it even more difficult for Security teams to stay on top of the challenge.
Human error is the single biggest risk to organizations who are working on the cloud. However, what we’ve seen about CISO’s level of concern suggests that security professionals already know that they need to make a change.
To summarize, with up to date insight from the report, we can isolate the greatest risks:
A new category of security tools is emerging to deal with these risks. As SaaS becomes the default system of record for organizations, SaaS Security Posture Management (SSPM) has been touted by Gartner amongst other technologies in its most recent hype cycle. These are defined by the analyst as “tools that continuously access the security risk, and manage the security posture of SaaS applications.”
Common tasks that SSPM tools take on, in order to continuously assess risk and identify misconfigurations across the SaaS estate, include:
As CSPM and CASB tools fail to address the challenges of a SaaS environment, SSPM has risen to the top of the enterprise agenda, and is the top pick in terms of priorities in 2021. 48% of respondents named SSPM tools as the #1 item on their priority list.

An emerging technology, just 8% are already using SSPM technology in their environment, which explains why so many are failing to check their applications in line with their growing concerns. However, 55% have SSPM on their radar, and only the remaining 37% aren’t currently planning to use this technology.
If you want to read the full report, just click here.


Remember when cybersecurity was mostly about firewalls, VPNs, and antivirus software? Those days are long gone. Now one of the most prevalent places for exploitation has to do with misconfigurations found in an organization's SaaS apps.
If you are in IT, you might have come across the following scenario: an admin of a business-critical SaaS app adds every user as an admin. Or they have used their admin privileges to turn off MFA because it’s too annoying and disrupts the workflow.
A recently published report found that 68% of enterprises consider cloud platform misconfigurations as the biggest threat to their cloud security. Another research from Cloud Security Alliance, 2021 State of Cloud Security, indicates that security misconfigurations are the main contributor for 22% of security incidents, second only to cloud provider issues (26%).
The list of possible misconfigurations, whether intentional or by mistake, can be endless. And unfortunately, these SaaS misconfigurations can lead to severe repercussions.
There are some exploited misconfigurations that are being used time and time again. Here are five examples from real-world attacks.
In May 2019, Salesforce self-sabotaged its security parameters by breaching itself. A scheduled update on Salesforce’s development systems disrupted the access permissions settings, giving employees of the organizations using the platform full access to Salesforce’s data.
The error not only allowed external users access to view or read sensitive information but also to ‘write’ permissions.
Salesforce fixed the error in access security controls but at the same time, accidentally created one of the biggest outages in the company’s history to take down access to 100 cloud instances.
60% of Microsoft Office 365 and G Suite tenants have been targeted with IMAP-based password-spraying attacks, according to researchers. The attackers target the legacy and insecure IMAP protocol to bypass MFA settings and compromise cloud-based accounts providing access to SaaS apps. It’s reported that Citrix was one such target in an ironic twist as they specialize in federated architectures, yet the FBI suggested that the attackers gained a foothold with password spraying and then bypassed additional layers of security.
The use of legacy protocols such as POP or IMAP, make it difficult for system administrators to set up and activate MFA. “Attacks against Office 365 and G Suite cloud accounts using IMAP are difficult to protect against with multi-factor authentication, where service accounts and shared mailboxes are notably vulnerable,” researchers say.
Security researcher Avinash Jain found a single security misconfiguration in the JIRA collaboration tool that opened up many Fortune 500 companies as well as NASA to a potential leak of corporate data and personal information. This information disclosure was the result of an authorization misconfiguration in Jira’s Global Permissions settings.
When the filters and dashboards for the projects/issues are created in JIRA, then by default the visibility was set to “All users” and “Everyone” respectively. Instead of sharing roadmap tasks etc. internally, it shared them publicly.
In March 2019, several companies unwittingly exposed sensitive corporate and customer data when their employees shared public links to files in their Box enterprise storage accounts.
Although data stored in Box enterprise accounts are private by default, users can share files and folders with anyone — if this user role configuration is enabled. The public sharing allows the any employee in the company to make the company’s data publicly accessible with a single click.
Security firm Adversis found that others outside an enterprise network can also discover these links. According to Adversis, Box admins should have reconfigured the default access for shared links to “people in your company” to reduce accidental exposure of data to the public.
This misconfiguration allowed Box users to expose a multitude of private information like passport photos, bank account and Social Security numbers, passwords, employee lists, financial data, invoices, and receipts.
There is a global setting in Zoom for the company to configure what happens when meetings are recorded. Can they be downloaded locally or only in the company’s protected cloud? Do they need a password or can they be saves without?
According to former NSA researcher Patrick Jackson, thousands of private Zoom recordings were exposed online when many recordings stored in Amazon Web Services (AWS) S3 buckets without passwords were found. The private videos ranged from elementary school remote classes, featuring the faces of students, to private therapy sessions, and business meetings including financial details.
The global setting to enforce password protection for recordings was critical in keeping these videos safer.
The absence of strong SaaS specific security measures allows attackers to take advantage — companies need deep visibility into their SaaS estate to monitor all settings, user permissions and configurations.
There are many solutions in cloud security, but the new category of SaaS Security Posture Management (SSPM), can assess a company’s SaaS security posture in a customized and automated manner that is tailored to the specifications of each application and aligns with company policy. And it’s not a one-time assessment; it is a continuous process that monitors and reinforces the company’s SaaS security.
The right SSPM solution, like Adaptive Shield, provides deep visibility and remediation for potential vulnerabilities in a company’s SaaS security posture, from misconfigurations and misappropriated privileges to suspicious SaaS usage. SSPMs are built to streamline and improve the security team’s efficiency, reducing their workload and stress while increasing protection for the company against any potential exposure or breach..
Now is the time to gauge your current SaaS security strength and to find out how to fortify your enterprise’s SaaS security posture.
This was first published in InfoSecurity Magazine on May 20, 2021.


We’re excited to announce that Adaptive Shield has made its debut on the Cyber 66, the Citizens JMP annual list of the hottest privately held cybersecurity companies. The annual survey highlights the 66 most well-positioned companies currently influencing the cybersecurity landscape.
In compiling the 2024 list, the researchers predicted 2024 would continue to be impacted by “high-profile breaches leveraging identity-based attacks.”
“Cybersecurity remains in a constant state of flux, with threat actors, the organizations they target, and the security tools that attempt to be the shield between the two continuously shifting their goals and related strategies,” Trevor Walsh, research analyst at the firm, said in the decision to add Adaptive Shield to the list in 2024.
Adaptive Shield is a key player in the growing arena of SaaS security, which includes SaaS Security Posture Management (SSPM) and ITDR categories, with the purpose of safeguarding companies amid the rapid increase in demand for SaaS applications, the report noted.
“We’re excited to be recognized as a leader in cybersecurity innovation at a critical juncture as SaaS becomes mainstream for business-critical activities,” said Maor Bin, CEO and co-founder of Adaptive Shield. “We remain committed to advancing SaaS security to help organizations protect their SaaS attack surface that is increasingly being targeted by sophisticated cyberattacks.”
Adaptive Shield covers more than 150 popular SaaS applications under its platform, enabling streamlined protection, detection, and response across an organization’s entire SaaS stack through Misconfiguration Management, SaaS-to-SaaS Access and Discovery, Identity Security Posture, Device-to-SaaS User Risk Management, and Identity Threat Detection & Response (ITDR).
The honor follows the additional investment secured by Adaptive Shield in 2023 from Blackstone Innovations Investments, bringing its total capital raised to $44M.
.png)
.png)
We've partnered with GuidePoint Security, the leading cybersecurity solution provider that helps organizations make better decisions that minimize risk. Through this partnership, GuidePoint Security's customers have the opportunity to expand their use of SaaS applications while staying secure.
As part of the Security Partner Program, Adaptive Shield’s SaaS Security Posture Management (SSPM) and Identity Threat Detection and Response (ITDR) solution is available through GuidePoint Security to address the risks associated with the usage of SaaS applications.
“Just like Cloud Security Posture Management (CSPM) is a necessity for cloud infrastructures, SSPM has now become the solution for every organization to implement to prevent and detect threats within SaaS environments,” said Maor Bin, CEO and co-founder of Adaptive Shield. “We look forward to working with GuidePoint Security, a leader in cybersecurity strategy, as Adaptive Shield continues its global expansion to fulfill the growing demand for comprehensive SaaS security.”
“Cyber-attack vectors are expanding across SaaS applications, challenging organizations’ security efforts with a new level of complexity,” said Justin Iwaniszyn, Director, New & Emerging Alliances, GuidePoint Security. “As threat actors become increasingly sophisticated, it's crucial for organizations to adopt comprehensive SaaS security strategies that effectively mitigate risk across their entire SaaS ecosystem."
Supporting a portfolio of 150 out-of-the-box SaaS integrations with leading business-critical applications, Adaptive Shield enables organizations to control and manage the security of their entire SaaS stack. Adaptive Shield’s capabilities include:
Originally announced on businesswire.com: https://www.businesswire.com/news/home/20240305787393/en/


Adaptive Shield is honored to announce that Frost & Sullivan recently assessed the Software-as-a-Service (SaaS) security posture management (SSPM) industry and based on its findings, recognizes Adaptive Shield with the 2023 Global Technology Innovation Leadership Award.
Ying Ting Neoh, research analyst for cybersecurity practice at Frost & Sullivan, said: “With continual enhancements to its SSPM technology offering to address customers’ pain points in the SaaS security space, the company is well-positioned as a technology innovation leader in the SSPM market.”
“Adaptive Shield has established a strong reputation and a steadily growing position in the global SSPM market. It is well positioned for continued growth, with its visionary and innovative platform for SaaS Security coupled with its established strategic partnerships and technology alliances,” added Neoh.
In the award, Frost & Sullivan states that Adaptive Shield offers an SSPM solution that helps customers secure their entire SaaS stack through risk management, threat prevention, and detection and response. Adaptive Shield’s SSPM platform provides a suite of capabilities with single-pane-of-glass visibility, such as:
In addition, Adaptive Shield’s SSPM platform expanded to enable over 140 out-of-the-box integrations of SaaS applications, making it the first and only SSPM solution provider with such a large number of out-of-the-box integrations. Its comprehensive security coverage of potential threats enhances visibility, security control, and application integration.
The SSPM platform also allows customers to easily manage sanctioned and unsanctioned applications connected to their core SaaS stack, regardless of the number of applications, thus minimizing the risk of SaaS-to-SaaS or third-party application access. This capability enables customers’ security teams to measure the access level to sensitive data across organizations’ SaaS stack while having advanced reporting capabilities that complement their risk assessments.
For its strong overall performance, Adaptive Shield was recognized with Frost & Sullivan’s 2023 Global Technology Innovation Leadership Award in the SaaS security posture management industry.
“Receiving Frost & Sullivan’s 2023 Global Technology Leadership Award in SaaS Security Posture Management is not just an accolade for Adaptive Shield, it’s a testament to our commitment in transforming the landscape of SaaS security,” said Maor Bin, CEO and co-founder of Adaptive Shield. “This recognition fuels our passion to not only protect, but empower businesses through revolutionizing the way they perceive and manage their SaaS security challenges.”
Each year, Frost & Sullivan presents this award to the company that has developed a product with innovative features and functionality that is gaining rapid acceptance in the market. The award recognizes the quality of the solution and the customer value enhancements it enables.
Frost & Sullivan Best Practices awards recognize companies in various regional and global markets for demonstrating outstanding achievement and superior performance in leadership, technological innovation, customer service and strategic product development. Industry analysts compare market participants and measure performance through in-depth interviews, analyses and extensive secondary research to identify best practices in the industry.


Today, we released that one of our customers achieved a 201% return on investment (ROI) in less than six months from adopting a SaaS Security Posture Management (SSPM) solution, according to results of a Forrester Consulting Total Economic Impact™ (TEI) study.
The 2024 Forrester Consulting TEI study is based on data from the customer experience of a global corporation with an annual revenue of over $10 Billion USD. The organization is undergoing rapid SaaS adoption across business-critical applications and has adopted Adaptive Shield’s SSPM platform in order to control and manage the security of their entire SaaS ecosystem.
The model Forrester designed to determine this ROI includes elements of SaaS Security score, operational efficiency against costs of a data breach like lost employee productivity, lawsuits and settlements, and regulatory fines.
“We started seeing some small incidents resulting from SaaS misconfiguration, so we needed to do something about it… The incident was a wake-up call for us that we really need to look at all the configurations at scale,” asserts the Chief Security Officer (CSO) of the $10 billion global media and information services corporation interviewed for the TEI.
After they brought on Adaptive Shield, the CSO shares, “When we look at the security score trends, we observed significant increase over time. In reality, the improvement is even greater because we have already fixed some issues during the POC (proof of concept).”
The financial analysis of the implementation of Adaptive Shield platform with this customer found benefits of $2.18 million over three years. The payback period on the original investment was less than six months. Results from utilizing Adaptive Shield included more efficient SaaS Security management with improved visibility for stakeholders, enhanced security compliance control, and increased collaboration between business and security teams.
“There is a common misconception that SaaS providers take care of the security of the organizations’ apps. While SaaS vendors invest a lot in their security, the market has now come to realize that it’s the organization’s ultimate responsibility to ensure that their apps’ security posture is monitored and managed internally. Similar to the case of IaaS and CSPM tools, ” says Maor Bin, CEO and co-founder of Adaptive Shield.
“With the frequency of SaaS attacks only growing and SaaS incidents continuously exposing organizations to data leaks, breaches, compliance failures, and other potential disruptions in business operations, SSPM is the only way for organizations to secure SaaS data. Beyond the qualitative, this TEI study quantitatively presents just how much Adaptive Shield helped improve our customer’s SaaS security and streamline business costs.”
Key benefits found in the study:


On October 7, 2023, as global news has reported, there was a brutal surprise attack by the Hamas terror organization on Israeli cities and villages. With thousands of civilian casualties, and hundreds taken hostage into the Gaza strip, Israel was forced to enter a state of war with Hamas.
At Adaptive Shield, our commitment to our team as well as to our customer’s business continuity are unwavering. This blog aims to shed light on the measures we are taking to ensure business continuity during these uncertain times.
Operational Resilience: We have large global teams across all departments, ensuring there is no business impact. We have also created business and tech readiness plans to adapt to changing circumstances, assessing potential scenarios to maintain operational continuity.
Communication Channels: Open and transparent communication is crucial. We will provide timely updates on any changes to our operations through various channels, keeping you informed and confident in our ability to navigate challenges.
Risk Mitigation: We are actively monitoring the situation and adjusting our strategies to mitigate potential risks. Our goal is to uphold the highest standards of service and protect the interests of our customers and partners.
Dedicated Support: Our dedicated customer success and support teams remain available to address any concerns or questions you may have. Your satisfaction and success are paramount to us, and we are committed to maintaining the quality of our relationships.
As we navigate these uncharted waters, Adaptive Shield remains steadfast. We understand the importance of stability and reliability in our relationships and partnerships, and we are confident in our ability to adapt, overcome, and emerge stronger together.
If you have any specific questions or if there's anything we can do to support you better, please don't hesitate to reach out.


We're excited to announce a new investment from Blackstone Innovations Investments, Blackstone's strategic investment arm, bringing our total capital raised to $44M. This investment will be used to accelerate Adaptive Shield’s mission to protect companies as the number of SaaS applications used by enterprises has continued to grow rapidly. This growth is creating a new and complex mesh of business-critical applications that are increasingly being targeted by attackers.
“With Blackstone's support, we will continue our trajectory for growth and expansion while keeping up with the constantly evolving threats.” - Maor Bin, CEO and Co-founder of Adaptive Shield
“Thinking about where attackers are going next is key to growing a world-class cybersecurity program that protects our brand, reputation, investors, and intellectual property,” says Adam Fletcher, Chief Security Officer at Blackstone. “We have partnered with and are using Adaptive Shield to help us continuously monitor the security posture of business-critical SaaS applications used across Blackstone to further protect the firm from attackers. We believe in Adaptive Shield’s mission and are excited to support the company with our investment as they enter their next stage of growth.”
With Adaptive Shield, organizations can prevent, detect, and respond to identity-centric SaaS threats through Misconfiguration Management, SaaS-to-SaaS Access and Discovery, Identity & Access Governance, Device-to-SaaS User Risk Management, and Identity Threat Detection & Response (ITDR).
"Blackstone's investment demonstrates its success with our offering and underscores Adaptive Shield’s innovative capabilities as the only SaaS security platform to integrate with more than 130 applications that covers an expansive SaaS attack surface,” said Maor Bin, co-founder and CEO at Adaptive Shield. “With Blackstone's support, we will continue our trajectory for growth and expansion while keeping up with the constantly evolving threats.”
"At Blackstone, we have a dedicated team of cybersecurity professionals advising hundreds of our portfolio companies to further strengthen the cyber defense across the entire Blackstone ecosystem,” says Adam Mattina, Deputy Chief Security Officer and Head of Portfolio Cybersecurity at Blackstone. “We view the SaaS ecosystem as one of the top emerging attack vectors today, and our usage and investment in Adaptive Shield is highly strategic for the broader Blackstone portfolio as we collectively strive to stay ahead of such threats.”
To learn more about Adaptive Shield’s different use cases, please visit the use cases overview page.
.png)
.png)
Adaptive Shield, June 13, 2023 – Adaptive Shield, an industry leader in SaaS security, today announces its partnership with leading cloud security provider Wiz as the company unveils Wiz Integrations (WIN). Adaptive Shield, hand selected as a launch partner, brings the power of SSPM to WIN, so that customers can seamlessly integrate Wiz into their existing workflows.
WIN enables Wiz and Adaptive Shield to share prioritized security findings with context including inventory, vulnerabilities, issues, and configuration findings. Mutual customers receive the following benefits:
The combined value of these two offerings will streamline security for organizations that are on a cloud journey, regardless of where they may be on that journey.
“This partnership enables security teams to complement CSPM security with SaaS security, providing security to cloud-based products. Additionally, this allows Security teams to make sure that the Wiz solution is secure, and detect any misconfigurations or threats to the security platform provided by Wiz” - Hananel Livneh, Head of Product Marketing
WIN is designed to enable a cloud security operating model where security and cloud teams work collaboratively to understand and control risks across their CI/CD pipeline. Wiz is setting the industry standard in integrated solution strategy to maximize operational capabilities of organizations with partners like Adaptive Sheild in WIN.


We are happy to announce that we have successfully earned the latest International Organization for Standardization (ISO) privacy certification ISO/IEC 27701:2019 ("ISO 27701") after an independent third-party audit by Standards Institution of Israel. Additionally, the company has successfully earned its Service Organization Control (SOC) 2 Type II certification, completed by Ernst & Young. These certifications, along with being GDPR compliant and ISO 27001 certified for many years, underscore Adaptive Shield’s unwavering commitment to the highest standards to protect its systems, users and data from constantly evolving risks and threats.
The ISO privacy standard includes requirements and provides guidance for establishing, implementing, maintaining and continually improving a Privacy Information Management System (PIMS). ISO 27701 builds on the International Standards Organization (ISO) 27000 series, a globally recognized framework for best practices in information security management.
“As a security organization, we are deeply committed to providing solutions to continuously monitor SaaS apps, users, and devices, and immediately identify, alert, and provide actionable remediation information, when needed,” said Maor Bin, our CEO. “As part of that core mission, it is our priority to maintain careful compliance with the global standards which protect data and the privacy of our customers, especially in increasingly complex SaaS environments and the evolving digital landscape.”
We recognize that SaaS apps like Microsoft 365, Slack, Zoom, and Salesforce are vital to the day-to-day operations of a business, but can often introduce security challenges. Featuring proactive, deep, continuous, and automated monitoring and management of business critical SaaS applications, Adaptive Shield’s SSPM platform allows security teams to gain control over these apps to harden security settings and reduce organizational risks.


Tel Aviv, February 27, 2023—Adaptive Shield, the leading SaaS Security company, today announced the release of its SaaS-to-SaaS Access Report. According to the research, employees are granting thousands of third-party apps access to the two most dominant workspaces, Microsoft 365 (M365) and Google Workspace. With no oversight or control from security teams, companies have no way to quantify the risk that these SaaS-to-SaaS connections present to their businesses.
While these SaaS-to-SaaS connections provide enhanced features that boost workflow efficiency, they also give permission for apps to read, update, create, delete, or otherwise engage with corporate and personal data. In its report, Adaptive Shield identifies how many SaaS apps are being connected to the core SaaS stack, specifically M365 and Google Workspace and business-critical apps such as Salesforce and Slack, the types of permissions being granted to these applications, and the risk level these apps present.
According to the research, companies with 10,000 SaaS users average 2,033 applications connected to M365 and 6,710 connected to Google workspace. For the companies using Google Workspace, that figure jumps to an average of 13,913 connected apps for 10,000 - 20,000 SaaS users.
While the risk level for permissions varies from one app to the next, Adaptive Shield researchers found that 39% of apps connected to M365 and 11% to Google Workspace have ‘high-risk’ permission access. Additional details on these include
“The simple app-to-app connectivity that makes SaaS apps vital productivity tools also makes them significantly dangerous,” said Maor Bin, CEO of Adaptive Shield. “While it’s clearly unrealistic to expect businesses to curb their reliance on SaaS apps, they cannot allow this adoption to go unchecked. To eliminate these risks companies must develop policies for integrating apps, prioritize employee training, and deploy monitoring solutions that help over-taxed security teams identify and eliminate high-risk permission sets before it’s too late.”
While these challenges are most prominent in M365 and Google Workspace, they are not exclusive to these apps. As part of this effort, Adaptive Shield examined two other business-critical apps, Slack and Salesforce. The research shows that organizations have an average 222 SaaS-to-SaaS apps for Slack and another 41 apps for Salesforce.
A final area of research are app categories that are connected most frequently. According to the research, email applications are far and away the number one connected category followed by apps related to file and document management, communications and meetings, and calendars and scheduling.
The Adaptive Shield full report, 2023 SaaS-to-SaaS Access Report: Uncovering the Risks & Realities of Third-Party Connected Apps, is available now.


Adaptive Shield has partnered with Datadog, the observability service for cloud-scale applications, to provide joint customers with the ability to stream and visualize SaaS security alerts from Adaptive Shield.
Adaptive Shield continuously monitors all SaaS apps, users, and associated devices, the platform immediately identifies, alerts, auto-fixes or provides actionable remediation information when any misconfiguration or security drift happens.
Datadog continuously monitors cloud applications, providing unified, real-time observability of customers’ entire technology stack including end-to-end traces, metrics, and logs. These originate from applications, infrastructure, and third-party services. These capabilities help businesses secure their systems, avoid downtime, and ensure customers are getting the best user experience.
Gilad Walden, VP of Product at Adaptive Shield asserts, “This partnership enables security teams to gain visibility, prioritize, and respond to SaaS Security configuration drifts reported by Adaptive Shield’s platform, within the Datadog dashboard”. Gilad continues, “This allows for an easy and streamlined incident management for all connected SaaS apps.”

This integration is one of the first OAuth integrations of Datadog with the added benefits of not having to enter API keys or application keys, reducing the risk of sensitive data leaks and simplifying the user experience.
How to Integrate

Once integrated, alerts are streamed into Datadog as Events and a dashboard is generated in Datadog for visualized alert analysis.
.png)
.png)
Tel Aviv, November 30, 2022—Adaptive Shield, the leading SaaS Security Posture Management (SSPM) company, today announced new capabilities to discover and monitor 3rd party apps connected to the core SaaS stack. With this new capability, Adaptive Shield is minimizing the risk that SaaS-to-SaaS, also known as 3rd party app access, presents. Security teams can now quickly and easily manage sanctioned apps and discover unsanctioned apps that have access to the company’s data.
Today’s modern workforces rely on SaaS apps to run their business — and employees in pursuit of productivity and efficiency connect hundreds to thousands of SaaS apps to the core stack, from the smallest plugin to more robust apps, without consulting the organization's security team. These employees connect apps without understanding the level of risk each presents, the types of permissions they are requesting, or whether the app itself is malicious. Without this departmental oversight, businesses cannot properly evaluate or manage their attack surface.
The challenge is exacerbated by the fact that 56% of organizations adopting SaaS apps state their top concern is the lack of visibility into connected apps, according to the 2022 SaaS Security Survey Report from Adaptive Shield and CSA (Cloud Security Alliance).
“As SaaS app dependency grows, so too does our comfort level in using these apps — this is why many grant access without considering the possible consequences. As a result, third-party app access has become the new executable file,” states Maor Bin, co-founder and CEO of Adaptive Shield. Bin continues, “Now, with these new capabilities, whether employees have connected 50 to 5000 apps, Adaptive Shield equips security professionals with the solution to regain control over their SaaS Security.”
Adaptive Shield recently announced their ability to integrate with 100+ SaaS apps, the first and only SSPM solution to provide this large number of out-of-the-box integrations. Their deep knowledge and expertise over the wide array of application characteristics, hubs and interconnected apps powers these new capabilities of 3rd party discovery within the Shadow IT domain.
From access scopes requested by these apps, to authorized users and cross referencing, the security team can now measure the level of access to sensitive data across the organization’s stack. In addition, the security team gains advanced reporting capabilities for effective and accurate risk assessments to drive actionable measures.
The original PR was released through Business Wire on Nov 30, 2022.


Tel Aviv, November 9, 2022—Adaptive Shield, the leading SaaS Security Posture Management (SSPM) company, today announced it is the first and only SSPM platform to cover 100 SaaS platforms and applications out of the box. Security teams will now be able to gain visibility and control of 100 SaaS apps and automate misconfiguration management, monitor SaaS-to-SaaS access, harden identity and access governance and manage SaaS risks stemming from user devices.
“It’s not enough to cover the core five business-critical apps,” asserts Gilad Walden, VP Product at Adaptive Shield. “While that is the start, an attack can come from any app. Security teams are also flying blind without visibility and control over a critical mass of their SaaS app stack. This is why the depth of security checks offered by each app’s integration is critical. Each of these 100 app integrations has been researched to ensure it provides comprehensive coverage of the potential threat models.”
Walden continues, “One of our favorite moments is seeing the customer’s reaction when they connect their entire SaaS stack. Instantly — and without any changes to their architecture — they gain deep visibility into all security controls and can finally identify and prioritize any potential threat.”
Adaptive Shield’s approach combats the widespread misunderstanding in the market about how organizations can best secure their SaaS stack and attain strong SaaS governance. Companies are investing solutions like CASB, manual audits, proprietary solutions, and others yet, their SaaS stacks remain unsecure.
In addition to the breadth, depth and context security teams gain for their SaaS app stack, Adaptive Shield’s flexible architecture enables security teams to keep up with the fast pace of new app releases and integrate on-demand.
Click to see the list of Adaptive Shield supported integrations
The original PR was released through Business Wire on Nov 9, 2022.


The ease with which SaaS apps can be deployed and adopted today is remarkable, but it has become a double-edged sword. On the one hand, apps are quickly onboarded, employees can work from anywhere, and there is little need for operational management. On the other hand, there are pain points that stem from the explosion of SaaS app usage, explained by the "3 V" s:
Named by Gartner as a MUST HAVE solution in the "4 Must-Have Technologies That Made the Gartner Hype Cycle for Cloud Security, 2021," SaaS Security Posture Management (SSPM) solutions come to answer these pains to provide full visibility and gain control of the company's SaaS security posture.
As one might expect, not all SSPM solutions are created equal. The Misconfiguration Management use case sits at the core of SSPM. However, there are more advanced use cases that tackle the emerging and growing challenges existing in the SaaS landscape.
When comparing SSPM options, here are some key features and capabilities to look out for (excerpted from the complete guide):
Run comprehensive security checks to get a clear look into your SaaS estate, at all the integrations, and all the domains of risk.
First and foremost for an SSPM's core solution, is the SSPM's ability to integrate with all your SaaS apps.
The other vital component to a core SSPM solution is the expanse and depth of the security checks. Each domain has its own facets for the security team to track and monitor.
Combat threats with continuous oversight and fast remediation of any misconfiguration
Remediating issues in business environments is a complicated and delicate task. The core SSPM solution should provide deep context about each and every configuration and enable you to easily monitor and set up alerts. This way vulnerabilities are quickly closed before they are exploited by cyberattacks.
SSPM vendors like Adaptive Shield provide you with these tools, which allow your security team to communicate effectively, shut down vulnerabilities, and protect your system.
Your SSPM solution should be easy to deploy and allow your security team to easily add and monitor new SaaS applications. Top security solutions should integrate easily with your applications and your existing cybersecurity infrastructure, to create a comprehensive defense against cyber threats.
In an effort to improve productivity, employees often extend the functionality of their primary SaaS applications by connecting them to a secondary SaaS app, or otherwise known as 3rd-party app access. These rights include the ability to read, create, update, and delete corporate or personal data. This access is granted in seconds, usually far outside the view of the IT and security teams, and significantly increases an organization's attack surface.
However, users rarely realize they've handed over significant permission rights to the new 3rd-party application. These 3rd-party applications, which can number in the thousands for larger organizations, all must be monitored and overseen by the security team.
To prevent secondary apps from providing an unauthorized gateway into your system, your SSPM solution should be equipped with the following capabilities:
Even before employees were routinely working from home, user devices posed a risk to corporate networks. Security teams had no visibility into the owners of different devices and couldn't ensure that the devices were secure. When individuals with advanced privilege levels use devices that are unsecured, they expand the attack surface with what amounts to an open gateway.
Track and monitor all device-to-SaaS user risk to eliminate surprise vulnerabilities
Associating Devices with Users
Over time, the number of users with access to different parts of an enterprise's system increases. While some users may move on, oftentimes they remain in the system and retain the same privileges that they had. Threat actors or disgruntled associates of the company can use these credentials to gain access to unauthorized areas of the system. Security teams need a tool to identify and disconnect these users from multiple environments and applications within the company. They also need to monitor every SaaS login and ensure that user activity meets security guidelines.
Identify all users with access to any system or application within the environment:
User Authorizations
Identifying Users
The Right SSPM solution PREVENTS your next attack.
SSPM is similar to brushing one's teeth: it's a foundational requirement needed to create a preventative state of protection. The right SSPM provides organizations continuous, automated surveillance of all SaaS apps, alongside a built-in knowledge base to ensure the highest SaaS security hygiene.
Get the complete guide along with the printable checklist here.


TEL AVIV, Israel - Sept 13 2022 - Adaptive Shield, the leading SaaS Security Posture Management (SSPM) company, today announced a partnership with Tenable, the Cyber Exposure Management company, to provide a consolidated posture management solution that correlates the risk of SaaS users and their endpoints.
While SaaS providers build in security features, it is the company’s responsibility to continuously cover all attack surfaces: from misconfigurations to identifying SaaS apps connected to the core SaaS app, while also detecting and remediating SaaS threats stemming from user devices with poor hygiene.
By correlating Tenable’s rich vulnerability insights within Adaptive Shield’s SaaS security posture technology, security teams will gain context and visibility to easily see and manage the risks that come from SaaS users and their associated devices. This partnership enables organizations to enrich their understanding of device and user posture and their influence on one another.
“When mitigating the SaaS attack surface, vulnerability management is an integral part of SaaS security hygiene, especially when it comes to privileged users and their device posture,” said Maor Bin, Co-Founder and CEO of Adaptive Shield. “By partnering with Tenable, we are proud to advance a new standard for organizations to protect their SaaS stack.”
“Understanding exposure and risk across SaaS deployments has never been more important than in today’s cloud-first world,” said Ray Komar, vice president of technical alliances, Tenable. “We’re excited to bring Adaptive Shield into our technology ecosystem, providing customers with increased visibility and context across their attack surface.”
For the full solution brief, take a look at our resources.
The original PR was released through Business Wire on Sept 13, 2022.


It's no secret that SaaS-to-SaaS apps can boost productivity, enable remote and hybrid work and are overall, essential in building and scaling a company's work processes.
It's an innocuous process much like clicking on an attachment was in the earlier days of email -- people don't think twice when connecting an app they need with their Google workspace or M365 environment, etc. Simple actions that users take, from creating an email to updating a contact in the CRM, can result in several other automatic actions and notifications in the connected platforms.
As seen in the image below, the OAuth mechanism makes it incredibly easy to interconnect apps and many don't consider what the possible ramifications could be. When these apps and other add-ons for SaaS platforms ask for permissions' access, they are usually granted without a second thought, not realizing that these addition connections present more opportunities for bad actors to gain access to their company's data.

How Do SaaS-to-SaaS Apps Work?
OAuth 2.0 has greatly simplified authentication and authorization, and offers a fine-grained delegation of access rights. Represented in the form of scopes, an application asks for the user's authorization for specific permissions. An app can request one or more scopes. Through approval of the scopes, the user grants these apps permissions to execute code to perform logic behind the scenes within their environment. These apps can be harmless or as threatening as an executable file.
There are four recommended ways to help secure a company's SaaS stack. Here's what a security team can share with employees and handle themselves to mitigate SaaS-to-SaaS app access risk.
The first step in cybersecurity always comes back to raising awareness. Once the employees become more aware of the risks and dangers that these OAuth mechanisms present, they will be more hesitant to use them. Organizations should also create a policy that enforces employees to submit requests for third party apps.
Security teams should gain visibility into every business critical app and review all the different third party apps that have been integrated with their business-critical SaaS apps - across all tenets. One of the first steps when shrinking the threat surface is gaining an understanding of the full environment.
Once the security team knows which third party apps are connected, they should map the permissions and the type of access that each third party app has been given. From there they will be able to see which third party app presents a higher risk, based on the higher level of scope. Being able to differentiate between an app that can read versus an app that can write will help the security team prioritize which needs to be handled first.
In addition, the security team should map which users granted these permissions. For example, a high-privileged user, someone who has sensitive documents in their workspace, who grants access to a third party app can present a high risk to the company and needs to be remediated immediately.
SaaS Security Posture Management solutions can automate the discovery of 3rd party apps. The right SSPM solution, like Adaptive Shield, has built-in logic that maps out all the 3rds party apps with access to the organization's SSPM integrated apps. This visibility and oversight empowers security teams so whether a company has a 100 or 600 apps, they can easily stay in control, monitor and secure their company's SaaS stack.
To secure a company's SaaS stack, the security team needs to be able to identify and monitor all that happens within their SaaS ecosystem. SaaS-to-SaaS access is just one use case in the SaaS Security Posture Management picture (take a look at the next addition in the series, SaaS-Device user protection).
Most existing cybersecurity solutions still do not offer adequate protection or a convenient way to monitor a company's SaaS stack, let alone the communications between their known apps and platforms, leaving companies vulnerable and unable to effectively know or control which parties have access to sensitive corporate or personal data.
Organizations need to be able to see all the configurations and user permissions of each and every app, including all the SaaS-to-SaaS apps that have been granted access by users. This way security teams can retain control of the SaaS stack, remediate any issues, block any apps using too many privileges and mitigate their risk.


Tel Aviv – July 6, 2022, Adaptive Shield today announced that its SaaS Security Posture Management (SSPM) platform has been recognized as a Trust Award finalist in the Best Cloud Security Posture Management Solution category for the 2022 SC Awards. Now in its 25th year, the SC Awards are cybersecurity’s most prestigious and competitive program where finalists are recognized for outstanding solutions, organizations, and people driving innovation and success in information security.
“Adaptive Shield and other Trust award finalists reflect astonishing levels of innovation across the information security industry and underscore vendor resilience and responsiveness to a rapidly evolving threat landscape,” said Jill Aitoro, Senior Vice President of Content Strategy at CyberRisk Alliance. “We are so proud to recognize leading products, people and companies through a trusted program that continues to attract both new entrants and industry mainstays that come back year after year.”
“Company reliance on cloud-native applications continues to accelerate, and with that come a host of new security challenges, especially managing configurations across hundreds of unique apps. To remediate SaaS issues and fully realize the benefits of these investments, businesses are turning to SaaS Security Posture Management (SSPM) solutions,” said Maor Bin, co-founder and CEO of Adaptive Shield. “We are thrilled to be named a finalist in the ‘Best Cloud Security Posture Management Solution category.’ This recognition validates the incredible work of our team and the platform’s success in delivering businesses the visibility needed to regain control of their entire SaaS environment.”
The 2022 SC Awards were the most competitive to date, with a record 800 entries received across 38 categories - a 21% increase over 2021. Entries for the SC Awards were judged by a world-class panel of industry leaders, from sectors including healthcare, financial services, manufacturing, consulting, and education, among others.
Winners will be announced during SC Awards week, scheduled to begin on August 22, 2022. A Meet the Winners networking reception celebration will take place during InfoSec World 2022, September 27th in Orlando, Florida.
About CyberRisk Alliance
CyberRisk Alliance (CRA) is a business intelligence company serving the high growth, rapidly evolving cybersecurity community with a diversified portfolio of services that inform, educate, build community, and inspire an efficient marketplace. Our trusted information leverages a unique network of journalists, analysts and influencers, policymakers, and practitioners. CRA’s brands include SC Media, SecurityWeekly, ChannelE2E, MSSP Alert, InfoSec World, Identiverse, Cybersecurity Collaboration Forum, its research unit CRA Business Intelligence, and the peer-to-peer CISO membership network, Cybersecurity Collaborative. Click here to learn more.
The original PR was released through Businesswire on July 6, 2022.


Adaptive Shield is officially On the Radar in Omdia's report for an innovative solution making a big impact in the SaaS security space.

In the report, Rik Turner, Senior Principal Analyst at Omdia, discusses accelerated cloud adoption, the rapid increase in threats, and ongoing shortage of skilled security professionals, that is driving the cybersecurity world towards more proactive approaches, after a decade in which reactive (detect and respond) ones held sway.
Rik Turner specializes in cybersecurity technology rents, IT security compliances, and call recording. His reports offer insights and analysis on the market evolution to help users determine what kind of technology and vendor they should pursue. Prior to joining Omdia RIk worked as an IT journalist, specializing in networking and security.
Rik Turner begins his analysis of Adaptive Shield with:
Adaptive Shield's SSPM Platform combines proactive, continuous, and automated monitoring capabilities with a built-in knowledge base of compliance standards and benchmarks. Once in place, it delivers visibility into the whole SaaS ecosystem, sending an alert whenever it detects a security misconfiguration. Security issues can be fixed automatically, or a ticket can be created for the customer’s security team, with detailed remediation steps.
By taking a close up look at the platform, Rik examines how the uses application programming interfaces (APIs) to query the apps and build a picture of the customer’s SaaS estate, highlighting misconfigurations, mistakes in set-up, and excessive access permissions.
The customer’s security team is provided with a user interface in which they can view how effectively each of their security controls, such as access control or their endpoint security platform, is addressing the vulnerabilities Adaptive Shield is detecting, with the ability to filter their view by app, security control, or compliance requirement, for instance.
With every SaaS application is a world unto itself each with its own API, Rik emphasizes the importance of an SSPM solution that is able to integrate a variety of apps. SaaS security
As Rik sees it, while Adaptive Shield is currently staying within the walls of the SSPM market segment, it plans to broaden its offering and enhance SaaS security by looking at the device posture of the app user and 3rd party app discovery. He predicts part of this will come through partnerships with other security vendors, such as those in endpoint security and vulnerability management. As the SSPM market continues to grow, so is it expected of Adaptive Shield.


After 2 years of virtual events, RSA Conference 2022 in San Francisco brought back face-to-face interaction. And wow, what an experience! From live sessions and parties to games and demos galore, RSA was packed with it all. Here’s a recap of Adaptive Shield at RSA.
Our CEO, Maor Bin took the stage at RSA to speak about a new SaaS vulnerability discovered by Adaptive Shield security researchers, within Microsoft’s OAuth application registration. Bin took the audience through a live demo of the vulnerability and demonstrated how it allows anyone to leverage the Exchange’s legacy API to create hidden forwarding rules in O365 mailboxes. But it didn’t stop there.

Bin’s Session was followed by a Birds of a Feather talk where he and a handful of security experts dove deeper into the vulnerability and its implications.

The CSA panel was made up of our CEO Maor Bin, CSA Global Vice President of Research John Yeoh, A10 Networks Vice President of Product Management Mikko Disini, Lacework Global Field CTO Chris Pedigo, and Orca Security Chief Executive Officer and Co-Founder Avi Shua. These leaders in cyber security discussed the risks organizations face in today’s digital world and whether security teams are properly supporting business transformation decisions. The panel dove into questions like, what are the challenges when tracking cloud and other digital assets, etc. It goes without saying that this session was insightful and thought provoking.
During RSA, Cyber Defense Magazine celebrated its 10th year of Global Infosec Awards. Cyber Defense Magazine shares cutting edge knowledge, real world stories and awards on the best ideas, products and services in the information technology industry.
We were thrilled to have Adaptive Shield named a winner of the 2022 Global InfoSec Awards as the Next Gen in SaaS/Cloud Security.
Over the 4 days at RSA our booth greeted many friendly faces. Our experts were always up and ready to chat with visitors and talk about SaaS security, SSPM, and give a live demo of the Adaptive Shield platform.

Everyone that visited our booth had the chance to play our game “How Fast Can You Fix Your SaaS Stack?”, where we tested people’s speed and knowledge to see who could configure 20 settings in under 30 seconds.
Players that got a score of 85% or higher got their pick from an assortment of games or toys, and our grand prize winner, Erick Binti, with a perfect score of 100% received a mini Apple speaker.

Our partner Torq joined us at our booth to give a demo of our paired solution. Torq is a no-code platform that’s purpose-built for security automation. Together with Adaptive Shield, Torq streamlines the deprovisioning process through automation, lifts the burden of manually auditing and deactivating accounts, and provides continuous visibility and control to increase the organization’s SaaS security posture.

To top off the hard day's work, Adaptive Shield co-sponsored the FOMO party with a live performance from the band, Incubus. With rock-out music, glowing bracelets, and tasty food, the FOMO party was definitely the place to be.


RSA 2022 was a great way to bring back in-person events and we are looking forward to seeing what next year has in store.



The SaaS app attack surface has widened and recent research shows that up to 63 percent of organizations have dealt with security incidents because of a SaaS misconfiguration. Lack of visibility, thousands of configurations for the security team to monitor and remediate, and too many departments with access are the leading causes of SaaS misconfigurations. There are unrealistic expectations on security teams and app owners (who sit outside the security team) to manually handle every app, configuration, and user role.
Gartner created the SSPM category in 2020 to address these challenges to refer to tools that enable security teams to have full and continuous visibility of SaaS security settings and configurations. Up until this category emerged, Cloud Security Posture Management (CSPM) and Cloud Access Security Broker (CASB) were considered able to secure the Saas stack. However, CSPM focuses on infrastructure-as-a-service security solutions, where SSPM is specifically catered to SaaS app technology. Meanwhile, while CASB and SSPM are both designed to address security issues within SaaS applications, CASB falls short as it identifies incidents after they happen. SSPM offers organizations a SaaS-specific, preventative solution that allows them to gain full visibility of their SaaS stack security.
According to our 2022 SaaS Security Survey completed in conjunction with CSA (Cloud Security Alliance), SSPM has become the top priority with 62% of companies currently using or planning to implement in the coming 24 months.
From the breadth of applications supported to the depth of its security checks, an SSPM provides organizations continuous, automated surveillance of all SaaS apps, alongside a built-in knowledge base to ensure the highest SaaS security hygiene. When comparing SSPM solutions there's a few key features to keep in mind to make sure your business is getting the best SaaS security.
When evaluating different SSPM the first thing to look out for is its ability to integrate all your needed SaaS apps. Every organization uses at least a handful of SaaS apps if not hundreds, each with their own unique settings. Any app can pose a risk and smaller apps often serve as a gateway for an attack, this is why it’s crucial to have every app to be fully integrated. As a rule of thumb, look for an SSPM with a minimum of 30 integrations that are adaptable and able to run checks on every data type to protect against misconfigurations.
The other vital component to an effective SSPM is the expanse and depth of the security checks. Every SaaS app has its list of domains to monitor, such as: identity and access management, malware protection, data leakage protection, auditing, access control for external users, and so on.
This goes hand in hand with continuous monitoring and remediation. Part of an SSPM’s job is to not only detect the threats but to combat them. Remediating issues in business environments is a complicated and delicate task. The best SSPM solution should provide context about each configuration, enable you to easily monitor, and set up alerts. When alerts do happen, the platform should map out remediation. This way, when misconfigurations do happen, a business is left vulnerable for a minimal window of time.
Part of what enables an SSPM solution to provide full visibility is its user and device inventory. User inventory takes into account all the different SaaS apps used by different employees and the level of access which they have. When a user fails a security check, security teams are immediately notified to enable a seamless user management and investigation across all SaaS apps. Device inventory allows security teams to see which devices have access to company SaaS apps and manage the risk based on the device hygiene score.
An effective SSPM maps out the security controls of major compliance frameworks such as SOC 2, ISO 27001 and NIST Special Publication 800-53, in order to provide in-depth security checks by app, user, severity or any other metric indicating misconfigurations. When misconfigurations or failed security checks do happen, security teams are not only alerting immediately, they also get a step-by-step remediation description to see exactly how to fix the SaaS misconfiguration
Another aspect that is growing in importance on the SaaS security landscape is that of 3rd party app access. Users don't think twice about connecting an app with their Google Workspace or M365 but these automatic actions are becoming a threat in the corporate cybersecurity landscape. That being said, 3rd party app access is also a key feature that helps boost companies’ productivity and enable remote work. Adaptive Shield, for example, gives security teams visibility into these business-critical apps and reviews the permission and access levels of different 3rd party apps being integrated to reduce the severity of a threat.
We are honored that Gartner has named Adaptive Shield a 2022 Gartner Cool Vendors™ in Application Security: Protection of Cloud-Native Applications. We believe that this is a powerful step not just for Adaptive Shield, but for the field of SaaS Security Posture Management (SSPM).


It’s without a doubt that the SaaS app attack surface has been continuing to grow as businesses have become more reliant on apps to organize and run their business-critical operations. To better understand how teams are dealing with their SaaS security posture, Adaptive Shield partnered with the leading organization dedicated to promoting best practices for ensuring cyber security, Cloud Security Alliance (CSA), to develop the 2022 SaaS Security Survey Report.

The goals of the study was to understand the current state SaaS security through investigating the following key areas of interest:
The 2022 SaaS Security Survey Report offers insight into the industry knowledge, attitudes, and options regarding SaaS security and related misconfigurations.
Maor Bin, CEO and co-founder of Adaptive Shield says:
“This survey shines a light on what CISOs and cybersecurity managers are looking for and need when it comes to securing their SaaS stack — from visibility, continuous monitoring and remediation to other ever-growing, critical use cases such as 3rd party application control and device posture monitoring. The SSPM market is maturing rapidly — and this type of zero-trust approach for SaaS is where the SSPM market is going. ”
CSA gathered responses anonymously from 340 CSA members from IT and security professionals from various organization sizes, industries, locations, and roles. (Sponsored by CSA Corporate Members, the study’s content development and editing rights remained absent of added influence.)
Among the survey’s key findings:
The survey concludes by suggesting key methods of improving SaaS security to help organizations implement the preventive measures that could secure them from the next breach.
If you want to see all the details, like more of organizations top SaaS security concerns, their policy when dealing with unsanctioned SaaS applications, and different methods for monitoring SaaS security configurations, download the full survey.


This new partnership delivers security controls over SaaS environments including the ability to identify high-risk users and non-compliant devices
Tel Aviv, March 15, 2022— Adaptive Shield, the leading SaaS Security Posture Management (SSPM) company, today announced it will partner with CrowdStrike, a leader in cloud-delivered protection of endpoints, cloud workloads, identity and data, to introduce a new Zero Trust Software-as-a-Service (SaaS) Security Posture solution to the CrowdStrike Store, a cybersecurity app marketplace. The solution makes it easy for security teams to quickly identify and manage risks coming from SaaS users and their associated devices.
Integration of Adaptive Shield’s SaaS Security Posture Management solution with the CrowdStrike Falcon platform empowers organizations with comprehensive SaaS application context and control to enhance SaaS Security posture for a holistic Zero Trust approach. Adaptive Shield provides visibility and remediation of potential risks in a SaaS stack that are caused by misconfigurations and misappropriated privileges. Available in the CrowdStrike Store, organizations can seamlessly implement comprehensive Zero Trust in their SaaS security, allowing them to easily identify high-risk users and non-compliant devices through device posture visibility and continuous risk assessment.
This new integration offers a holistic approach to the accelerating challenges in SaaS security. The SaaS security threat landscape continues to grow exponentially in size and complexity as businesses deploy more and more apps to support remote workers and boost employee productivity.
“An infected device is one of the ways that threat actors can infiltrate an organization’s SaaS stack. For example, security teams get hundreds of events related to Account Takeovers, even though they keep ensuring password changes within their organization. Security teams can’t address each and every event, instead, they need and want to prevent it from happening in the first place,” said Maor Bin, CEO of Adaptive Shield. “This is why partnering with CrowdStrike is so vital. Through this collaboration, we will deliver to security teams contextual endpoint telemetry that is then linked with SaaS application insights. As a result, teams can harden their SaaS access to threats with speed and accuracy.”
“Lack of visibility and device context with the growing number of SaaS applications makes it difficult for teams to get the right application controls and risk assessment required for SaaS security,” said Geoff Swaine, vice president of global programs, CrowdStrike Store and technology alliances at CrowdStrike. “With Adaptive Shield available in the CrowdStrike Store, customers can try, buy and deploy trusted applications, leveraging our single lightweight agent architecture and extending our enriched telemetry to fortify organizations’ SaaS security posture management. Extending the CrowdStrike Zero Trust capabilities to the SaaS stack provides the visibility and insights necessary to easily identify and eliminate risks.”
For the full solution brief, take a look at our resources.
To read more about the Adaptive Shield’s solution on the CrowdStrike Store, click here.
The original PR was released through PR Newswire on March 15, 2022.
.png)
.png)
TEL AVIV, Israel, Jan. 11, 2022 -- Adaptive Shield, the leading SaaS Security Posture Management (SSPM) company, today announced that it has joined the Cloud Security Alliance (CSA), the world's leading organization dedicated to defining and raising awareness of best practices to help ensure a secure cloud computing environment.
The threat landscape for SaaS security is vast as businesses rely on a multitude of SaaS apps. While these apps include built-in security features, the responsibility to continuously monitor misconfigurations falls to the company. Adaptive Shield's SaaS Security Posture Management (SSPM) solution provides clear visibility into a business's entire SaaS stack. It then proactively sends detailed alerts when it identifies misconfigurations and misappropriated user privileges to enable quick remediations of all potential risks.
"Any discussion about cloud and security is incomplete if it doesn't include the growing role of SaaS apps and the security challenges that accompany these investments," said Maor Bin, Co-Founder and CEO of Adaptive Shield. "We are so excited to join the Cloud Security Alliance. Working together, we will be able to generate greater awareness around the latest security threats, most specifically the ones resulting from misconfigurations in SaaS applications and how to best eliminate them."
"The Cloud Security Alliance is committed to helping businesses realize the full benefits of the cloud by elevating global awareness around the steps companies must take to secure these environments. One area where we see a growing need for education are SaaS applications," said Jim Reavis, co-founder, and CEO of the Cloud Security Alliance. "As a leading SaaS authority, we welcome Adaptive Shield to the community and know that organizations will benefit from their unique insights around SaaS configuration challenges and the steps business must take to secure their environment."
About the Cloud Security Alliance
The Cloud Security Alliance (CSA) is the world's leading organization dedicated to defining and raising awareness of best practices to help ensure a secure cloud computing environment. CSA harnesses the subject matter expertise of industry practitioners, associations, governments, and its corporate and individual members to offer cloud security-specific research, education, certification, events, and products. CSA's activities, knowledge, and extensive network benefit the entire community impacted by cloud — from providers and customers to governments, entrepreneurs, and the assurance industry — and provide a forum through which diverse parties can work together to create and maintain a trusted cloud ecosystem. For further information, visit us at www.cloudsecurityalliance.org, and follow us on Twitter @cloudsa.
This PR was first published through PR Newswire on January 11, 2022.


With 2021 drawing to a close and many closing their plans and budgets for 2022, the time has come to do a brief wrap up of the SaaS Security challenges on the horizon. Here are the top 3 SaaS security posture challenges as we see them.
The Mess of Misconfiguration Management
The good news is that more businesses than ever are using SaaS apps such as GitHub, Microsoft 365, Salesforce, Slack, SuccessFactors, Zoom, and many others, to enable employees to maintain productivity under the most challenging of circumstances. As for the bad news, many companies are having a hard time adequately addressing the ever-changing security risks of each app.
This challenge begins with a simple miscalculation—businesses are tasking security teams with ensuring that the security configurations for each app is set correctly. While that may seem like the logical choice, these apps are like snowflakes, no two are the same, including their specific settings and configurations. This is exacerbated by SaaS environments that contain hundreds of apps. Add it all up and what’s left is an unrealistic burden being placed squarely on the shoulders of security teams. These teams do not have the superhuman computing power to be able to monitor thousands of configurations and user permissions daily to secure the organization’s SaaS app stack, without a SaaS Security Posture Management (SSPM) solution.
Users, Privileged Users Everywhere
One only has to consider the typical employee, untrained in security measures, and how their access or privileges increase the risk of sensitive data being stolen, exposed, or compromised. The ease with which SaaS apps can be deployed and adopted is remarkable — and with employees working everywhere, the need for strengthened governance for privileged access is clear.
This has been a long time coming; the shifts in the working climate have further accelerated the process, yet SaaS adoption has been gaining ground for years. Organizations today need the capability to reduce risk caused by over-privileged user access and streamline user-to-app access audit reviews by gaining consolidated visibility of a person’s accounts, permissions, and privileged activities across their SaaS estate.
Ransomware through SaaS
When threat actors decide to target your SaaS applications, they can use more basic to the more sophisticated methods. Similar to what Kevin Mitnick in his RansomCloud video, a traditional line of a business email account attack through a SaaS application follows this pattern:
This is a specific type of attack through SaaS, however, other malicious attacks through OAuth applications can occur in an organization’s environment.
Final Thoughts
Gartner named this domain as one of the “4 Must-Have Technologies That Made the Gartner Hype Cycle for Cloud Security, 2021.
With a SaaS Security Posture Management (SSPM) platform, like Adaptive Shield, you can prevent such attacks and automate the prioritization and remediation processes to fix any misconfiguration issues as they happen.
.png)
.png)
Tel Aviv, December 7, 2021—Adaptive Shield, the leading SaaS Security Posture Management (SSPM) company, today announced a tech integration with Okta, Inc. (NASDAQ: OKTA), the leading independent identity provider. Working together, the companies will deliver businesses an integrated solution to manage SaaS security configurations, enhance Identity and Access Management (IAM), and strengthen governance for privileged access.
The threat landscape for SaaS security is vast and continues to expand as businesses rely on an increasing number of SaaS apps. While these apps come with built-in security features, at the end of the day, the ultimate responsibility to continuously fix potential misconfigurations falls on the security team, which often has no visibility into what’s going on in their enterprise SaaS stack.
The answer is SaaS Security Posture Management (SSPM), which was named one of the “4 Must-Have Technologies That Made the Gartner Hype Cycle for Cloud Security, 2021. Adaptive Shield’s solution provides businesses continuous visibility and remediation for potential risks in the SaaS stack caused by misconfigurations and misappropriated privileges. Through this partnership, the companies provide an integrated solution that manages SaaS security configurations with deep visibility into Identity & Access Management while introducing more stringent governance for users with privileged access to confidential company information.
“Businesses continue to recognize the vital role that SaaS apps play in empowering their hybrid workforce and increasing efficiency. But asking security teams to monitor and handle SaaS-related misconfigurations with no automated solution is unrealistic,” said Maor Bin, CEO and Co-Founder of Adaptive Shield. “Through this integration with Okta, we deliver a seamless solution for a fortified SaaS Security and Identity & Access Management”.
This new joint offering delivers significant benefits, including:
Easy to Manage SaaS Security Configurations
Businesses can measure and elevate their SaaS Security posture by automatically assessing critical misconfigurations in their SaaS app’s settings, such as measure security posture by security domain, application, user, and compliance standard for an overall normalized posture score and spot misconfigurations while they occur. Adaptive Shield’s SSPM also enables to benchmark against compliance frameworks such as SOC II, ISO 27001, PCI-DSS, industry best practices (NIST, CIS), etc.
Enhanced Identity and Access Management
Implement IAM best practices, such as validation of user’s access control and authentication settings (MFA, password complexity, etc.), validation of role-based access management (as opposed to individual-based access), validation of access governance, detection of configuration drifts, alignment with compliance policies, and more.
Strengthened Governance for Privileged Access
Reduce risk caused by over-privileged user access and streamline user-to-app access audit reviews by gaining consolidated visibility of a person’s accounts, permissions, and privileged activities across their SaaS estate.
"Okta is committed to creating a world where anyone can safely use any technology. This includes SaaS-based solutions that have become imperative to businesses as they evolve and become more decentralized," said Austin Arensberg, Senior Director, Okta Ventures. "Adaptive Shield's success in eliminating the risks that come with the use of SaaS applications aligns with our commitment to bring simple and secure access to people and organizations everywhere."
This was first published through PR Newswire on December 8, 2021.


Today, we announced a $30M series A round of financing led by New York-based global private equity and venture capital firm Insight Partners, with additional investors including Okta Ventures and existing investor, Vertex Ventures Israel. Adaptive Shield will use the funding to enable companies to secure their SaaS stacks, many of which are already compromised due to misconfigurations.
As businesses rely on multiple SaaS applications, typically hundreds of them, ensuring that each is configured properly becomes unmanageable – our 2021 report found that 85 percent of respondents cite SaaS misconfigurations as one of the top three risks. This issue is being exacerbated by unrealistic expectations that are being placed on app owners— most organizations today are delegating security to less-trained staff who sit outside the security department’s day-to-day purview.
Our SaaS Security Posture Management Suite (SSPM) removes this burden and risk by providing deep visibility and remediation for potential risks caused by misconfigurations and misappropriated privileges. In September, SSPM was named one of the “4 Must-Have Technologies That Made the Gartner Hype Cycle for Cloud Security, 2021.” Gartner states, “SSPM tools reduce risk by continuously scanning for and eliminating configuration mistakes, which are the most common cloud security failures.”
“Expecting security teams to stay on top of SaaS Security misconfigurations without a proper SSPM solution in place is like expecting a bodyguard to protect an invisible person. Deep visibility and continuous maintenance of SaaS security hygiene is crucial to keeping the company secure” said Maor Bin, CEO and Co-Founder of Adaptive Shield. “Thanks to this latest round of funding, we will be able to further evolve our SSPM offering while extending our reach to meet growing demands from businesses around the globe looking to increase their SaaS usage while eliminating any risk.”
Adaptive Shield’s SSPM Suite features proactive, continuous and automated monitoring capabilities and a built-in knowledge base of compliance standards and benchmarks. As a SaaS that integrates with SaaS, the Adaptive Shield solution can be live within minutes. Once in place, it delivers customers clear visibility into their whole SaaS ecosystem, sending detailed alerts at the first sign of a security misconfiguration and proactively fixing these for all global settings and user privileges.
“As SaaS adoption rises and these threats continue to intensify, Adaptive Shield's Fortune 100 customers have made it clear that with its application-agnostic architecture and ability to rapidly connect to any data object, only one company is capable of securing a business's evolving SaaS estate," said Thomas Krane, Principal at Insight Partners. "We look forward to partnering with Adaptive Shield and supporting their rapid growth in the years ahead.” Thomas Krane will join Adaptive Shield’s board.
“Adaptive Shield’s ramp up time in our environment was immediate and provided key insights to our security team without overwhelming users with too much data,” said Stephen Ward, Managing Director at Insight Partners and former CISO of Home Depot. “Adaptive Shield’s solution is focused on immediate risk reduction and product value. Their strong founding team, with an impressive security pedigree, make Adaptive Shield a standout in the industry.
This latest round of finances also includes an investment from Okta Ventures, which commences a technology integration between the two companies.
“Okta is committed to creating a world where anyone can safely use any technology. This includes SaaS-based solutions that have become imperative to businesses as they evolve and become more decentralized,” said Austin Arensberg, Director, Okta Ventures. “Adaptive Shield’s success in eliminating the risks that come with the use of SaaS applications aligns with our commitment to bring simple and secure access to people and organizations everywhere.”
About Insight Partners
Insight Partners is a leading global venture capital and private equity firm investing in high-growth technology and software ScaleUp companies that are driving transformative change in their industries. Founded in 1995, Insight Partners has invested in more than 400 companies worldwide and has raised through a series of funds more than $30 billion in capital commitments. Insight’s mission is to find, fund, and work successfully with visionary executives, providing them with practical, hands-on software expertise to foster long-term success. Across its people and its portfolio, Insight encourages a culture around a belief that ScaleUp companies and growth create opportunity for all. For more information on Insight and all its investments, visit insightpartners.com or follow us on Twitter @insightpartners.
The original PR was released through PR Newswire on October 5, 2021.


LAS VEGAS, NEVADA, AUGUST 2, 2021 – Adaptive Shield, the leading SaaS Security Posture Management (SSPM) company, today announced that is has been named a winner in the Black Unicorn Awards for 2021 in the subcategory of Top 10 Baby Black Unicorns for 2021 at Black Hat USA 2021.
“We’re excited to name Adaptive Shield as a winner among a small, elite group of cybersecurity industry leaders in our third annual Black Unicorn awards,” said Judges Robert R. Ackerman Jr. of www.allegiscyber.com, David DeWalt of www.nightdragon.com, Dr. Peter Stephenson of Cyber Defense Labs and Gary Miliefsky of www.cyberdefensemediagroup.com.
Adaptive Shield competed against many of the industry’s leading providers of cybersecurity products and services for this prestigious award. The term “Baby Black Unicorn” signifies a cybersecurity company that has the potential to reach a $1 billion dollar market value within 3-5 years as determined by private or public investment.
“We are thrilled and honored to be named a Top 10 Baby Black Unicorn for 2021,” said Maor Bin, CEO of Adaptive Shield. “With accelerated adoption in the past few years, SaaS apps have now become the default system of record, and their safe implementation and use cannot be emphasized enough. It is our mission to provide the enterprise’s security teams complete control of their organizations' SaaS apps with visibility, detailed insights and remediation across all SaaS apps.”
The challenge of keeping up with every SaaS configuration is a known and top concern for CISOs today. The SaaS environment is dynamic and continually updating. As employees are added or removed and new apps onboarded, permissions and configurations must be reset, changed, and updated in addition to staying on top of the ever-evolving industry standards and best practices (NIST, MITRE, etc.). While SaaS providers build in security features, it is up to the company’s security team to fix the potential vulnerabilities and configuration weaknesses.
Adaptive Shield has already been implemented in multiple Fortune 500 companies to spearhead their SaaS security efforts.
About Adaptive Shield
Adaptive Shield, the leading SaaS Security Posture Management (SSPM) company, enables security teams to locate and fix configuration weaknesses quickly in their SaaS environment, ensuring compliance with company and industry standards. Adaptive Shield works with many Fortune 500 enterprises to help them gain control over their SaaS threat landscape. Our management team has vast experience in cybersecurity leadership, delivering cybersecurity solutions and cloud enterprise software. For more information, visit us at www.adaptive-shield.com or follow us on LinkedIn.
About Cyber Defense Awards
This is Cyber Defense Magazine’s 9th year of honoring cybersecurity innovators, in this case the Black Unicorn Awards for 2021 on our Cyber Defense Awards platform. In this competition, judges for these prestigious awards includes cybersecurity industry veterans, trailblazers and market makers Gary Miliefsky of CDMG, Dr. Peter Stephenson of CDMG, Robert R. Ackerman Jr. of Allegis Cyber and David DeWalt of NightDragon with much appreciation to emeritus judge Robert Herjavec of Herjavec Group.
About Cyber Defense Magazine
Cyber Defense Magazine was founded in 2012 by Gary S. Miliefsky, globally recognized cyber security thought leader, inventor and entrepreneur and continues to be the premier source of IT Security information. We are managed and published by and for ethical, honest, passionate information security professionals. Our mission is to share cutting-edge knowledge, real-world stories and awards on the best ideas, products and services in the information technology industry. We deliver electronic magazines every month online for free, and limited print editions exclusively for the RSA, BlackHat and IPEXPO conferences and our limited edition paid reprint subscribers. Cyber Defense Magazine is a proud member of the Cyber Defense Media Group (CDMG).
This PR was first released through PR Newswire on August 2, 2021.


Tel-Aviv, Israel, Tokyo, Japan — Adaptive Shield, leaders in SaaS Security Posture Management (SSPM), is pleased to announce that it has entered into a distribution agreement with Macnica Networks Corp., Japan's global technology solutions company that analyzes cyber threats targeting Japanese organizations and provides security solutions.
Today, SaaS apps have become the business of record, from the company’s CRM and customer support tools to IT tools, HR management systems, dashboards, workspaces, and much more. The use of SaaS apps doesn’t come without risk. With the multitude of settings, controls, and policies to manage and track on every SaaS app in use, many misconfigurations arise. While SaaS providers build in security features, it is up to the company’s security team to fix any potential vulnerabilities and configuration weaknesses.
By partnering with Adaptive Shield, Macnica Networks will utilize the cloud security knowledge they have cultivated alongside Adaptive Shield’s technology to support the safe use of SaaS applications by enterprises.
“Cloud services are essential to business today, yet maintaining a consistent policy across platforms, business units and user groups is a difficult problem. Adaptive Shield is unparalleled in its ability to provide enterprises a continuous, and automated SaaS security solution and we are proud to partner with them to make this solution available to our customers and enhance our cloud security portfolio,” says Jun Ikeda, President of Macnica Networks.
Through this partnership, Japanese companies will gain clear visibility of their whole SaaS ecosystem with all the potential places for infiltration -- and get detailed alerts at the first sign of configuration drift or anomaly. Adaptive Shield also provides built-in remediation tools so the security team can open a ticket to fix the issue with no go-between and no lengthy additional steps.
“The cooperation with Macnica is another important step in our mission to provide security teams complete control of their organizations' SaaS applications with visibility, detailed insights and remediation of all SaaS misconfigurations,” asserts Maor Bin, CEO of Adaptive Shield. “We are thrilled to partner with Macnica Networks, leaders in cybersecurity in Japan. Through this collaboration, we will further accelerate the safe use of SaaS applications by Japanese companies, helping them maintain a clean, safe and efficient SaaS app environment."
About Macnica Networks
Macnica Networks works with a large number of overseas companies to provide the latest technological advances in network devices and software. Its extensive range of products, and installation and maintenance support services make it a favorite of governmental and educational establishments, and private sector corporations.
This PR was first released through PR Newswire on July 20, 2021.


Adaptive Shield Wins Next-Gen Vulnerability Assessment, Remediation and Management Award in the 9th Annual Global InfoSec Awards at #RSAC 2021
SAN FRANCISCO, MAY 20, 2021 – Market leader in SaaS Security Posture Management (SSPM), Adaptive Shield has been awarded:
“We’re thrilled to receive this prestigious cybersecurity award from Cyber Defense Magazine. We know Adaptive Shield’s technology can profoundly help security professionals to mitigate the rising challenges in today’s evolving SaaS threat landscape. We are proud to join the impressive cohort of award-winning cyber security solutions.” says Maor Bin, CEO of Adaptive Shield.
Gary S. Miliefsky, Publisher of Cyber Defense Magazine asserts, “Adaptive Shield embodies three major features we judges look for to become winners: understanding tomorrow’s threats, today, providing a cost-effective solution and innovating in unexpected ways that can help stop the next breach.”
This is Cyber Defense Magazine’s ninth year of honoring global InfoSec innovators. Our submission requirements are for any startup, early stage, later stage or public companies in the INFORMATION SECURITY (INFOSEC) space who believe they have a unique and compelling value proposition for their product or service. Learn more at www.cyberdefenseawards.com
The judges are CISSP, FMDHS, CEH, certified security professionals who voted based on their independent review of the company submitted materials on the website of each submission including but not limited to data sheets, white papers, product literature and other market variables. CDM has a flexible philosophy to find more innovative players with new and unique technologies, than the one with the most customers or money in the bank. CDM is always asking “What’s Next?” so we are looking for Next Generation InfoSec Solutions.
With over 5 Million monthly readers and growing, and thousands of pages of searchable online infosec content, Cyber Defense Magazine is the premier source of IT Security information for B2B and B2G with our sister magazine Cyber Security Magazine for B2C. We are managed and published by and for ethical, honest, passionate information security professionals. Our mission is to share cutting-edge knowledge, real-world stories and awards on the best ideas, products and services in the information technology industry. We deliver electronic magazines every month online for free, and special editions exclusively for the RSA Conferences. CDM is a proud member of the Cyber Defense Media Group. Learn more about us at Cyber Defense Magazine and visit Cyber Defense TV and Cyber Defense Radio to see and hear some of the most informative interviews of many of these winning company executives. Join a webinar at Cyber Defense Webinars and realize that infosec knowledge is power.


Released last week, the CISO/Security Vendor Relationship podcast, hosted by David Spark and Mark Johnson, with our sponsored guest, Travis Hoyt, TIAA’s Managing Director of exec cybersecurity technology went live!
Here’s a recap if you haven’t had a chance to hear it yet.
Travis opened the show with his ten-second tip, advising listeners they need to get started managing the security of their SaaS portfolio, and reminding them that they shouldn’t “sacrifice good for great.” It’s an important message in a world where many data breaches are caused by simple misconfigurations that allow hackers to simply log in to their target’s SaaS applications.
Throughout the podcast, Travis shared insights on a wide array of security issues. The three cybersecurity experts discussed Rob Lemos’ Dark Reading report claiming that you can’t necessarily trust patches that are often incomplete, before the conversation shifted in the NSA’s recent guidance on creating a Zero Trust security model.
For the humorous segment where David asks what’s worse – he gave the scenarios of being a victim of ransomware or having to work with a team of “brilliant jerks” who say no to everything. Mike concluded that ransomware was a one-time issue while dealing with brilliant jerks was something he’d have to contend with every day, and Travis preferred to deal with difficult people than navigate a ransomware issue.
The conversation transitioned into a look at SaaS Posture Management, which is where it really got interesting (as you might expect, this is where they started talking about us). The group discussed the need for SaaS apps to be more consistent to get configuration telemetry as well as the need for controls that can apply a global security posture across all SaaS apps within a company’s footprint. That’s where Adaptive Shield comes in, being able to collate, monitor and do an in-depth analysis of a company’s whole SaaS security posture.
Travis shared some of the benefits that Adaptive Shield offers: for one, the large portfolio of SaaS platforms within the Adaptive Shield, which allowed them to implement immediately. Onboarding was fast, and they could see right away if the SaaS apps conformed to company policy standards. He added that any apps that weren’t in the portfolio were able to be brought online rather quickly, due to the architecture of the Adaptive Shield platform.
Travis remarked that one of the features they were pleasantly surprised to find was the admin monitoring capabilities, which show which SaaS apps’ configuration settings changed by which admins. Travis said that the system would help security teams detect questionable activities.
According to Travis, CASB and proxy solutions provided a lot of information but didn’t offer visibility into the configurations of the tenants themselves, which was an area he needed to address.
Catch the whole episode, including a story about a coffee maker that Travis received as a gift that he couldn’t accept, at the CISO / Security Vendor Relationship podcast.


A typical enterprise has on average 288 SaaS applications, which according to the 2020 SaaS Trends Reports increases 30% year over year. No need to spell it out, but that’s a lot of data points, workloads and sensitive information flowing. Enter Snowflake, the Data Cloud company that gives companies the ability to unify all of their siloed data into one place and execute diverse analytic workloads. Snowflake also provides a multitude of cloud data security measures that comply with government and industry regulations. Yet, outside the domain of Snowflake’s robust native security controls, potential vulnerabilities and configuration weakness can still occur.
It's understood by industry experts that most of the successful attacks on cloud services stem from misconfiguration, mismanagement and mistakes. The configuration vulnerabilities are up to the company’s security team to monitor and protect. Yet with the multitude of users and programs, it is near impossible to run manual, continuous monitoring and security checks for each and every SaaS in use. To further complicate matters, SaaS owners often do not sit within the security team but in the departments that most utilize the SaaS. These professionals are not as trained or as vigilant in the continuous, complex needs of configuration and posture, which sometimes leads to tension between departments and opacity of the security protocols in place for that SaaS.
Even slight misconfigurations can leave a company wide open for a breach. The security teams need to be able to track and monitor these gaps at all times. Consider these scenarios:
1. Client Session Clone
Scenario: An enabled client clones a new session from previously used tokens for the account and user.
What is the risk? A malicious attacker can acquire a token and use it in a new session.
2. Inline URL Export
Scenario: Data is exported to an external location.
What is the Risk? If this data is highly sensitive, it can fall into the wrong hands. security teams or Business Ops can lock this functionality to keep the data protected.
3. Account Admin Default Role
Scenario: Account admins inadvertently use the ACCOUNTADMIN role to create objects and assign users additional roles, then designate one of these roles as their default.
What is the risk? ACCOUNTADMIN role has the most power to protect or access the company’s infrastructure. If a default role is easily or mistakenly created and the wrong user accesses it, then the company is exposed.
Companies need their SaaS security posture managed and monitored -- and that’s where Adaptive Shield comes into play. With Adaptive Shield, it doesn’t matter how many users and SaaS programs are in play throughout the organization. Adaptive Shield will perform a SaaS security audit and continuously extract and collate the information for a clear view into the company’s SaaS security landscape. Within minutes, security teams will be able to see their SaaS security posture and take the appropriate steps to remediate.
Security teams can drill down to the specifics, and slice the data by application, domain, compliance framework, or user. They can then choose to remediate an issue within the system or open a ticket in their own security department. For those business owners not part of or trained in security teams, there’s a functionality to set up scoped user access to give the app’s business owner the ability to receive alerts about misconfigurations in that SaaS. This way, the business owner can not only remediate the issue themselves, but also learn more about how to harden the company’s security posture without too much friction with the security team.
Adaptive Shield’s mission is to ensure every company has a secure SaaS framework. That’s why Adaptive Shield has teamed up with Snowflake -- to offer Snowflake admins the use of Adaptive Shield for free. By using Adaptive Shield with Snowflake, users will not only get enhanced visibility, but the ability to mitigate organizational exposure and enable continuous security for all global settings and user privileges.
Remember the three scenarios mentioned above? These are the Adaptive Shield security checks that protect against those risks:
Security Check 1: Client Session Clone
Adaptive Shield tracks and reports when an enabled client clones a new session from previously used tokens for the account and user. If found to have failed this security check, security teams can then remediate the situation and put future protocols in place to prevent it from recurring

Security Check 2: Prevent Inline URL Export
Adaptive Shield tracks and reports if the proper configuration is in place to keep data from being exported to an external location. If found to have failed this security check, security teams can adjust configurations to prevent a sensitive data export from happening again.

Security Check 3: Account Admin Default Role
Adaptive Shield monitors and reports if there is the most secure configuration to create an ACCOUNTADMIN role. That way when objects and users are created by the ACCOUNTADMIN role, it is with purpose and thought, limiting risk from inadvertent or misunderstood permissions.

All Adaptive Shield findings and report data can be accessed directly via Snowflake Data Marketplace. This makes Adaptive Shield a great way to start leveraging your Snowflake as a security data lake, with powerful analytics, flexible reporting and cost-effective storage. Combine SaaS issues with other datasets like vulnerability scans and awareness training for a unified view into your security posture.

Adaptive Shield integrates with Snowflake and dozens of other SaaS applications. The Snowflake configuration check is currently available at no cost.
To get started, go to the Snowflake Data Marketplace and request access to the free Snowflake configuration check from Adaptive Shield.


Identities in SaaS applications can be either human, associated with individuals, or non-human, such as service accounts, API keys, and 3rd party app OAuth authorizations. Any unsecured identity in a SaaS app can create an opening for cybercriminals to compromise, leading to data breaches, compliance violations, and financial losses.
In a webinar hosted by The Hacker News, Maor Bin, CEO and co-founder of Adaptive Shield, and CISO James Azar discuss how to protect SaaS applications from exposure to identity risks through a strong identity security posture.
Watch the full recording of the webinar here.
“SaaS applications are all about identity. This is the modern IT stack,” says Bin. “It’s about securing your entire stack, not one application or another. Threat actors will not sit at home and do nothing, they will go after the less secure application in the chain. There will always be more attacks.”
As Bin explains in the webinar, the challenge in securing identities in SaaS applications is not only their increasing volume and velocity of change in the SaaS environment, but the fact that each one is so different from the other. As security teams are not responsible for most apps, gaining visibility into the apps is crucial, he says.
Azar agrees. “When you talk to cybersecurity practitioners, the number one challenge they are dealing with is a lack of visibility in asset management. If you are running SaaS applications with limited visibility into the assets that you have, you are blind to any risks or threats to your SaaS stack,” he says.
In the webinar, Bin reviews the key characteristics of identity security for human and non-human accounts and how they differ, especially the fact that non-human identities behave differently, making threats more difficult to detect.
Human identity security components:
How non-human identities are different:
Despite the risks, non-human account monitoring is typically neglected. Human accounts get higher priority from a security perspective. Human and non-human accounts are often managed in a non-centralized manner.
It comes down to the fact that “you can’t secure what you can’t see,” says Bin.
Dedicated controls are needed for both human and non-human identities and to combine them into one view.

To ensure SaaS identity security for both human and non-human accounts, an Identity Threat Detection and Response (ITDR) mechanism comes in as a crucial layer to stitch everything together. Creating a strong identity fabric for identity security posture management within an SSPM, ITDR can identify irregularities specific to non-human identities including anomalous patterns of behavior.
Therefore a combination of prevention (SSPM) and threat detection (ITDR) can secure all types of user accounts, human and non-human, Bin concludes.
Watch The Hacker News webinar to learn more about Adaptive Shield’s SSPM and ITDR capabilities for identity security posture management.


This past month, Adaptive Shield partnered with Panorays (a SaaS-based third-party security risk management platform) to produce a joint webinar Pinpoint Your SaaS App Risks: From Evaluation to Usage. These two security experts, Maor Bin, CEO of Adaptive Shield, and Demi Ben Ari, CTO OF Panorays, discussed the evolution of third-party apps, the tools used to secure them, and the best practices and processes for using these tools. Here are some of the highlights and key takeaways.
Click here to watch the full recorded webinar.
Maor Bin, CEO & Co-Founder at Adaptive Shield, brings over 16 years of experience in the cyber security industry. Before founding Adaptive Shield, Maor served as a cybersecurity intelligence officer in the IDF and later led SaaS Threat Detection Research at Proofpoint.
Demi Ben Ari, CTO & Co-Founder at Panorays, is a software engineer, entrepreneur, and international tech speaker. He has over 10 years of experience in building systems both from the field of near real-time applications and big data distributed systems.
Demi Ben Ari: “The SaaS stack that you are using today is really your new attack surface”
As illustrated in Figure 1, the supply chain has become more complicated and complex due to many changes in the industry.

It's clear that 3rd party apps like Salesforce, Slack, and Monday are critical to businesses and have become an inseparable part of employee’s day to day. It’s also clear that proper risk assessment and security for these apps is vital.
Demi takes a moment to discuss how this risk is understood in today’s market:
“Think that today when we were speaking about third-party breaches that people speak about and echo in the media… it isn't really an attack, right? There is a vulnerability exposed to the world and a lot of hackers and a lot of malicious actors actually try to exploit them with the spray and pray attack. So most of it is not even really targeted.”
This signifies two things. The first being that most breaches are happening simply as a result of apps being poorly secured. The second is understanding that attackers are continuing to explore new means to access and exploit organization's data and this can be true for both targeted and non-targeted organizations, meaning hardening security settings for every app cannot be overstated.
For example, Salesforce is crucial to today's business but in order to operate, the app houses sensitive information that if leaked could potentially ruin a business. The 2022 SaaS Security Survey Report shows that while the investment in SaaS applications is growing, the investment in security tools and staff is lagging behind, as seen in Figure 2.

Organizations need a new tool set to secure the onboarding of new apps and other developments in their SaaS landscape. However, the process needed for organizations to secure their 3rd party apps goes far beyond just implementation; organizations need to evolve their security protocols to include a continuous and repetitive means of evaluating and hardening app security.
Demi: “We spoke about identification and how to know all the vulnerabilities, but it’s a process, and the process does not finish at ‘I'm installing something and this magic box will solve all of my problems’...the continuous monitoring aspect is really crucial.”
Maor Bin: “We need to understand first of all what we need to do to create this [continuous assessment] process internally to work in a secure fashion.” Maor outlines the process of initial and continuous SaaS security assessment into three levels – discovering and assessing risks, obtaining and maintaining hygiene, and managing threats.

Figure 3 outlines the entire process that security teams should be conducting and repeating in order to keep their SaaS stack secure. While the details of this process should be customized to each organization's size, needs, and resources, the overall methodology is the key to create a continuously secure SaaS environment.
The first step in securing one’s SaaS ecosystem is having comprehensive and robust discovery processes to learn of the potential apps’ digital footprint. Security teams need to understand where they have visibility and, more importantly, where they don't. Addressing blind spots should be a top priority to ensure risk can be discovered and reduced.
Then, throughout the onboarding process, from users, their permissions, and their devices, security teams can be hyper aware of all the moving parts that should be checked. Organizations also need to be able to identify and discover SaaS-to-SaaS applications, including ones that are connected without the security team’s knowledge. Today's workforce depends on apps that easily connect with the user's workspace.These 3rd-party applications, which can number in the thousands for larger organizations, all must be monitored and overseen by the security team.
Once the initial assessment is complete, security teams must maintain (or increase) the level of hygiene. Security teams should focus on closing gaps that exist in their posture to remediate faster and reduce risk. This requires that security teams evaluate configurations, compliance requirements, and other changes in their SaaS estate not just once, but repeatedly.
The final step is threat management. Security teams must identify misconfigurations or vulnerabilities in a device or user that is causing risk and quickly remediate the issue.
Gartner recently named a new security discipline called Identity Threat Detection and Response (ITDR). ITDR incorporates detection mechanisms that investigate suspicious posture changes and activities, and responds to attacks to restore the integrity of the identity infrastructure.
ITDR incorporates strong SaaS Security IAM Governance methodologies and best practices that are found in SaaS Security Posture Management solutions (SSPM). This enables security teams to gain continuous and consolidated visibility of user accounts, permissions, and privileged activities across the SaaS stack, such as:
Regardless of how secure an organization's SaaS posture is, new threats continue to emerge and security teams need the right tools to combat them.
Maor Bin: “We need to understand the privacy policy for these 3rd party applications. We have a process for it when it comes to endpoint, which we call application control, and everybody understands that they need to do it for their endpoints…but when it comes to 3rd party apps, things are falling between the cracks.”
Demi Ben Ari: “It always starts from visibility and onboarding. Eventually when you end up with continuous monitoring, it’s also continuously onboarding all of these third-party engagements, and this can be on multiple layers.”
Salesforce can be used as an example of these layers and is considered the first layer. Next, a user may install 5 plug-in applications from the app exchange – apps that may not even be verified by a security expert – creating the second layer, also called SaaS-to-SaaS access or 3rd party app access. This second layer alone already introduces dozens of granted permissions into your environment, multiplying the attack surface. It doesn't stop there – an app connected in the second layer may have its own connected plug-ins which in turn create the third layer and so on and so forth. Security teams must have an assessment process for onboarding the entire entity from the core apps to all its plugins.
Maor iterates: the first step is to identify and discover all these applications and then understand what other apps are connected. History has taught us that many breaches happen as a result of attackers gaining access to small supported apps as opposed to the core SaaS workspace.
Maor: “The idea, when we talk about security, is not just protecting one application or a handful of applications, it’s protecting your entire stack”.
The high volumes of apps, users, and settings makes maintaining a secure SaaS stack a near impossible challenge. Security teams need all-around visibility into different aspects of their SaaS stack while simultaneously implementing and maintaining continuous security assessments. SaaS Security Posture Management (SSPM) solutions enable security teams to gain complete control over their SaaS stack and significantly aid in implementing the continuous process of assessment.
SSPM combat the challenges existing in the SaaS landscape through:


Forrester, a research and advisory company, offers organization’s a variety of services including research and consulting. Their reports help professionals understand their customer’s behavior, concerns, and interests to help organizations make more informed decisions. Their Trend Report ‘Embrace A Paradigm Shift In SaaS Protection: SaaS Security Posture Management’ looks at the increased use of SaaS apps and the value of an SSPM solution. This blog will summarize key takeaways from the report.
Click here to read the full report.
“Organizations’ cloud-first or on-premises augmentation strategies caused an explosive, decentralized, and uncontrolled growth of SaaS application use. Consequently, the increase in the number of cloud assets has also increased overall IT risks.”
The ease with which SaaS apps can be adopted is remarkable, but it has become a double-edged sword. The cloud has enabled organizations to store and manage near endless data and scale their operations, but it has opened the doors for relentless attackers and new attack vectors. Organizations have dozens to over a hundred different SaaS apps critical to maintaining day-to-day operations, each with nuanced access patterns from sharing, uploading, downloading, sorting, searching, and filtering activities.
Access patterns and activities, when looked at individually, may appear harmless. However when looked at as part of a bigger picture, security teams can often quickly identify risk by spotting unusual behavior, suspicious geolocations movements, and uncommon access requests. Organizations not only gain visibility into different domains and activities but also monitor data movement to and from SaaS apps to help detect threats.
The skills shortage and gap between application owners and security teams only adds to the challenge. The report found that even the largest organizations interviewed stated that they lack the resources needed to fully understand the connectivity between SaaS apps and their security implications. Organizations are in dire need of a security solution, such as an SSPM, which is able to provide visibility and understanding into these apps.
In turn, an effective SSPM needs to be able to integrate with all their apps to support the organization's security policies and goals. Contextualized visibility into each app helps security teams prioritize configuration weaknesses and increase time and efficiency to remediation across multiple attack surfaces.
“SSPM solutions differ in breadth and depth of SaaS app coverage”
Simply put, not all SSPM solutions are created equal. SSPMs can vary in the amount of apps they support, the thoroughness of their security checks, and the range of their capabilities. Forrester describes needed functionalities within the organization’s chosen SSPM solution:

At Adaptive Shield, we like to boil it down to four main use cases: misconfiguration management, SaaS-to-SaaS access discovery, device-to-SaaS user management, and identity and access management governance. An SSPM will present detailed and dedicated security checks within each of these use cases.
The 2023 SaaS Security Posture Management Checklist covers all the critical features and capabilities to look out for when evaluating a solution.
“SSPM solutions can make recommendations on how to trim business users’ privileges without impeding their user experience (i.e., they continue to have access to data and the SaaS application functionality that they need to do their jobs without access to data they do not need).”
An SSPM’s user inventory is one of many critical features. A user inventory helps security teams gain visibility of users, their privileges, and user-specific failed security checks. By gaining in-depth knowledge of user permissions and behavior, security teams can identify inactive users, overprivileged admins, and other user-specific threats. SSPMs can help trim unnecessary user privileges without limiting access to the data needed to complete their work.
The report outlines the following identity and access management related SaaS settings that SSPM solutions can enforce.
It's not surprising that SaaS apps do not properly guard organization’s data and are susceptible to data breaches. SSPM solutions provide relief to security experts by offering data protection features such as:


“SaaS applications have native security controls as part of their offering which makes them security products themselves — that security teams now need to manage”.
Asserted by Adaptive Shield’s CEO, Maor Bin partnered with Okta’s VP of Strategy, Stephen Lee in the Security Boulevard Webinar: SaaS Security Trends, Challenges, and Solutions for 2022. This joint webinar discusses the struggles that security professionals face today and how organizations can address the risks stemming from key attack areas. This blog highlights some of the dialogue between these two industry thought leaders.
(For the whole webinar, click here.)
Organizations use dozens to hundreds of apps throughout different departments and with each app comes a sea of configurations to set and secure, not once but constantly. Over time, apps have updates and new security settings or new users with different permissions levels to add or adjust. Security teams need to invest many resources to continuously be on the lookout for misconfigurations and quickly remediate them.
The challenge of managing configurations goes beyond the sheer volume to the intricacies of understanding each app.
Stephen Lee: “If you look at the SaaS applications out there and you go to that security tab or that user management tab – they all look different. Sometimes, you almost have to be that specific app expert to be able to know what to do.”
Maor Bin: “That's one of the reasons for the challenge of securing your SaaS estate – you have so many applications and each one is different from the other one.”
Different apps may have the same or similar security settings but the names of these settings and how to access them can differ vastly. Security teams who are trying to manually secure each configuration have to be an expert on every single app to secure them, which is a far from realistic request.
Stephen Lee: “One beautiful thing about SaaS applications is that it's very easy to integrate with them. [However] once you've shared the power with the downstream applications or clients that are talking to it and then it all becomes ‘who is the weakest link?’ and that becomes a potential security hole.”
SaaS-to-SaaS access has become a balance between the convenience of having end users be able to easily integrate and use these applications (that boost productivity and remote work) and the ability for security teams to have the necessary visibility to secure and monitor these apps.
The risks from SaaS-to-SaaS app access stem from the connection process; the app requests permissions in the user’s workspace and oftentimes, the app is asking for high-risk permissions (the app could also be malicious itself, unbeknownst to the user). Typically defined as allowing an app to gain access to user data (e.g. read/write permissions and more), high-risk permissions, and any unknown app, should only be granted access after the secure team has been able to fully vet it and have a system in place to monitor it.
The 2022 SaaS Security Survey Report demonstrates just how prevalent of a concern 3rd party app access is for today’s CISOs and security professionals.

Maor Bin: “The challenge is not only misconfigurations and native security controls within SaaS applications but what actually happens after you login, what happens within your device…and get a better understanding of what's going on with your users. So for example: if you see you have a Office 365 admin and this user has 3 critical vulnerabilities on their device, it’s obviously a huge problem because this isn't just a regular SaaS user accessing the SaaS applications but it's an admin with privileged roles.”
When individuals with advanced privilege levels use devices that are unsecured, they expand the attack surface with what amounts to an open gateway.
With today's modern workforce working from home, cafes, or even abroad, security teams need to secure all the devices the employees are using. Personal devices are vulnerable to data theft and can inadvertently pass on malware that was downloaded for personal use into the organization’s environment. Lost or stolen devices can also provide a gateway for criminals to access the network.
Stephen Lee: “You can hire the best IT folks and you can hire the best app admins, the best Security Experts… but things do happen. I think it’s not about how to prevent it from happening; I think it’s a lot about mitigation, mitigating the risk…This is relevant to not just a small company with 50 people all the way up to large Enterprises.”
“There's a lot of stuff happening outside of what Okta is able to manage…For us, I’m excited to see how Adaptive Shield can help solve these problems.”
In order to cover the many attack surfaces of SaaS apps, an SSPM solution can enable security teams to gain control of the core misconfiguration management use case; and go beyond to the added layers of SaaS-to-SaaS access, device-to-SaaS user risk, and identity and access management governance.
If you’d like to learn more, contact one of our experts here.


After 2 years of virtual events, RSA Conference 2022 in San Francisco brought back face-to-face interaction. And wow, what an experience! From live sessions and parties to games and demos galore, RSA was packed with it all. Here’s a recap of Adaptive Shield at RSA.
Our CEO, Maor Bin took the stage at RSA to speak about a new SaaS vulnerability discovered by Adaptive Shield security researchers, within Microsoft’s OAuth application registration. Bin took the audience through a live demo of the vulnerability and demonstrated how it allows anyone to leverage the Exchange’s legacy API to create hidden forwarding rules in O365 mailboxes. But it didn’t stop there.

Bin’s Session was followed by a Birds of a Feather talk where he and a handful of security experts dove deeper into the vulnerability and its implications.

The CSA panel was made up of our CEO Maor Bin, CSA Global Vice President of Research John Yeoh, A10 Networks Vice President of Product Management Mikko Disini, Lacework Global Field CTO Chris Pedigo, and Orca Security Chief Executive Officer and Co-Founder Avi Shua. These leaders in cyber security discussed the risks organizations face in today’s digital world and whether security teams are properly supporting business transformation decisions. The panel dove into questions like, what are the challenges when tracking cloud and other digital assets, etc. It goes without saying that this session was insightful and thought provoking.
During RSA, Cyber Defense Magazine celebrated its 10th year of Global Infosec Awards. Cyber Defense Magazine shares cutting edge knowledge, real world stories and awards on the best ideas, products and services in the information technology industry.
We were thrilled to have Adaptive Shield named a winner of the 2022 Global InfoSec Awards as the Next Gen in SaaS/Cloud Security.
Over the 4 days at RSA our booth greeted many friendly faces. Our experts were always up and ready to chat with visitors and talk about SaaS security, SSPM, and give a live demo of the Adaptive Shield platform.

Everyone that visited our booth had the chance to play our game “How Fast Can You Fix Your SaaS Stack?”, where we tested people’s speed and knowledge to see who could configure 20 settings in under 30 seconds.
Players that got a score of 85% or higher got their pick from an assortment of games or toys, and our grand prize winner, Erick Binti, with a perfect score of 100% received a mini Apple speaker.

Our partner Torq joined us at our booth to give a demo of our paired solution. Torq is a no-code platform that’s purpose-built for security automation. Together with Adaptive Shield, Torq streamlines the deprovisioning process through automation, lifts the burden of manually auditing and deactivating accounts, and provides continuous visibility and control to increase the organization’s SaaS security posture.

To top off the hard day's work, Adaptive Shield co-sponsored the FOMO party with a live performance from the band, Incubus. With rock-out music, glowing bracelets, and tasty food, the FOMO party was definitely the place to be.


RSA 2022 was a great way to bring back in-person events and we are looking forward to seeing what next year has in store.



Companies store an incredibly large volume of data and resources within SaaS apps like Box, Google Workplace, and Microsoft 365. SaaS applications make up 70% of total company software usage, and as businesses increase their reliance on SaaS apps, they also increase their reliance on security solutions.
SaaS security is not a new problem, however, the attack surface has widened. It started with managing misconfigurations and now goes far beyond. Today, it takes a holistic approach that includes the continuous monitoring and management of user access, roles and permissions, 3rd party apps installed by users, risks deriving from SaaS user devices and Identity Threat Detection & Response (ITDR).
Securing numerous potential attack vectors for each user becomes a challenge when dealing with a diverse range of applications, each having its own unique characteristics. Additionally, the environment is dynamic, from SaaS vendors recognizing the importance of security and continually enhancing their applications with robust security measures to the ever-evolving user governance required (onboarding, deprovisioning, adjustments in roles and permissions). These controls are effective only when properly configured by the organization, for each app and each user, on an ongoing basis. If that’s not enough, these applications are managed by various business departments, making it impractical for the security team to exercise complete control.
The objective in SaaS security is finding the balance between securing applications while still enabling users to do their jobs efficiently.
Below we explain each attack vector and line of defense for a strong SaaS ecosystem security lifecycle.
Misconfigured SaaS settings are one of the leading causes of SaaS data breaches. Security teams have no visibility into security-related aspects of these apps that in most cases are managed by the business departments. To further complicate the picture, each SaaS application uses its own language for settings. This prevents security teams from developing an easy-to-use guide for business teams directing their security efforts. With companies easily averaging over 100 applications, each with hundreds of configurations and multiple users, deciphering and managing security settings is no easy task.
Adaptive Shield integrates with more than 130 SaaS applications to monitor and manage security misconfigurations through in-depth security checks and auto/step-by-step remediation.

Image 1: Bird’s-eye view of the security posture by app

Image 2: List of security checks categorized by app, domain, severity, numbers of users, etc.
Identity Threat Detection and Response (ITDR) capabilities feature a set of security measures designed to detect and respond to identity-related security threats based on key Indicators of Compromise (IOCs). These IOCs provide forensic signs of a potential breach, such as malware, data breaches, unusual behavior, and other suspicious events. ITDR closes the gap between continuous identity governance and identity threat detection within the SaaS ecosystem, covering Tactics, Techniques, and Procedures (TTPs) and unusual User & Entity Behavior Analytics (UEBA) such as account takeover through compromised identities.
When it comes to SaaS threats, existing threat detection and identity management methods don’t go far enough. Today’s SaaS environments are complex and ITDR capabilities within these landscapes require deep knowledge and proven expertise in the way SaaS applications are designed.
Adaptive Shield’s engines cross-reference and analyze in-context TTPs and suspicious events from multiple sources, enabling the accurate detection of very complex and subtle threats.
As a means of prevention and first line of defense, SSPM should operate as the security layer in the identity fabric to establish robust user governance. This includes excessive permissions, access entitlement, user deprovisioning, and more, across the entire SaaS stack. Adaptive Shield provides organizations with deep and consolidated visibility and control of user accounts, roles, permissions, privileged users, and activities.
Identity governance use cases include:

Image 3: View of User Inventory broken down by privileges and user-specific security checks.

Image 4: View of Threat Center and activity information
To improve app functionality, many users integrate third-party apps into the core SaaS stack. These integrations take place without the knowledge of the security team and often ask for intrusive permission scopes, such as the ability to read, write, and delete data. While many of these applications are harmless, if taken over by a threat actor they can cause significant damage.
Adaptive Shield detects every connected third-party application, as well as identifies their scopes. Security teams can then review the information, and make an informed decision on whether to continue using the application.
3rd party app use cases include:

Image 5: View of 3rd-party connected apps with their severity levels and accessed scopes.
The login-anywhere nature of SaaS enables users to access sensitive corporate systems using unmanaged and compromised devices. These devices, which may contain malware, can be exploited to capture access credentials and tokens that can be used by threat actors. This is particularly high-risk when being done by an admin with broad access within the application.
Your SaaS security tool must review device data, and associate each device with a user. When high-privilege users access SaaS apps on a device that contains critical vulnerabilities, it pours the entire application at risk. Managing that risk is a key element of maintaining a secure SaaS stack.

Image 6: View of the SaaS User Device Inventory
Device-to-SaaS Risk Management includes:
Click here to request a short demo and get started with Adaptive Shield


Every SaaS app user and login is a potential threat; whether it’s bad actors or potential disgruntled former associates, identity management and access control is crucial to prevent unwanted or mistaken entrances to the organization’s data and systems.
Since enterprises have thousands to tens of thousands of users, and hundreds to thousands of different apps, ensuring each entrance point and user role is secure is no easy feat. Security teams need to monitor all identities to ensure that user activity meets their organization’s security guidelines.
Identity and Access Management (IAM) solutions administer user identities and control access to enterprise resources and applications. As identities became the new perimeter, making sure this area is governed by the security team is vital.
Gartner has recently named a new security discipline called Identity Threat Detection and Response (ITDR) that incorporates detection mechanisms that investigate suspicious posture changes and activities, and responds to attacks to restore the integrity of the identity infrastructure.
ITDR incorporates strong SaaS Security IAM Governance methodologies and best practices that are found in SaaS Security Posture Management solutions (SSPM), enabling security teams to gain continuous and consolidated visibility of user accounts, permissions, and privileged activities across the SaaS stack, such as:
Whether you are a CISO, IT or on the Governance, Risk and Compliance (GRC) team, this article will cover the role of Identity and Access Management Governance as part of the organization’s SaaS security program.
IAM Governance enables the security team to act upon arising issues by providing constant monitoring of the company’s SaaS Security posture as well as its implementation of access control.
There are a few critical prevention domains where an SSPM can manage Identity and Access Management Governance: 1) Misconfigurations 2) Vulnerabilities 3) Exposure.
IAM controls need to be properly configured on a continuous basis. The IAM configurations should be monitored for any suspicious changes and ensure that the appropriate steps are taken to investigate and remediate when relevant.
For example, an organization can enable MFA across the organization and not require it. This gap in policy enforcement can leave the organization at risk — and an SSPM can alert the security team about this gap.
The SSPM solution can utilize patching or compensating controls to address commonly exploited vulnerabilities in the identity infrastructure such as the SaaS user’s device. For example, a privileged CRM user can present a high risk to the company if their device is vulnerable. To remediate potential threats that stem from devices, security teams need to be able to correlate SaaS app users, roles, and permissions with their associated devices' hygiene. This end-to-end tactic enables a holistic zero-trust approach to SaaS security.
Another critical vulnerability stems from authentication protocols that the password access is limited to a single-factor authentication method, such as with legacy protocols like IMAP, POP, SMTP and Messaging API (MAPI). An SSPM can identify where these protocols are in place across the organization’s SaaS stack.
The SSPM helps to reduce the attack surface by identifying and mitigating places of exposure. For example, removing unnecessary or excessive privileges or allowing an external admin for a business-critical app. (See figure 1.)

Additionally, 3rd party app access, also known as SaaS-to-SaaS access can leave an organization exposed. Users connect one app to another app to either provide enhanced features or user’s information (e.g contacts, files, calendar, etc). This connection boosts workflow efficiency and as a result, employees’ workspaces are connected to multitudes of different apps. However, the security team is most often in the dark about which apps have been connected to their organization’s ecosystem, unable to monitor or mitigate any threats.
IAM is a method for hardening access control, whereas IAM Governance in SSPMs offer continuous monitoring of these features to ensure security teams have full visibility and control of what's happening in the domain.


Typically, when threat actors look to infiltrate an organization’s SaaS apps, they look to SaaS app misconfigurations as a means for entry. However, employees now use their personal devices, whether their phone or personal laptop, etc. to get their jobs done. If the device’s hygiene is not up to par, it increases the risk for the organization and widens the attack surface for bad actors. And so, Endpoint (Device) Protection — through EDR, XDR, and vulnerability management solutions – has arisen as a critical factor in SaaS Security.
The challenge in remediating the threats posed by endpoints and devices lies in the ability to correlate between the SaaS app users, their roles, and permissions with their associated devices' compliance and integrity levels. This end-to-end approach is what's needed for the organization to implement a holistic, zero-trust approach for their SaaS Security.
Not a simple feat, however, automated SaaS Security Posture Management solutions, like Adaptive Shield, can now provide visibility that correlates the SaaS user and their associated devices with the device’s hygiene score.
How do you classify high-risk devices in the context of SaaS security?
Devices that are owned, or used by users with high levels of permissions to the company’s core SaaS apps. For example, someone who has high levels of access to the company’s CRM can present a high risk to the company if their device is vulnerable and this needs to be remediated immediately. These high-risk devices serve as a critical threat vector to an organization’s SaaS environment.
Security teams should continuously map devices to their users and their associated permissions to get a handle on which devices/users pose the highest risk.
As mentioned, the more privileged the user, the higher their device is at risk. To gain deep observability into the user, app and device posture, security teams need to check the hygiene of their users’ devices, for example up-to-date OS configurations, and any vulnerabilities. With that assessment and score in hand, security teams can map and monitor the user’s SaaS app access (in addition to, of course, securing the SaaS apps themselves).
Once these cross references are in place and accessible, organizations can enable “soft” enforcement enhancements, through policies and organizational best practices. This way security teams can monitor risks and threats without severely limiting the user.
Zero-trust is a concept much batted about in cybersecurity vernacular today. While many consider it a buzzword, its meaning represents an important approach that can not be emphasized enough. To wholly secure the organization’s SaaS stack, end-to-end, and continuously, calls for a holistic and automated solution.
Adaptive Shield has been built to resolve not only the need for management of the SaaS app configurations themselves, but also the devices the organization’s employees use. (Not to mention third party app access — and you can read more about that here.) When integrated with MDM (mobile device management) solution, Adaptive Shield will pull the device data and map the device to the owner.

By looking at the device posture while conducting a SaaS security assessment, organizations can achieve a holistic zero trust approach.


It's no secret that SaaS-to-SaaS apps can boost productivity, enable remote and hybrid work and are overall, essential in building and scaling a company's work processes.
It's an innocuous process much like clicking on an attachment was in the earlier days of email -- people don't think twice when connecting an app they need with their Google workspace or M365 environment, etc. Simple actions that users take, from creating an email to updating a contact in the CRM, can result in several other automatic actions and notifications in the connected platforms.
As seen in the image below, the OAuth mechanism makes it incredibly easy to interconnect apps and many don't consider what the possible ramifications could be. When these apps and other add-ons for SaaS platforms ask for permissions' access, they are usually granted without a second thought, not realizing that these addition connections present more opportunities for bad actors to gain access to their company's data.

How Do SaaS-to-SaaS Apps Work?
OAuth 2.0 has greatly simplified authentication and authorization, and offers a fine-grained delegation of access rights. Represented in the form of scopes, an application asks for the user's authorization for specific permissions. An app can request one or more scopes. Through approval of the scopes, the user grants these apps permissions to execute code to perform logic behind the scenes within their environment. These apps can be harmless or as threatening as an executable file.
There are four recommended ways to help secure a company's SaaS stack. Here's what a security team can share with employees and handle themselves to mitigate SaaS-to-SaaS app access risk.
The first step in cybersecurity always comes back to raising awareness. Once the employees become more aware of the risks and dangers that these OAuth mechanisms present, they will be more hesitant to use them. Organizations should also create a policy that enforces employees to submit requests for third party apps.
Security teams should gain visibility into every business critical app and review all the different third party apps that have been integrated with their business-critical SaaS apps - across all tenets. One of the first steps when shrinking the threat surface is gaining an understanding of the full environment.
Once the security team knows which third party apps are connected, they should map the permissions and the type of access that each third party app has been given. From there they will be able to see which third party app presents a higher risk, based on the higher level of scope. Being able to differentiate between an app that can read versus an app that can write will help the security team prioritize which needs to be handled first.
In addition, the security team should map which users granted these permissions. For example, a high-privileged user, someone who has sensitive documents in their workspace, who grants access to a third party app can present a high risk to the company and needs to be remediated immediately.
SaaS Security Posture Management solutions can automate the discovery of 3rd party apps. The right SSPM solution, like Adaptive Shield, has built-in logic that maps out all the 3rds party apps with access to the organization's SSPM integrated apps. This visibility and oversight empowers security teams so whether a company has a 100 or 600 apps, they can easily stay in control, monitor and secure their company's SaaS stack.
To secure a company's SaaS stack, the security team needs to be able to identify and monitor all that happens within their SaaS ecosystem. SaaS-to-SaaS access is just one use case in the SaaS Security Posture Management picture (take a look at the next addition in the series, SaaS-Device user protection).
Most existing cybersecurity solutions still do not offer adequate protection or a convenient way to monitor a company's SaaS stack, let alone the communications between their known apps and platforms, leaving companies vulnerable and unable to effectively know or control which parties have access to sensitive corporate or personal data.
Organizations need to be able to see all the configurations and user permissions of each and every app, including all the SaaS-to-SaaS apps that have been granted access by users. This way security teams can retain control of the SaaS stack, remediate any issues, block any apps using too many privileges and mitigate their risk.


In a world where identity is the new perimeter, user passwords are essential to protect your SaaS applications from unauthorized access. Effective password policies that are enforced at the corporate level reduce the gateway into your corporate data.
SaaS applications include a number of security settings that promote safe password use. When these settings are misconfigured, however, users can use passwords that are easily guessed by threat actors or can be discovered by hackers during a brute-force attack.
Compromised passwords do more than provide threat actors with access to information that should be protected. They open the possibility of an account takeover attack. Savvy threat actors may take their infiltration to the next level, particularly when accessing high-privilege accounts. Once in, they create new high-privilege users accounts that can be weaponized to download confidential data, conduct ransomware attacks, or maintain long-term espionage programs.
Password configurations make up about 6% of all SaaS app settings. Despite their small number, they play a large role in limiting access to sensitive information.
The configurations within the SaaS application are in place to better secure account access, which is why we’re sharing some key password configuration benchmarks for Salesforce, M365, and Google Workspace.
Password configurations cover the makeup of acceptable passwords as well as passwords for different categories of users. These configurations include:
There was a time when security experts universally recommended users update their passwords every 60-90 days to prevent accounts from being accessed by cybercriminals. As a result, most users got in the habit of using easily memorable passwords that didn’t change much.
In 2017, Digital Identity Guidelines from the National Institute of Science and Technology (NIST) recognized that this approach led to an overall weakening of user passwords. Instead, they recommended strong passwords that only need to be changed in the event of a user request or evidence of an authenticator or credentials being compromised.
Salesforce’s settings take the NIST recommendation into account with two settings. Passwords Expiration and Profile Passwords Expiration should both be set so that they never automatically expire.
To do so, first set the general policy following these steps:
This password setting is governed by default in the general Password Policies of the account but can be overridden by selecting a different setting in a specific profile.
Take the following steps for specific profiles, which can be used to override the general policies for a specific user account.
Here are some Salesforce user benchmarks to measure your settings against.

Microsoft 365 uses several settings to prevent users from using easily guessable words as their passwords, which helps defend against password spray attacks.
The Custom Banned Password and the Enforce Custom Banned Password security settings allow administrators to add a list of up to 1,000 words that cannot be included in a password. The Password Protection for Windows Server Mode and Password Protection for Windows Server Active Directory configurations are relevant for organizations using hybrid environments. These two settings configure Azure Active Directory to work with on-prem data centers, and prevent the use of corporate specified words.
The list of banned words should include corporate keywords, such as company products, trademarks, or executive names. It should also include things like local sports teams names, popular players, or famous actors.
Here are some M365 benchmarks to measure your settings against.

App passwords can be used in some circumstances to bypass MFA security checks and company-monitored SSO. These apps can be easily compromised when threat actors get a user’s login credentials.
Super Admins with App Passwords is particularly dangerous. These high-privilege users require app passwords so they can access apps when SSO is down. However, this access is risky because it bypasses multi-factor authentication. Configurations should be set to periodically confirm with Super Admins that they require their high-privilege level of access.
Regular users that are accessing apps with a password should also be approached, through the system, to confirm that they require access to specific apps. Those who are no longer in need of the applications should remove apps that they no longer need.
Here are some Google Workspace benchmarks to measure your settings against.

Passwords are most effective when coupled with MFA or as part of an SSO.
Strong passwords policy includes:
Up next in our Benchmark for SaaS Apps Series is Endpoint Protection.


Malware is harmful code designed to infect, damage, or provide access to computer systems. It can take many different forms, including viruses, worms, Trojan horses, ransomware, adware, and spyware. While it is easy to understand how that impacts a computer or mobile device, it is less clear when discussing SaaS applications.
However, malware can be used for various purposes, such as stealing sensitive information, destroying or altering data, causing system failures or crashes, and creating a backdoor for hackers to gain unauthorized access to a system. It spreads through infected email attachments, downloads, malicious websites, or vulnerabilities in a system's software or security protocols.
Research has shown that 40% of businesses using SaaS applications have malware hidden within the files and documents stored in their SaaS stack. Almost any file, from presentations, spreadsheets, and documents to images and PDFs can have harmful malware embedded within it. Once the file is accessed, the malware may have a chance to enter the user’s device or network and cause damage.
SaaS applications include settings designed to prevent the spread of malware in this manner. These configurations can protect against malware, as they reduce the vulnerabilities in a system that malware can exploit. Malware often targets known security weaknesses and exploits them to gain access to a system or to spread throughout a network. By setting security configurations, users remove these vulnerabilities and make it more difficult for malware to gain a foothold in your system.
Clickjacking is a type of attack that takes something which appears safe, such as a button or link on a webpage, and hides a malicious link within it. Once clicked upon, it can lead to data intrusions, unauthorized email, credential changes, or other site-specific results.
Within Salesforce, hidden iframes can be maliciously placed to entice users to click buttons and links that are in the hidden iframe. Once the user clicks on the link, they have triggered some type of attack.
There are four levels of protection to prevent clickjacking attacks from taking place:
Here are the malware configuration benchmarks that you can use to measure your security posture.
Please note: Data in these tables comes from over 200 anonymized customer tenants in the Adaptive Shield platform

The best way to prevent malware from causing any damage is to prevent it from reaching your users’ inboxes. However, malware does occasionally find a way to get past filters and checks within email gateways and make its way to the user.
With Zero Hour Auto Purge enabled, Microsoft 365 continues to check unread messages in the inbox for malware. This advanced level of protection stops all types of malicious code from entering the system, preventing large-scale attacks capable of infecting an entire network.
However, Zero Hour Auto Purge is only effective when it is enabled. To turn it on, follow these steps.
Here are the malware configuration benchmarks that you can use to measure your security posture.
.png)
Google Workspace prevents malware from reaching your inbox with a series of settings that identify malicious codes, encrypted messages, and harmful links. Some of these measures include scanning email attachments and blocking those with malware, identifying phishing emails, blocking malicious links from reaching the inbox, and using encrypted connections to prevent unauthorized access.
When it detects suspicious attachments and encrypted messages, Google Workspace isolates the attachments, moving them to the spam folder or into quarantine. Users are protected from unknown senders and the damage they wish to inflict on the company.
However, Google Workspace is only able to provide those protections when its settings are configured securely. To prevent suspicious attachments and scripts from unknown senders from reaching employee inboxes, follow these steps.
Here are the malware configuration benchmarks that you can use to measure your security posture.

Up next in our Benchmark for SaaS Apps Series is Password Management.


Data leakage is the unauthorized transmission of data from within an organization to external destinations or parties. In a SaaS context, it can refer to data that is exposed without passwords or an expiration date. The data may contain sensitive financial records, customer PII, strategic documents, or any number of things that are best kept within the organization.
Data Leakage Protection (DLP) are the configurations within the SaaS applications that limit exposure. They make up 13% of all SaaS app configurations, protecting sensitive data in Google Workspace, Microsoft 365 (M365), Salesforce, Box, Workplace, ServiceNow, and hundreds of other applications.
Employees often need to share documents with external stakeholders, including vendors, partners, and freelancers. To truly be secure, files should be authorized for use by specific users and include an expiration date when the file is no longer accessible. However, this can become difficult in practice.
When multiple users within a vendor need to review the document, employees must choose between clicking “share with all users” or add specific users that can access the files. For employees that aren’t security experts or concerned about security issues, sharing with anyone with the link is the preferred choice. They don’t need to add multiple users to a file or be bothered by file-sharing requests.
The trade-off for that convenience is a weakening of document security. When files don’t require passwords or login names, they can be accessed by anyone. The configurations within the SaaS application are in place to prevent this type of exposure, which is why we’re sharing some key benchmarks that companies are using for high-risk DLP configurations in Salesforce, M365, and Google Workspace.
Monitoring files that have been shared outside the organization is a difficult task. Once files have been shared, it is almost impossible to track their distribution. The types of configurations that are most concerning from a DLP perspective center on:
Salesforce relies on configurations to prevent data from being exposed to external users. When set correctly, Guest User Sharing Rules ensure that documents remain secure and that only authenticated guest users can access a file.
However, when Guest User Sharing Rules are enabled, uncredentialed users can access any document that matches the sharing rule’s criteria. In its guidelines, Salesforce tells administrators to implement security controls that match the sensitivity of the data, and reminds users that “Salesforce is not responsible for any exposure of your data to unauthenticated users based on this change from default settings.”
While there are use cases for allowing this permission, it is critical that security teams periodically review their sharing settings to protect confidential files from exposure. To check those permissions:
Benchmark your Data Leakage Protection settings against other Salesforce users.

Automated email forwarding to external email addresses can pose a security risk, as confidential information and files may be shared outside the organization. Microsoft 365’s configurations enable administrators to configure inbox rules that prevent users and administrators from mailbox forwarding.
Outbound spam filter policies can be used to control automatic forwarding. By turning the setting off or selecting Automatic - System-controlled, automatic forwarding to external email addresses is disabled.
Here are some M365 benchmarks to measure your settings against.

Google Workspace enables users to have desktop access to their files in Google Drive by deploying the Backup and Sync client. However, this feature stores Google files locally on the desktop, where they can be opened and read by anyone with access to the computer.
To reduce the risk of data leaks, desktop access to Drive should be removed. To do so, follow these steps:
Here are some Google Workspace benchmarks to measure your settings against.

Data leakage is a serious problem facing organizations using SaaS applications. Users often want reduced friction when sharing files with external parties, but that reduced friction can expose company secrets to others.
Security teams can better secure company documents by:
Up next in our Benchmark for SaaS Apps Series is Malware Protection.


Access control is the key to your SaaS kingdom. It determines who has access, their permission levels, and the steps they need to take to enter into the system.
Access control is the center of your SaaS security foundation, which is why it accounts for 59% of all SaaS configurations. Of the 13,000 configurations Adaptive Shield checks out of the box, over 7,500 address access control.
Access control is a multi-level domain, with layers of security elements all intended to prevent unauthorized users and threat actors from accessing your data. This first line of defense requires oversight and nuanced approach to balance SaaS usability and availability with security.
Access control configurations impact every employee within the company with access to specific apps. Employees from different teams may require different areas of access, while employees with a team may need different levels of access.
In an app like Salesforce, IT admins need administrative access. Some sales personnel may need access to marketing costs, while others might also need access to reports. On the sales team, sales reps should only have access to their leads, while sales managers should have access to all the leads within their department or domain.
Creating these types of role-based access profiles is complex, and it’s tempting to over-permission users. The configuration settings may appear overwhelming, which is why we’re sharing some foundational settings within Salesforce, Microsoft 365, and Google Workspace for an effective access control policy.
Salesforce is the leading CRM in the market. It contains an immense amount of sensitive information, and protecting that data is of paramount importance. Comprehensive user authentication policies are vital to ensuring security.
Connecting Salesforce to your organization’s SSO/IDP solution is one of the core ways to ensure and enforce access control. Over 80% of the Salesforce instances our research team reviewed have enabled SSO. However, only 2% of those organizations required users to login through SSO.
A surprising 98% of organizations allow their users to access Salesforce using a basic username and password authentication. This misconfiguration enables threat actors to capture usernames and passwords through sophisticated phishing attacks or other means. Once that username is compromised, threat actors have access to a wealth of customer and pipeline data.
Here are some other Access Control configuration benchmarks that you can use to measure your security posture against.


Microsoft 365 documents, presentations, spreadsheets, and email are among a company’s most valuable resources. Sharepoint servers contain files, making it easy for employees to collaborate on critical projects. The data within Microsoft 365 demands robust access control. Here are Access Control benchmarks to measure your company against.
Legacy authentication protocols in M365 may be undermining your entire security setup. Security teams can implement SSO, harden password policies, require MFA, and keep Azure Active Directory updated and well maintained – and still find themselves exposed.
Legacy authentication protocols within M365 means usernames and passwords are often stored on the device. These login credentials are sent at every request, increasing the likelihood of those access credentials being compromised especially if sent without Transport Layer Security (TLS).
Basic authentication, while necessary for companies using legacy software, is unable to enforce MFA and is superseded by modern authentication. These include IMAP, OAB, Exchange ActiveSync (EAS), and others.
As a result, over 80% of the M365 instances we reviewed had at least one legacy authentication protocol enabled, and over 50% had two or more. 10% have almost all legacy authentication protocols enabled, and many of them are used daily.

As a result, over 80% of the M365 instances we reviewed had at least one legacy authentication protocol enabled, and over 50% had two or more. A surprising 10% have almost all legacy authentication protocols enabled, and many of them are used daily.

Like M365, Google Workspace uses legacy authentication protocols, such as IMAP and POP. In addition, it uses some high-risk configurations that are unique to Google Workspace. App Passwords are a special tool used to connect third party applications to a SaaS stack. App Passwords can provide access into an application, and they don’t require MFA for authentication.
App Passwords were created to allow external apps to integrate with Google Workspace as the equivalent of an API key. However, they allow users to bypass MFA and SSO.
To strengthen an organization’s security and reduce risk, app passwords should never be used by super admins. Regular users can use App Passwords, as long as the passwords are monitored and rotated appropriately.


Access Control is a significant security function and creates the first line of defense of an organization’s SaaS security policy. In turn, security teams are responsible for strengthening and ensuring an organization’s access control.
Security teams can begin creating a strong foundation of access control by:
Up next in our Benchmark for SaaS Apps Series is Data Leakage Protection, the practice of detecting and preventing data breaches, exfiltration, or unwanted destruction of sensitive data.


As organizations work toward securing their SaaS apps, security teams are looking for benchmarks that can help guide their efforts. SaaS ecosystems are growing quickly, and without some standardized tool to measure success, most security teams lack the data to know where they stand.
In our Benchmarks for SaaS Apps series, we’ll share benchmark data for five high-impact security domains. These domains contain thousands of settings, spanning organizational users, applications, and instances. When configured correctly, they limit data access to authorized users, protect against SaaS ransomware, and limit potential breaches.
Each article in this series will cover high-risk configurations in Google Workspace, Microsoft 365, and Salesforce, as well as provide data that can be applied to every app in your SaaS stack.
The top five security domains in SaaS are:
Adaptive Shield cybersecurity experts and researchers extracted anonymized data from hundreds of tenants and apps within the Adaptive Shield system.
First up in the series is Access Control!
.webp)
.webp)
The healthcare industry is under a constant barrage of cyberattacks. It has traditionally been one of the most frequently targeted industries, and things haven't changed in 2023. The U.S. Government's Office for Civil Rights reported 145 data breaches in the United States during the first quarter of this year. That follows 707 incidents a year ago, during which over 50 million records were stolen.
Health records often include names, birth dates, social security numbers, and addresses. This treasure trove of data is used in identity theft, tax fraud, and other crimes. It is the high value of the data that makes healthcare applications such a promising target.
The healthcare industry was hesitant to adopt SaaS applications. However, SaaS applications lead to better collaboration among medical professionals, leading to improved patient outcomes. That, combined with SaaS's ability to reduce costs and improve financial performance, has led to the industry fully embracing SaaS solutions.
Today, medical facilities store patient records, billing records, and other sensitive data containing both PHI (protected health information) and PII (personally identifiable information) are in many cases stored in Salesforce, Google Workspace, and Microsoft 365.
In the United States, medical data is protected under HIPAA, the Health Insurance Portability and Accountability Act. Security failings impacting more than 500 individuals are broadly reported in the media and are accompanied by significant fines.
SaaS applications like Salesforce, when they contain HIPAA-compliance add-ons, are secure enough to prevent threat actors from entering the applications and accessing patient data. SaaS applications are always updated to the latest version and don't have the same types of vulnerabilities found in on-premises software.
SaaS developers invest heavily in delivering secure software solutions. They maintain teams of security professionals who constantly monitor and update their software to address emerging threats. These applications run on advanced infrastructure with robust physical security measures, redundant systems, and disaster recovery systems. They adhere to strict industry standards, ensuring the highest level of security and compliance for healthcare data.
In a report issued in August 2022 by the Office of Information Security and the Health Sector Cybersecurity Coordination Center (HC3) on the impact of social engineering on healthcare, researchers found that 45% of all attacks on the healthcare industry began with a phishing attack. Employees were manipulated into handing over their login credentials, allowing threat actors to enter through the front door.
SaaS applications have multiple layers of defense against those types of breaches. For example, many SaaS applications require MFA during login. Without a one-time password, most threat actors will be thwarted when trying to access with just a username and password. Second, many organizations require SSO to access their apps. This additional layer of identity fabric creates more complexity for threat actors as they attempt to breach the SaaS application. There are over 100 security checks within Salesforce and Microsoft 365 that combine to form a strong perimeter of defense.
It wasn't long ago that anyone who managed to breach a SaaS application had carte blanche to do anything within their permission set. Steal credentials from an admin, and the entire app could be in control of the threat actor within minutes. That is no longer the case.
Leading SaaS security tools have added a layer of identity threat detection and response (ITDR) to the equation. This last line of defense ensures that if threat actors were able to access the application, security teams are alerted when threat actors enter the SaaS app, even if they access the application with valid credentials.
ITDR recognizes behavioral anomalies within the individual user. If a threat actor enters a SaaS stack and acts suspiciously, ITDR will flag those behaviors and alert the security team, who can disable the user account and conduct an investigation.
The healthcare industry is already familiar with role-based access to medical records. Those who don't need access to patient records aren't able to review medical files. This approach is critical to SaaS security. By following the Principle Of Least Privilege (POLP), each user is only able to access materials required for their role. If credentials for those users are compromised, threat actors will be unable to access the PHI data that they are searching for.
A SaaS Security Posture Management (SSPM) platform, like Adaptive Shield, is the most important tool used to defend healthcare applications. SSPMs conduct 24/7 automated monitoring of security settings, staying on top of settings and alerting security personnel when configurations are changed. If a user mistakenly reduces the app's security posture, SSPMs help to ensure that the misconfiguration is closed quickly.
SSPMs also monitor third-party applications that connect to the core SaaS apps. It tracks their permissions and triggers an alert when granted permissions exceed corporate policy or HIPAA standards. It tracks dormant users, external users, and authorized users, ensuring that they, like physicians treating patients, do no harm to the application.
By implementing an SSPM, healthcare organizations can ensure that the sensitive patient data stored within the applications are secure.


Today, we released that one of our customers achieved a 201% return on investment (ROI) in less than six months from adopting a SaaS Security Posture Management (SSPM) solution, according to results of a Forrester Consulting Total Economic Impact™ (TEI) study.
The 2024 Forrester Consulting TEI study is based on data from the customer experience of a global corporation with an annual revenue of over $10 Billion USD. The organization is undergoing rapid SaaS adoption across business-critical applications and has adopted Adaptive Shield’s SSPM platform in order to control and manage the security of their entire SaaS ecosystem.
The model Forrester designed to determine this ROI includes elements of SaaS Security score, operational efficiency against costs of a data breach like lost employee productivity, lawsuits and settlements, and regulatory fines.
“We started seeing some small incidents resulting from SaaS misconfiguration, so we needed to do something about it… The incident was a wake-up call for us that we really need to look at all the configurations at scale,” asserts the Chief Security Officer (CSO) of the $10 billion global media and information services corporation interviewed for the TEI.
After they brought on Adaptive Shield, the CSO shares, “When we look at the security score trends, we observed significant increase over time. In reality, the improvement is even greater because we have already fixed some issues during the POC (proof of concept).”
The financial analysis of the implementation of Adaptive Shield platform with this customer found benefits of $2.18 million over three years. The payback period on the original investment was less than six months. Results from utilizing Adaptive Shield included more efficient SaaS Security management with improved visibility for stakeholders, enhanced security compliance control, and increased collaboration between business and security teams.
“There is a common misconception that SaaS providers take care of the security of the organizations’ apps. While SaaS vendors invest a lot in their security, the market has now come to realize that it’s the organization’s ultimate responsibility to ensure that their apps’ security posture is monitored and managed internally. Similar to the case of IaaS and CSPM tools, ” says Maor Bin, CEO and co-founder of Adaptive Shield.
“With the frequency of SaaS attacks only growing and SaaS incidents continuously exposing organizations to data leaks, breaches, compliance failures, and other potential disruptions in business operations, SSPM is the only way for organizations to secure SaaS data. Beyond the qualitative, this TEI study quantitatively presents just how much Adaptive Shield helped improve our customer’s SaaS security and streamline business costs.”
Key benefits found in the study:


Effective marketing operations today are driven by the use of Software-as-a-Service (SaaS) applications. Marketing apps such as Salesforce, Hubspot, Outreach, Asana, Monday, and Box empower marketing teams, agencies, freelancers, and subject matter experts to collaborate seamlessly on campaigns and marketing initiatives.
These apps serve as the digital command centers for marketing professionals. They house essential go-to-market strategies, and are often connected to live payment systems authorized to spend substantial budgets. Ensuring their security is a complex task, given the multitude of applications, application owners, configurations within each app, users, interconnected apps and more. In this article, we explore the top Marketing SaaS application use cases, from external users and publicly shared links to connected apps and credit cards — and how to ensure the security and integrity of the data stored within them.
Marketing departments frequently grant administrative or high-access permissions to agency and freelance partners who need access to sensitive reports and data in order to perform. However, managing these external users can be a daunting task. It's vital to closely monitor their permissions and trim them down to the minimum necessary level. Additionally, there's often a gap between the time an employee leaves an agency and when the agency notifies the client. During this period, former employees can retain their access.
Collaboration with agencies often requires sharing files, project management boards, and folders with various team members. Using one set of public links for all users is a tantalizing option, as it cuts down on administrative tasks every time a new user is introduced into the project.
However, this approach can inadvertently expose sensitive assets to former agency employees or other unintended recipients, as public links can be used by anyone.
Marketing budgets often involve significant sums of money, and this financial data is highly sensitive. It's not uncommon for external agencies to manage these budgets, and if left unsecured, it could lead to malicious activities like unauthorized data access or the running of negative campaigns. Organizations need to ensure that access configurations are tightly controlled, with Identity Threat Detection & Response (ITDR) mechanisms sending alerts when users exhibit anomalous behavior.
Marketing departments rely heavily on prospect and customer data, which is stored and analyzed in SaaS databases like Customer Relationship Management (CRM) systems, Marketing Automation Hubs, and Sales Development Representative (SDR) tools.
Protecting this sensitive data is highly important and requires robust access controls, multi-factor authentication (MFA), and constant monitoring of internal user behavior.
Marketing teams utilize a wide array of connected applications to support their daily operations. These range from calendar apps, to video conferencing plugins, design, project management tools and ad optimization apps. Each of these applications requests different levels of permissions to access company data, some of which are quite intrusive. Organizations need visibility to quantify the risk from these applications.
SaaS apps hold the key to productive and efficient work. Any potential data leak or breach is not only a problem for the organization at large, but especially for the Marketing department, who retains the ultimate responsibility for ensuring the brand. Any reputational damage, especially if caused by a MarTech solution, would bring severe impact.
SaaS Security Posture Management (SSPM) platforms enable security teams to work collaboratively with Marketing and ensure the security of these applications. SSPMs monitor and manage internal and external users, ensure tight access controls across the SaaS stack, and safeguard sensitive data. The right SSPM solution will ensure that no operational workflows are disrupted and that all marketing stakeholders remain efficient and productive.


Mergers and acquisitions (M&A) are exciting times for organizations. Initially, most of the attention is focused on integrating two companies into a single entity, and exploring the new capabilities brought on due to the merger. In this environment, surrounded by organizational changes and amid swirling questions surrounding responsibility, SaaS security is often nothing more than an afterthought that falls through the cracks.
While that attitude is understandable, it exposes companies to risk. Additional applications mean a larger attack surface, and delays in reviewing and upgrading SaaS security may expose newly acquired secrets to threat actors.
While there are a myriad of benefits to securing your new SaaS stack, here are three that demand your immediate attention.
During M&A, companies typically find they have multiple versions of the same applications in their SaaS stack. It can take years before all the applications are seamlessly integrated into a single instance, and some applications are never reconciled.
If the two companies originated in different industries, their configurations may be set to meet different compliance standards. Now that they are under the same corporate umbrella, those standards must be aligned.
Furthermore, different companies have different policies. With the two companies under a single roof, security teams must be able to automatically compare the differences to identify best practices and align the different instances under a single policy.
Employees are a common casualty in an M&A. When let go, they are removed from the Identity Provider (IdP) and automatically deprovisioned from any SaaS app connected to the company’s IdP.
While this would seem to solve the problem of former employees logging into corporate SaaS applications, it is only a partial solution. Applications connected to the company’s SSO will automatically deprovision the user’s SSO account. However, users will retain their access rights to any application that is not connected to the SSO. These users must be removed manually.
App admins introduce another challenge to security teams. While their SSO access may be deprovisioned, these users typically have local access as well. The combination of admin rights and local access means that employees in this category can inflict significant damage to their former employer. This includes the ability to change settings to make data public, add new user accounts to exploit at a later date, download and expose PII or corporate secrets, and delete all assets saved within the application.
Gaining a full picture of your users and their access is essential from the moment the acquisition is complete.
Companies in different countries and industries are held to different standards by regulatory agencies. These requirements apply to all company assets, including ones that are newly purchased.
While all companies do some form of due diligence on the security standards being maintained by the target company, the first time they can actually apply their standards to purchased SaaS applications is post-merger.
Public breaches following an M&A are a PR nightmare; ones that occur because newly acquired applications are non-compliant are a disaster. Customers and partners question the entire merger, and tend to look for other providers they can trust.
To avoid these issues and others, it’s vital that security teams rapidly review and monitor their newly acquired applications. An SSPM platform can be connected to applications over API in minutes, and begin sharing its findings quickly.
In addition to a posture score for each connected app, security teams can export app user lists for the entire SaaS stack. With that information in hand, they can run reports to identify users who must be deprovisioned, and have their SOAR automatically remove access to former employees.
SSPM-based ITDRs monitor the entire SaaS stack and will recognize the techniques, tactics, and processes of threat actors. Furthermore, it can identify anomalous user behavior, and prevent application breaches from turning into data breaches.
SSPMs can also show which misconfigured settings are hurting compliance scores, and help your organization meet required regulatory standards.
As time moves on, SSPMs will enable security teams to compare security settings from different instances of the same application. App owners and security teams can create benchmarks that derive from the best practices of both organizations, as they move forward in integrating the two SaaS stacks.
After a merger is an interesting time in every part of the organization. For SaaS security, it’s an important opportunity to secure the SaaS stack and allow business to proceed as usual.


Earlier this week, ServiceNow announced on its support site that misconfigurations within the platform could result in “unintended access” to sensitive data. For organizations that use ServiceNow, this security exposure is a critical concern that can result in a major data leakage of sensitive corporate data.
ServiceNow is a cloud-based platform used for automating IT service management, IT operations management, and IT business management for customer service, as well as HR, security operations, and a wide variety of additional domains. This SaaS application is considered to be one of the top business-critical applications due to its infrastructural nature, extensibility as a development platform, and access to confidential and proprietary data throughout the organization.
Simple List is an interface widget that pulls data that is stored in tables and uses them in dashboards. The default configuration for Simple List allows the data in the tables to be accessed remotely by unauthenticated users. These tables include sensitive data, including content from IT tickets, internal classified knowledge bases, employee details, and more.
These misconfigurations have actually been in place since the introduction of Access Control Lists in 2015. To date, there were no reported incidents as a result. However, considering the recent publication of the data leakage research, leaving it unresolved can now expose companies more than ever.
It’s important to point out that this issue was not caused by a vulnerability in ServiceNow’s code but by a combination of configurations that exist throughout the platform.
This issue stems from security controls in a ServiceNow Access Control List (ACL) widget called Simple List, which puts records into easily readable tables. These tables organize information from multiple sources and have configurations with a default setting of Public Access.
Because these tables are the core of ServiceNow, the issue isn’t contained within a single setting that can be fixed. Potentially, this needs to be remediated in multiple locations within the application in combination with the usage of the UI widget, and throughout all tenants. To further complicate the issue, changing a single setting could break existing workflows connected to the Simple List tables, causing severe disruption of existing processes.
On the other hand, leaving these tables and applications exposed could have major security implications now that this issue has received so much attention.
We encourage all ServiceNow customers to review the recent guidance published by ServiceNow in their knowledge base article – General Information | Potential Public List Widget Misconfiguration.
To summarize, exposure assessment and remediation measures shall include:
Organizations that use a SaaS Security Posture Management (SSPM) solution are able to gain visibility into ServiceNow’s configurations and remediate the issue based on the recommendations.

To help organizations secure ServiceNow, Adaptive Shield is offering a free ServiceNow assessment for this issue. After a quick validation of your org, our Security research team will send you a report detailing any exposure your portals may have from this misconfiguration.
Click here to request the complimentary assessment.


The Quick Serve Restaurant (QSR) industry is built on consistency and shared resources. National chains like McDonald’s and regional ones like Cracker Barrel grow faster by reusing the same business model, decor, and menu, with little change from one location to the next.
QSR technology stacks mirror the consistency of the front end of each store. Despite each franchise being independently owned and operated, they share subscriptions to SaaS applications, or use multiple tenants of the same application. Each app is typically segmented by store. Corporate IT and Security has access to the entire database, while each franchise has visibility into its own data.
These SaaS apps cover everything from CRMs to supply chains to marketing and HR. The data within is used to understand consumer habits, improve marketing campaigns, and manage employees. Like every other industry, QSR SaaS apps contain a wealth of data that needs to be secured.
At the same time, we’re seeing food chains come under attack. While it is unclear whether the recent breaches at fast food chains involved SaaS applications, what is clear is that threat actors are increasingly turning their attention to restaurant chains. QSRs have unique challenges and should take specific, significant security measures to protect their SaaS applications.
Like all businesses, QSRs need to prevent their data from falling into the hands of threat actors. In addition, QSRs have a secondary concern that few other businesses experience.
Burger King has about 7,000 franchises in the United States. These individually owned and operated restaurants often compete with each other. The different franchises may store data within the same SaaS applications. However, the data is segmented to prevent stores from seeing intra-chain competitor data.
Segmenting data so that the corporate CISO team has a full view of their applications, regional management offices have access to aggregated data within their region, and individual franchises are only able to see their data requires sensitive configurations through role-based access tools.
If misconfigured, data can easily be exposed within the chain. System administrators must constantly monitor their configurations to ensure this doesn’t happen.
In addition to sharing segmented applications, many QSRs use different tenants of the same application. Each tenant must be secured separately, with its configurations following the guidelines of the chain.
Some stores may have instances of applications that are highly secure, while others may have poor security posture. Ensuring that each branch maintains strict security standards in this type of environment is a monumental task.
Another unique challenge for today’s QSRs stems from the fact that they have been one of the major players affected by COVID-19 and the great resignation. Many restaurants have cut back hours, reverted to drive-thru only, or operate with skeleton crews trying to serve their customers.
The employee shortage means that more employees are given access to systems that would have been controlled by managers in the past. The shortage is also driven by employees staying at the job for short periods of time. These employees are not “cyber-trained,” and are far more susceptible to social engineering attacks like phishing. Furthermore, they tend to be younger, and don’t always appreciate the repercussions of sharing their login credentials with friends and social networks.
As a result, onboarding and deprovisioning employees from thousands of chains across the globe is more important than ever before. Former employees need their access revoked as quickly as possible to limit the likelihood of data leaks, breaches, and other cyber attacks.
To battle these unique challenges, a SaaS Security Posture Management (SSPM) can come into the picture. SSPMs help restaurants manage the settings that separate data by store. It also compares different tenants, letting the corporate CISO team know which stores, regions, and countries have secured their applications, and which have misconfigurations that could result in data leaks or breaches.
Furthermore, SSPM alerts restaurants when they have connected high-risk third party apps to the core hub, or if their employees are accessing the SaaS application with low-hygiene devices. It governs users and access, ensuring that security tools like MFA are in place, and reviews user activity to detect threats that could lead to breaches.
When security settings are misconfigured, it lets app administrators and security teams know when configuration drifts have made data accessible to other stores, and offers remediation guidelines to help them reseal the data wall between franchises.
With an effective SSPM tool in place, QSRs can manage their restaurants using SaaS applications with confidence that their data is safe.


The Cloud Security Alliance (CSA), the world’s leading organization dedicated to defining standards, certifications, and best practices to help ensure a secure cloud computing environment, today released the findings of its latest survey, SaaS Security Survey Report: 2024 Plans & Priorities. Commissioned by Adaptive Shield, the leading SaaS Security Posture Management (SSPM) company, the survey gathered responses from 1,000-plus C-level security executives and professionals from all over the world, with the majority from North American enterprises.
“Many recent breaches and data leaks have been tied back to SaaS apps. We wanted to gain a deeper understanding of the incidents within SaaS applications, and how organizations are building their threat prevention and detection models to secure their SaaS ecosystem," said Hillary Baron, lead author and Senior Technical Director for Research, Cloud Security Alliance. “This explains why 71% of respondents are prioritizing their investment in security tools for SaaS, most notably turning to SaaS Security Posture Management (SSPM) as the solution to secure their entire SaaS stack.
“The attack surface in the SaaS ecosystem is widening and just as you would secure a cloud infrastructure with Cloud security posture management, organizations should secure their SaaS data and prioritize SaaS security,” asserts Maor Bin, CEO and co-founder of Adaptive Shield. “In last year’s survey, 17% of respondents said they were using SSPM. This year that figure has soared, with 80% currently using or planning to use an SSPM by the end of 2024. This dramatic growth is fueled by the fact that 55% of organizations stated they recently experienced a SaaS security incident, which resulted in ransomware, malware, data breaches, and more. Threat prevention and detection in SaaS is critical to a robust cybersecurity strategy spanning SaaS Misconfigurations, Identity and Access Governance, SaaS-to-SaaS Access, Device-to-SaaS Risk Management, and Identity Threat Detection & Response (ITDR).”
Among the survey’s key findings:
The survey gathered more than 1,000 responses from IT and security professionals from various organization sizes, industries, locations, and roles.


When SaaS applications started growing in popularity, it was unclear who was responsible for securing the data. What's far murkier, however, is where the data responsibility lies on the organization's side. For large organizations, this is a particularly challenging question. They store terabytes of customer data, employee data, financial data, strategic data, and other sensitive data records online.
SaaS data breaches and SaaS ransomware attacks can lead to the loss or public exposure of that data. Depending on the industry, some businesses could face stiff regulatory penalties for data breaches on top of the negative PR and loss of faith these breaches bring with them.
Finding the right security model is the first step before deploying any type of SSPM or other SaaS security solution.
There are several different groups of players involved in the SaaS security ecosystem.
SaaS App Owners – When business units subscribe to SaaS software, someone from within the business unit is typically responsible for setting up and onboarding the application. While they may have some help from IT, the application is their responsibility.
They choose settings and configurations that align with their business needs, add users, and get to work. SaaS App Owners recognize the need for data security, but it isn't their responsibility or something they know very much about. Some mistakenly assume that data security is only the responsibility of the SaaS vendor.
Central IT – In most large organizations, Central IT is responsible for things like infrastructure, hardware, and passwords. They manage IDP and servers, as well as oversee help desk activities. SaaS applications typically do not fall under their direct domain.
Central IT is more familiar with security requirements than the average employee, but it isn't their primary concern. However, it is important to keep in mind that they aren't security professionals.
Security Teams – The security team is the natural fit for implementing security controls and oversight. They are tasked with creating and implementing a cybersecurity policy that applies across the organization.
However, they have several challenges inhibiting their ability to secure applications. For starters, they are often unaware of SaaS applications that are being used by the company. Even for applications that they are aware of, they lack access to the configuration panels within the SaaS stack, and aren't always aware of the unique security aspects associated with each application. Those are controlled and maintained by the SaaS App Owners and Central IT.
GRC Teams – Compliance and governance teams are tasked with ensuring that all IT meets specific security standards. While they don't play a specific role in securing corporate assets, they do have oversight and need to determine whether the company is living up to its compliance responsibilities.
SaaS Vendor – While the SaaS vendor is absolved from any responsibility to secure the data, they are the team that built the security apparatus for the SaaS application, and have a deep knowledge of their application and its security capabilities.
Securing the entire SaaS stack requires close collaboration between the security experts and those managing and running their individual SaaS applications. We developed this RACI chart to share our perspective on the departments that are responsible, accountable, consulted, and informed for the different tasks involved in securing SaaS data.
Bear in mind, this table is not one size fits all, but a framework based on the way we see many companies handling their SaaS security roles. It should be adapted to the needs of your organization.

Developing the RACI matrix is important, but without the right tools in place, implementing security responsibilities becomes a near-impossible task.
Adaptive Shield’s SSPM platform facilitates clear communication between the security team and app owners. This communication includes alerts when misconfigurations occur that weaken the individual app’s security posture and when threats are detected by our IAM governance tools.
Communication is channel agnostic, so users can receive messages and alerts over email, Slack, Splunk, or the messaging platform of choice. All security-related notifications include remediation steps, providing app owners and central IT with a clear understanding of the steps required to mitigate the risk.
Within the platform, app owners have visibility and access to the app or apps under their control. They can see the status of their security settings, their security score, their users, third-party SaaS applications that are connected to their app, and the devices being used to access their SaaS app.
App owners and central IT are also able to dismiss a security alert due, either because it doesn’t apply or due to business needs, and consult with the security team on risk.
It’s easy for SaaS application security to be overlooked. It sits outside the view of the security team and is managed by competent professionals whose responsibilities don’t include security.
However, the data contained within the SaaS applications are often the lifeblood of an organization, and failure to secure the data can have disastrous consequences.
Fully protecting the data from exposure requires a cross-team effort and commitment from all parties involved, as well as a sophisticated SSPM platform built for SaaS in the real world.


Over the last year, we’ve seen increasing evidence of an upcoming recession. Interest rate hikes and inflation, energy uncertainty, and the war in Ukraine are all harbingers of rough times ahead. CNBC reported that more than 50,000 employees from Twitter, Meta, Amazon, Salesforce, and other tech companies lost their jobs in November. While no one knows exactly what 2023 will bring to the labor market, organizations need to be prepared for potential downsizing.
Removing user access for employees who no longer require access to company SaaS applications should be fairly straightforward. Most companies will disable users from their active directory and expect those users to be automatically removed from every application they have access to.
That works well when the SaaS app was set up with an SSO. However, many SaaS apps aren’t set up with an SSO. When users are removed from the IDP, they retain their login credentials.
Furthermore, many high-privilege users have extra accounts that are not managed within the IDP. This particularly applies to admins and app owners. Those users retain their high-privilege access, which can put all the data within the application at risk.
When SaaS applications are created, the install team typically creates multiple testing user accounts that are not associated with an IDP. These accounts are granted various levels of access, depending on the functionality or activity being tested. Often, these accounts are given names that are easy to remember, and since the account may be shared by multiple users, passwords are often a simple phrase or number pattern that is easy to share and remember. After setup is completed, these accounts are dormant but can be used to provide access.
Additionally, teams will often share a single user license among multiple employees. Again, these accounts are frequently high-privilege with easy-to-remember passwords, simplifying the team’s ability to get their work done.
These dormant and shared high-privilege accounts represent a significant threat during periods of downsizing. Former employees can use them to easily access corporate SaaS apps and sabotage or steal corporate IP. During periods of downsizing, security should be tightened to include reviewing permissions of these types of accounts, rotating passwords, and limiting shared accounts to situations where it is the only option.
User accounts are also frequently given to external users. As teams collaborate with vendors and partners, it’s more efficient to provide access to the system rather than have employees copy, paste, and email data to their partners. While some accounts are limited through RBACs, often times partner and vendor accounts have full access.
These external user accounts always create a degree of risk for organizations. However, when employees are let go and vendors lose their connection to the company, the risk level increases. Unaffiliated third-party vendors and partners may share data with competitors The only thing standing between company data and the public internet are login credentials. Company and customer data may be stolen, leaked, or shared with competitors.
User inventories provide a complete account of each user in every SaaS system. These were easy to assemble when everything was done on-premises. However, the transition to the cloud and SaaS applications has decentralized user data and limited the view of security personnel.
An effective user inventory would enable security teams and SaaS app owners to find and disable these types of accounts, eliminating the threat they pose following layoffs.
The inventory should be the single source of truth for everything a security team needs to know about a user. It should include login names the user may use on different applications, mulitple login names a high-privilege user might have for a single app, the applications that they can access, and the level of privilege they have within the application. It is vital to disable every access credential once an individual is no longer part of the organization.
However, the user inventory also needs to include test accounts, shared accounts, and external user accounts. Security personnel should be able to see which accounts are not using corporate IDP, the last date the account accessed the system, and access roles that are available to the user account. With that information in hand, security teams and app owners can make an informed decision as to whether these accounts represent a threat and need their access removed or limited.
Downsizing can be traumatic for a company and its employees, but is usually done to protect the long-term interests of the organization. Ensuring that data remains safe throughout this challenging period is not an easy task, but with the right tools in place, security teams and app owners can ensure the integrity and security of their SaaS.


Business leaders may fear an upcoming recession, but they fear falling behind their competitors even more. PwC’s November Pulse Survey found that 35% of executives are planning an acquisition or divestiture within the next 12-18 months. M&A has proven itself to be a key to business resurgence, strategic growth, and capability expansion.
One area that’s often overlooked during M&A due diligence is a target company’s SaaS landscape. These applications, which host tremendous amounts of sensitive company and customer data on the cloud, are often left unsecured through misconfigurations, orphan user accounts, and third-party applications with high permission sets.
While SaaS applications are secured by the app developer, the data within them can be easily exposed. Most large organizations have over 40 million toggles, switches, and checkboxes across their SaaS landscape that have to be set correctly to prevent data breaches, ransomware attacks, and malware.
Connecting an acquisition target’s SaaS stack to an SSPM can be done easily through existing APIs. Once connected, it takes just minutes to see the target’s SaaS hygiene and evaluate whether risk levels for the data within SaaS apps.
Merging two companies together is always high risk. By connecting an SSPM and looking under the SaaS hood, security analysts can offer their perspective on the merger and the level of risk they are taking on.
Getting ready for M&A? See how Adaptive Shield can protect you from SaaS surprises. Schedule a demo today.


Last month, The Verge reported on an amusing story of abusing Slack in a design, technology, science, and science fiction website. Tom McKay of IT Brew successfully hid on Slack after leaving the company in 2022 by assuming the persona of "Slackbot," remaining undetected by management for months. McKay shared screenshots of his antics on X and confirmed the escapade to The Verge. By changing his profile picture to resemble an angrier version of Slackbot's icon and altering his name to "Slackbot" using a special character (Unicode character “о”), McKay's account evaded deletion, allowing him to send bot-like messages to colleagues such as, “Slackbot fact of the day: Hi, I’m Slackbot! That’s a fact. Have a Slack-ly day!”.
On first read McKay's escapade seems as a lighthearted reminder of the potential for mischief in digital spaces. This was how the cyber community of Hacker News of Y Combinator received this news, which prompted users to share their own experiences from the old days, including a story from the days of dialup internet. However, as the thread continued, some people started wondering about the security impact. The r/sysadmin subreddit on the other hand was quick to realize the lack of an offboarding process. Other Slack admins shared their frustration and challenges of securing the SaaS app.
When employees transition out of an organization, it's imperative for security that access to corporate assets be promptly revoked. While much of this process is automated through workflows that remove employees from the identity provider (IdP), manual deprovisioning is necessary for applications not integrated into the IdP. Challenges in permanently removing users from SaaS applications include applications not synced with the IdP, the use of shared passwords among teams, and individuals retaining access through previously shared credentials acquired during their tenure. Failure to fully offboard users poses significant risks such as data theft or breaches, either by former employees or unauthorized individuals with stolen credentials. Overcoming these hurdles is crucial for maintaining robust security measures within organizations.
Slack is a leading collaboration and communication platform, revolutionizing how teams work together. With its intuitive interface, real-time messaging, and extensive integration options, Slack has gained popularity among organizations of all sizes. However, as with any cloud-based platform, it is crucial to address security issues and concerns to protect sensitive data and maintain a secure working environment. While Slack offers robust security measures, it is essential to be proactive in addressing potential security issues and concerns. Organizations must recognize the value of the data shared within the application, including sensitive files, proprietary information, and confidential communications.
To secure Slack, here are some best practices to follow:
As the cyber threat landscape evolves, even lighthearted stories like this one provide important lessons for organizations as they fortify their defenses against sophisticated attacks. The fake Slackbot underscores the pressing need for comprehensive security measures and proper off-boarding.
The easiest way to deprovision users from SaaS applications is through a SaaS Security Posture Management (SSPM) platform that is integrated with a SOAR. Using automated workflows, these processes quickly identify and fully deprovision offboarded employees who maintained access to SaaS applications.
By using an SSPM, enterprises can confidently move forward, knowing that access to their applications is under their full control.
Have users you need to deprovision? Download our latest ebook, Offboarding Employees from Your SaaS Stack in 7 Steps!
.png)

GitHub is in the news again, with malicious repositories stealing login credentials and cryptocurrency from developers’ devices. According to researchers at antivirus firm G-Data, these repositories, which are near clones of legitimate repositories, all lead to one of at least 13 GitHub repositories that install the RisePro malware.
Users have to go through several steps before they download the malware. They begin by downloading a README.md file, which contains a password for cracked software. From there, they can access the installer. The MSI installer unpacks a new executable file. Once the loader is executed, the malicious payload is injected into the victim’s device. RisePro gathers sensitive data and exfiltrates it to a Telegram channel.
While there are a number of settings one should check to make sure their GitHub is secure, protection from this type of attack begins with encouraging users to verify the authenticity of repositories before interacting with them. In this case, many of the repositories often mimic the naming of genuine repositories to confuse users.
GitHub has several configurations that organizations should secure to minimize the risk of accidental exposure. For example, enabling secret scanning and push protection for public and private repositories safeguards code against unauthorized access and code modifications.
Personal access tokens (PAT) should also be closely monitored. Configure the application to send alerts when unused PATs need to be revoked to prevent misuse, or let the security team know when an excessive amount of PATs are created.
Branch protection also plays a key role in GitHub security. To ensure that no malicious code is inserted into the main branch, all commits should be signed with a GPG or S/MIME signature. Furthermore, all code should pass a review that meets the company’s standards before it is merged.
Finally, security teams should review audit logs to find unauthorized changes. GitHub logs include information about additions to the codebase, which can be used for early detection of suspicious activities and identifying unauthorized access.
As the cyber threat landscape evolves, it becomes increasingly crucial for organizations to strengthen their defenses against sophisticated attacks, such as the one analyzed in this blog post. The recent malicious campaign targeting GitHub environments highlights the urgent need for robust security measures.
Deploying a SaaS Security Posture Management (SSPM) solution is essential for enhancing the security of GitHub environments. This involves prioritizing measures to counter coming from repositories. Furthermore, the importance of an Identity Threat Detection and Response (ITDR) solution cannot be emphasized enough, particularly for swiftly identifying and addressing incidents such as account compromises, unusual activities, and potential data leaks.
The insights shared in this blog post offer valuable guidance for organizations aiming to reinforce their security posture. They underscore the interdependence between SSPM solutions and ITDR capabilities in establishing a comprehensive SaaS security framework. By embracing these approaches, organizations can proactively shield their digital assets, ensuring resilience against evolving cyber threats while upholding the confidentiality, integrity, and availability of sensitive data.


In recent weeks, a concerning wave of cyber attacks has been targeting Microsoft Azure environments, compromising crucial user accounts, including those of senior executives. Proofpoint researchers have identified an ongoing malicious campaign, which utilizes sophisticated techniques like credential phishing and cloud account takeover (ATO).
This blog post will summarize and shed light on the nature of this attack. It will delve into some configurations that could mitigate the attack, and advise on activities to monitor within Azure to help organizations safeguard themselves.
The campaign, which started in late November 2023, employs credential phishing and cloud account takeover techniques. Threat actors use individualized phishing lures in shared documents, leading users to malicious websites. The targets vary across organizations, impacting individuals in different roles, including sales directors, account managers, and high-ranking executives.
Specific indicators of compromise (IOCs) include a Linux user-agent used during the access phase, primarily accessing Office365 applications. Full information on the IOCs can be found in the Proofpoint Community Alert.
Once compromised, attackers engage in MFA manipulation, data exfiltration, internal and external phishing, financial fraud, and mailbox rule creation to cover their tracks. The attackers' operational infrastructure involves proxies, data hosting services, and hijacked domains, with the use of proxy services to mask their location. Notably, non-proxy sources like Russia-based Selena Telecom LLC and Nigerian providers Airtel Networks Limited and MTN Nigeria Communication Limited may be involved.
While the campaign hasn't been attributed to a specific threat actor, Russian and Nigerian involvement is suggested based on previous cloud attacks.
In the ever-changing landscape of cybersecurity, hardening a SaaS environment and implementing robust threat detection capabilities are complementary strategies. They work together to create a resilient defense, reducing the attack surface, preventing vulnerabilities, and swiftly responding to emerging threats. Ultimately, they safeguard an organization's digital assets and ensure the confidentiality, integrity, and availability of sensitive information. In the next sections, we will show how to harden Microsoft Azure environments while implementing threat detection capabilities.
There are many legitimate uses of user-sent mail forwarding rules and addresses. However, as seen in these attacks it can lead to data leakage. Microsoft’s forwarding controls are complex and located in multiple places, including user and admin levels. It is important to review these settings and harden them.
Simultaneous activity from two different origins – Unless the attacker is sitting at a desk next to the compromised user, activity will be registered within the account from the compromised user and the attacker from different locations.
User appears from an unusual IP – A smart attacker can try to operate in hours when the compromised user is inactive to avoid simultaneous activity from two different origins. In such a case, it is important to monitor activity coming from an unusual IP.
User appears with an unusual device – Similar to an unusual IP, an unusual device can indicate a potential attack. In these attacks, Proofpoint noted that a Linux user-agent was used, which is a clear example of an unusual behavior.
User registered an authentication method from an unusual IP – Sometimes users change devices, go on vacation, and do other unusual things that may be legitimate from an unusual IP. However, changing an authentication method from an unusual IP is a red flag.
Brute force & password spray – These traditional attack vectors were not mentioned as used in this specific attack. Yet, these should always be mentioned and monitored while securing against an account takeover attack.
Downloads – Such as massive downloads from unusual IPs, or just uncharacteristic massive downloads.
Mailbox forwarding rules - Since massive downloads are frequently flagged, attackers are trying to find more elegant methods for data exfiltration. These include setting up mailbox forwarding rules that automatically forward every email from the victim to the attacker's email account. These are especially suspicious when coming from an unusual IP, or to an untrusted domain.
As the cyber threat landscape evolves, it becomes imperative for organizations to fortify their defenses against sophisticated attacks like the one dissected in this blog post. The malicious campaign targeting Microsoft Azure environments underscores the pressing need for comprehensive security measures.
Implementing a SSPM solution is paramount to hardening the Azure environment, with a focus on mitigating risks associated with credential phishing, cloud account takeover, and data exfiltration. Additionally, the significance of an ITDR solution cannot be overstated, especially when it comes to timely detection and response to account takeovers, unusual activities, and potential data breaches.
The insights provided in this blog post serve as a guide for organizations to bolster their security posture, emphasizing the symbiotic relationship between SSPM solutions and ITDR capabilities for a holistic SaaS security platform. By adopting these strategies, organizations can proactively safeguard their digital assets, ensuring resilience in the face of evolving cyber threats and maintaining the confidentiality, integrity, and availability of sensitive information.


Recent incidents continue to shed light on vulnerabilities that organizations face. A notable case involves a networking products company whose support website inadvertently exposed sensitive customer information, as reported by KrebsOnSecurity. This incident underscores the critical importance of robust security measures in safeguarding customer data. In this blog post, we'll delve into the details of the exposure, explore potential causes, and discuss actionable items to enhance security in Salesforce.
In this case, the support website that experiences a data exposure and was utilized by the networking products company was Salesforce. This lapse allowed unintended access to customer information, including device details, warranty status, and serial numbers. Discovered by a 17-year-old intern named Logan George, the incident highlights the potential risks associated with inadvertent data exposure.
Upon discovering the issue, the networking products company swiftly addressed the problem, emphasizing that the exposure resulted from a recent upgrade to its support portal. The company assured users that it has fixed the issue and currently has no reason to believe that any identifiable or personal customer data was compromised.
The company has not provided specific details on when the user rights issue was introduced. This raises concerns about the adequacy of user permissions within Salesforce assets, echoing a broader issue of misconfigurations that can lead to data exposure. This is the second time in less than a year that a Salesforce misconfiguration exposes sensitive information (that we know of).
In the wake of this incident, it is essential for businesses, particularly those dependent on platforms like Salesforce, to adopt strong security protocols. Here are key security principles crucial for safeguarding Salesforce. These security recommendations hold significance even in the absence of specific insights into the factors contributing to this particular data breach.
Salesforce Communities (“Experience”) refers to a feature within the Salesforce platform that allows organizations to create branded, customizable communities for collaboration and engagement with customers, partners, and employees in a secure and personalized online environment. Salesforce Communities often involve the sharing of sensitive data such as customer information, partner details, or internal communications. Proper security measures help safeguard this data from unauthorized access or breaches.
Salesforce Communities allow a high degree of customization. Therefore it's important to ensure that objects, files, records, and configurations follow best practices to minimize vulnerabilities. Regularly review and update security settings to adapt to evolving threats. Emphasis should be put on configurations that allow access and visibility to all users or guests.
In Salesforce, an object is a fundamental data structure used to store and organize information. Objects in Salesforce are akin to database tables and are central to the platform's data model. Salesforce provides a variety of standard objects, and users can also create custom objects to meet specific business requirements. Objects are made up of fields, which define the types of data that can be stored in them. Salesforce provides robust security features that allow administrators to control access to objects, fields, and records. This ensures that users have appropriate permissions to view, edit, or delete data. Objects should be reviewed constantly in order to make sure they are not exposed to unauthorized access. Also, make sure that they are not publicly accessible. Validate who has access to what object and how such access was given (such as Profile or Permission set).
Implementing robust authentication mechanisms ensures that only authorized users have access to the community. This involves using secure login methods and controlling user access based on their roles and permissions within the organization. Setting up strong password policies, requiring MFA, and using SSO is a good start. Complement good login methods with strong control on access to data with visibility into Profiles and Permission Sets making sure there is no permission sprawl and that all user access is only to “need to know”. Finally, implement monitoring tools and conduct regular audits to track user activities, identify potential security incidents, and ensure compliance with security policies.
The recent incident involving the networking products company's support website serves as a reminder of the ongoing challenges in managing large systems and the importance of robust cybersecurity measures. By implementing the suggested actionable items, organizations can fortify their defenses against potential data exposure risks, ensuring a safer digital environment for both the company and its customers.
Click here to read more about Salesforce’s Top Use Cases
.png)
.png)
A major player in the US telecommunications industry, with over 117,000 employees, recently experienced an insider data breach that has impacted nearly half of its workforce. The breach, discovered on December 12, 2023, occurred on September 21, 2023, when an unauthorized employee accessed a file containing sensitive information of over 63,000 employees.
The exposed data includes full names, physical addresses, Social Security numbers, national IDs, gender, union affiliations, date of birth, and compensation information. Fortunately, customer information remains unaffected.
The US telecommunications giant, in response to the breach, has emphasized its commitment to enhancing internal security measures. While there is currently no evidence of malicious exploitation or widespread data leaks, the company is taking proactive steps to prevent future incidents.
Sensitive employee data resides in Human Resources Information Systems (HRIS) and Applicant Tracking Systems (ATS), with Workday being a notable example. Sensitive records stored within these systems include:
As HR departments adopt more SaaS-based HRIS and ATS systems, they must take measures to prevent the cybersecurity risks associated with storing sensitive data on a cloud-based service. This is why HRIS and ATS systems based on SaaS became a prime target for threat actors. The Telecom incident underscores the urgency for organizations to fortify the security of these platforms.
In addition to the points addressed in the original breach article, it is important to understand the complexity of permission structures within their HR platforms and how they impact access control.
Organizations must invest time and resources to fully understand the permissions granted within their HR platforms. This includes not only knowing which employees have access to sensitive data but also understanding the specific actions they can perform with that data, for example read, modify, delete, etc. A lack of clarity in permission structures can lead to inadvertent exposure of sensitive information and increase the risk of insider threats. HR systems can have a very complex system composed of Security groups, Domains (within a Functional Area for example), Organizations, Roles, criterias, and more which interact with each other and add complexity that can create a security issue. Moreover, the importance of visibility into who has permission to what and through which controls cannot be overstated.
Continuous monitoring against insider threats is essential. Organizations should implement systems that provide real-time insights into user activities within HRIS. This includes monitoring for unusual behavior patterns such as excessive downloads, granting access to an external user (maybe their private email) and any deviations from normal usage patterns.
Continuous monitoring is not a one-time effort but an ongoing process. Regularly reviewing access logs, conducting periodic audits, and leveraging advanced analytics to detect anomalies are vital components of a comprehensive security strategy. This proactive approach allows organizations to identify and address potential security issues before they escalate into major breaches. An example of such a serious security issue is a threat actor changing the bank account details of an employee so that their payroll is redirected to the hacker's account. This example emphasizes the importance of safeguarding HRIS systems.

The recent data breach at the US telecommunications giant highlights the vulnerability of even major corporations to insider threats. By learning from such incidents, organizations can take proactive steps to secure their HR platforms, implement continuous discovery mechanisms, fortify their overall cybersecurity posture, and ensure a comprehensive understanding of complex permission structures. Constant adaptation and improvement are essential in the ever-changing landscape of cybersecurity.


AT&T Cybersecurity recently discovered phishing attacks conducted over Microsoft Teams. During a group chat, threat actors distributed malicious attachments to employees, which led to the installation of DarkGate malware on the victim’s systems.
This attack shines a bright light on the everchanging phishing surface as it expands from email to communication applications like Teams. This blog post will shed light on the attack, draw parallels between a previously identified vulnerability, and provide actionable remediation steps to fortify your organization against threats of this nature.
Inside the Attack
The attackers leveraged Microsoft Teams to send over 1,000 group chat invites. Once targets accepted the invitation, they were manipulated into downloading a file containing DarkGate malware.
This attack vector exploits the default settings in Microsoft Teams, which allows external users to message other tenants’ users. The scale of this threat is significant, as Microsoft Teams’ massive user base is an attractive target for cybercriminals.
In light of previously identified vulnerabilities and misconfigurations in Microsoft Teams, it is evident that the platform is susceptible to multiple attack vectors. One previous vulnerability involved an insecure direct object reference (IDOR), which allowed threat actors to bypass file-sharing restrictions and deliver malware directly to a target’s Teams inbox. Understanding the interconnected nature of these vulnerabilities is crucial when crafting a comprehensive security strategy.
Remediation
This vulnerability affects all organizations using Microsoft Teams in its default configuration. The following measures prevent threat actors from bypassing traditional payload delivery security controls, and mitigate the risk. These measures also help prevent the GIFShell vulnerability and the IDOR vulnerability found by Max Corbridge and Tom Ellson from JUMPSEC's Red Team.
To fortify your organization against these phishing attacks and vulnerabilities, Adaptive Shield’s security research team recommends implementing the following remediation measures:
1. Review External Access
Assess the need for external tenants to message members of your organization. If it is not essential, disable external access in the Microsoft Teams Admins Center. Set the “Choose which external domains your users have access to” configuration to “Block all external domains.
If external communication through Teams is required, enable access only for specific domains that regularly interact with users through Teams, to strike a balance between the organization’s communication needs and its security.
2. Block Invitations of External Users to Shared Channels
Shared Channel owners have the ability to invite external users to join their channel. This allows external users to read and write messages. In the Microsoft Teams Admin Center, under teams policy, toggle “Invite external users to shared channels” to off.

Figure 1: Microsoft Teams’ Teams Policy Configurations
3. Limit Conversation Starters
Prevent unmanaged external Teams users from initiating conversations within your organization. In the Microsoft Teams External Access configurations, disable "External users with Teams accounts not managed by an organization can contact users in my organization." By limiting who can start conversations, you reduce the likelihood of unauthorized access and communication.

Figure 2: Microsoft Teams External Access Configurations
4. Use Defender for Teams
Organizations that use Microsoft Defender for Office 365 can activate the Safe Attachments for Office 365 in the global settings to prevent users from inadvertently sharing malicious files in OneDrive and SharePoint+OneDrive. Once activated, Safe Attachments prevent users from opening or downloading files that are identified as malicious.

Figure 3: Microsoft Defender detects malware files
5. Educate Staff
Raise awareness among staff about social engineering campaigns that use productivity apps like Microsoft Teams. Emphasize that phishing attacks can take various forms beyond traditional emails. Encourage a security-conscious mindset and provide ongoing training so employees recognize and report suspicious activities.
Conclusion
As the threat landscape continues to evolve, organizations must stay proactive in securing their communication SaaS platforms. By learning from recent phishing attacks and vulnerabilities, you can bolster your defenses against cyber threats. Implementing the recommended remediation measures will contribute to a more secure Microsoft Teams environment, safeguarding your organization and its sensitive data from malicious actors. Stay informed, stay vigilant, and prioritize SaaS security to ensure the resilience of your SaaS data.


In a recent cybersecurity event reported by Lawrence Abrams in Bleeping Computer and disclosed by the Microsoft Security Response Center, Microsoft found itself at the center of a cyber-attack. Nobelium, a Russian state-sponsored hacking group also known as APT29 and Midnight Blizzard, breached Microsoft corporate email accounts for over a month. The attack, which was discovered on January 12, underscores the need for enhanced cybersecurity measures, even for industry giants like Microsoft.
Microsoft disclosed that the breach was initiated in November 2023 when threat actors, identified as Nobelium, executed a password spray attack to compromise a legacy non-production “test” tenant account. A password spray attack involves attempting unauthorized access to multiple accounts by systematically testing a list of potential login names and passwords. Nobelium parlayed their access into the test account to access a small portion of Microsoft’s corporate email accounts for over a month, including those belonging to at least one member of their leadership team.
At this time, more detailed information on the breach is being withheld by Microsoft. However, the following suggestions are basic security recommendations based on the disclosed information.
The breach highlights the critical importance of implementing multi-factor authentication (MFA) as a primary defense against unauthorized access. By adding an extra layer of security beyond passwords, MFA can thwart unauthorized access attempts, providing a robust defense against password spray attacks.
Single Sign-On (SSO) integration minimizes the attack surface, reducing potential points of compromise. Widely adopting and enforcing SSO could significantly enhance security posture, preventing unauthorized access to critical systems.
The compromise was initiated through a “test” account, and should serve as a reminder for the need to conduct regular audits that identify and deactivate unused accounts. Adopting the Principle of Least Privilege (POLP) is crucial to prevent unauthorized access.
The breach highlights the potential risks associated with underestimating the security of test accounts. Organizations should apply the same level of security diligence to test accounts and sandboxes as they do to production accounts to avoid exploitation by threat actors.
Continuous monitoring of identity activity is crucial for detecting anomalous behavior indicative of a security breach. Implementing advanced identity and access management solutions together with identity threat detection solutions allows organizations to swiftly identify and respond to unauthorized access attempts.
Microsoft emphasizes that the breach was not caused by vulnerabilities in their products or services but resulted from a brute force password attack on compromised accounts. While investigations are ongoing, Microsoft assures that the breach has not materially impacted its operations. This incident serves as a stark reminder that even tech giants must remain vigilant against evolving cyber threats.
As Microsoft continues to share additional details about the breach, it should prompt organizations worldwide to reassess and reinforce their cybersecurity protocols. We will continue to monitor this story, and update our recommendations as needed. However, the steps recommended here should be adopted by every organization that is serious about minimizing the risk of a similar attack.


On Wednesday, December 13, MongoDB detected an exposure in their systems, and customer account metadata and contact information. MongoDB is currently conducting an investigation to determine the extent of the exposure. In an email sent out to customers, MongoDB CISO Lena Smart informed users that at present they were “not aware of any exposure to the data customers store in MongoDB Atlas.” Despite these assurances, customers using MongoDB Atlas, the SaaS service provided by MongoDB, may be concerned that their managed environment is at risk.
MongoDB is a widely used and versatile NoSQL database management system that provides a flexible, scalable, and high-performance solution for handling unstructured or semi-structured data. Known for its document-oriented architecture, MongoDB stores data in JSON-like BSON documents, allowing for dynamic schema design and easy scalability. It is favored by developers for its ability to handle large amounts of data and its support for complex queries, making it a popular choice for modern, data-intensive applications.
MongoDB has told The Hacker News that the incident is still under investigation, and it’s not known how threat actors entered into the platform. However, the company believes the unauthorized access has been going on for some time before discovery. This type of exposure, where the threat actor has access for an extended period of time, is an indicator of data theft.
Due to the exposed customer account metadata and contact information, MongoDB has advised that customers be vigilant for social engineering and phishing attacks. Threat actors often use this type of data in developing sophisticated attacks.
Furthermore, MongoDB encourages all Atlas customers to activate multi-factor authentication (MFA) and implement a password rotation policy.
Adaptive Shield automatically checks MFA configurations, as well as all security-related settings in Atlas, as part of its automated monitoring processes, and issues alerts if the application is at risk. If you aren’t using Adaptive Shield, our security experts recommend checking the following settings to secure your Atlas instance:
Enterprises that use Adaptive Shield’s SaaS Security Posture Management (SSPM) platform can easily gain visibility into MongoDB’s Atlas posture. Adaptive Shield has 15 security checks covering access control, MFA, key management, and other security domains. Adaptive Shield also discovers admin and local accounts, as well as consolidates multiple identities into a single user for contextualized visibility into users accessing applications to enhance MongoDB security.



Earlier this month, threat actors leveraged compromised credentials to access Sumo Logic’s Amazon Web Services account. Sumo Logic immediately took down the infrastructure exposed by the incident, and conducted a rotation of credentials to prevent further compromises.
Sumo Logic is a cloud-based log management and analytics platform that empowers organizations to gain actionable insights from their machine-generated data. The platform is designed to handle and analyze massive volumes of log data, providing real-time visibility into the health and performance of applications, systems, and infrastructure. Sumo Logic helps organizations make informed decisions, troubleshoot issues, and optimize their IT environments by offering a centralized and scalable solution for log management, monitoring, and analytics.
At this time, Sumo Logic has reported that there is no evidence to suggest the breach will impact any of its customers.
It’s important to point out that the Sumo Logic breach was not a misconfiguration or vulnerability, but a breach caused by compromised credentials. The company reported that it has added extra security measures to further protect its system, including improved monitoring and fixing any gaps that might lead to future breaches of this nature.
Sumo Logic has recommended that its customers immediately rotate their Sumo Logic API Access key. This helps prevent attackers from using old keys that may have been compromised.
As an added precaution, Sumo Logic recommends that its customers rotate 3rd-party credentials that have been stored with Sumo Logic for data collection by the hosted collector (e.g., credentials for S3 access) or as part of webhook connection configuration.
Adaptive Shield’s platform has two security checks that are aligned with Sumo Logic’s recommendations.
Organizations that use Adaptive Shield’s SaaS Security Posture Management (SSPM) platform can easily gain visibility into Sumo Logic’s posture. Adaptive Shield has over 25 security checks for Sumo Logic, covering access control, key management, password management, and other security domains. Adaptive Shield also discovers administrative accounts and local accounts and consolidates multiple user identities into a single user as it monitors users and user behavior. This data, which is further enriched by other applications in the SaaS stack, provides contextualized visibility into those who are accessing the application and their behavior within the app, and is used to further secure the application.


Earlier this week, ServiceNow announced on its support site that misconfigurations within the platform could result in “unintended access” to sensitive data. For organizations that use ServiceNow, this security exposure is a critical concern that can result in a major data leakage of sensitive corporate data.
ServiceNow is a cloud-based platform used for automating IT service management, IT operations management, and IT business management for customer service, as well as HR, security operations, and a wide variety of additional domains. This SaaS application is considered to be one of the top business-critical applications due to its infrastructural nature, extensibility as a development platform, and access to confidential and proprietary data throughout the organization.
Simple List is an interface widget that pulls data that is stored in tables and uses them in dashboards. The default configuration for Simple List allows the data in the tables to be accessed remotely by unauthenticated users. These tables include sensitive data, including content from IT tickets, internal classified knowledge bases, employee details, and more.
These misconfigurations have actually been in place since the introduction of Access Control Lists in 2015. To date, there were no reported incidents as a result. However, considering the recent publication of the data leakage research, leaving it unresolved can now expose companies more than ever.
It’s important to point out that this issue was not caused by a vulnerability in ServiceNow’s code but by a combination of configurations that exist throughout the platform.
This issue stems from security controls in a ServiceNow Access Control List (ACL) widget called Simple List, which puts records into easily readable tables. These tables organize information from multiple sources and have configurations with a default setting of Public Access.
Because these tables are the core of ServiceNow, the issue isn’t contained within a single setting that can be fixed. Potentially, this needs to be remediated in multiple locations within the application in combination with the usage of the UI widget, and throughout all tenants. To further complicate the issue, changing a single setting could break existing workflows connected to the Simple List tables, causing severe disruption of existing processes.
On the other hand, leaving these tables and applications exposed could have major security implications now that this issue has received so much attention.
We encourage all ServiceNow customers to review the recent guidance published by ServiceNow in their knowledge base article – General Information | Potential Public List Widget Misconfiguration.
To summarize, exposure assessment and remediation measures shall include:
Organizations that use a SaaS Security Posture Management (SSPM) solution are able to gain visibility into ServiceNow’s configurations and remediate the issue based on the recommendations.

To help organizations secure ServiceNow, Adaptive Shield is offering a free ServiceNow assessment for this issue. After a quick validation of your org, our Security research team will send you a report detailing any exposure your portals may have from this misconfiguration.
Click here to request the complimentary assessment.


Recently, Max Corbridge and Tom Ellson from JUMPSEC's Red Team discovered a vulnerability in Microsoft Teams. This vulnerability allows for the introduction of malware into organizations using Microsoft Teams in its default configuration. In this blog post, we will delve into the details of this vulnerability and explore its potential impact.
In Microsoft Teams' default configuration, external tenants can reach out to staff members within an organization using Teams. Despite the presence of a banner indicating that the message is from an external tenant, a considerable number of staff members are prone to clicking on such messages. Exploiting this behavior, threat actors can bypass client-side security controls and send files containing malware to target organizations.
While messaging staff members from another organization, users are prohibited from sending files. However, researchers have discovered a method to circumvent this control, enabling seamless delivery of malware directly into a target's inbox. Leveraging an insecure direct object reference (IDOR) vulnerability, threat actors manipulate the recipient ID on the request and send malicious payloads. These files appear as innocuous attachments in the target's Teams inbox, disguising their true nature.
This vulnerability poses a significant risk as it bypasses most modern anti-phishing security controls. Furthermore, the payload is delivered through a trusted SharePoint domain, eliminating the suspicion associated with clicking on links in emails.
This vulnerability affects all organizations using Microsoft Teams in its default configuration. Although it has the potential to bypass traditional payload delivery security controls, there are measures that organizations can take to mitigate the risk. These are the same measures that can also help prevent the GIFShell vulnerability.
Assess whether your organization truly requires external tenants to message your staff. If not, tighten the security controls and disable external access in the Microsoft Teams Admin Center by setting the "Choose which external domains your users have access to" configuration to "Block all external domains". If communication with external tenants is necessary, consider in the above configuration allowing communication only with specific domains that your organization regularly interacts with. This approach strikes a balance by blocking unknown external sources while maintaining essential communication channels.
Prevent unmanaged external Teams users from starting a conversation with people in the organization by disabling the "External users with Team accounts not managed by an organization can contact users in my organization" configuration.

Raise awareness among staff members about the possibility of social engineering campaigns using productivity apps like Microsoft Teams. It is crucial to recognize that email is not the sole avenue for social engineering attack.
Enable Automated Protection with an SSPM
If you are already an SSPM solution, these Microsoft Teams configurations should be part of the platform’s security checks. The following actions can help the security team gain a better understanding of an organization's SaaS attack surface and its security posture.
Thanks to the efforts of Max Corbridge and Tom Ellson, a critical vulnerability in Microsoft Teams has been identified. With the widespread adoption of Microsoft Teams and its vast user base, this vulnerability poses a significant concern for organizations. By understanding the risks and implementing appropriate mitigation measures such as simple configurations, organizations can better protect themselves against this vulnerability and stay one step ahead of threat actors.
.png)
.png)
According to a recent report by cybersecurity expert Brian Krebs, several organizations, including banks and healthcare providers, are leaking sensitive information due to a misconfiguration in Salesforce Communities. Communities, which allows Salesforce users to easily create websites, has two means of entry. Some sites require user login, while others allow guests to view content without any authentication.
The misconfiguration reported on by Krebs gives unauthenticated guest users access to records, some of which contain sensitive information like social security numbers and bank account information. Krebs notes that this is not an isolated incident and that configuration-based security risks are a common problem across many SaaS products on the market today. This post will cover the leak as well as best practices to secure your Salesforce Community.
Salesforce Community Sites are designed to provide a platform for users to engage with one another, share information, and collaborate. The custom-branded sites run on Salesforce’s Lightning framework and are integrated with the Salesforce instance. Guest user access is a feature that allows unauthenticated users to view designated content and resources without requiring a login.
However, Salesforce administrators sometimes erroneously give guest users access to internal resources, which can lead to unauthorized users accessing private information and data leaks. In the Krebs report, security researcher Charan Akiri said he identified hundreds of organizations with misconfigured Salesforce Community sites.
Salesforce states that the data exposures are not the result of vulnerabilities in the Salesforce platform but are due to customers' misconfigured access control permissions. In September 2022, Salesforce issued an advisory in which it recommended that users utilize its Guest User Access Report package to assist in reviewing access control permissions for unauthenticated users. Krebs also cited a written statement from Salesforce, in which the company said it continues to release “robust tools and guidance for our customer.”
One of the organizations with multiple misconfigured Salesforce Community sites is a US State. The team had hastily created multiple Community sites in response to the COVID-19 pandemic which were not subject to the State’s normal security review process. The State’s Chief Information Security Officer said his “team is frustrated by the permissive nature of the platform.”
He is not the only one; reading the responses to the Krebs article on the Salesforce subreddit (r/salesforce) is alarming. One Salesforce admin admitted on Reddit that “I accidentally did this at my last company when I was messing around with our Knowledge sites.” Another one acknowledged that this “mistake is easily made.”
As this leak is not due to a vulnerability in Salesforce's app, it is important to note which configurations can lead to such a leak, and overall how customers can and should continuously control (assess, monitor, and remediate) the app’s configurations.
Additionally, the issue with misconfigurations providing pathways to critical data is not unique to Salesforce. SaaS products have become increasingly complex over time, making it challenging for administrators and security teams to ensure that the correct security and access configurations are in place. Moreover, SaaS providers often introduce new features into their products, which can expose customers to new risks that negatively impact their organization's security posture.
An additional challenge is the gap of knowledge between app owners and security experts, and the complex responsibility assignment matrix for SaaS security.
Salesforce admins can take the following steps to prevent their sensitive data from being exposed to guests in Communities:
If you are already an Adaptive Shield customer, these configurations have been monitored by our platform for the past couple of years, as Adaptive Shield’s cyber experts have a deep understanding of this Salesforce domain. The following actions can help the security team gain a better understanding of an organization's SaaS attack surface and its security posture.


Nissan North America is informing customers of a data breach that occurred at a third-party service provider. The security incident was reported to the Office of the Maine Attorney General on January 16, 2023, and it was disclosed that almost 18,000 customers were affected by the breach. According to the notification, Nissan received notice of the data breach from one of its software development vendors on June 2022. The vendor had received customer data from Nissan to use in developing and testing software solutions, which was inadvertently exposed due to a poorly configured cloud-based public repository.
Nissan took immediate action to secure the exposed repository and launched an internal investigation. It was determined that an unauthorized person had likely accessed the data. The exposed data includes full names, dates of birth, and Nissan account numbers, but does not include credit card details or Social Security numbers. Nissan says that to this date, there has been no evidence that any of this information has been misused.
There are two key lessons to learn from the incident. The first is the recurring lesson about the importance of securing repository access (such as GitHub, GitLab, Bitbucket, and more). Just last week we published a blog post covering the breach of Slack’s GitHub repositories. In the case of the 3rd party vendor Nissan used, the issue is even simpler than the previous ones –- organizations must make sure that private repositories used for code development and testing stay private, and only open repositories (such as sharing back to the community) should be public. Security teams must constantly monitor and evaluate which repositories are open, and who should have access to other repositories. Any changes to the visibility of a repository should be alerted, logged, and evaluated by the security team.

Figure 1. Changing repository settings in Github
The second is the use of real customer data for development and testing purposes. This should be discouraged, and instead, use synthetic data mimicking the real data. In my previous blog post, Not All Sandboxes Are for Children: How to Secure Your SaaS Sandbox this was discussed in depth. The main problem is that many times, for no good reason, test environments are not considered as important to secure and keep good configuration hygiene compared to a production environment. But time and time again this is shown to be an Achilles' heel. Many times real data is used in such environments and combined with low security and minimum safeguards, leads to data leakage.
The impact of such a breach is considerable. Not only was sensitive customer data stolen, but Nissan needed to publicly send out notifications, report it to the Office of the Maine Attorney General, and also gave all the affected customers a one-year membership of identity protection services through Experian for free.
You can protect your organization by securing your repository and making sure all repositories that need to be private stay private. Additionally, treat test environments just like production environments from a security standpoint. These are measures that, if done correctly, and with the aid of automatic tools, can keep your organization and customer data secure.


Earlier today, a story broke that GitHub repositories of Slack were breached over the holiday weekend. Slack detected the breach after noticing suspicious activity, and in their investigation found that stolen Slack employee tokens were the source of the breach.
As a result of the attack, private Slack code repositories were downloaded, but no customer data was exposed.
While Slack is in the news today, they are definitely not the first, and will not be the last. Among the numerous breaches thus far, the Dropbox breach consisting of 130 Dropbox GitHub repositories is noteworthy. This was done using credentials that were stolen in a phishing attack, the current method of choice for bad actors. This also was discovered by noticing suspicious activity. GitHub itself has fallen victim to a breach that resulted in stolen repositories using stolen OAuth user tokens issued to two third-party OAuth integrators – Heroku and Travis-CI.
These breaches show how important it is to secure repositories. This is even more true in the modern cloud-based world where repositories are hosted within SaaS platforms for managing Git – such as GitHub, GitLab, Bitbucket, and others. These repositories are the keys to the kingdom. Sometimes repositories include databases of customers, patients, assets, and other sensitive data. This type of breach is a disaster for any company.
Once accessed, the attacker has an intimate understanding of how the product was built and can use that information to compromise the product in follow-up attacks.
To protect against such attacks, organizations should follow these security measures:

As seen in the incidents mentioned above, monitoring is key. Make sure to enable audit logs and consume them to gain visibility to user actions, in addition to having tools, like a SaaS Security Posture Management solution (SSPM), for threat detection.
These are just some of the many methods, tools, and configurations that should be used to secure access to a repository. In addition, employees should be trained to detect phishing and keep their credentials safe and secure.
A breach of a repository in a Git SaaS is not a force majeure. With proper security tools and training the risk can be reduced drastically.


During the last week of March, three major tech companies - Microsoft, Okta, and HubSpot - reported significant data breaches. DEV-0537, also known as LAPSUS$, performed the first two. This highly sophisticated group utilizes state of the art attack vectors to great success. Meanwhile, the group behind the HubSpot breach was not disclosed. This blog will review the three breaches based on publicly disclosed information and suggest best practices to minimize the risk of such attacks succeeding against your organization.
On March 21, 2022, HubSpot reported the breach which happened on March 18. Malicious actors compromised a HubSpot employee account that the employee used for customer support. This allowed malicious actors the ability to access and export contact data using the employee’s access to several HubSpot accounts.
With little information regarding this breach, defending against an attack is challenging, but a key configuration within HubSpot can help. This is the “HubSpot Employee Access” control (shown in the figure below) in HubSpot’s account setting. Customers should disable this setting at all times, unless they require specific assistance, and then immediately turn it off after completing the service call.

A similar setting appears in other SaaS applications and should be disabled there as well. Employee access is typically recorded in Audit Logs, which should be reviewed regularly.
Okta subcontracts some of its customer support to the Sitel Group. On January 21, an Okta security team member received an alert that a new MFA factor was added to a Sitel Group employee account from a new location.
An investigation revealed that a Sitel support engineer’s computer was compromised using a remote desktop protocol. This known vulnerability is normally disabled except when specifically needed — which helped Okta investigators narrow the timeframe for the attack to a five-day window between Jan. 16-21, 2022.
Due to the limited access support engineers have to their system, the impact on Okta customers was minimal. Support engineers don’t have access to create or delete users or download customer databases. Their access to customer data is quite limited as well.
On March 22, DEV-0537, which is more commonly known as LAPSUS$, shared screenshots online. In response, Okta released a statement saying, “there are no corrective actions our customers need to take.” The following day the company shared details of its investigation, which included a detailed response timeline.
While this breach was limited in the damage it caused, it offers three important security lessons.
See Cloudflare's investigation of the January 2022 Okta compromise for a good example of a response to such a breach.
On March 22, Microsoft Security shared information relating to an attack it suffered at the hands of DEV-0537. Microsoft had a single account compromised, which resulted in source code being stolen and published.
Microsoft assured its users that the LAPSUS$ attack didn’t compromise any of their information, and further stated that there was no risk to any of their products due to the stolen code.
Microsoft did not specifically share how the breach was carried out, although it did alert readers that LAPSUS$ actively recruits employees at telecoms, major software developers, call centers, and other industries to share credentials.
The company also offered these suggestions for securing platforms against these attacks.
For a full list of Microsoft’s recommendations, see this note.
Securing SaaS platforms is a major challenge, and as seen this week, even global enterprises need to stay on top of their security. Malicious actors continue to evolve and improve their attack methods, which forces organizations to constantly be on the lookout and prioritize their SaaS security.
Strong passwords and SSO solutions are no longer enough by themselves. Companies need advanced security measures, such as strong MFA, IP allow lists, and blocking unnecessary support engineer access. An automated solution like SaaS Security Posture Management (SSPM) can help security teams stay on top of these issues.
The importance of device security in SaaS is another takeaway from these attacks. Even a fully secured SaaS platform can be compromised when a privileged user accesses a SaaS app from a compromised device. Leverage a security solution that combines device security posture with SaaS security posture for full, end-to-end protection.
The challenge of securing SaaS solutions is complex and beyond burdensome to complete manually. SSPM solutions, like Adaptive Shield, can provide automated SaaS security posture management, with configuration control, endpoint posture management, and 3rd party application control.