Identity Threat Detection & Response
Detect & Respond to SaaS Threats

The Ultimate SaaS Security Posture Management Checklist: 2024 Edition
GET THE CHECKLIST
The Annual SaaS Security Survey Report: 2025 CISO Plans and Priorities
Learn more
The Annual SaaS Security Survey Report: 2025 CISO Plans and Priorities
GET THE REPORT CrowdStrike
CrowdStrike
Adaptive Shield’s SSPM & ITDR Platform Features and Capabilities
Download


The Ultimate SaaS Security Posture Management Checklist: 2024 Edition
GET THE CHECKLIST
The Annual SaaS Security Survey Report: 2025 CISO Plans and Priorities
Learn more
The Annual SaaS Security Survey Report: 2025 CISO Plans and Priorities
GET THE REPORT CrowdStrike
CrowdStrike
Adaptive Shield’s SSPM & ITDR Platform Features and Capabilities
Download
Detect & Respond to SaaS Threats
Identity Threat Detection & Response (ITDR) is a set of security measures designed to detect and respond to identity-centric threats. Clear Indicators of Compromise (IoCs) and Unusual User & Entity Behavior Analytics (UEBA) provide forensic signs of a potential breach, such as malware, data breaches and other suspicious events. With the broadest and deepest app coverage in the market, Adaptive Shield’s engines cross-reference and analyze in-context suspicious events from multiple sources, enabling the accurate detection of sophisticated and subtle threats.
Threat prevention through continuous hygiene is key in order to secure the SaaS ecosystem, while ITDR provides an additional, second layer of protection for SaaS applications.
A breach can originate from poor hygiene, such as inadequate user governance, misconfigurations, 3rd party connected apps, or user devices with low hygiene. As a means of prevention, SSPM should operate as the security layer in the identity fabric to establish robust user governance.
As an additional layer of defense, ensure threat detection mechanisms are in place to identify IOCs, such as suspicious activities, malicious applications, or changes to security and sensitive configurations.
Once a threat is detected, the security team can immediately respond and initiate an automatic mitigation action based on forensic data provided by Adaptive Shield or connect to any SIEM & SOAR system to streamline the response process.

The Ultimate SaaS Security Checklist 2025 Edition
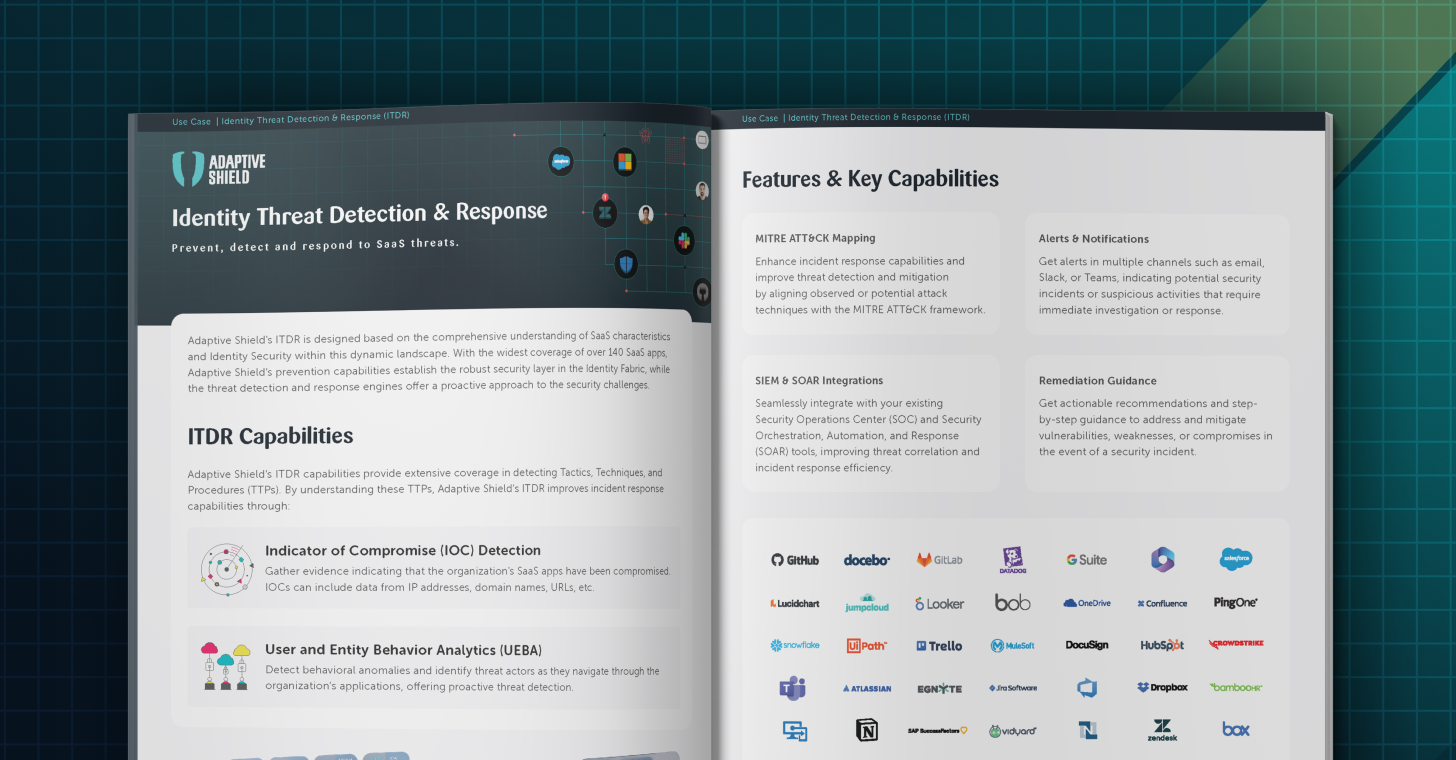
Identity Threat Detection & Response: Solution Brief

Identity Threat Detection and Response (ITDR) – Rips in Your Identity Fabric