As corporate SaaS stacks have grown in magnitude and complexity, so has the need to secure them from evolving risks and threats. Today, organizations need a robust SaaS Security program with visibility over the entire SaaS ecosystem and the different domains vital in securing it. This article will serve as a beginner’s guide into the complex world of SaaS security to help readers understand the range of use cases required in a comprehensive SaaS security solution.
What Is "The SaaS Security Ecosystem"?
The SaaS security ecosystem addresses the complete security life cycle for SaaS apps, from endpoint security, Identity and Access Management (IAM), and threat monitoring and response capabilities to addressing overall SaaS ecosystem risks. Securing the SaaS ecosystem requires an approach that is both broad in terms of covering every application and deep in terms of security checks. As businesses become increasingly SaaS dependent, this holistic SaaS ecosystem security program becomes more vital, helping protect an organization by eliminating risks and mitigating threats using the latest cybersecurity methodologies. While the SaaS security ecosystem is a large and diverse world, a good place to start is understanding the use cases.
What Are the Crucial Use Cases in SaaS Security?
To protect one’s organization, it’s important to understand the crucial use cases and how they help secure entry points and handle the challenges within the SaaS ecosystem.
1. Misconfiguration Management
SaaS apps have the security tools in place to ensure full data security – yet only takes one changed setting to have an organization’s data exposed. In fact, misconfigured SaaS settings are one of the leading causes of data breaches, stolen data, and SaaS ransomware. Enterprises have thousands of security controls in their SaaS stack and if this weren’t enough of a challenge, security teams often lack the visibility into these controls as app owners frequently sit outside the security team’s domain.
Misconfiguration management enables organizations to reduce threats in their SaaS apps by identifying drifts in security controls and alerting the security team. A comprehensive solution will even offer contextual recommendations or step-by-step remediation guides to help restore a configuration to its secure setting.
2. Identity & Access Governance
SaaS security doesn’t stop at the app itself. Users play a crucial role in creating a secure SaaS ecosystem. Identity & access governance help security teams manage these users and their access by providing security teams with consolidated visibility of user accounts, permissions, and privileged activities. This allows security teams to identify privileged users, trim permissions to the right level of access, and thoroughly deprovision users when needed.
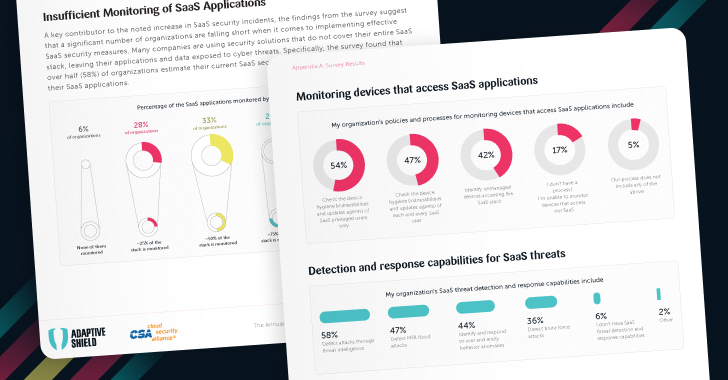
3. Device-to-SaaS Risk Management
User devices play a large role in the SaaS ecosystem. Poor device hygiene poses a major risk, as personal devices are susceptible to data theft, while lost or stolen corporate devices can provide a gateway for criminals to access the network. When individuals with advanced privilege levels use devices that are unsecured, they expand the attack surface with what amounts to an open gateway.
With device-to-SaaS risk management, security teams can identify users with poor device hygiene as well as any unmanaged devices that are accessing the SaaS stack. The right SaaS security solution allows security teams to correlate the user, application, and device, and then filter by privileged users or high-risk devices. Once the security team has a strong understanding of the user and their access level, they can effectively evaluate the level of risk a personal device poses.
4. SaaS-to-SaaS Access Discovery and Control
Today, SaaS apps also integrate with other apps, which results in a magnitude of apps connected to the core SaaS hubs, such as Microsoft 365. This interconnectivity is called SaaS-to-SaaS access but is also referred to as third-party app access. Each of these subsidiary apps requires permissions that grant them access to your core SaaS apps. The sensitivity level of these permissions can vary from low-medium risk to high risk. A recent report found that 39% of apps connected to M365 have ‘high-risk’ permission access, including the ability to read, create, update, and delete data.
A SaaS security solution should include SaaS-to-SaaS access discovery and control to help security teams analyze and baseline all third-party apps connected to the organization’s core SaaS stack. This use case provides visibility into the apps that are connected and the risk levels associated with their granted permissions. A security solution should also be able to detect any malicious apps that have been installed.
5. Identity Threat Detection & Response
ITDR is an identity-centric security category, developed in response to cybercriminals targeting the Identity and Access Management (IAM) infrastructure. Once a user’s identity is compromised, threat actors have the credentials needed to steal an organization’s data. ITDR is composed of three main principles:
- Posture: A breach can originate from poor hygiene such as inadequate user governance, misconfigurations, third-party apps, or user devices with low hygiene. Continuous posture management is crucial to minimize risk.
- Detection: As an additional layer of defense, ensure threat detection mechanisms are in place to identify indications of compromise (IOC), such as suspicious activities, malicious applications, or changes to security and sensitive configurations.
- Response:Once a threat is detected, the security team can immediately respond and initiate a mitigation action based on forensic data provided by Adaptive Shield and connect to any SOAR to streamline the remediation process.
Conclusion
In order to secure their growing SaaS stack, organizations must develop a holistic SaaS security program. The best solution centers on a comprehensive approach to all SaaS apps in the stack, securing identity-based access points as well as endpoint devices that access SaaS applications and 3rd party applications that are connected to the SaaS hubs, while enhancing the organization’s ability to prevent threats.