Reporting
Adaptive Shield’s reporting functionality ensures that stakeholders are always kept up to date on the status of your SaaS security. Reports are fully configurable, allowing users to adapt the design and content based on their reporting needs.
Use pre-made reports or create your own with data from security checks, compliance, users, devices, apps, permissions, data, and domains.
How This Can Help You
Send SaaS Posture Reports to Management
Share SaaS risk level with your CISO, executives, and other stakeholders
Update GRC on SaaS Compliance
Automate daily, weekly, or monthly compliance reports based on over 20 compliance and regulatory standards
Monitor Changes in Key Attack Vectors
Track configuration posture, user permissions, data leakage risk, and other critical factors over time.
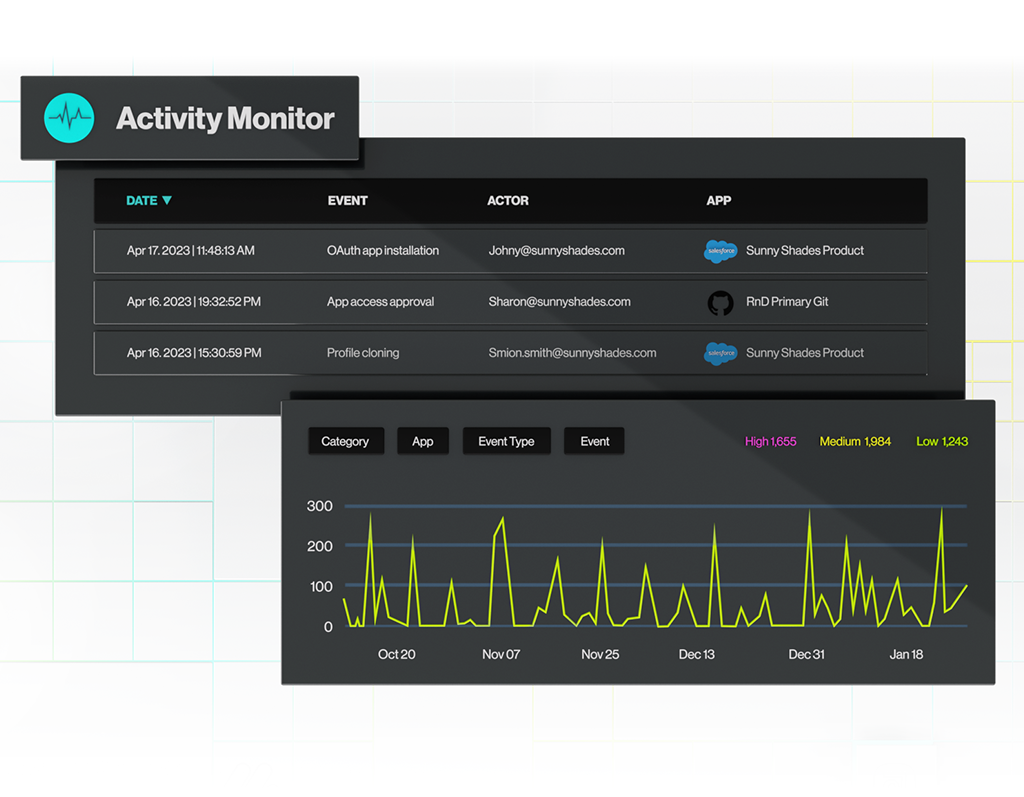
Activity Monitor
Adaptive Shield’s Monitor collects SaaS logs and normalizes the data for every event within your SaaS stack. This enables security teams to visualize a high volume of data through an intuitive UI and detect indications of compromise (IOC) and threats within the context of the application or user. Using filtering tools, security personnel can quickly hone in on suspicious activities and detect insider threats.
Name, description, and location of each event
Categorization of events, including IOC and Threat
Actors and applications involved in each event
Severity level of each threatening event
Actor activity profile
From there, security teams can take a deep dive into the events’ history and further investigate.
How This Can Help You
Protect Against Compromised User Accounts
Identify and manage accounts with suspicious or inadequate activity
Internal Threat
Identify unusual user behavior
Build an Audit Trail
Gather forensics and further investigate the case
Export Normalized Data
Send event data to external BI systems for further analysis