Let’s Get Technical
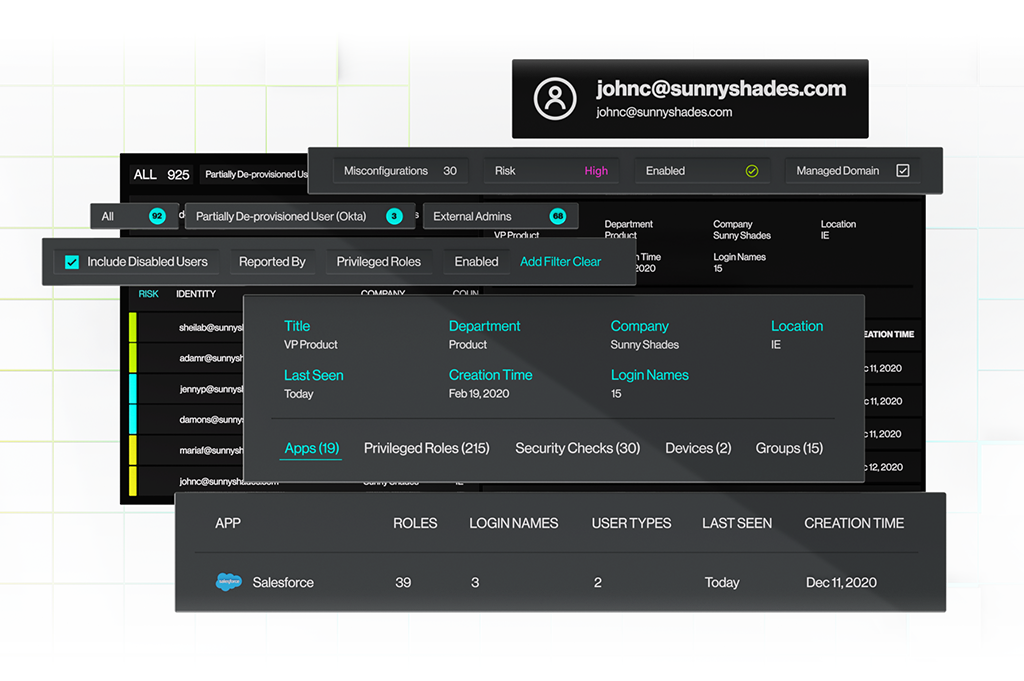
Risk level associated with the user based on role and existing configurations.
Activated/deactivated users.
How This Helps You
Privileged Roles
Identify users with the highest permissions within each application to prioritize misconfiguration management, device management, and third-party app access
Permission Trimming
Ensure each SaaS user has the right level of access needed to ensure business operations while preventing unnecessary access to sensitive data