Managing GenAI Riskswith SSPM
The GenAI revolution risks in SaaS environments

The Ultimate SaaS Security Posture Management Checklist: 2024 Edition
GET THE CHECKLIST
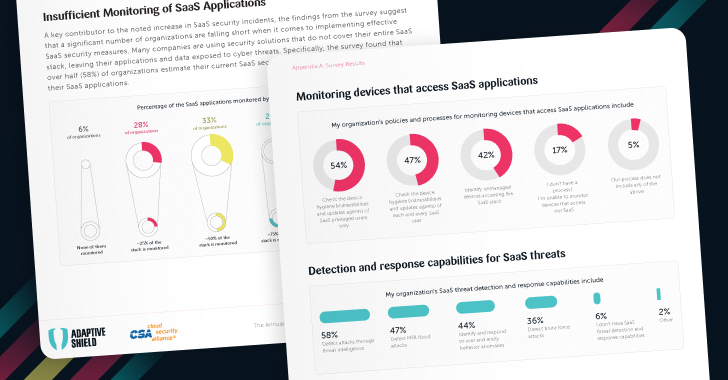
The Annual SaaS Security Survey Report: 2025 CISO Plans and Priorities
Learn more
The SSPM Justification Kit
GET THE KIT CrowdStrike
CrowdStrike
Adaptive Shield’s SSPM & ITDR Platform Features and Capabilities
Download


The Ultimate SaaS Security Posture Management Checklist: 2024 Edition
GET THE CHECKLIST
The Annual SaaS Security Survey Report: 2025 CISO Plans and Priorities
Learn more
The SSPM Justification Kit
GET THE KIT CrowdStrike
CrowdStrike
Adaptive Shield’s SSPM & ITDR Platform Features and Capabilities
Download
The GenAI revolution risks in SaaS environments
The workforce is rapidly adopting SaaS applications with GenAI to increase efficiency, including AI apps such as GitHub Copilot, Salesforce Einstein, and Microsoft 365 Copilot. While increasing automation and improving productivity, the use of GenAI introduces new risks including data leakage, attack surface expansion, new areas of exploitation, and privacy concerns, as well as new challenges to meet compliance and government requirements.
Security posture management for AI SaaS applications or AI configurations involves continuous monitoring and risk management. An SSPM solution alerts users to any security drifts and provides step-by-step remediation, enabling the app owner and security team to collaborate and resolve issues. A crucial part of this process includes detecting AI shadow apps adopted by users and discovering interconnected GenAI applications while calculating risk based on their requested scopes.
Delve into the security posture of any AI application within the SaaS stack and prioritize addressing application configuration drifts.
Control AI-related security settings within SaaS applications to prevent data leakage or any exposure. This includes identifying excessive user access and determining which users possess permissions to manage GenAI features.
Identify GenAI Shadow apps, including suspected malicious applications, to automatically revoke access based on their risk level.
Oversee interconnected GenAI applications and the level of risk they pose to the SaaS hubs, including reviewing permission scopes.
AI potentially accesses sensitive data in a more sophisticated and comprehensive manner than traditional methods. The ability of AI to analyze and correlate information from multiple sources could lead to a more extensive data exposure. With Adaptive Shield you can govern security controls to avoid data leakage.

The Ultimate SaaS Security Checklist 2025 Edition

Adaptive Shield Solution Brief
The Annual SaaS Security Survey Report: Plans and Priorities for 2024