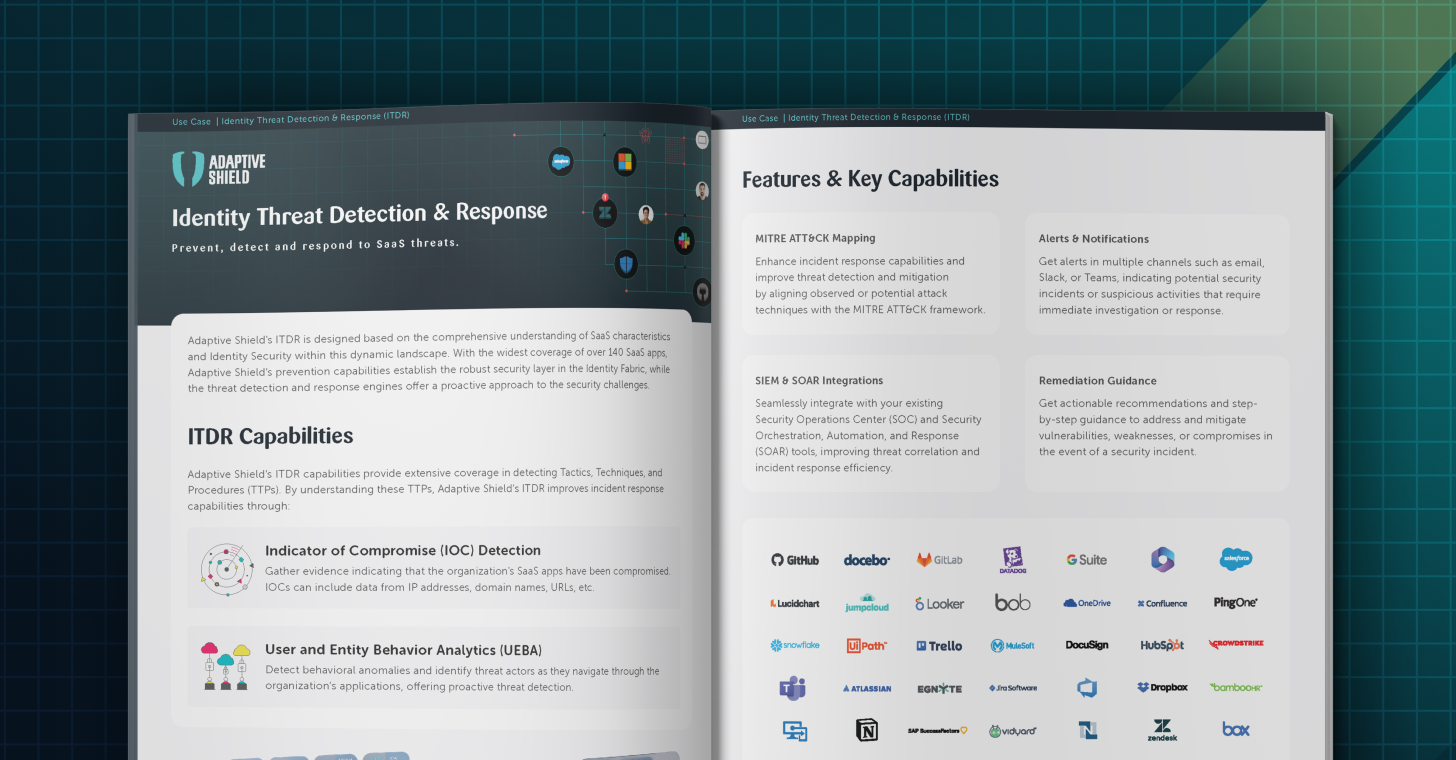
What is Access Control?
Access control in SaaS Security relates to the methods and policies implemented to regulate user access to the SaaS applications and their associated data. It involves managing permissions, roles, and authentication mechanisms to ensure that only authorized individuals and authorized non-human accounts can access the SaaS platform and its resources. Access control in SaaS security often employs techniques such as multi-factor authentication, role-based access control (RBAC), and granular permission settings to mitigate risks associated with unauthorized access, data breaches, and insider threats. By effectively implementing access control measures, organizations can safeguard their sensitive data and maintain compliance with regulatory requirements in the SaaS environment.
What are the different ways organizations control access to their SaaS applications?
Password Policy
Require passwords to meet specific complexity criteria, such as a minimum length, inclusion of capital and lowercase letters, numbers, and special characters. Some organizations mandate regular password changes, although some prefer users maintain strong passwords for long periods of time. Most organizations prevent users from reusing passwords.
Single Sign-On (SSO)
SSO enables users to access multiple SaaS applications with a single set of login credentials, streamlining authentication and improving user experience while maintaining security.
Multi-Factor Authentication (MFA)
Passwords alone are not sufficient to protect against unauthorized access in SaaS applications, as they can be easily guessed, stolen, or cracked through techniques like phishing or brute force. Multi-factor authentication adds an extra layer of security by requiring users to provide multiple forms of identification before gaining access. This can include something they know (password), something they have (smartphone), or something they are (fingerprint or facial recognition).
By implementing MFA, even if an attacker manages to obtain a user’s password, they would still need the second authentication factor, making it significantly harder for unauthorized users to breach the system.
Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC) is a widely adopted access control model in SaaS security. It involves categorizing users into various roles based on their job responsibilities and granting permissions accordingly.
This allows security teams to implement the Principle of Least Privilege (POLP), the concept of granting users and applications only the minimum level of access necessary to perform their required tasks. This approach aims to reduce the potential impact of security breaches or unauthorized activities. RBAC simplifies the process of access management by reducing administrative overhead, ensuring a scalable and manageable approach to security.
For example, in a CRM SaaS application, a sales representative may have access to customer data and the ability to update records, while a customer support agent might only have read-only access to the same data.
Regular User Access Reviews
Conducting regular access reviews is crucial to ensure that users have access only to the resources they need for their current responsibilities. This reduces the risk of dormant accounts or unauthorized access to sensitive data. Organizations need to gain visibility and properly deprovision former employees, dormant accounts, and external users.
Former employees need to be completely deprovisioned. Often organizations assume this happens automatically when an employee is removed from the company’s Identity Provider (IdP), but that’s not always the case. Similarly, external user accounts may stay active even after projects end if user access isn’t promptly or properly revoked. The organization doesn’t know who has access to their sensitive data unless they conduct a review and decide whether to close the user account.
Audit Logs & Monitoring
Comprehensive logging and monitoring mechanisms should be in place to track user activities within the SaaS application. Audit logs can help in identifying suspicious behavior, potential security breaches, or policy violations. Monitoring these logs in real-time allows for timely response to security incidents.
Should External Users Have Access to Your SaaS Apps?
Most organizations need to provide SaaS access to external users to facilitate collaboration with agencies or contractors. However, organizations should take precautions when providing external access. Here are some best practices for collaborating with external users.
Limit Privileges
External users should not be granted admin rights. Their access should be limited based on need.
Require User Authentication
Don’t allow external users to access documents with a link. Require some type of authentication
Do Not Allow Shared Passwords
Maintain control by blocking the sharing of passwords among external users
Limit Application Invitations
When possible, add an expiration date to invitations so that they can’t be used to gain access after a project is over
Remove Access When the Project Ends
Is there a difference between human and non-human accounts in relation to Access Control?
SaaS applications are accessed by human and non-human accounts. Human accounts typically gain access through usernames and passwords, MFA, and SSO. Non-human accounts are typically authorized at the time they are created, and are never asked for a secondary method of authentication.
Non-human accounts are often overlooked as organizations control access to their applications. However, their unfettered access makes them a target of threat actors. Organizations should monitor non-human accounts through their user inventory, and ensure that they are not over-permissioned. Non-human account configurations must be monitored to ensure controls are in place to limit privileges granted to these accounts.
Conclusion
As the adoption of SaaS solutions continues to rise, ensuring robust access control in SaaS security is of paramount importance. Organizations must implement a well-structured RBAC, combining role-based permissions, multi-factor authentication, regular user access reviews, and comprehensive monitoring.
By taking a proactive approach to access control, businesses can fortify their SaaS applications against unauthorized access and potential cyber threats. Moreover, a strong access control strategy fosters trust among users, customers, and partners, ultimately leading to a successful and secure SaaS environment.