- Solution
- By Category
- What is SSPM?
- Top Ten Integrations
Google Workspace

The Ultimate SaaS Security Posture Management Checklist: 2024 Edition
GET THE CHECKLIST - Platform
- Platform Features
- Main Features
- Prevention Features
- Posture By App
- Detection & Response Features
- Remediation
- Integrations

The Annual SaaS Security Survey Report: 2025 CISO Plans and Priorities
Learn more - Resources
- Library
- All Resources
- Blogs
- All Blogs

The Annual SaaS Security Survey Report: 2025 CISO Plans and Priorities
GET THE REPORT - Partners
- Tech Partners
 CrowdStrike
CrowdStrike- Business Partners
- Partner Program

Adaptive Shield’s SSPM & ITDR Platform Features and Capabilities
Download - Company


- Solution
- By Category
- What is SSPM?
- Top Ten Integrations
Google Workspace

The Ultimate SaaS Security Posture Management Checklist: 2024 Edition
GET THE CHECKLIST - Platform
- Platform Features
- Main Features
- Prevention Features
- Posture By App
- Detection & Response Features
- Remediation
- Integrations

The Annual SaaS Security Survey Report: 2025 CISO Plans and Priorities
Learn more - Resources
- Library
- All Resources
- Blogs
- All Blogs

The Annual SaaS Security Survey Report: 2025 CISO Plans and Priorities
GET THE REPORT - Partners
- Tech Partners
 CrowdStrike
CrowdStrike- Business Partners
- Partner Program

Adaptive Shield’s SSPM & ITDR Platform Features and Capabilities
Download - Company
- All topics
- Analyst & Research
- Breach Debrief
- Company News
- Compliance
- Industries
- Product Updates
- SaaS Security
- Threat Detection
- Use Cases

A New Paradigm for Business Unit – Security Team Relations
Tension has long stood at the heart of the business team-security relationship. Business units want to meet corporate targets and choose the most effective software to get the job done. Security teams want to ensure data is secure and try to limit risk. When software was all on-prem, the security team was in command; they […]

Adaptive Shield Partners with Deloitte to Deliver Holistic, Comprehensive SaaS Security for Global Organizations
Implementing SaaS Security with a Powerful Platform and Top-Tier Managed Security Services Adaptive Shield and Deloitte are partnering to help organizations establish a robust SaaS security posture to prevent cybersecurity attacks and data breaches expanding with the adoption of cloud-based services. Organizations are storing an extensive volume of data and assets in SaaS applications such […]

A Guide to Lockdown of Salesforce Links
Collaboration and cooperation are among the key benefits Salesforce offers its customers. The application’s sharing tools are typical of any cloud-based environment. However, ease of sharing is a two-sided coin, and there is a potential risk associated with publicly accessible links. Leaked documents can result in severe consequences, such as competitors gaining access to sensitive […]

Breach Debrief Series: Twilio’s Authy Breach is a MFA Wakeup Call
Inside the Hack Earlier this week, Twilio issued a security alert informing customers that hackers had exploited a security lapse in the Authy API to verify Authy MFA phone numbers. Hackers were able to check if a phone number was registered with Authy by feeding the number into an unauthenticated API endpoint. Using this data, […]

Securing Supply Chains After Baltimore
In March, a container ship leaving the Helen Delich Bentley Port of Baltimore struck a support piling holding up the Francis Scott Key Bridge, knocking the bridge into the water and killing six workers who were aboard the bridge. With the port closed for an unknown duration and traffic to the port limited due to […]

A WIN for Cloud Security with Adaptive Shield and Wiz
It’s easy to confuse CSPM and SSPM (Cloud Security Posture Management and SaaS Security Posture Management). They both secure assets on the cloud, automatically identify misconfigurations, and detect identity-based threats. The difference between the two lies in the areas that they protect. SSPMs secure SaaS applications, while CSPMs secure cloud services, such as AWS or […]

The NCSC’s Take on SaaS
Since 2016, the National Cyber Security Centre (NCSC) has been tasked with making the United Kingdom the safest place to live and work online. The organization offers practical guidance, incident response services, aids in recovery, and distills lessons learned from cyber incidents into valuable guidance for the future. The Cyber Security Breaches Survey is used […]

Breach Debrief Series: Snowflake MFA Meltdown Creates Data Leak Blizzard
On May 27, a threat actor group called ShinyHunters announced that it was selling 560 million records stolen in a data breach. The records include names, email addresses, physical addresses, and partial credit card numbers. This personally identifiable information (PII) can be used to conduct sophisticated phishing attacks, which could lead to future leaks. Experts […]

Cloud Security Alliance Survey Finds 70% of Organizations Have Established Dedicated SaaS Security Teams
Seventy percent of organizations have prioritized investment in SaaS security, establishing dedicated SaaS security teams, despite economic uncertainty and workforce reductions. This was a key finding in the fourth Annual SaaS Security Survey Report: 2025 CISO Plans and Priorities released today by the Cloud Security Alliance (CSA), the world’s leading organization dedicated to defining standards, […]

Adaptive Shield Wins 2024 Fortress Cybersecurity Award
SSPM platform recognized for its innovation in Zero Trust category Adaptive Shield has been recognized for its exceptional SaaS Security Posture Management (SSPM) platform in the prestigious 2024 Fortress Cybersecurity Awards, presented by the Business Intelligence Group. The SaaS security leader was named a winner in the Zero Trust category. “In today’s digital age, cybersecurity […]

The New SaaS Security Ceiling – Capabilities You Need In a SaaS Security Platform
There was a time, not long ago, when SaaS security meant managing application configurations. Cutting-edge solutions might have included some type of third-party connected app monitoring tool, or user governance. In today’s SaaS security ecosystem, those capabilities are table stakes. Most security teams have recognized that they cannot consider their SaaS stack secure without 24/7 […]

SaaS vs. IaaS: Why Does IaaS Get All the Security Attention?
In many ways, IaaS and SaaS are very different. Infrastructure-as-a-Service (IaaS) is a place where developers use virtualized resources to compute, network, and store data. Software-as-a-service is a piece of software that is hosted on the cloud. Despite their apparent differences, IaaS and SaaS each contain critical corporate information that must be secured. Securing IaaS […]
Managing GenAI Risks with SSPM
GenAI risks explained and how Adaptive Shield’s new GenAI risk management capabilities within its SSPM platform enable security teams to manage and control them What is SaaS Security? SaaS vendors invest heavily in security controls, providing organizations with the necessary tools to secure their SaaS environments. This investment, however, often leads to confusion regarding the […]
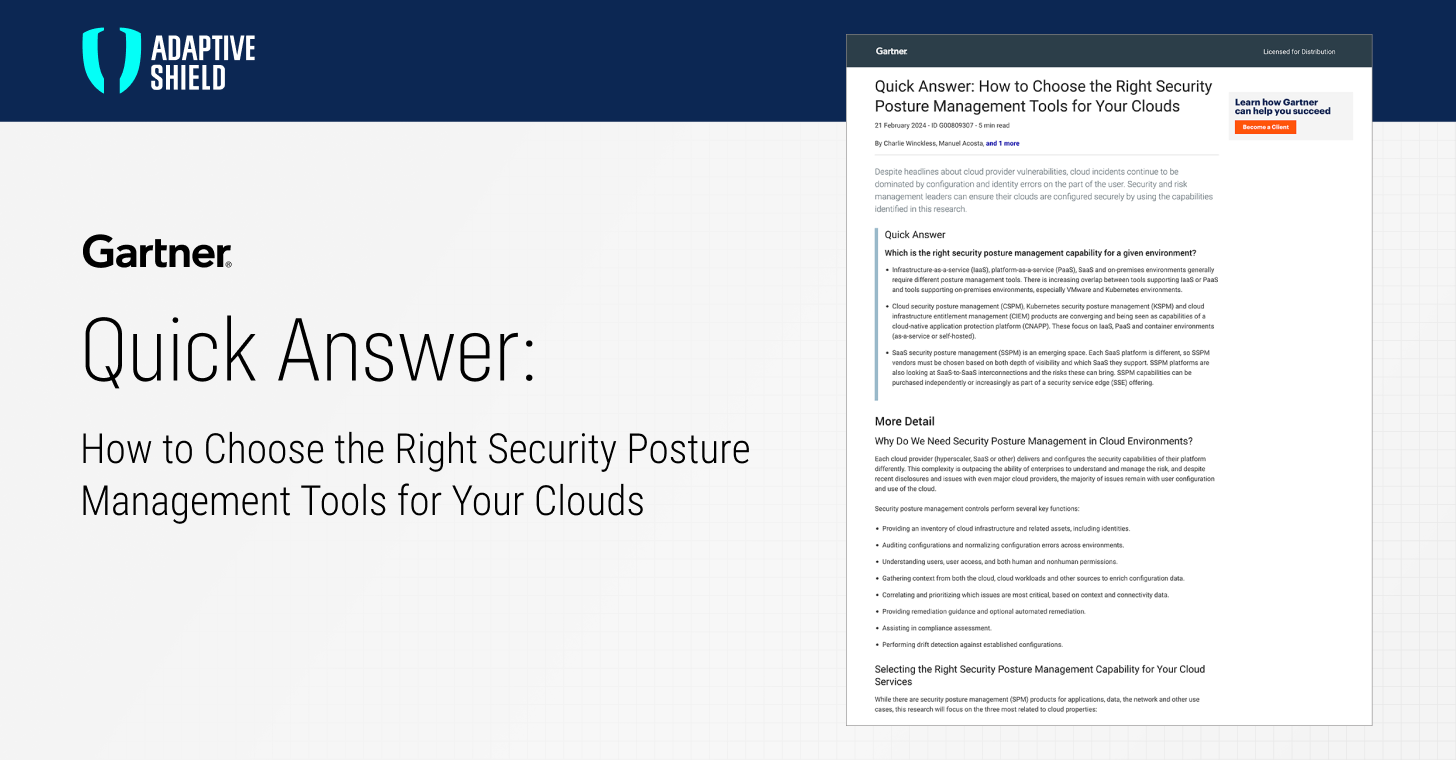
Choosing the Right Security Posture Management for Your Clouds
The rapid uptake of cloud services is presenting a challenge for organizations to keep their ecosystems safe from security breaches. To provide guidance, Gartner® recently published a Quick Answer report for security and risk management leaders on security posture management tools for cloud environments. As “cloud incidents continue to be dominated by configuration and identity […]
Webinar Spotlight: Identity Security for Human and Non-Human Identities
Identities in SaaS applications can be either human, associated with individuals, or non-human, such as service accounts, API keys, and 3rd party app OAuth authorizations. Any unsecured identity in a SaaS app can create an opening for cybercriminals to compromise, leading to data breaches, compliance violations, and financial losses. In a webinar hosted by The […]
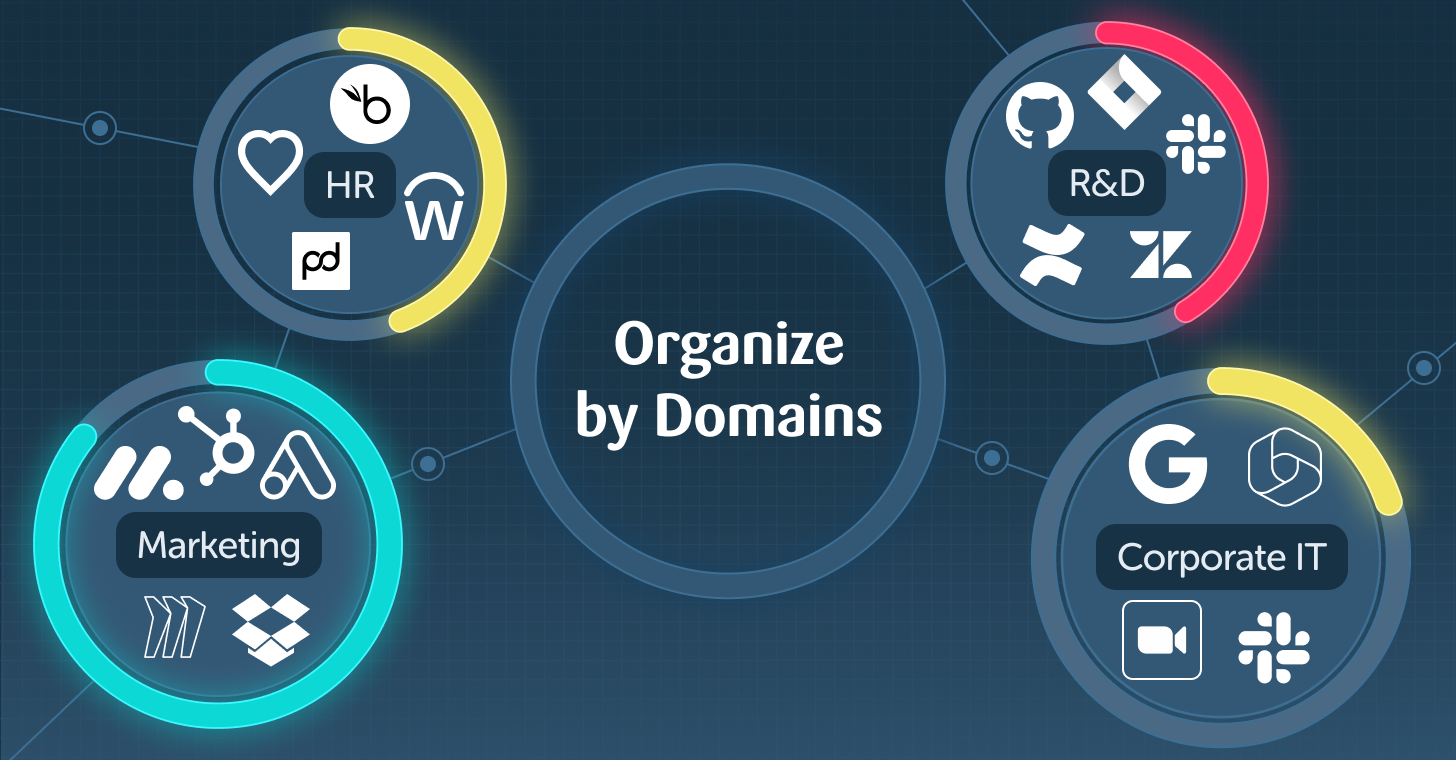
Measuring SaaS Security by Business Unit, Subsidiary or Team
Adaptive Shield’s SaaS Security Posture Management (SSPM) platform has transformed the way organizations secure and monitor their applications. In our latest update, we add a new dimension to improve accountability and reporting – the ability to measure SaaS Security posture by business unit, subsidiary, team, or any other bucket of choice SaaS applications are used […]

Detangling a Confusing Threat Detection for SaaS Landscape
Detection and response sit at the heart of any well-thought-out cybersecurity program. As resilient and strong as perimeter-based defenses are, most security professionals will concede that threats can make their way into the network, device, or application. Detection and response tools come into play after the breach has occurred, but often are able to stop […]

How to Protect Patients and Their Privacy in Your SaaS Apps
The healthcare industry is under a constant barrage of cyberattacks. It has traditionally been one of the most frequently targeted industries, and things haven’t changed in 2023. The U.S. Government’s Office for Civil Rights reported 145 data breaches in the United States during the first quarter of this year. That follows 707 incidents a year […]

Adaptive Shield Named to Cyber 66 List
We’re excited to announce that Adaptive Shield has made its debut on the Cyber 66, the Citizens JMP annual list of the hottest privately held cybersecurity companies. The annual survey highlights the 66 most well-positioned companies currently influencing the cybersecurity landscape. In compiling the 2024 list, the researchers predicted 2024 would continue to be impacted […]

Breach Debrief Series: The Fake Slackbot
Last month, The Verge reported on an amusing story of abusing Slack in a design, technology, science, and science fiction website. Tom McKay of IT Brew successfully hid on Slack after leaving the company in 2022 by assuming the persona of “Slackbot,” remaining undetected by management for months. McKay shared screenshots of his antics on […]

Breach Debrief Series: Bait and Switch at GitHub
GitHub is in the news again, with malicious repositories stealing login credentials and cryptocurrency from developers’ devices. According to researchers at antivirus firm G-Data, these repositories, which are near clones of legitimate repositories, all lead to one of at least 13 GitHub repositories that install the RisePro malware. Users have to go through several steps […]

SaaS Compliance through the NIST Cybersecurity Framework
A major player in the US telecommunications industry, with over 117,000 employees, recently experienced an insider data breach that has impacted nearly half of its workforce. The breach, discovered on December 12, 2023, occurred on September 21, 2023, when an unauthorized employee accessed a file containing sensitive information of over 63,000 employees. The exposed data includes full […]

Adaptive Shield Now Offered Through GuidePoint Security
We’ve partnered with GuidePoint Security, the leading cybersecurity solution provider that helps organizations make better decisions that minimize risk. Through this partnership, GuidePoint Security’s customers have the opportunity to expand their use of SaaS applications while staying secure. As part of the Security Partner Program, Adaptive Shield’s SaaS Security Posture Management (SSPM) and Identity Threat […]
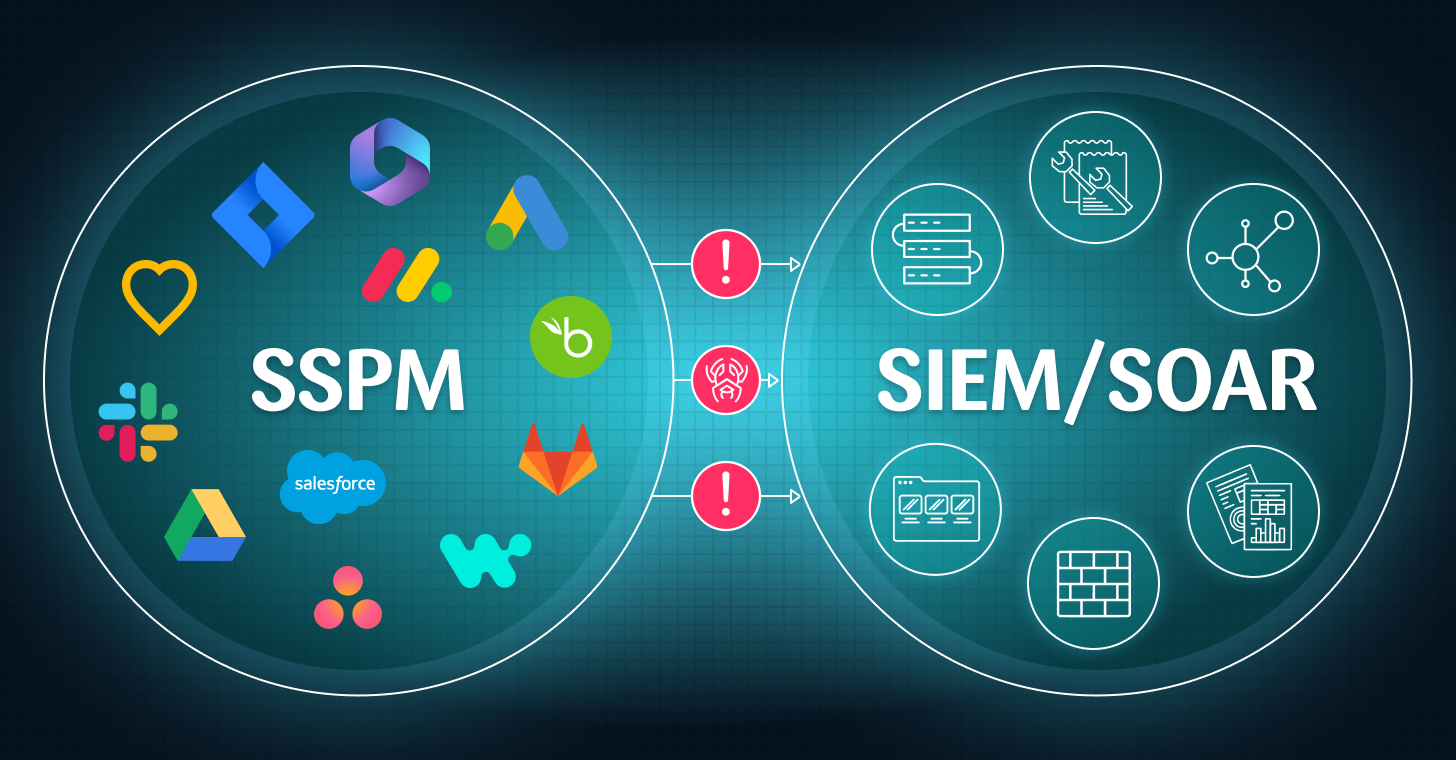
Automating the Remediation Process: Connecting Your SSPM and SIEM/SOAR
Oftentimes, there is a disconnect between identifying SaaS Security weak spots and remediation. Your SaaS Security Posture Management (SSPM) platform may have detected that MFA is turned off for admins, or a threat that requires immediate intervention by either the security team or the app owners. SIEM/ SOAR Security Orchestration, Automation, and Response (SOAR) and […]

Phishing in Azure Cloud: A Targeted Campaign on Executive Accounts
In recent weeks, a concerning wave of cyber attacks has been targeting Microsoft Azure environments, compromising crucial user accounts, including those of senior executives. Proofpoint researchers have identified an ongoing malicious campaign, which utilizes sophisticated techniques like credential phishing and cloud account takeover (ATO). This blog post will summarize and shed light on the nature […]

Salesforce Data Security Challenges in Wake of the Recent Breach
Recent incidents continue to shed light on vulnerabilities that organizations face. A notable case involves a networking products company whose support website inadvertently exposed sensitive customer information, as reported by KrebsOnSecurity. This incident underscores the critical importance of robust security measures in safeguarding customer data. In this blog post, we’ll delve into the details of […]

Insider Data Breach at US Telecom Provider is a Wake-Up Call for HR Information Systems Security
A major player in the US telecommunications industry, with over 117,000 employees, recently experienced an insider data breach that has impacted nearly half of its workforce. The breach, discovered on December 12, 2023, occurred on September 21, 2023, when an unauthorized employee accessed a file containing sensitive information of over 63,000 employees. The exposed data […]

Keeping SaaS Data Under Wraps
A Case Study on How a $10B Global Media Firm Significantly Improved SaaS Security Posture Media firms in the business of image and reputation don’t want to get bad publicity. With regulations requiring companies to report data breaches, information companies handling personal data must take extra cybersecurity caution. Take for example the case study of […]

Frost & Sullivan Recognizes Adaptive Shield with 2023 Global Technology Innovation Leadership Award in SSPM
Adaptive Shield is honored to announce that Frost & Sullivan recently assessed the Software-as-a-Service (SaaS) security posture management (SSPM) industry and based on its findings, recognizes Adaptive Shield with the 2023 Global Technology Innovation Leadership Award. Ying Ting Neoh, research analyst for cybersecurity practice at Frost & Sullivan, said: “With continual enhancements to its SSPM […]

Breach Debrief Series: Addressing Microsoft Teams Phishing Threats
AT&T Cybersecurity recently discovered phishing attacks conducted over Microsoft Teams. During a group chat, threat actors distributed malicious attachments to employees, which led to the installation of DarkGate malware on the victim’s systems. This attack shines a bright light on the everchanging phishing surface as it expands from email to communication applications like Teams. This […]

Breach Debrief Series: Even Microsoft Isn’t Perfect
In a recent cybersecurity event reported by Lawrence Abrams in Bleeping Computer and disclosed by the Microsoft Security Response Center, Microsoft found itself at the center of a cyber-attack. Nobelium, a Russian state-sponsored hacking group also known as APT29 and Midnight Blizzard, breached Microsoft corporate email accounts for over a month. The attack, which was […]

Adaptive Shield Delivered 201% ROI for SaaS Security for $10B Enterprise, According to Total Economic Impact Study
Today, we released that one of our customers achieved a 201% return on investment (ROI) in less than six months from adopting a SaaS Security Posture Management (SSPM) solution, according to results of a Forrester Consulting Total Economic Impact™ (TEI) study. The 2024 Forrester Consulting TEI study is based on data from the customer experience […]
The Fast Evolution of SaaS Security from 2020 to 2024 (Told Through Video)
SaaS Security’s roots are in configuration management. An astounding 35% of all security breaches begin with security settings that were misconfigured. In the past 3 years, the initial access vectors to SaaS data have widened beyond misconfiguration management. “SaaS Security on Tap” is a new video series that takes place in Eliana V’s bar making […]

New Year’s Resolution: 5 Steps to Clean Out Your User Inventory
As we near the end of 2023, it’s an opportune moment to assess your roster of SaaS users. Beyond the potential cost savings from eliminating unnecessary license fees, maintaining a well-organized user inventory plays a crucial role in fortifying the security of your SaaS applications. Here are five compelling security reasons to clean your user […]

Top 7 Trends Shaping SaaS Security in 2024
Over the past few years, SaaS has developed into the backbone of corporate IT. Service businesses, such as medical practices, law firms, and financial services firms, are almost entirely SaaS based. Non-service businesses, including manufacturers and retailers, have about 70% of their software in the cloud. These applications contain a wealth of data, from minimally […]

MongoDB Exposure Could Impact SaaS App Atlas
On Wednesday, December 13, MongoDB detected an exposure in their systems, and customer account metadata and contact information. MongoDB is currently conducting an investigation to determine the extent of the exposure. In an email sent out to customers, MongoDB CISO Lena Smart informed users that at present they were “not aware of any exposure to […]

Analyzing the Forrester Wave™: SaaS Security Posture Management, Q4 2023
The dynamic landscape of cybersecurity is witnessing a paradigm shift, with the SaaS Security Posture Management (SSPM) market emerging as a critical and pivotal player in safeguarding organizations against evolving cloud-based threats. As a clear must-have solution, Forrester has now brought to market their SSPM Wave, laying out their assertions and designating the top providers […]

Your Guide to Offboard Users from Your SaaS Apps
Former employees retaining SaaS app access happens far more often than businesses care to admit. Nearly a third of all employees retain some degree of access to the SaaS stack. When employees move on, voluntarily or otherwise, it’s in the organization’s best interests to remove all access to corporate assets. Much of this process is […]
How to Handle Retail SaaS Security on Cyber Monday
If forecasters are right, over the course of today, consumers will spend $13.7 billion. Just about every click, sale, and engagement will be captured by a CRM, Marketing or Customer Service platform and more operational apps. Inventory applications will trigger automated re-orders; communication tools will send automated email and text messages confirming sales and sharing […]

Sumo Logic Discloses Cloud Exposure
Earlier this month, threat actors leveraged compromised credentials to access Sumo Logic’s Amazon Web Services account. Sumo Logic immediately took down the infrastructure exposed by the incident, and conducted a rotation of credentials to prevent further compromises. Sumo Logic is a cloud-based log management and analytics platform that empowers organizations to gain actionable insights from […]
Top 5 Marketing Tech SaaS Security Challenges
Effective marketing operations today are driven by the use of Software-as-a-Service (SaaS) applications. Marketing apps such as Salesforce, Hubspot, Outreach, Asana, Monday, and Box empower marketing teams, agencies, freelancers, and subject matter experts to collaborate seamlessly on campaigns and marketing initiatives. These apps serve as the digital command centers for marketing professionals. They house essential […]

SaaS Security After the M&A
Mergers and acquisitions (M&A) are exciting times for organizations. Initially, most of the attention is focused on integrating two companies into a single entity, and exploring the new capabilities brought on due to the merger. In this environment, surrounded by organizational changes and amid swirling questions surrounding responsibility, SaaS security is often nothing more than […]

ServiceNow Data Exposure
Earlier this week, ServiceNow announced on its support site that misconfigurations within the platform could result in “unintended access” to sensitive data. For organizations that use ServiceNow, this security exposure is a critical concern that can result in a major data leakage of sensitive corporate data. ServiceNow is a cloud-based platform used for automating IT […]

Ensuring Business Continuity in Times of War
On October 7, 2023, as global news has reported, there was a brutal surprise attack by the Hamas terror organization on Israeli cities and villages. With thousands of civilian casualties, and hundreds taken hostage into the Gaza strip, Israel was forced to enter a state of war with Hamas. At Adaptive Shield, our commitment to […]

The Ultimate SaaS Security Posture Management (SSPM) Checklist
Cloud security is the umbrella that holds within it: IaaS, PaaS and SaaS. Gartner created the SaaS Security Posture Management (SSPM) category for solutions that continuously assess security risk and manage the SaaS applications’ security posture. With enterprises having 1,000 or more employees relying on dozens to hundreds of apps, the need for deep visibility […]
Right Sizing Permissions Across the SaaS Stack
Overpermissioning is one of the seven deadly SaaS sins. It paves a path straight to data leakage and catastrophic data breaches, and unnecessarily stretches resources that would be better served addressing other cyber threats. This phenomenon happens for any number of reasons. Some admins decide to grant users all access so they aren’t bothered by […]

Video Blog: Why 3rd-Party Apps Are Taking Over Your SaaS Stack
The great thing about SaaS applications is that they are quick to install and ready from the start to get employees using them for their endless business needs. They easily integrate with third-party applications to increase functionality and make it easier for employees to get their job done. The downside, of course, is this integration […]

7 Steps to Kickstart Your SaaS Security Program
SaaS applications are the backbone of modern businesses, constituting a staggering 70% of total software usage. Applications like Box, Google Workplace, and Microsoft 365 are integral to daily operations. This widespread adoption has transformed them into potential breeding grounds for cyber threats. Each SaaS application presents unique security challenges, and the landscape constantly evolves as […]

Identity Threat Detection and Response: Rips in Your Identity Fabric
Why SaaS Security Is a Challenge In today’s digital landscape, organizations are increasingly relying on software-as-a-service (SaaS) applications to drive their operations. However, this widespread adoption has also opened the doors to new security risks and vulnerabilities. The SaaS security attack surface continues to widen. It started with managing misconfigurations and now requires a […]

GitHub: Leakier than an Unsecured S3 Bucket
Over the last three years, Simple Storage Service (S3) buckets in Amazon Web Services (AWS) have leaked a lot of information. An American publishing company for educational content exposed grades and personal information for 100,000 students. A consumer ratings and review website exposed 182 GB worth of data covering American and Canadian senior citizens. Thousands […]

Adaptive Shield Secures Strategic Investment from Blackstone
We’re excited to announce a new investment from Blackstone Innovations Investments, Blackstone’s strategic investment arm, bringing our total capital raised to $44M. This investment will be used to accelerate Adaptive Shield’s mission to protect companies as the number of SaaS applications used by enterprises has continued to grow rapidly. This growth is creating a new […]

Understand Your SaaS Security Challenges: Use Cases Overview
Companies store an incredibly large volume of data and resources within SaaS apps like Box, Google Workplace, and Microsoft 365. SaaS applications make up 70% of total company software usage, and as businesses increase their reliance on SaaS apps, they also increase their reliance on security solutions. SaaS security is not a new problem, however, […]

Global Retailers Must Keep an Eye on Their SaaS Stack
Brick-and-mortar retailers and e-commerce sellers may be locked in a fierce battle for market share, but one area both can agree on is the need to secure their SaaS stack. From communications tools to order management and fulfillment systems, much of today’s critical retail software lives in SaaS apps in the cloud. Securing those applications […]

Why High Tech Companies Struggle with SaaS Security
It’s easy to think high-tech companies have a security advantage over other older, more mature industries. Most are unburdened by 40 years of legacy systems and software. They draw some of the world’s youngest, brightest digital natives to their ranks, all of whom consider cybersecurity issues their entire lives. Perhaps it is due to their […]

New Security Vulnerability in Microsoft Teams
Recently, Max Corbridge and Tom Ellson from JUMPSEC’s Red Team discovered a vulnerability in Microsoft Teams. This vulnerability allows for the introduction of malware into organizations using Microsoft Teams in its default configuration. In this blog post, we will delve into the details of this vulnerability and explore its potential impact. The Configuration In Microsoft […]

SaaS in the Real World: How Global Food Chains Can Secure Their Digital Dish
The Quick Serve Restaurant (QSR) industry is built on consistency and shared resources. National chains like McDonald’s and regional ones like Cracker Barrel grow faster by reusing the same business model, decor, and menu, with little change from one location to the next. QSR technology stacks mirror the consistency of the front end of each […]

Why High-Tech and Telecom Companies Struggle with SaaS Security
As SaaS adoption continues to grow in the business landscape, it brings emerging security challenges that high-tech and telecom companies must grapple with. A particularly attractive target for cybercriminals, the telecom industry allows attackers to inflict maximum damage with little effort. The combination of interconnected networks, customer data, and sensitive information allows cybercriminals to inflict […]

Adaptive Shield Announced as Launch Partner for Wiz Integrations (WIN)
Adaptive Shield, June 13, 2023 – Adaptive Shield, an industry leader in SaaS security, today announces its partnership with leading cloud security provider Wiz as the company unveils Wiz Integrations (WIN). Adaptive Shield, hand selected as a launch partner, brings the power of SSPM to WIN, so that customers can seamlessly integrate Wiz into their […]
New Cloud Security Alliance Survey Finds SaaS Security Has Become a Top Priority for 80% of Organizations
The Cloud Security Alliance (CSA), the world’s leading organization dedicated to defining standards, certifications, and best practices to help ensure a secure cloud computing environment, today released the findings of its latest survey, SaaS Security Survey Report: 2024 Plans & Priorities. Commissioned by Adaptive Shield, the leading SaaS Security Posture Management (SSPM) company, the survey […]

Adaptive Shield Strengthens Security Posture with New Certifications
We are happy to announce that we have successfully earned the latest International Organization for Standardization (ISO) privacy certification ISO/IEC 27701:2019 (“ISO 27701”) after an independent third-party audit by Standards Institution of Israel. Additionally, the company has successfully earned its Service Organization Control (SOC) 2 Type II certification, completed by Ernst & Young. These certifications, […]
Benchmarks for SaaS Apps: Password Management
What are Password Policies and Configurations? In a world where identity is the new perimeter, user passwords are essential to protect your SaaS applications from unauthorized access. Effective password policies that are enforced at the corporate level reduce the gateway into your corporate data. SaaS applications include a number of security settings that promote safe […]

Why Telecoms Struggle with SaaS Security
The telecom industry has always been a tantalizing target for cybercriminals. The combination of interconnected networks, customer data, and sensitive information allows cybercriminals to inflict maximum damage through minimal effort. It’s the breaches in telecom companies that tend to have a seismic impact and far-reaching implications — in addition to reputational damage, which can be […]

Benchmarks for SaaS App: Malware Protection
How does Malware Impact the SaaS Stack? Malware is harmful code designed to infect, damage, or provide access to computer systems. It can take many different forms, including viruses, worms, Trojan horses, ransomware, adware, and spyware. While it is easy to understand how that impacts a computer or mobile device, it is less clear when […]

Breach Debrief Series: Salesforce Community Sites
According to a recent report by cybersecurity expert Brian Krebs, several organizations, including banks and healthcare providers, are leaking sensitive information due to a misconfiguration in Salesforce Communities. Communities, which allows Salesforce users to easily create websites, has two means of entry. Some sites require user login, while others allow guests to view content without […]
Benchmarks for SaaS Apps: Data Leakage Protection
What are Data Leakage and Data Leakage Protection? Data leakage is the unauthorized transmission of data from within an organization to external destinations or parties. In a SaaS context, it can refer to data that is exposed without passwords or an expiration date. The data may contain sensitive financial records, customer PII, strategic documents, or […]

CASB vs SSPM
CASBs and SSPM are complementary solutions that focus on different aspects of SaaS data security. CASBs apply corporate policies relating primarily to identity, permissions, and data encryption while SSPM protects data from each individual SaaS app based on the usage and settings within each application including identity, permissions, data encryption, and much more. What is […]

What’s the Difference Between CSPM & SSPM?
Cloud Security Posture Management (CSPM) and SaaS Security Posture Management (SSPM) are frequently confused. The similarity of the acronyms notwithstanding, both security solutions focus on securing data in the cloud. In a world where the terms cloud and SaaS are used interchangeably, this confusion is understandable. This confusion, though, is dangerous to organizations that need […]
Benchmarks for SaaS Apps: Access Control
What is Access Control? Access control is the key to your SaaS kingdom. It determines who has access, their permission levels, and the steps they need to take to enter into the system. Access control is the center of your SaaS security foundation, which is why it accounts for 59% of all SaaS configurations. Of […]
Benchmarks for SaaS Apps: A Guide to Measure Your Company’s SaaS Baselines & Risk
As organizations work toward securing their SaaS apps, security teams are looking for benchmarks that can help guide their efforts. SaaS ecosystems are growing quickly, and without some standardized tool to measure success, most security teams lack the data to know where they stand. In our Benchmarks for SaaS Apps series, we’ll share benchmark data […]

Think Before You Share the Link: SaaS in the Real World
Collaboration sits at the essence of SaaS applications. The word, or some form of it, appears in the top two headlines on Google Workspace’s homepage. It can be found six times on Microsoft 365’s homepage, three times on Box, and once on Workday. Visit nearly any SaaS site, and odds are ‘collaboration’ will appear as […]

Top 7 SaaS Security Activities at RSA 2023
It’s that time of the year, when RSA brings together leaders and visionaries from across the cybersecurity world. During these four days, visitors gain insight, join conversations, and experience solutions that make an impact on their business and career. From live sessions and parties to games and demos galore, RSA packs it all. That being […]

SaaS Rootkit Exploits Hidden Rules in Microsoft 365
Microsoft is a primary target for threat actors, who scour Microsoft applications for weaknesses. Our security research team at Adaptive Shield recently discovered another new attack vector caused by a vulnerability within Microsoft’s OAuth application registration that allows attackers to leverage Exchange’s legacy API to create hidden forwarding rules in Microsoft 365 mailboxes. To understand […]

How to Apply NIST Principles to SaaS in 2023
The National Institute of Standards and Technology (NIST) is one of the standard-bearers in global cybersecurity. The U.S.-based institute’s cybersecurity framework helps organizations of all sizes understand, manage, and reduce their cyber-risk levels and better protect their data. Its importance in the fight against cyberattacks can’t be overstated. While NIST hasn’t directly developed standards […]
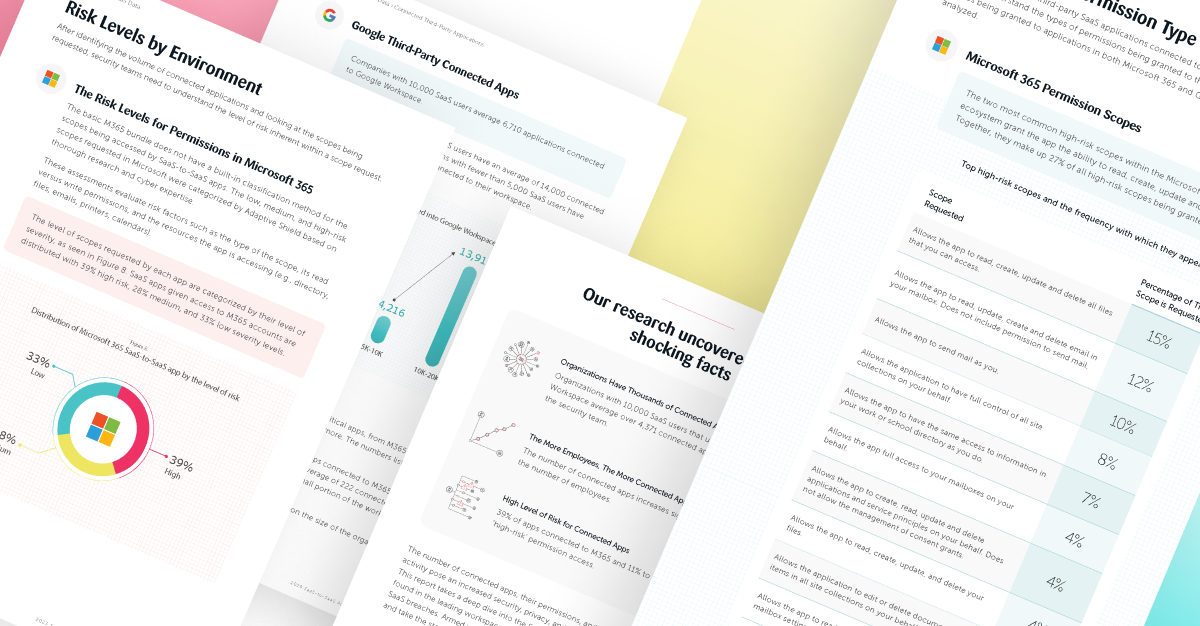
Shocking Findings from the 2023 Third-Party App Access Report
Spoiler Alert: Organizations with 10,000 SaaS users that use M365 and Google Workspace average over 4,371 additional connected apps. SaaS-to-SaaS (third-party) app installations are growing nonstop at organizations around the world. When an employee needs an additional app to increase their efficiency or productivity, they rarely think twice before installing. Most employees don’t even realize […]

Granting 3rd-Party Apps Access to Microsoft 365 and Google Workspace Presents Major Security Risks, According to Adaptive Shield Report
Tel Aviv, February 27, 2023—Adaptive Shield, the leading SaaS Security company, today announced the release of its SaaS-to-SaaS Access Report. According to the research, employees are granting thousands of third-party apps access to the two most dominant workspaces, Microsoft 365 (M365) and Google Workspace. With no oversight or control from security teams, companies have no […]
SaaS in the Real World: Who’s Responsible to Secure This Data
When SaaS applications started growing in popularity, it was unclear who was responsible for securing the data. What’s far murkier, however, is where the data responsibility lies on the organization’s side. For large organizations, this is a particularly challenging question. They store terabytes of customer data, employee data, financial data, strategic data, and other sensitive […]

What Are the Cyber Risks with SaaS?
Security teams can’t protect every byte within their digital footprint. Limited resources mean making choices, and so security teams run assessments to evaluate the value of their assets, the cost to protect those assets, and the damage to the company should an asset be breached or compromised. In some industries, regulatory requirements shape those decisions, […]

Adaptive Shield Partners with Datadog for Seamless SaaS Security Management
Adaptive Shield has partnered with Datadog, the observability service for cloud-scale applications, to provide joint customers with the ability to stream and visualize SaaS security alerts from Adaptive Shield. Adaptive Shield continuously monitors all SaaS apps, users, and associated devices, the platform immediately identifies, alerts, auto-fixes or provides actionable remediation information when any misconfiguration or […]

SaaS Security Posture Management (SSPM) as a Layer in Your Identity Fabric
The move to SaaS and other cloud tools has put an emphasis on Identity & Access Management (IAM). After all, user identity is one of the only barriers standing between sensitive corporate data and any unauthorized access. The tools used to define IAM make up its identity fabric. The stronger the fabric, the more resistant […]

Why Do User Permissions Matter for SaaS Security?
Earlier this year, threat actors infiltrated Mailchimp, the popular SaaS email marketing platform. They viewed over 300 Mailchimp customer accounts and exported audience data from 102 of them. The breach was preceded by a successful phishing attempt and led to malicious attacks against Mailchimp’s customers’ end users. Three months later, Mailchimp was hit with another […]

Breach Debrief Series: Nissan North America
Nissan North America is informing customers of a data breach that occurred at a third-party service provider. The security incident was reported to the Office of the Maine Attorney General on January 16, 2023, and it was disclosed that almost 18,000 customers were affected by the breach. According to the notification, Nissan received notice of […]

100 Apps, Endless Security Checks
On average, organizations report using 102 business-critical SaaS applications, enabling operations of most departments across an organization, such as IT and Security, Sales, Marketing, R&D, Product Management, HR, Legal, Finance, and Enablement. An attack can come from any app, no matter how robust the app is. Without visibility and control over a critical mass of […]

SaaS in the Real World: User Access After Downsizing
Over the last year, we’ve seen increasing evidence of an upcoming recession. Interest rate hikes and inflation, energy uncertainty, and the war in Ukraine are all harbingers of rough times ahead. CNBC reported that more than 50,000 employees from Twitter, Meta, Amazon, Salesforce, and other tech companies lost their jobs in November. While no one […]

Slack GitHub Breach: How It Happened and How You Can Protect Your Repository
Earlier today, a story broke that GitHub repositories of Slack were breached over the holiday weekend. Slack detected the breach after noticing suspicious activity, and in their investigation found that stolen Slack employee tokens were the source of the breach. As a result of the attack, private Slack code repositories were downloaded, but no customer […]

SaaS in the Real World: M&A Due Diligence
Business leaders may fear an upcoming recession, but they fear falling behind their competitors even more. PwC’s November Pulse Survey found that 35% of executives are planning an acquisition or divestiture within the next 12-18 months. M&A has proven itself to be a key to business resurgence, strategic growth, and capability expansion. One area that’s […]

Keeping SaaS Apps HIPAA Compliant
Healthcare has been cautious in moving toward cloud technologies and SaaS applications. Concerns over privacy and the need to comply with HIPAA regulations had left them stuck using on-premises software solutions. However, COVID forced healthcare organizations to develop telehealth models. Patients increasingly wanted digital access to their records, and healthcare organizations recognized the need to […]

Top 4 SaaS Security Threats for 2023
With 2022 coming to a close, there is no better time to buckle down and prepare to face the security challenges in the year to come. This past year has seen its fair share of breaches, attacks, and leaks, forcing organizations to scramble to protect their SaaS stacks. March alone saw three different breaches from […]

What is SSPM?
The short answer: It’s no secret that in today’s day and age, organizations rely heavily on hundreds of SaaS apps for their day-to-day operations. While SaaS apps include a host of native security settings, they need to be hardened and monitored by the organization’s security team. SaaS Security Posture Management (SSPM), a category created by […]
Webinar Spotlight: Pinpoint Your SaaS App Risks from Evaluation to Usage
This past month, Adaptive Shield partnered with Panorays (a SaaS-based third-party security risk management platform) to produce a joint webinar Pinpoint Your SaaS App Risks: From Evaluation to Usage. These two security experts, Maor Bin, CEO of Adaptive Shield, and Demi Ben Ari, CTO OF Panorays, discussed the evolution of third-party apps, the tools used […]
Adaptive Shield Releases SaaS-to-SaaS Capabilities to Minimize Supply Chain Risks
Tel Aviv, November 30, 2022—Adaptive Shield, the leading SaaS Security Posture Management (SSPM) company, today announced new capabilities to discover and monitor 3rd party apps connected to the core SaaS stack. With this new capability, Adaptive Shield is minimizing the risk that SaaS-to-SaaS, also known as 3rd party app access, presents. Security teams can now […]

Key Takeaways from Forrester’s Embrace A Paradigm Shift In SaaS Protection: SaaS Security Posture Management Report
Forrester, a research and advisory company, offers organization’s a variety of services including research and consulting. Their reports help professionals understand their customer’s behavior, concerns, and interests to help organizations make more informed decisions. Their Trend Report ‘Embrace A Paradigm Shift In SaaS Protection: SaaS Security Posture Management’ looks at the increased use of SaaS […]
Use Case Series: Identity and Access Management Governance
Every SaaS app user and login is a potential threat; whether it’s bad actors or potential disgruntled former associates, identity management and access control is crucial to prevent unwanted or mistaken entrances to the organization’s data and systems. Since enterprises have thousands to tens of thousands of users, and hundreds to thousands of different apps, […]

Adaptive Shield Announces 100 SaaS App Integrations for Comprehensive SaaS Security
Tel Aviv, November 9, 2022—Adaptive Shield, the leading SaaS Security Posture Management (SSPM) company, today announced it is the first and only SSPM platform to cover 100 SaaS platforms and applications out of the box. Security teams will now be able to gain visibility and control of 100 SaaS apps and automate misconfiguration management, monitor […]

Webinar Spotlight: SaaS Security Trends, Challenges, and Solutions for 2022
“SaaS applications have native security controls as part of their offering which makes them security products themselves — that security teams now need to manage”. Asserted by Adaptive Shield’s CEO, Maor Bin partnered with Okta’s VP of Strategy, Stephen Lee in the Security Boulevard Webinar: SaaS Security Trends, Challenges, and Solutions for 2022. This joint […]

The Ultimate SaaS Security Posture Management Checklist, 2023 Edition
The ease with which SaaS apps can be deployed and adopted today is remarkable, but it has become a double-edged sword. On the one hand, apps are quickly onboarded, employees can work from anywhere, and there is little need for operational management. On the other hand, there are pain points that stem from the explosion […]

New 2022 SaaS Security Survey Report Shines a Light on CISOs’ Perspectives for Today’s Enterprises
It’s without a doubt that the SaaS app attack surface has been continuing to grow as businesses have become more reliant on apps to organize and run their business-critical operations. To better understand how teams are dealing with their SaaS security posture, Adaptive Shield partnered with the leading organization dedicated to promoting best practices for […]
Not All Sandboxes Are for Children: How to Secure Your SaaS Sandbox
When creating a Sandbox, the mindset tends to be that the Sandbox is considered a place to play around, test things, and there will be no effect on the production or operational system. Therefore, people don’t actively think they need to worry about its security. This mindset is not only wrong, but extremely dangerous. When […]

Ensuring SaaS Security in ISO Compliance
The International Organization for Standardization (ISO) sets standards across various industries. As an internationally recognized standards organization, its two information technology security standards – ISO 27000:2018 and ISO 27001:2013 – can be used to help build out a strong security posture. SaaS security is critical to ISO compliance in the modern business world. However, with […]

Adaptive Shield and Tenable Partner to Enhance SaaS Security Posture
TEL AVIV, Israel – Sept 13 2022 – Adaptive Shield, the leading SaaS Security Posture Management (SSPM) company, today announced a partnership with Tenable, the Cyber Exposure Management company, to provide a consolidated posture management solution that correlates the risk of SaaS users and their endpoints. While SaaS providers build in security features, it is […]

GIFShell Attack Through Microsoft Teams: What Is It and How You Can Protect Yourself from It
Another day, another attack method. The Short Story GIFShell attack technique enables bad actors to exploit several Microsoft Teams features to act as a C&C for malware, and exfiltrate data using GIFs without being detected by EDR and other network monitoring tools. The technique assumes an already-compromised target. GifShell Attack Architecture & Process Discovered by […]
Misconfigurations 101: The Three V’s of SaaS App Configurations Weaknesses
The ease with which SaaS apps can be deployed and adopted is remarkable, but it has quickly become a double-edged sword. On one hand, the availability of SaaS tools enables employees to work from anywhere. For IT and security teams however, the adoption of SaaS apps has become a daunting endeavor. CISOs and security professionals […]

The Next Trends In SaaS Security
According to Okta’s Business of Work report, large companies use 187 different SaaS apps on average, and this number is only growing—Gartner reports that end-user spending on SaaS will reach more than $171 billion in 2022. As this investment trend continues, new critical SaaS challenges emerge beyond the classic use case of misconfiguration and user […]
SaaS Security Use Case Series: Device-to-SaaS User Risk
Typically, when threat actors look to infiltrate an organization’s SaaS apps, they look to SaaS app misconfigurations as a means for entry. However, employees now use their personal devices, whether their phone or personal laptop, etc. to get their jobs done. If the device’s hygiene is not up to par, it increases the risk for […]

SaaS Security Use Case Series: SaaS-to-SaaS Access
It’s no secret that SaaS-to-SaaS apps can boost productivity, enable remote and hybrid work and are overall, essential in building and scaling a company’s work processes. It’s an innocuous process much like clicking on an attachment was in the earlier days of email — people don’t think twice when connecting an app they need with […]
What It Takes to Tackle Your SaaS Security
It’s not a new concept that Office 365, Salesforce, Slack, Google Workspace or Zoom, etc. are amazing for enabling the hybrid workforce and hyper productivity in businesses today. However, there are three main challenges that have arisen stemming from this evolution: (1) While SaaS apps include a host of native security settings, they need to […]

Adaptive Shield Selected as SC Media Trust Award Finalist for Best Cloud Security Posture Management Solution
Tel Aviv – July 6, 2022, Adaptive Shield today announced that its SaaS Security Posture Management (SSPM) platform has been recognized as a Trust Award finalist in the Best Cloud Security Posture Management Solution category for the 2022 SC Awards. Now in its 25th year, the SC Awards are cybersecurity’s most prestigious and competitive program […]

Omdia’s On the Radar Report Covers Adaptive Shield’s SSPM Solution
Adaptive Shield is officially On the Radar in Omdia’s report for an innovative solution making a big impact in the SaaS security space. In the report, Rik Turner, Senior Principal Analyst at Omdia, discusses accelerated cloud adoption, the rapid increase in threats, and ongoing shortage of skilled security professionals, that is driving the cybersecurity world […]
Top 5 Configurations to Check When Setting Up a New SaaS App
The old days of buying new software, installing it on the company servers, and making sure everything works is gone. All hail the new IT king – SaaS platforms. Ready to go from the start, no installation needed, no hardware involved, and easy to connect the organization and its users. An IT department haven of […]

RSA 2022 Recap
After 2 years of virtual events, RSA Conference 2022 in San Francisco brought back face-to-face interaction. And wow, what an experience! From live sessions and parties to games and demos galore, RSA was packed with it all. Here’s a recap of Adaptive Shield at RSA. Maor Bin’s Session: The SaaS RootKit: A New Attack Vector […]

Best Practices for an SSPM Solution to Help You Secure Your SaaS App Stack
The SaaS app attack surface has widened and recent research shows that up to 63 percent of organizations have dealt with security incidents because of a SaaS misconfiguration. Lack of visibility, thousands of configurations for the security team to monitor and remediate, and too many departments with access are the leading causes of SaaS misconfigurations. […]

Adaptive Shield Recognized as a 2022 Gartner® Cool Vendors™
We are excited to announce that Gartner has named us a 2022 Gartner Cool Vendors™ in Application Security: Protection of Cloud-Native Applications. According to the Gartner report, “Digital business initiatives have accelerated, and this, in turn, has accelerated development of cloud-native applications. This creates challenges in terms of securing these applications.” At a time when […]

Manual vs. SSPM: Research on What Streamlines SaaS Security Detection & Remediation
When it comes to keeping SaaS stacks secure, IT and security teams need to be able to streamline detection and remediation of misconfigurations in order to best protect their SaaS stack from threats. However, while companies adopt more and more apps, their increase in SaaS security tools and staff has lagged behind, as found in […]

7 Significant Findings from the 2022 SaaS Security Survey Report
Last year, we spearhead our first annual SaaS Security Survey Report, where the findings illuminated the SSPM landscape and where the market was holding. In the 2022 SaaS Security Survey Report, in collaboration with CSA, we examine the state of SaaS security in today’s enterprises and see how much the market and the overall space of […]

Top 13 Cloud and SaaS Security Talks at RSA 2022
Every year the leaders and entrepreneurs of the cybersecurity world come together for four days for the annual RSA Conference. During these four days, visitors gain insight, join conversations, and experience solutions that could make an impact on their businesses and careers. Finally, after many years of the event being virtual, RSA is back in […]

SSPM Solving the SaaS Security Challenge of “Too Much to Do, Too Little Time”
“How many people do you know that clean their house once a quarter? …you have to keep a certain level of hygiene both in your house and your SaaS stack.” Uttered by our CEO, Maor Bin, in a webinar with Omdia Senior Principal Analyst, Rik Turner about the growing need to take a proactive, automated approach […]

Top 5 Attacks in Commonly Used SaaS Apps
Remember when cybersecurity was mostly about firewalls, VPNs, and antivirus software? Those days are long gone. Now one of the most prevalent places for exploitation has to do with misconfigurations found in an organization’s SaaS apps. If you are in IT, you might have come across the following scenario: an admin of a business-critical SaaS […]
Into the Breach: Breaking Down 3 SaaS App Attacks in 2022
During the last week of March, three major tech companies – Microsoft, Okta, and HubSpot – reported significant data breaches. DEV-0537, also known as LAPSUS$, performed the first two. This highly sophisticated group utilizes state of the art attack vectors to great success. Meanwhile, the group behind the HubSpot breach was not disclosed. This blog […]

Adaptive Shield Partners With CrowdStrike to Introduce Zero Trust SaaS Security Posture Solution to CrowdStrike Store
This new partnership delivers security controls over SaaS environments including the ability to identify high-risk users and non-compliant devices Tel Aviv, March 15, 2022— Adaptive Shield, the leading SaaS Security Posture Management (SSPM) company, today announced it will partner with CrowdStrike, a leader in cloud-delivered protection of endpoints, cloud workloads, identity and data, to introduce […]

How SSPM Simplifies Your SOC2 SaaS Security Posture Audit
An accountant and a security expert walk into a bar… SOC2 is no joke. Whether you’re a publicly held or private company, you are probably considering going through a Service Organization Controls (SOC) audit. For publicly held companies, these reports are required by the Securities and Exchange Commission (SEC) and executed by a Certified Public […]
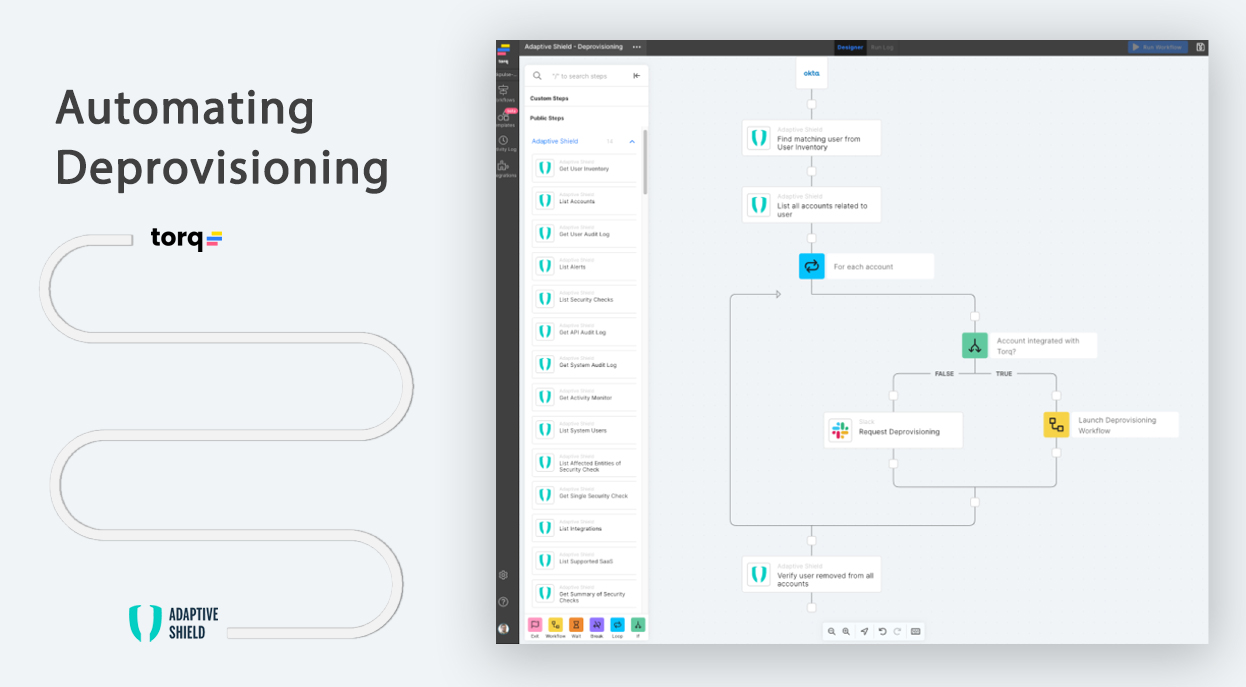
The Importance of Automated Offboarding to Keep Your SaaS Stack Safe
In the busy enterprise computing environment, user onboarding and offboarding is a fact of daily life. When employee counts range into five figure territory — and entire networks of contractors have to be accounted for as well — it’s easy to lose track of who’s, literally, coming and going. Oftentimes, there are “offboarding” steps that […]

Adaptive Shield Joins Cloud Security Alliance to Raise Awareness Around Critical SaaS Risks
TEL AVIV, Israel, Jan. 11, 2022 — Adaptive Shield, the leading SaaS Security Posture Management (SSPM) company, today announced that it has joined the Cloud Security Alliance (CSA), the world’s leading organization dedicated to defining and raising awareness of best practices to help ensure a secure cloud computing environment. The threat landscape for SaaS security […]

Adaptive Shield and Okta Join Forces to Deliver Integrated Solution for Fortified SaaS Security and Identity and Access Management
Tel Aviv, December 7, 2021—Adaptive Shield, the leading SaaS Security Posture Management (SSPM) company, today announced a tech integration with Okta, Inc. (NASDAQ: OKTA), the leading independent identity provider. Working together, the companies will deliver businesses an integrated solution to manage SaaS security configurations, enhance Identity and Access Management (IAM), and strengthen governance for privileged […]

Top 3 SaaS Security Threats for 2022
With 2021 drawing to a close and many closing their plans and budgets for 2022, the time has come to do a brief wrap up of the SaaS Security challenges on the horizon. Here are the top 3 SaaS security posture challenges as we see them. The Mess of Misconfiguration Management The good news is […]

A Guide to Shift Away from Legacy Authentication Protocols in Microsoft 365
Introduction Microsoft 365 (M365), formerly called Office 365 (O365), is Microsoft’s cloud strategy flagship product with major changes ahead, such as the deprecation of their legacy authentication protocols. Often stored on or saved to the device, Basic Authentication protocols rely on sending usernames and passwords with every request, increasing the risk of attackers capturing users’ […]

SaaS Attacks: Lessons from Real-Life Misconfiguration Exploits
It’s unfortunate, but true: SaaS attacks continue to increase. You can’t get around it, COVID-19 accelerated the already exploding SaaS market and caused industries not planning on making a switch to embrace SaaS. With SaaS apps becoming the default system of record for organizations, it has left many struggling to secure their company’s SaaS estate. […]
Securing SaaS Apps: CASB vs. SSPM
There is often confusion between Cloud Access Security Brokers (CASB) and SaaS Security Posture Management (SSPM) solutions, as both are designed to address security issues within SaaS applications. CASBs protect sensitive data by implementing multiple security policy enforcements to safeguard critical data. For identifying and classifying sensitive information, like Personally Identifiable Information (PII), Intellectual Property […]

Adaptive Shield Receives $30M Series A Investment from Insight Partners to Help Businesses Gain Control of All their SaaS Investments
Today, we announced a $30M series A round of financing led by New York-based global private equity and venture capital firm Insight Partners, with additional investors including Okta Ventures and existing investor, Vertex Ventures Israel. Adaptive Shield will use the funding to enable companies to secure their SaaS stacks, many of which are already compromised […]

The 2021 SaaS Security Report Uncovers Top Security Concerns of Today’s CISOs
The 2021 SaaS Security Survey report is a deep-dive on the state of SaaS security for today’s enterprises. It looks at the top risks that security professionals identify in their organizations, how CISOs feel about the security of an ever-growing SaaS-based environment, and how this concern impacts the approach they use for protecting and managing […]
Who Has Control: The SaaS App Admin Paradox
Imagine this: a company-wide lockout to the company CRM, like Salesforce, because the organization’s external admin attempts to disable MFA for themselves. They don’t think to consult with the security team and don’t consider the security implications, only the ease which they need for their team to use their login. This CRM, however, defines MFA […]

Ransomware Through SaaS: The New Frontier
It might sound dramatic to call ransomware a “scourge on business,” but the reality is that more companies are impacted every day. Some of these attacks hit the news cycle, but many don’t. As you look to protect yourself against the ever-burgeoning threat landscape, securing your Software-as-a-Service (SaaS) application stack is more important than ever. […]

How Were 38 Million Records Exposed from Microsoft’s Power Apps?
August 24th, The Hacker News reported about a massive leak of 38 million records from upwards of a thousand web apps. These records included Microsoft’s own employee information (a.o. home addresses, social security numbers and vaccination status) which were left exposed online for anyone to find. Governmental bodies from places such as Maryland and New […]

Adaptive Shield Named Winner in Black Unicorn Awards for 2021
LAS VEGAS, NEVADA, AUGUST 2, 2021 – Adaptive Shield, the leading SaaS Security Posture Management (SSPM) company, today announced that is has been named a winner in the Black Unicorn Awards for 2021 in the subcategory of Top 10 Baby Black Unicorns for 2021 at Black Hat USA 2021. “We’re excited to name Adaptive Shield […]

The Cybersecurity Executive Order 2021: What It Means for Cloud and SaaS Security
In response to malicious actors targeting US federal IT systems and their supply chain, the President released the “Executive Order on Improving the Nation’s Cybersecurity (Executive Order).” Although directed at Federal departments and agencies, the Executive Order will likely have a ripple effect through the Federal technology supply stream. Private companies and enterprises will look […]

Salesforce Release Updates: A Cautionary Tale for Security Teams
On the surface, Salesforce seems like a classic Software-as-a-Service (SaaS) platform. Someone might even argue that Salesforce invented the SaaS market. However, the more people work with the full offering of Salesforce, the more they realize that it goes beyond a traditional SaaS platform’s capabilities. For example, few people talk about managing the security aspects […]

Adaptive Shield Partners with Macnica Networks for Expansion into Japan
Tel-Aviv, Israel, Tokyo, Japan — Adaptive Shield, leaders in SaaS Security Posture Management (SSPM), is pleased to announce that it has entered into a distribution agreement with Macnica Networks Corp., Japan’s global technology solutions company that analyzes cyber threats targeting Japanese organizations and provides security solutions. Today, SaaS apps have become the business of record, […]

NIST Cybersecurity Framework: A Quick Guide for SaaS Security Compliance
When I want to know the most recently published best practices in cyber security, I visit The National Institute of Standards and Technology (NIST). From the latest password requirements (NIST 800-63) to IoT security for manufacturers (NISTIR 8259), NIST is always the starting point. NIST plays a key role as a US standard-setter, due to […]

How the Work-From-Home Shift Impacts SaaS Security
The data is in. According to IBM Security’s 2020 Cost of a Data Breach Report, there is a 50% increase in cloud usage for enterprises across all industries. The number of threats targeting cloud services, predominantly collaboration services like Office 365, has increased 630%. Moreover, 75% of respondents report that discovery and recovery time from […]

Adaptive Shield named Winner for Next Gen in Vulnerability Management during RSA Conference 2021
Adaptive Shield Wins Next-Gen Vulnerability Assessment, Remediation and Management Award in the 9th Annual Global InfoSec Awards at #RSAC 2021 SAN FRANCISCO, MAY 20, 2021 – Market leader in SaaS Security Posture Management (SSPM), Adaptive Shield has been awarded: Next Gen Vulnerability Assessment, Remediation and Management “We’re thrilled to receive this prestigious cybersecurity award from […]

Why SaaS Security is So Hard
It’s never quiet in the era of cybercrime — and becoming the more common vector for bad actors and infiltration is within the company’s SaaS security posture. With the SaaS market growing at 30% per year and with Deloitte and others predicting that post-covid, the SaaS model will be even more widespread, it is safe […]

The Weakest Link in Your Security Posture: Misconfigured SaaS Settings
In the era of hacking and malicious actors, a company’s cloud security posture is a concern that preoccupies most, if not all, organizations. Yet even more than that, it is the SaaS Security Posture Management (SSPM) that is critical to today’s company security. Recently Malwarebytes released a statement on how they were targeted by Nation-State […]

CISO/Security Vendor Relationship Podcast Talks About SaaS Security Posture and More
Released last week, the CISO/Security Vendor Relationship podcast, hosted by David Spark and Mark Johnson, with our sponsored guest, Travis Hoyt, TIAA’s Managing Director of exec cybersecurity technology went live! Here’s a recap if you haven’t had a chance to hear it yet. Travis opened the show with his ten-second tip, advising listeners they need […]

Adaptive Shield Delivers SaaS Security on the Snowflake Data Marketplace
A typical enterprise has on average 288 SaaS applications, which according to the 2020 SaaS Trends Reports increases 30% year over year. No need to spell it out, but that’s a lot of data points, workloads and sensitive information flowing. Enter Snowflake, the Data Cloud company that gives companies the ability to unify all of […]
Solarwinds Source Code Breach – How to Protect Your Source Code Management Platform
If you’re a security professional, by now, you’ve already heard about the epic Solorigate or Sunburst breach. The massive hack was exposed in mid-December 2020 (ah 2020; the “gift” that just keeps on giving…) and compromised numerous high-profile companies and government organizations. Security giant FireEye first discovered the widespread breach which resulted in obtaining code […]

What Airports Have in Common With SaaS Security Misconfigurations
Airports are among the most secure buildings in the world. Whether it’s London’s Heathrow, The Windy City’s O’Hare, or any other airport across the globe, what’s certain is that they deploy an impressive array of scanning equipment, facial recognition tools, physical security teams, and artificial intelligence systems to keep operations flowing smoothly and prevent threats. […]

Prevent Unwanted Guests in Your Mailboxes
SaaS vendors are continuously improving their native security controls, with the intention of preventing misconfigurations that can lead to dangerous consequences. In practicality, this means that if a SaaS provider has reason to believe a user’s mailbox has been hacked, the user will receive an alert directly to their inbox notifying them of the suspicious […]

Worried About SaaS Misconfigurations? You Should Be. Check These 5 Settings Everybody Misses
Enterprises depend on SaaS applications for countless functions, like collaboration, marketing, file sharing and more. But problematically, they often lack the resources to configure those apps to prevent cyberattacks, data exfiltration, and other risks. Catastrophic and costly data breaches result from SaaS security configuration errors. The Verizon 2020 Data Breach Investigations Report found that errors […]

Account Takeovers (ATOs): Why They Happen, What Organizations are Doing to Prevent Them, And Why it’s Not Enough
Account Takeovers (ATOs) are a major threat to organizations around the world. This common form of attack occurs when a cyber criminal uses legitimate credentials to gain unauthorized access to user accounts. Once inside, the attacker may steal data (PII or sensitive corporate data), steal money, and perform fraud campaigns. Each year, organizations lose millions […]
Extending Complete Control Across SaaS Applications With Adaptive Shield
As security professionals who have spent more than a few years in the industry, we know a good challenge when we see one. That’s why we started Adaptive Shield–to address the critical issue of proactively maintaining continuous security for the myriad of SaaS applications used in organizations across the globe. Today, organizations have anywhere from […]

Using Zoom? Stay Secure With These 12 Tips
On March 11th, 2020, the World Health Organization recognized the global outbreak of COVID-19 as a pandemic. In times like these, many companies encourage or mandate their employees to work from their homes to ensure they remain healthy and safe. During mandatory Work From Home situations, business communication and productivity are major factors of success. […]











